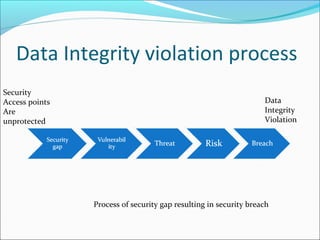
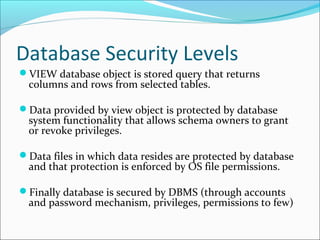
This document discusses database security. It introduces the CIA triangle of confidentiality, integrity and availability as key security objectives. It describes various security access points like people, applications, networks and operating systems. It also discusses vulnerabilities, threats, risks and different security methods to protect databases. The document provides an overview of concepts important for implementing database security.