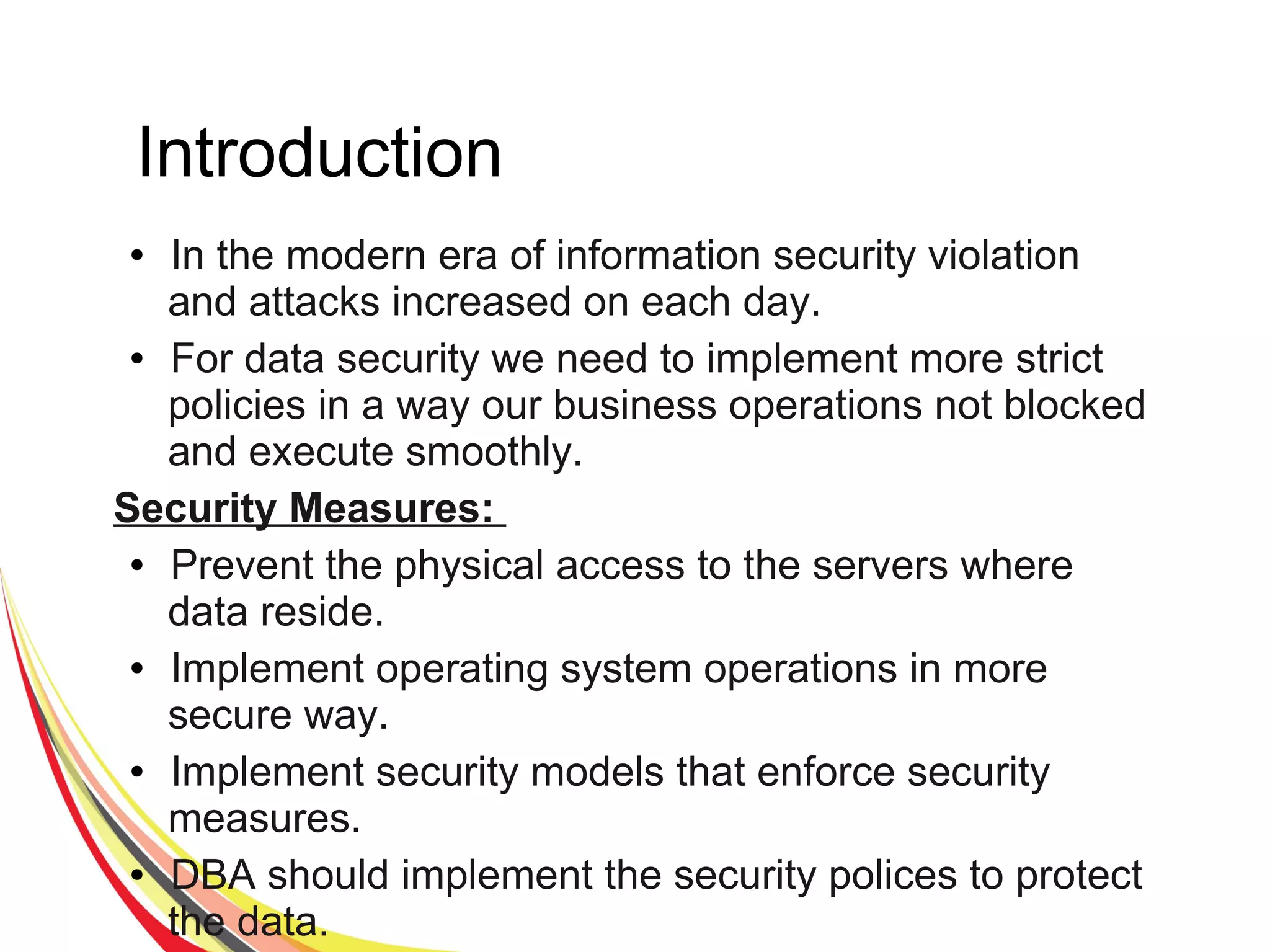
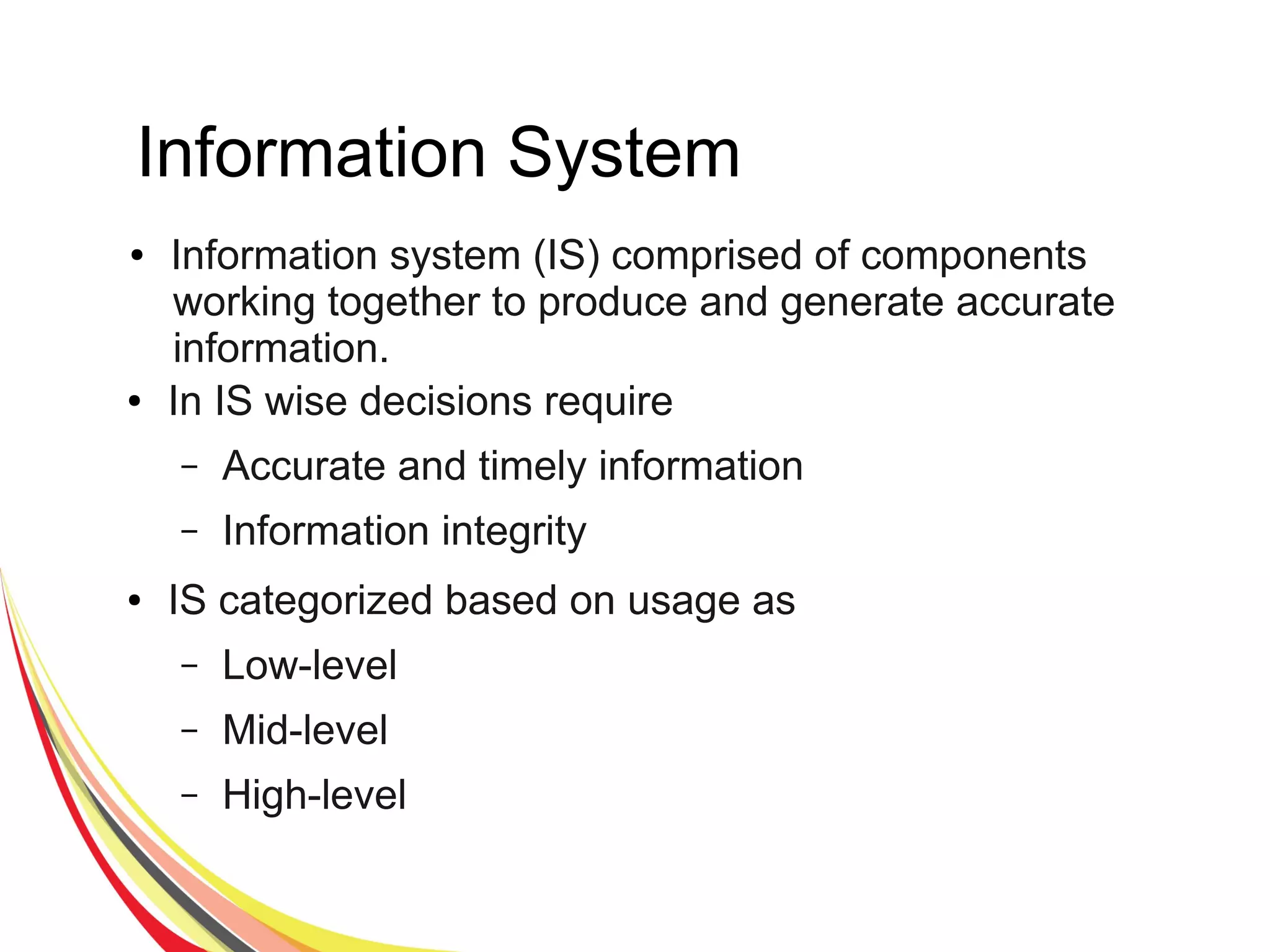
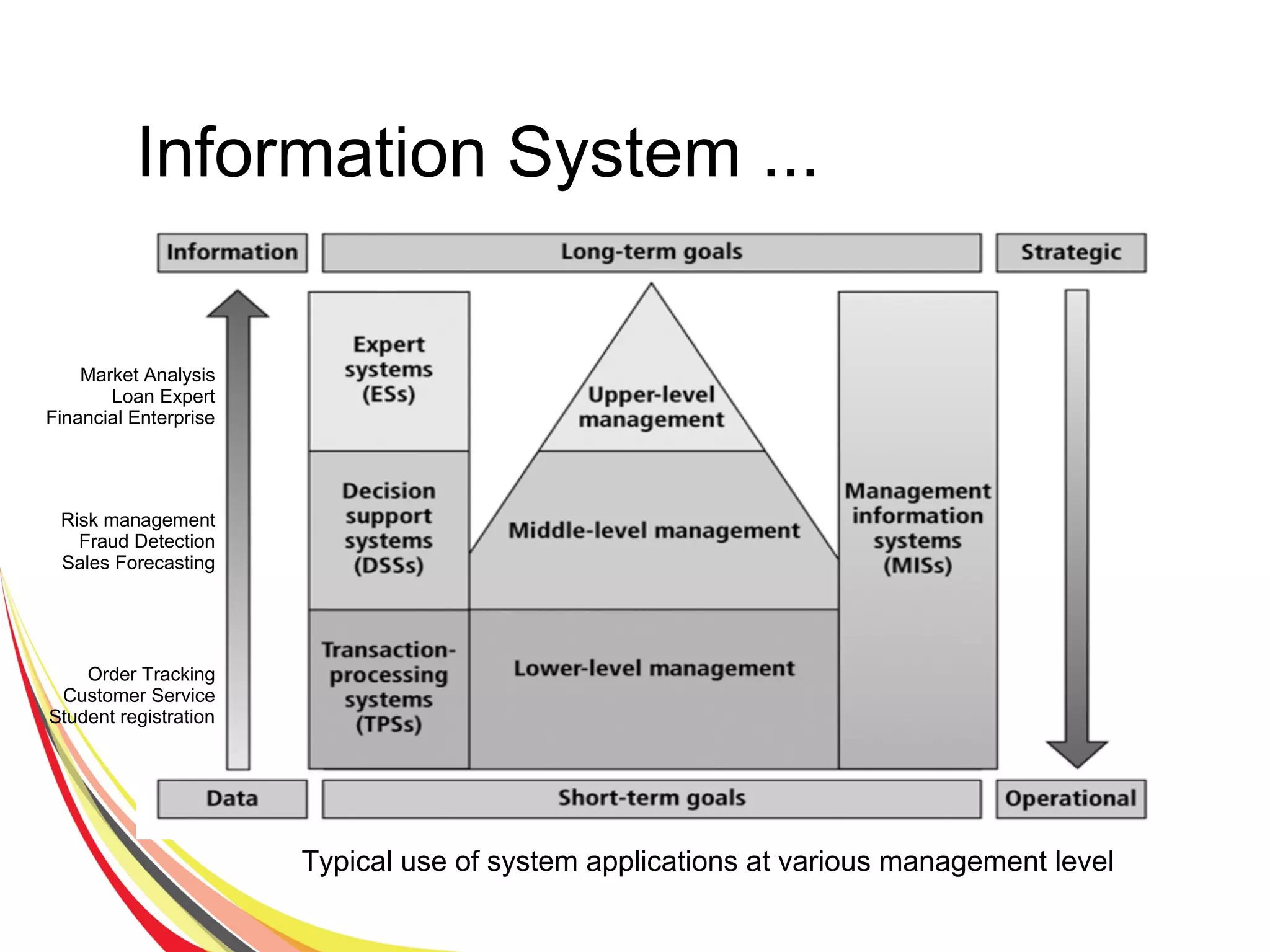
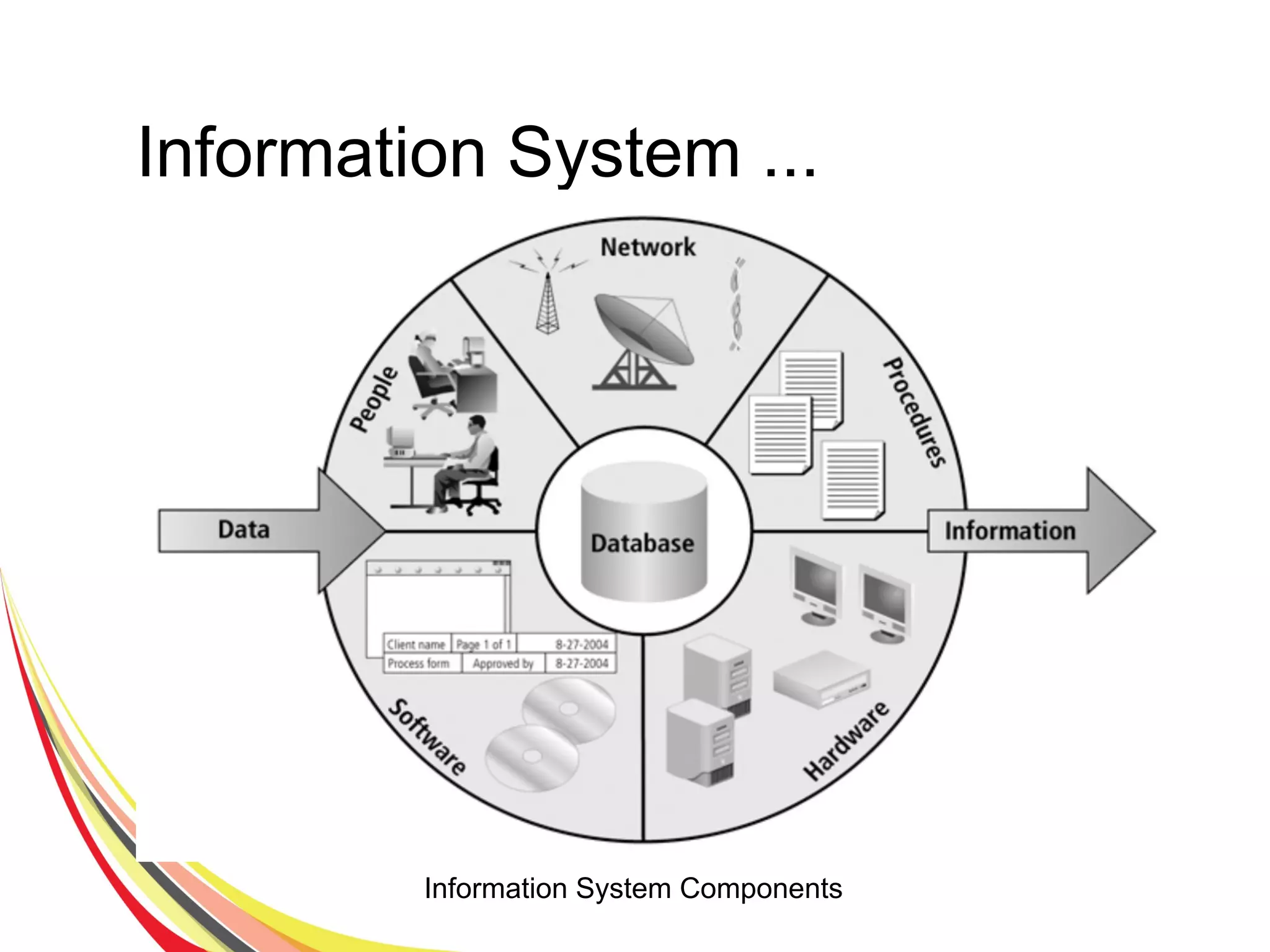
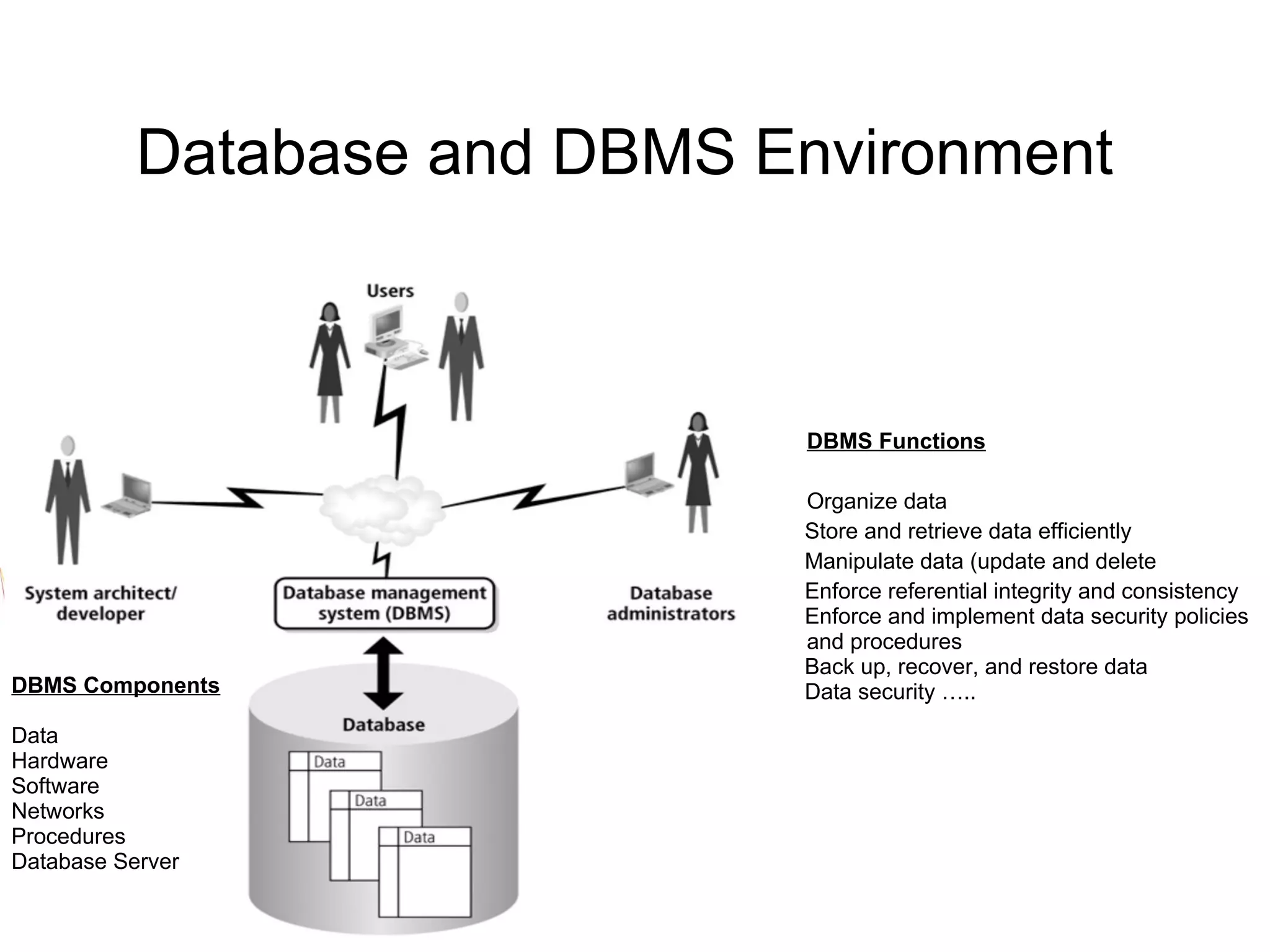
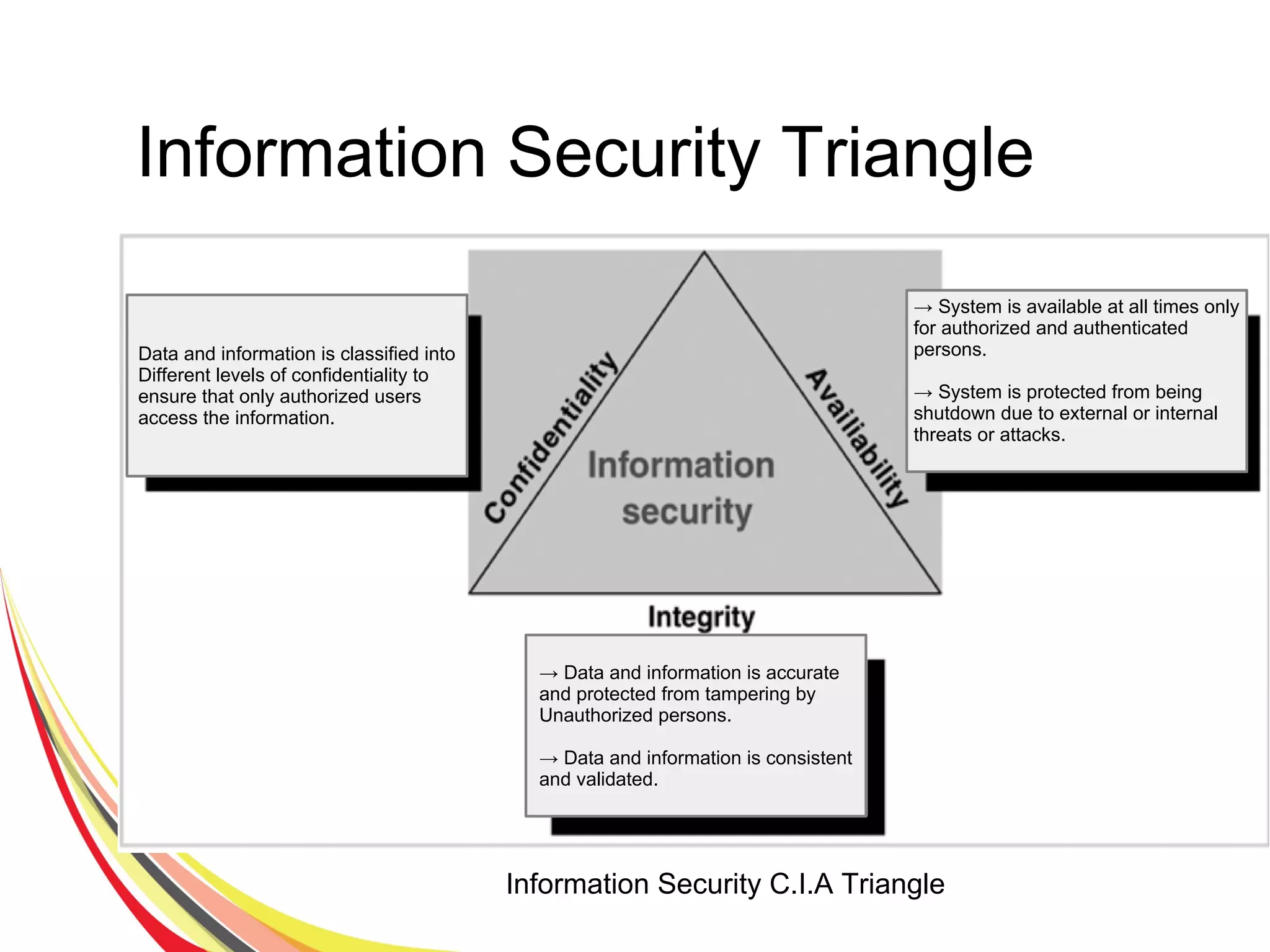
