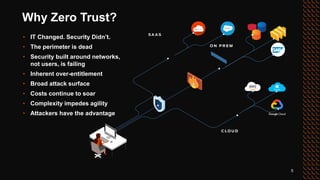
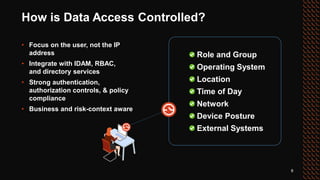
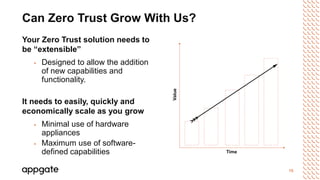
The document outlines the Zero Trust security model, emphasizing its necessity in modern hybrid and multi-cloud environments, moving away from outdated perimeter security principles. It describes how Zero Trust enhances security by eliminating 'default trust' and focuses on user-centric access control, supporting various devices and operating systems. Additionally, it highlights the model's adaptability, cost-effectiveness, and the need for organization-wide understanding and implementation.