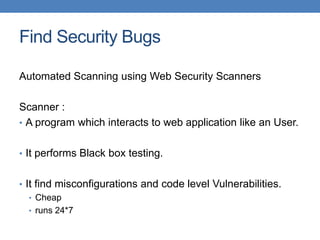
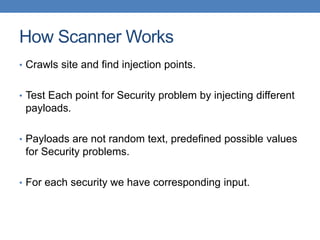
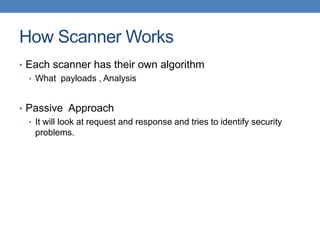
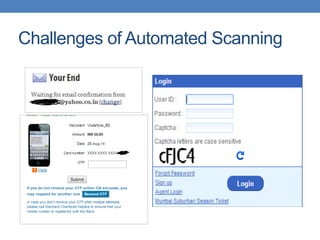
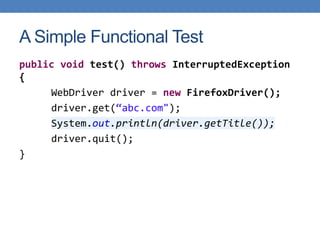
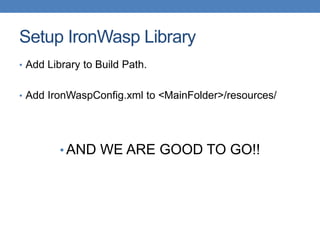
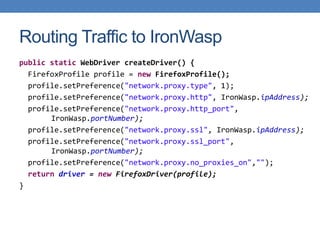
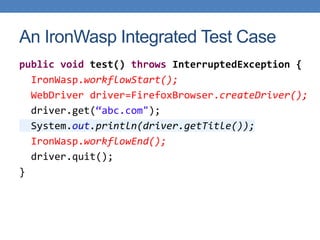
This document discusses using functional test automation with the open source web application security scanner IronWasp to provide automated security testing of web applications. It outlines how Selenium test cases can be integrated with IronWasp to allow the scanner to crawl and test the full application workflow, providing security checks across all functional flows. This improves on traditional scanners by allowing testing of login screens, multi-page sequences, and ensuring the scanner has valid inputs to exercise all application features.