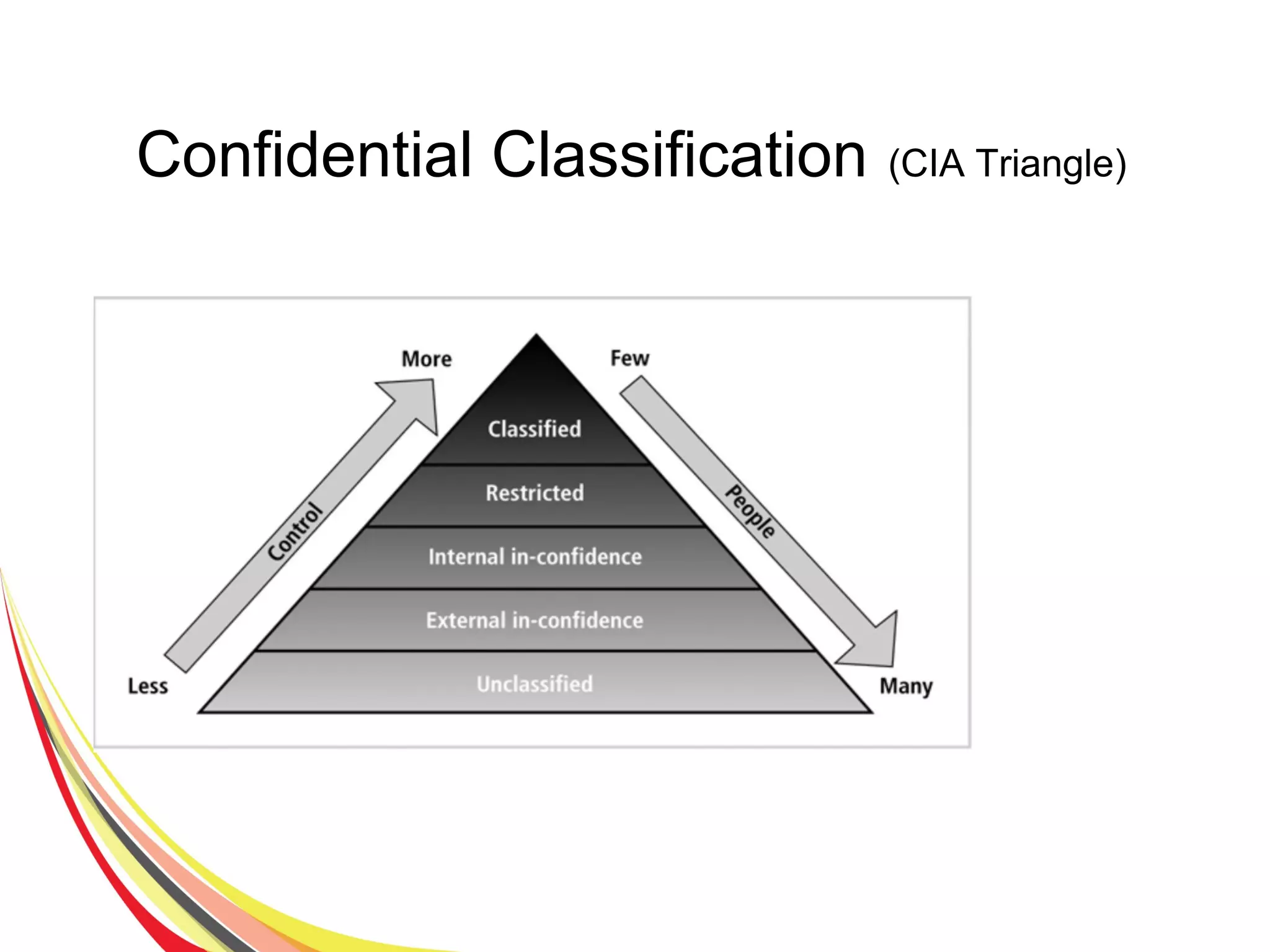
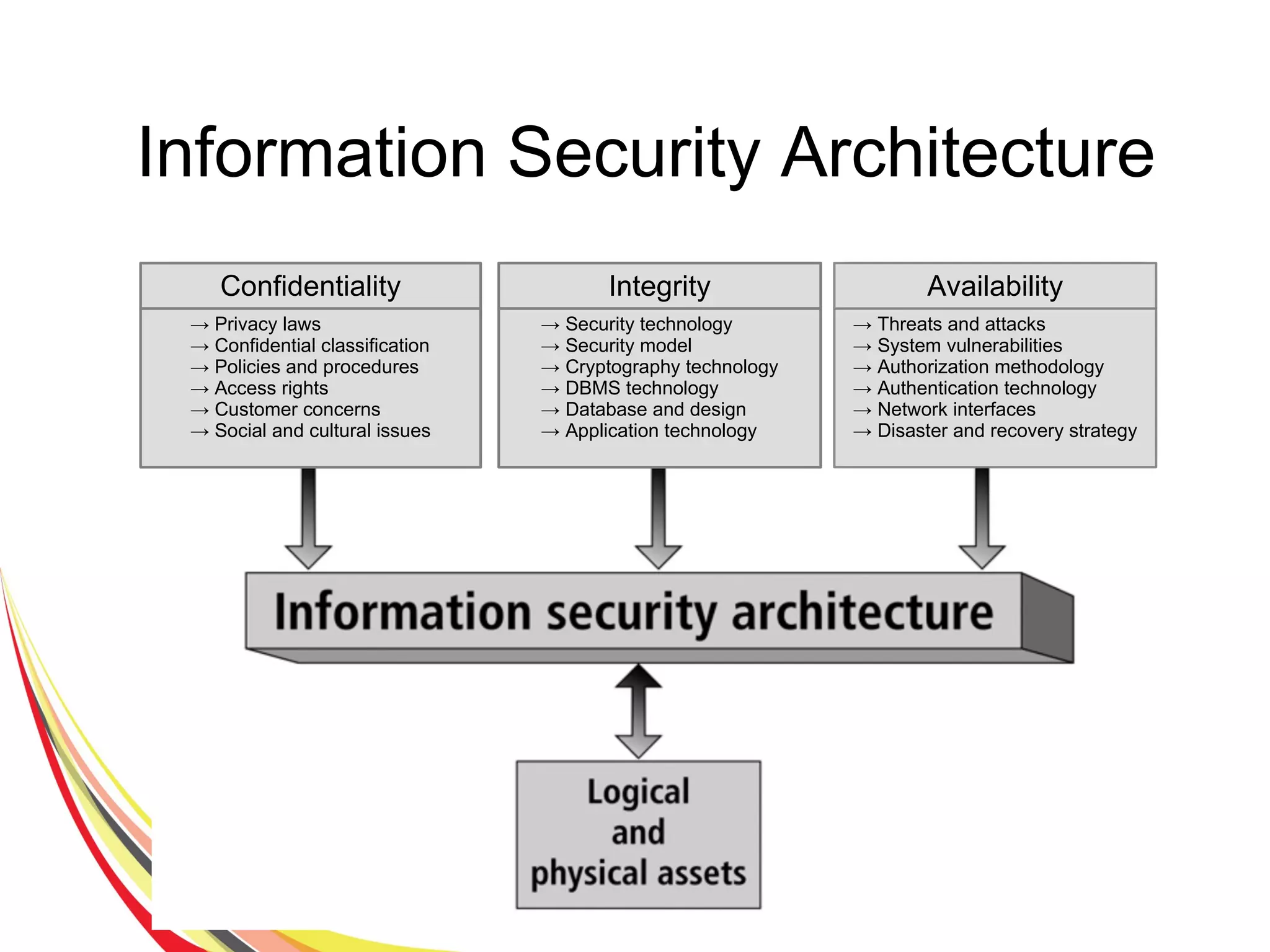
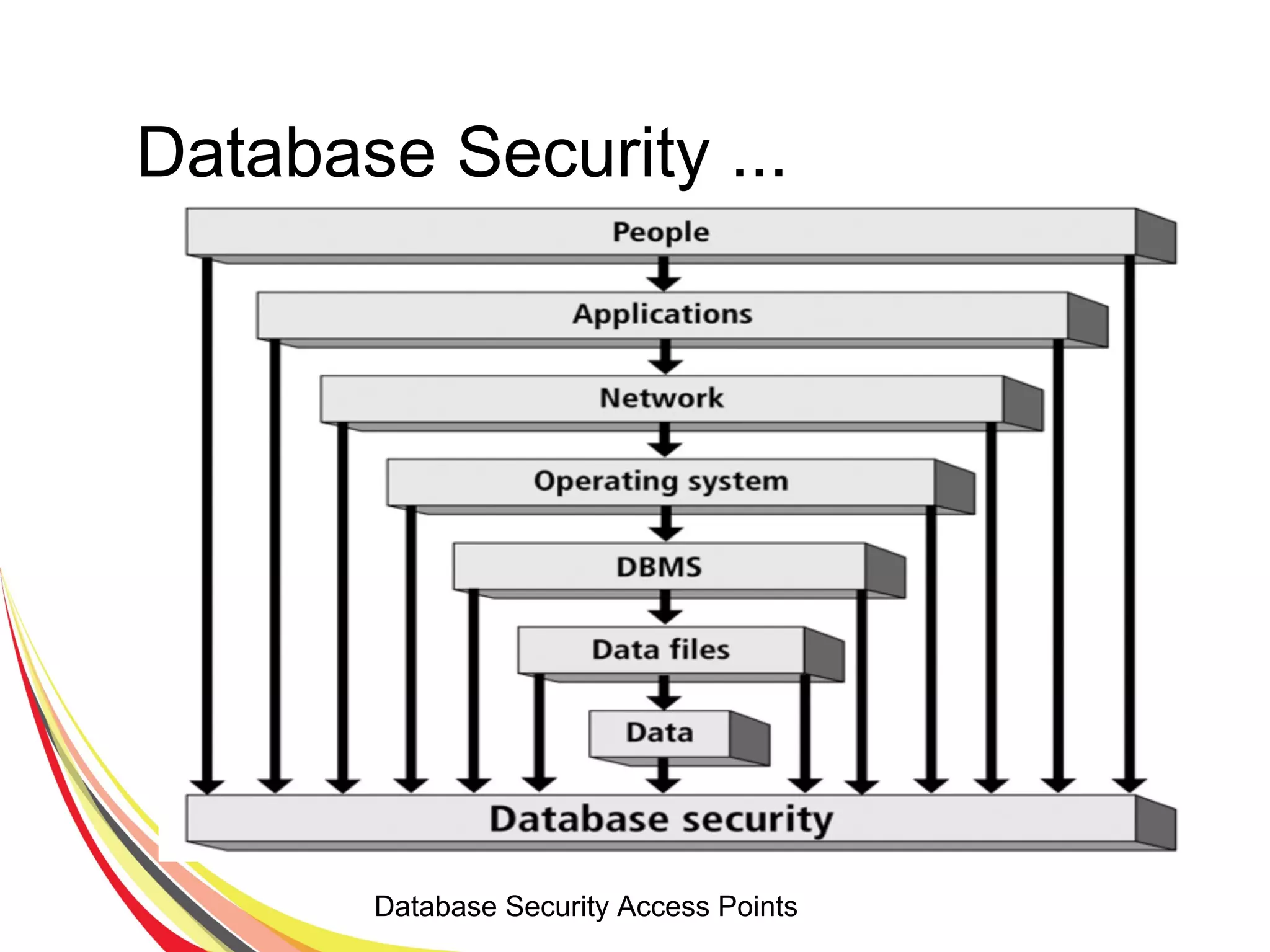
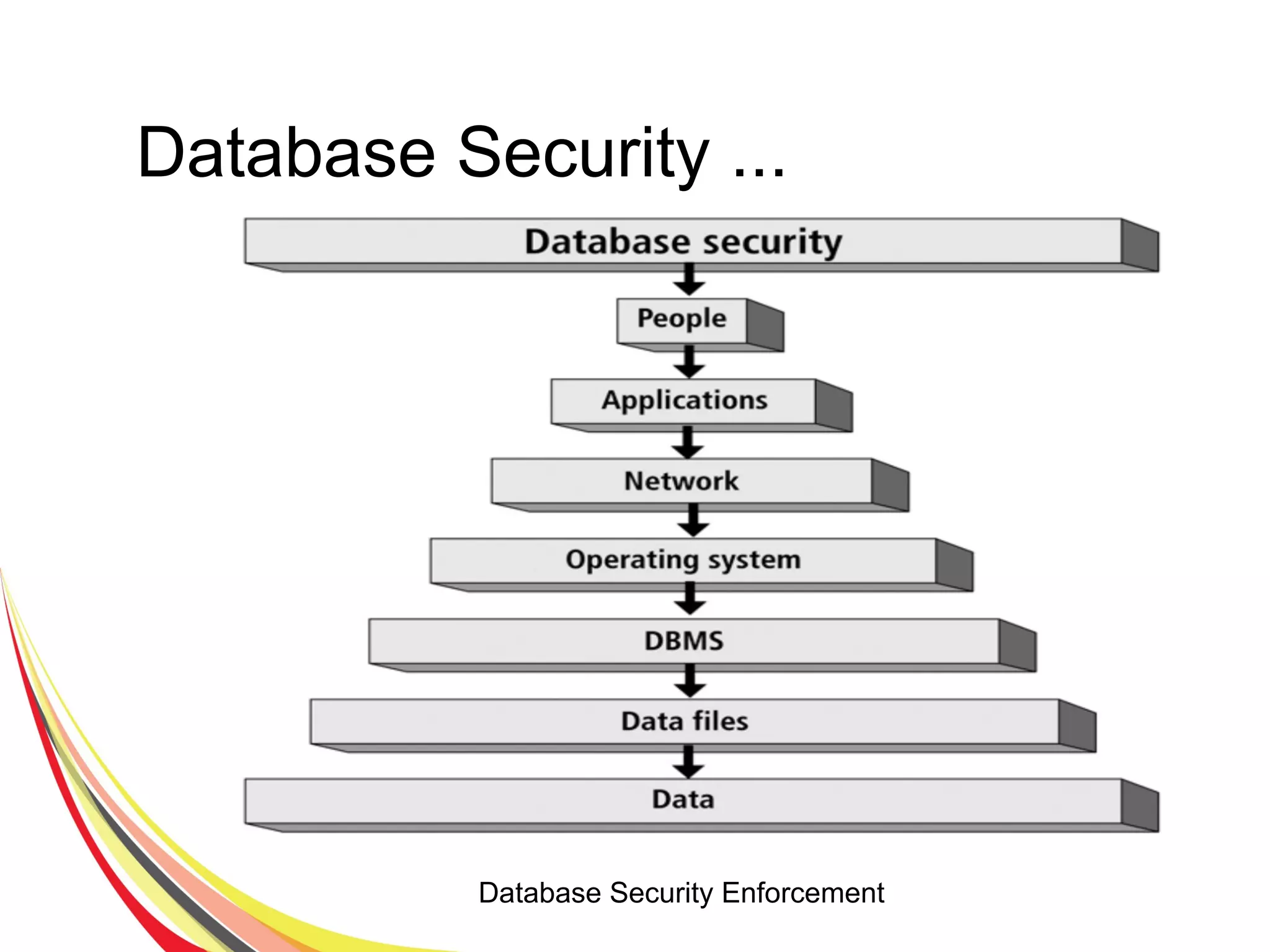
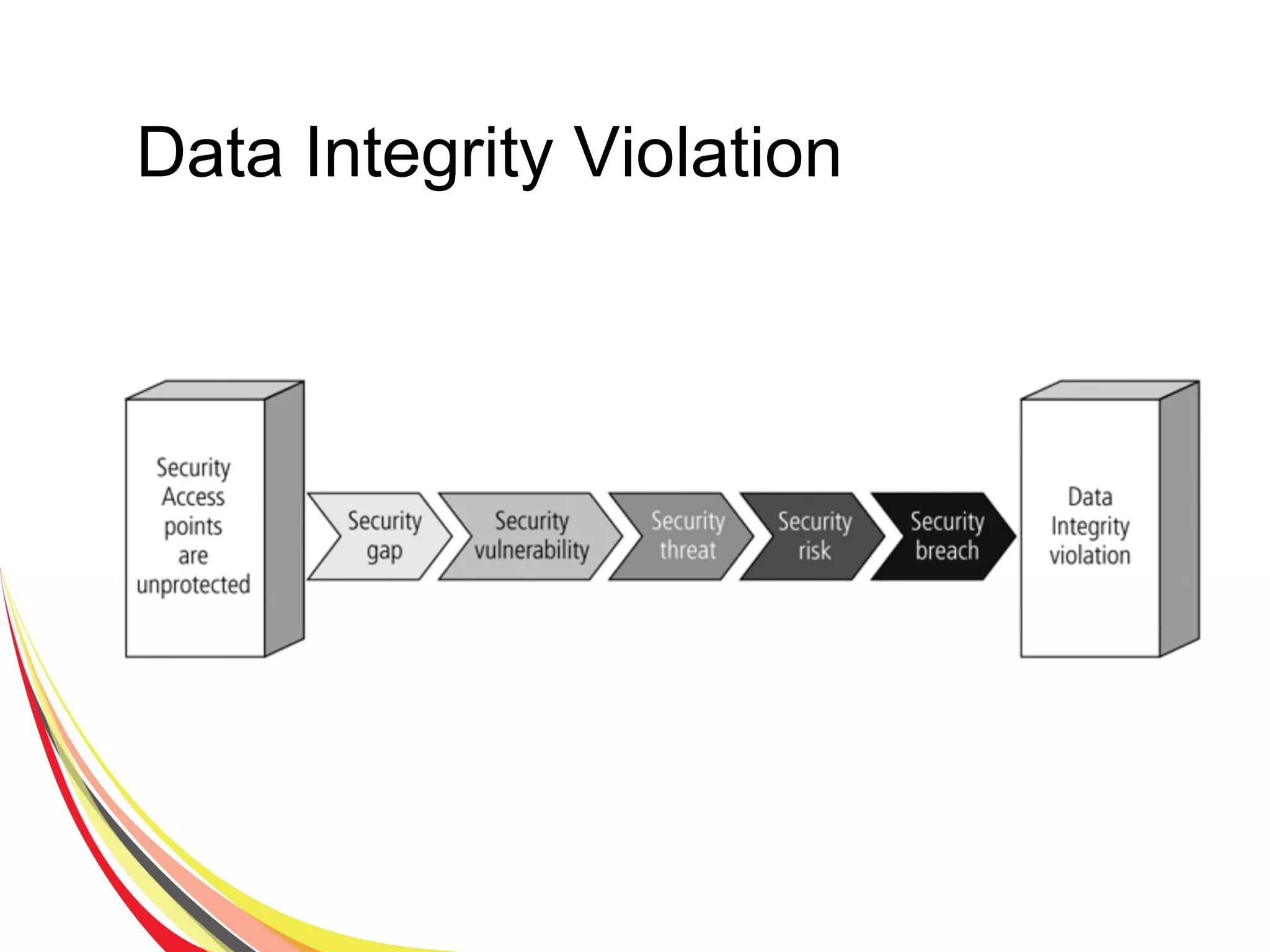
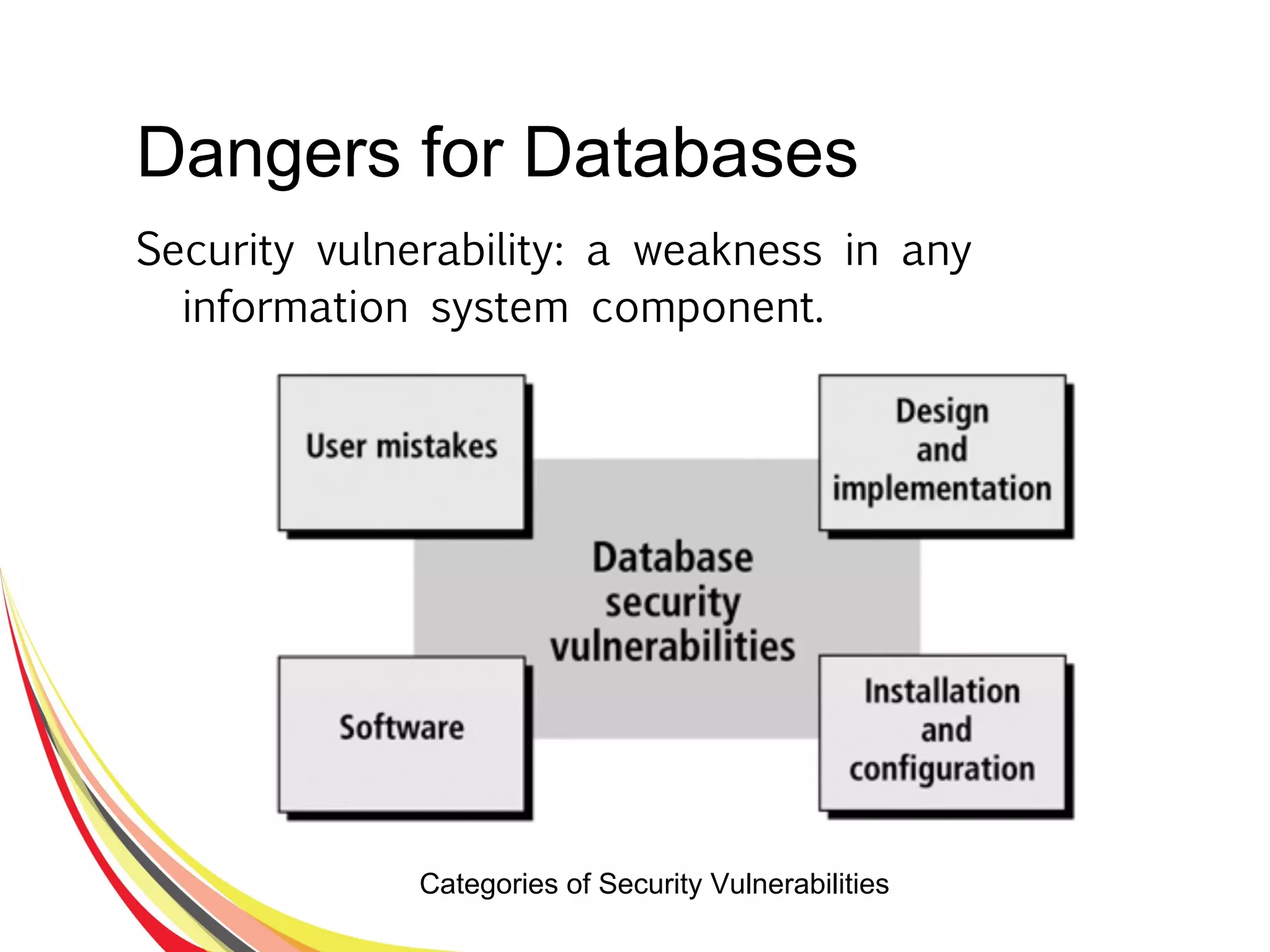
