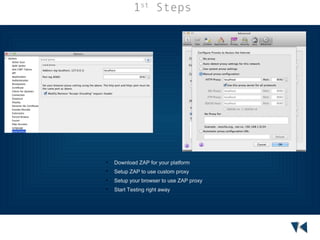
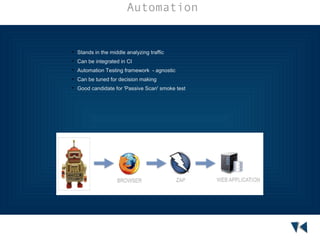
Security testing is a process to determine if an information system protects data and functions as intended, and involves challenges like requiring specialized skills, ongoing effort, tools, budgets, and automation. The Zed Attack Proxy (ZAP) is an easy-to-use tool for finding vulnerabilities in web applications that can be used by developers, testers, and security specialists of all experience levels through both automated and manual scanning. ZAP provides passive and active scanning, reports, integration with CI/CD pipelines, and is open source.