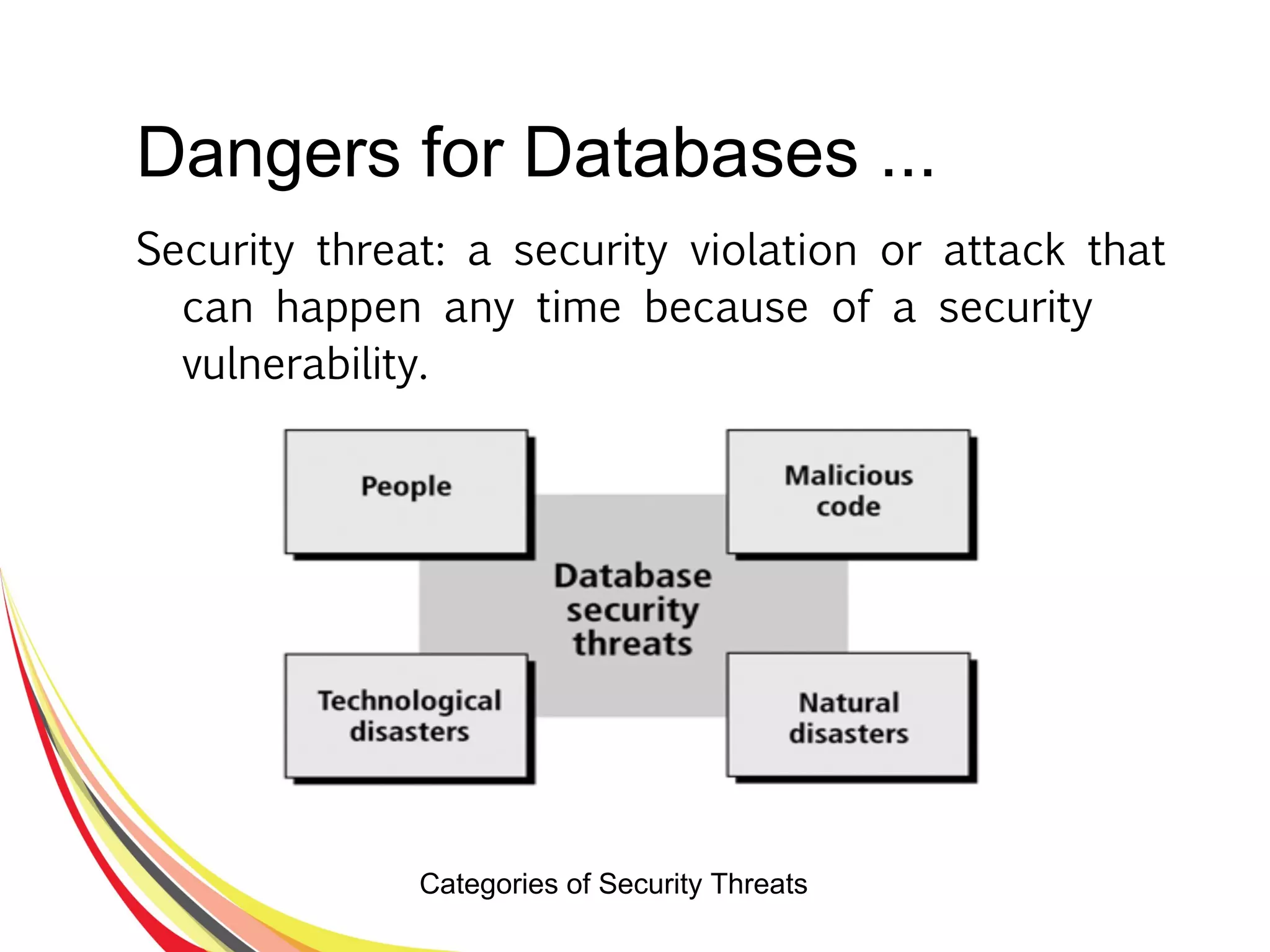
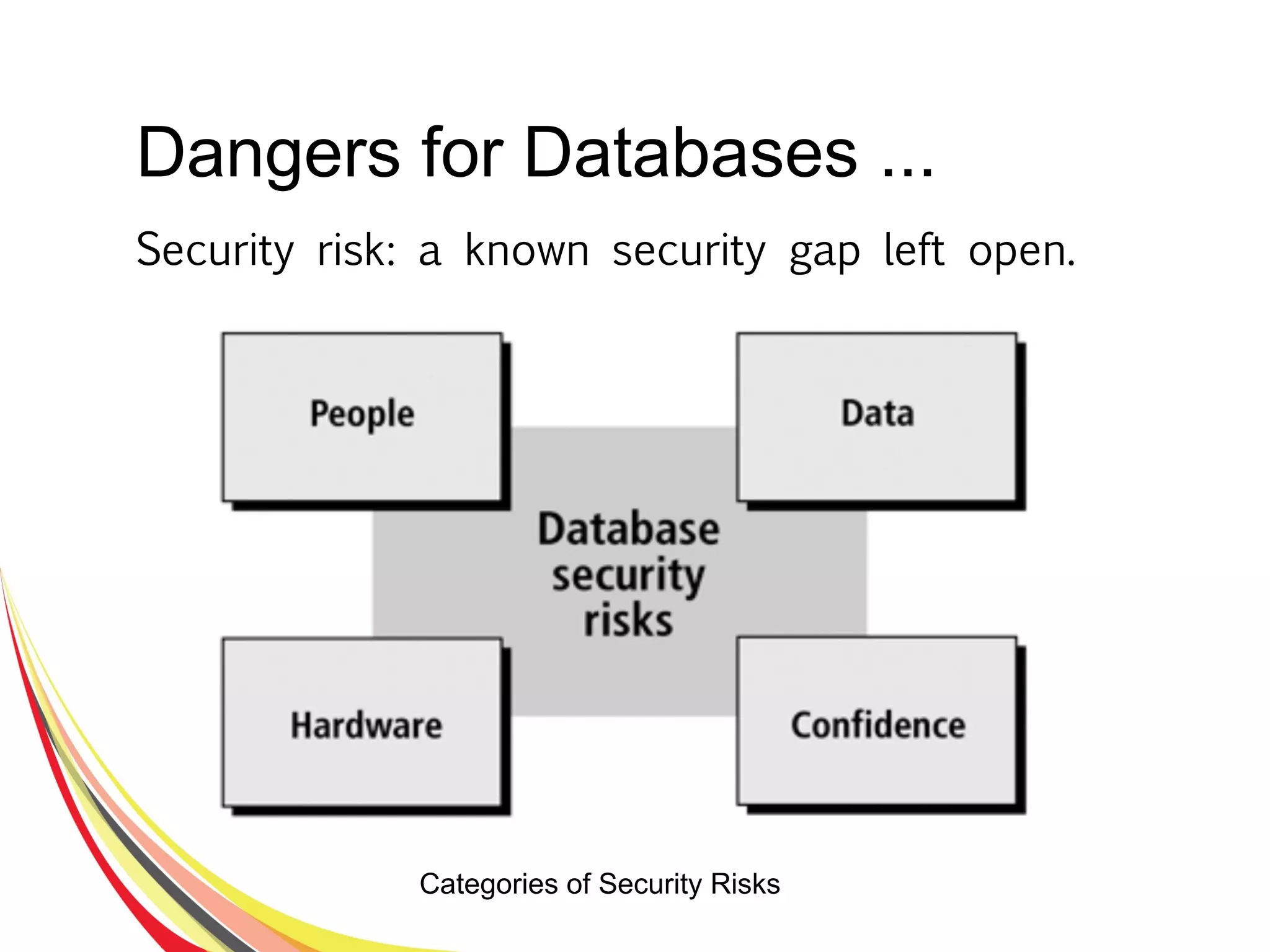
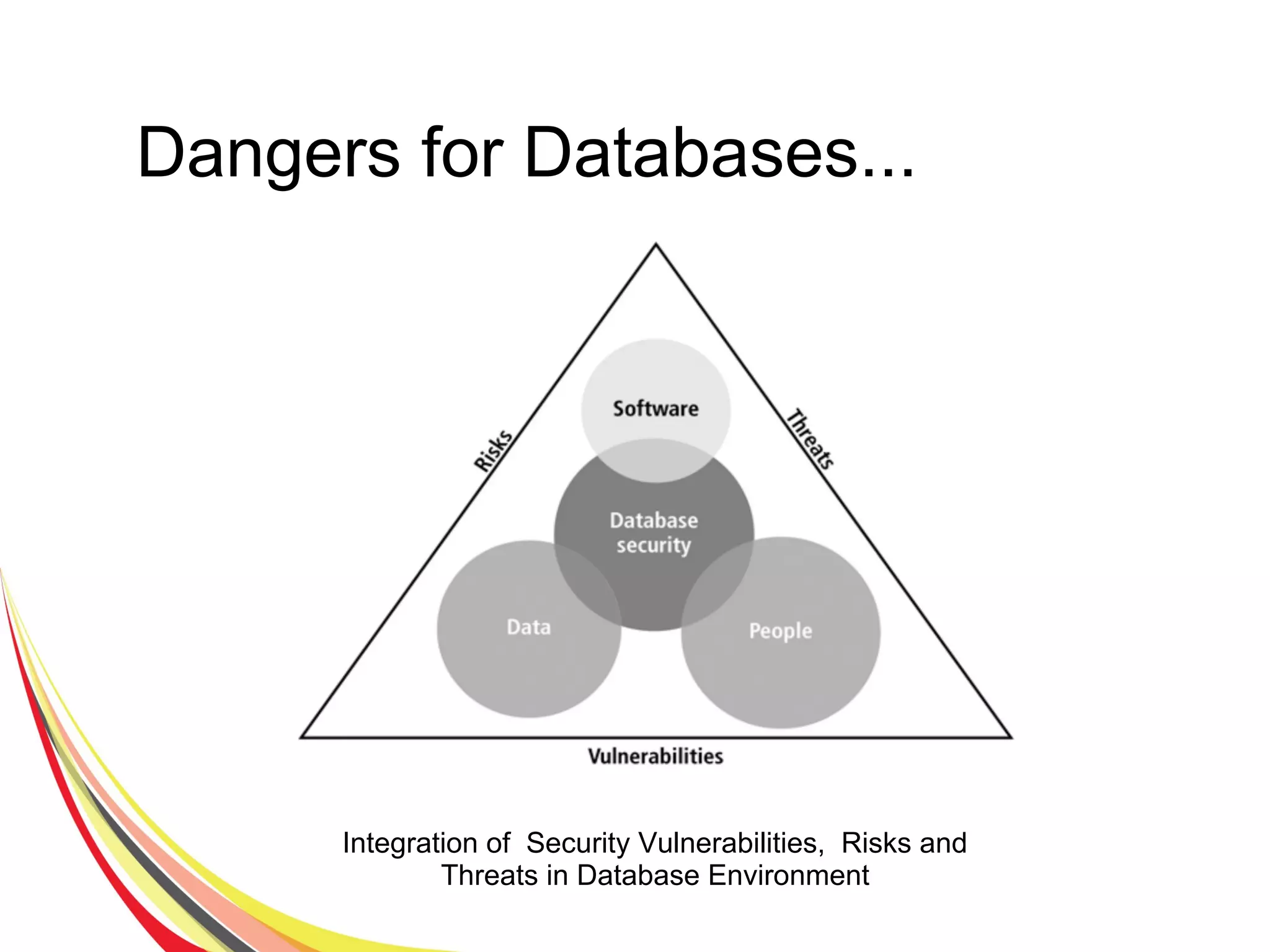
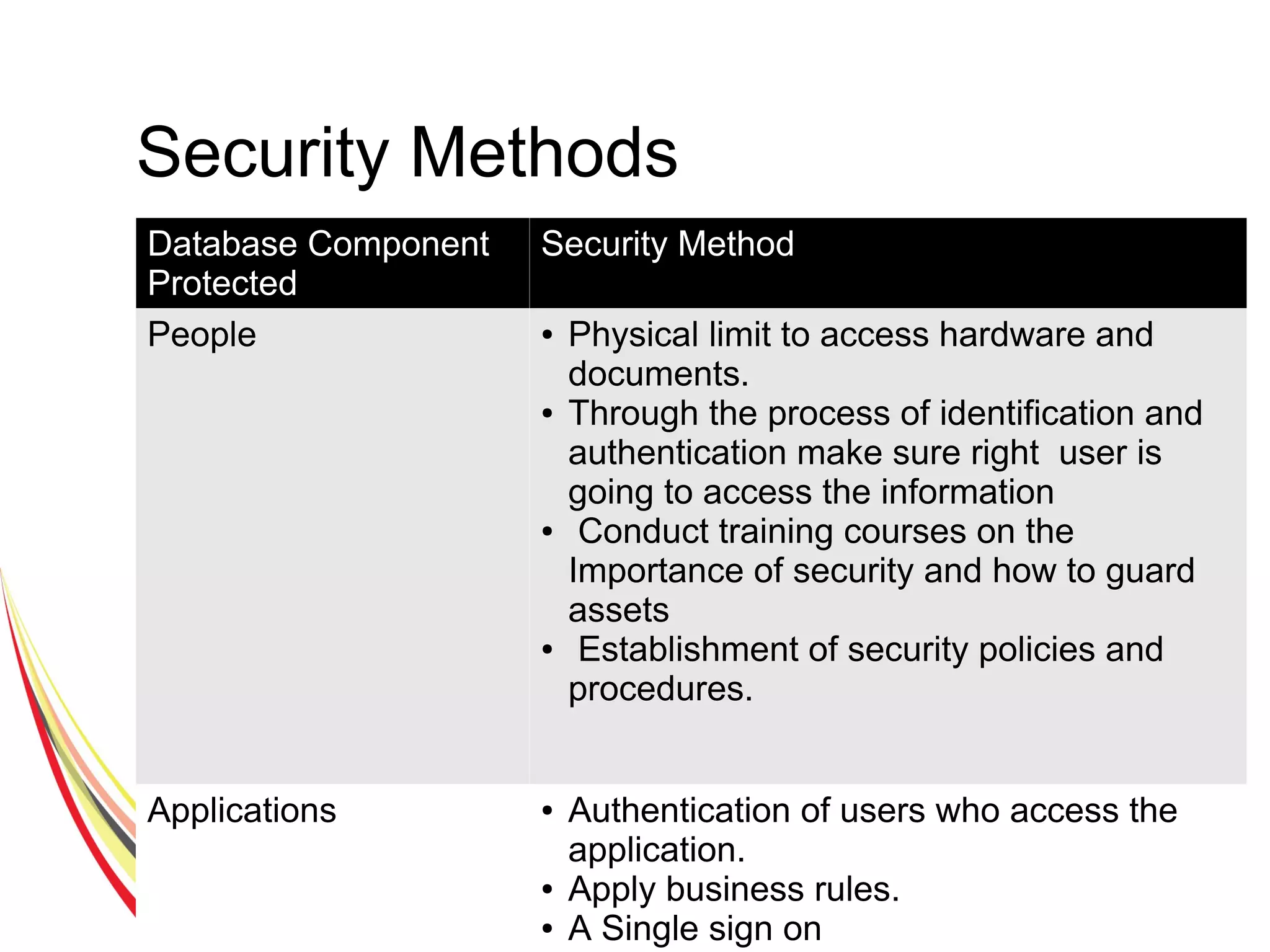
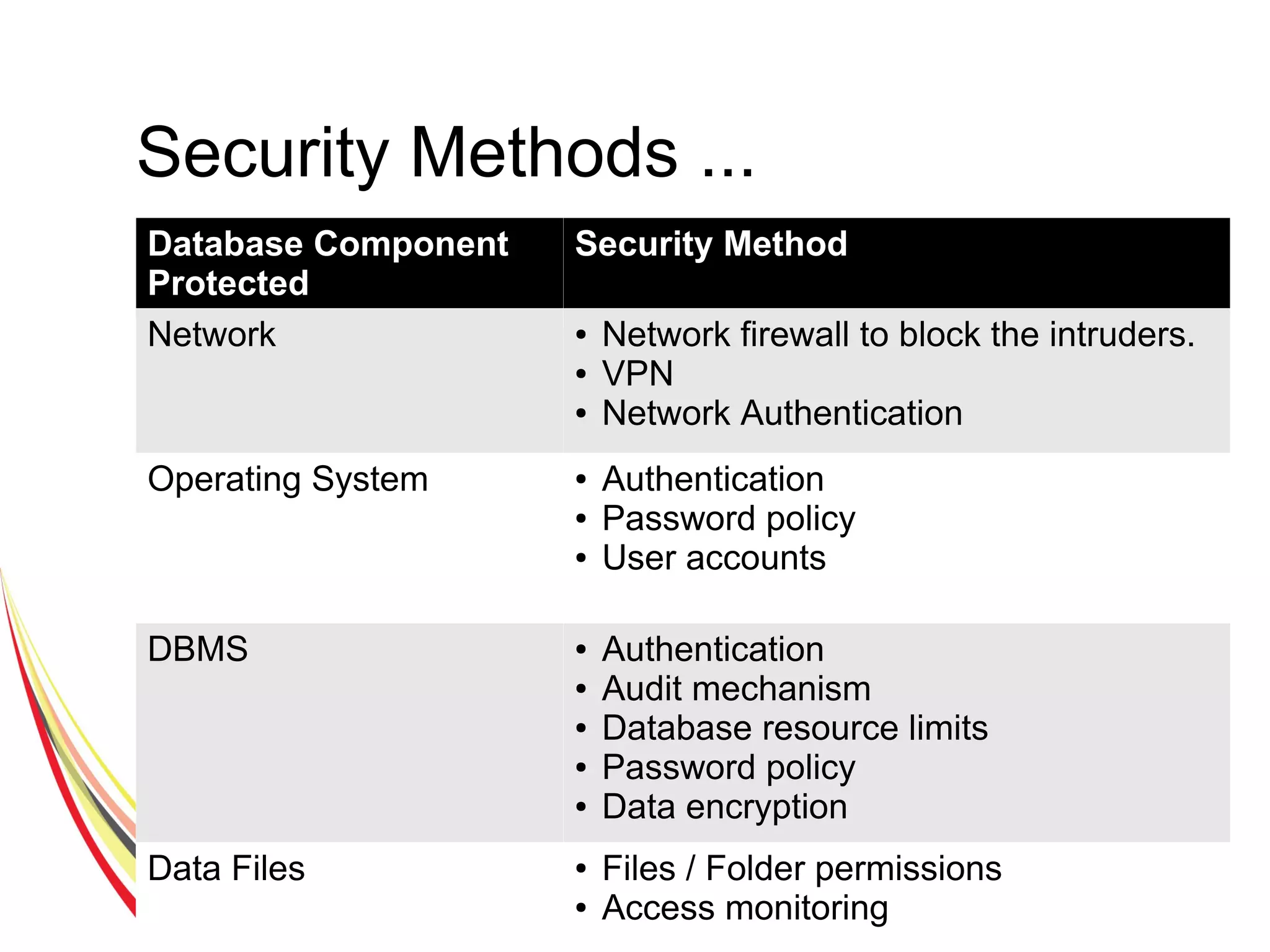
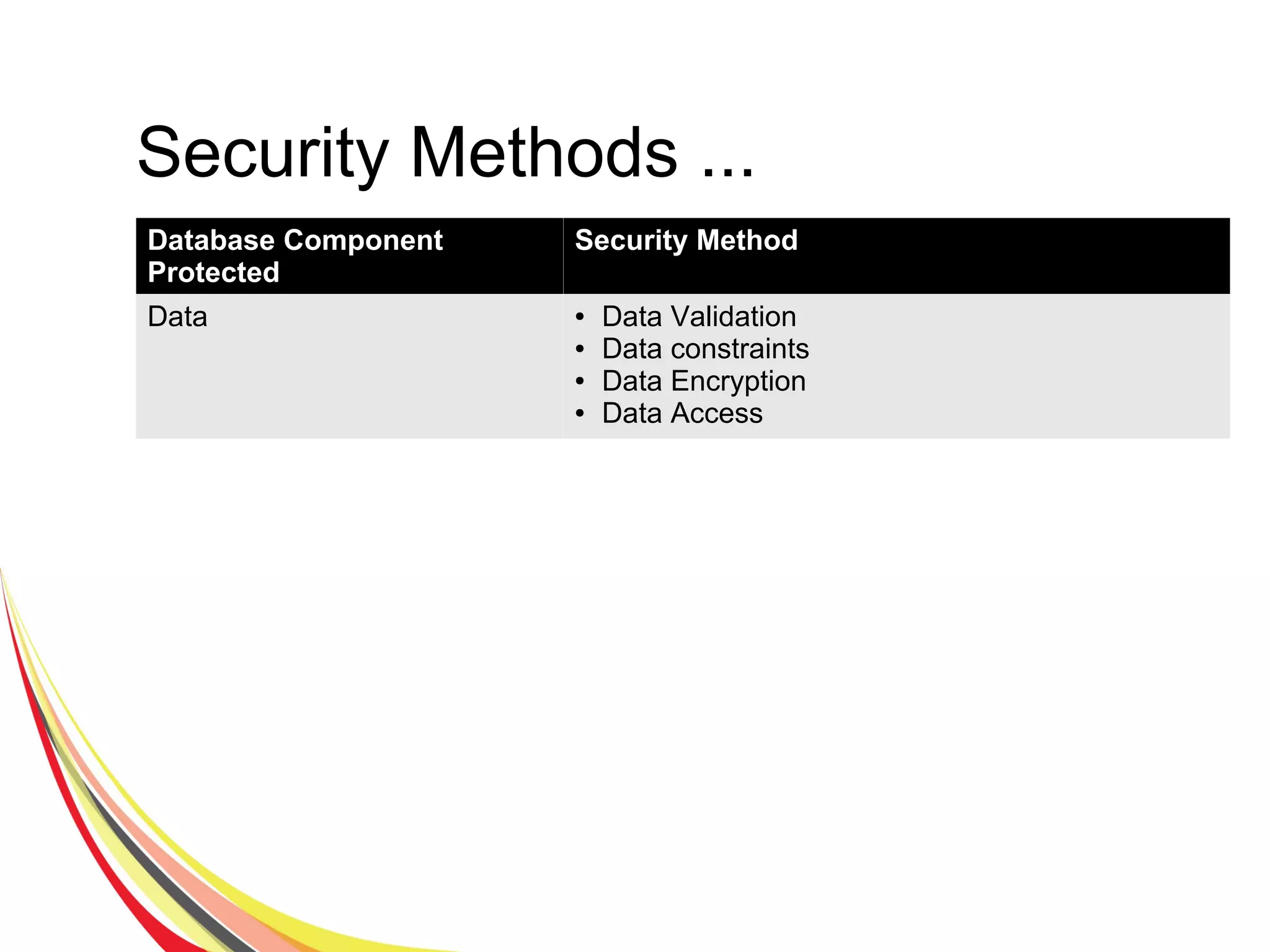
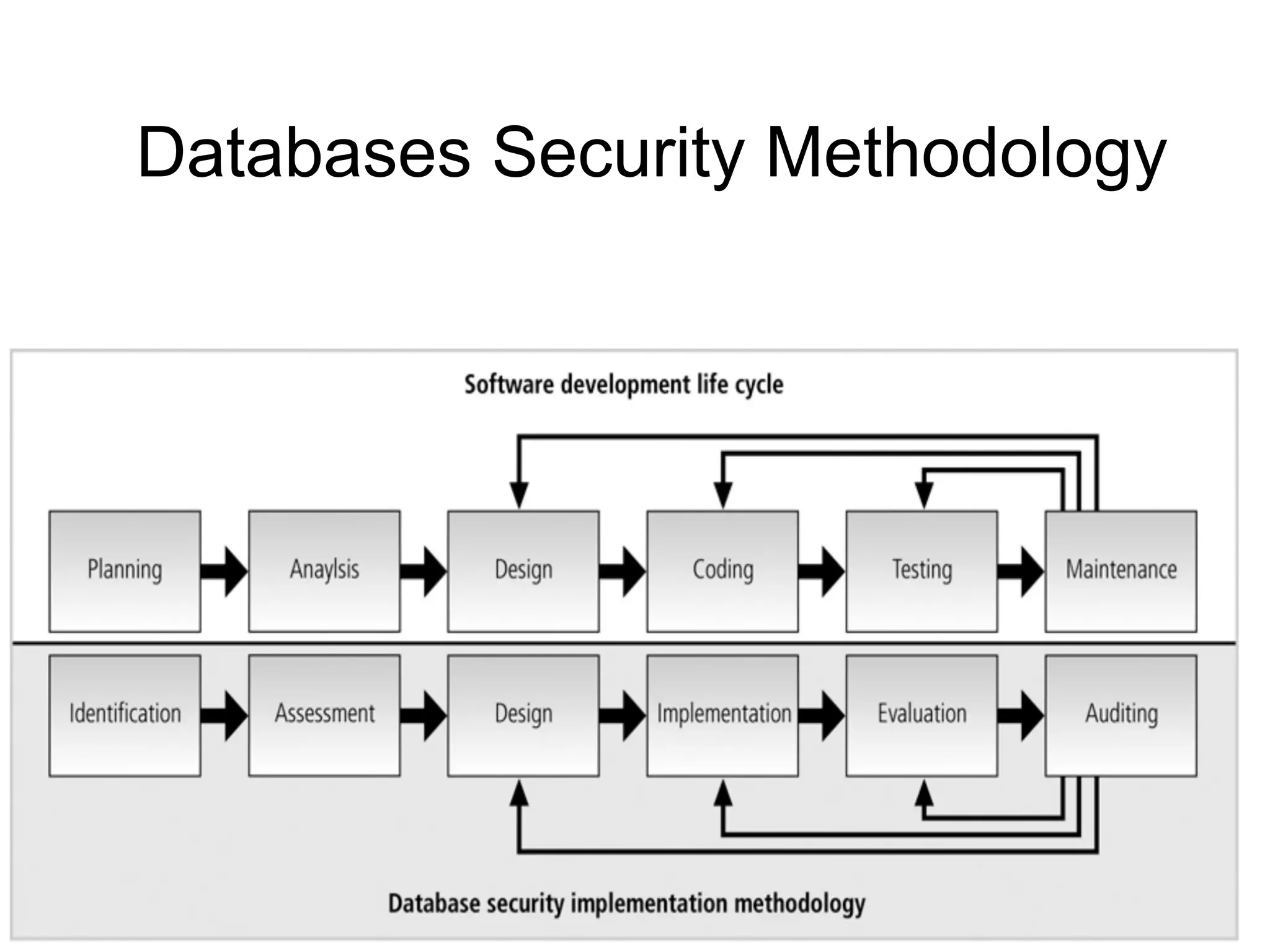
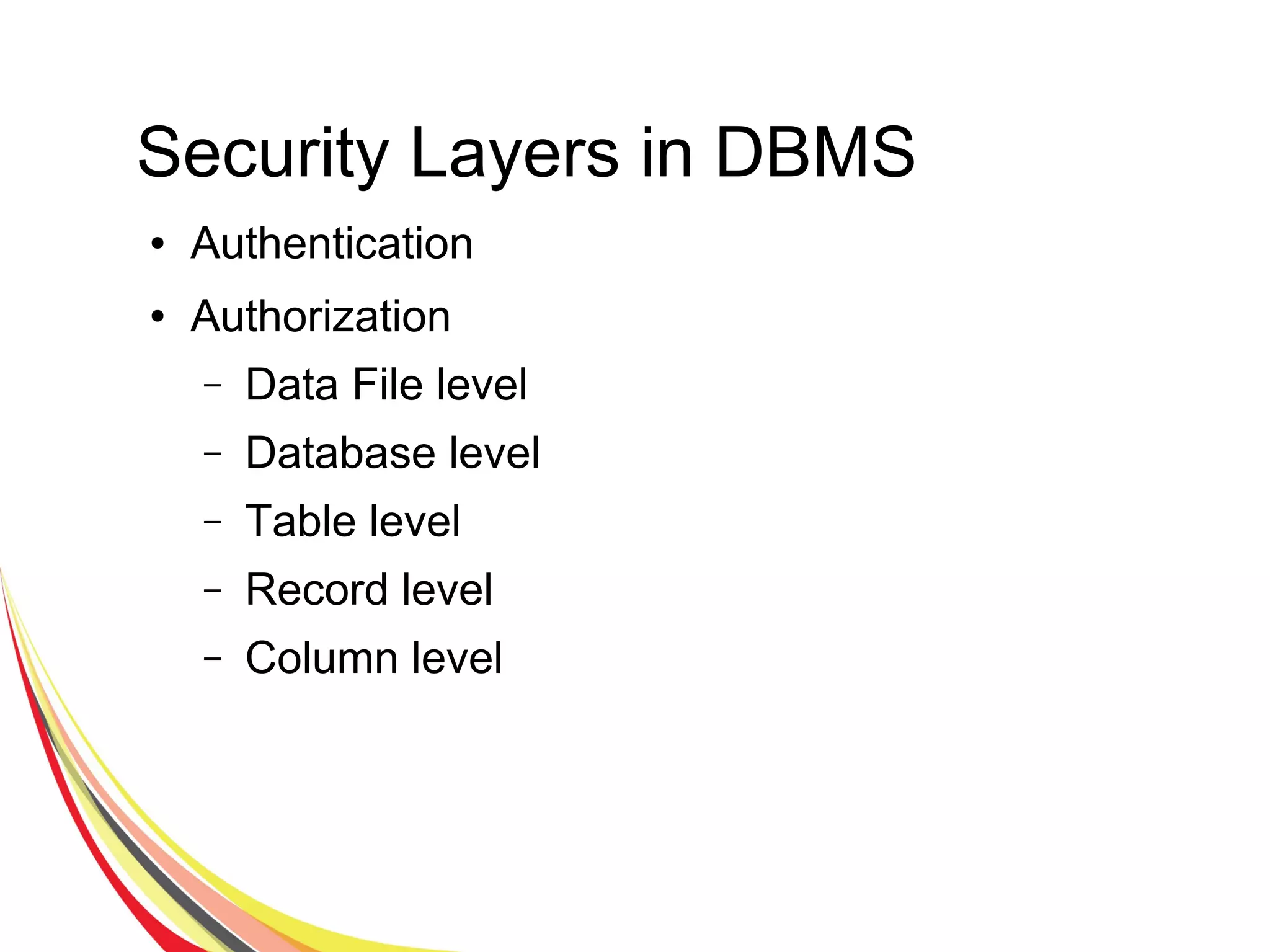
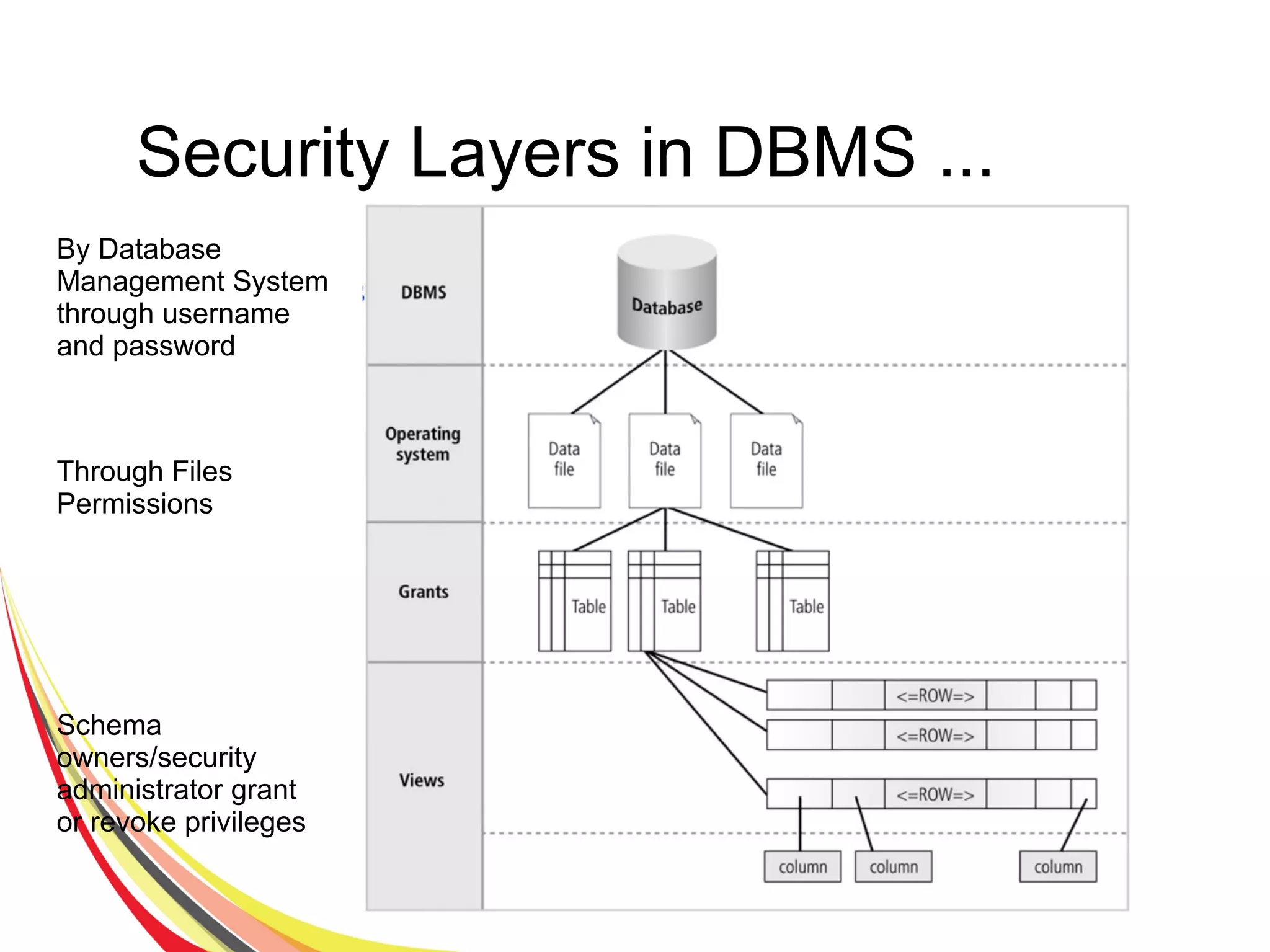
The document discusses various aspects of database security, including the necessity of safeguarding data integrity and confidentiality through established security policies and methodologies. It outlines the components and functions of information systems, the importance of access control, and various security layers within database management systems (DBMS). Additionally, it addresses security vulnerabilities, threats, and risks, alongside methods such as authentication and user authorization to ensure data protection.
















![DCL and Authorization
● GRANT Syntax
GRANT privilege_name ON object_name
TO {user_name | PUBLIC | role_name}
[with GRANT option];
● Here, privilege_name: is the access right or privilege
granted to the user.
● object_name: is the name of the database object like
table, view etc.,.
● user_name: is the name of the user to whom an access
right is being granted.
● Public is used to grant rights to all the users.
● With Grant option: allows users to grant access rights to
other users.](https://image.slidesharecdn.com/datasecurityandintigrity-160726045051/75/Data-security-and-Integrity-39-2048.jpg)