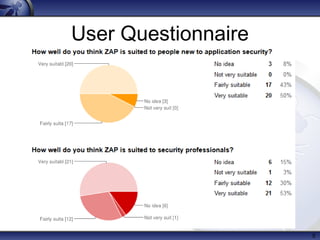
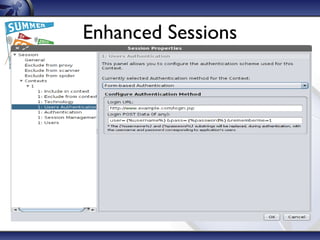
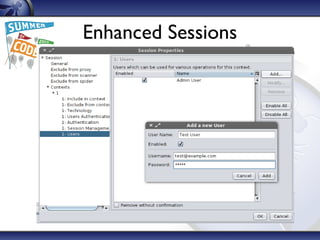
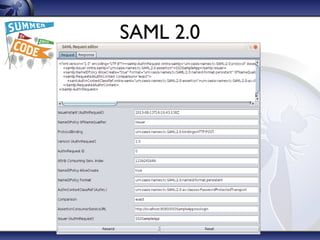
The document details the OWASP Zed Attack Proxy (ZAP), a free and open-source web application penetration testing tool ideal for both beginners and professionals. It outlines ZAP's principles, main features, and recent innovations, such as enhanced session handling and advanced reporting capabilities. The document encourages community involvement and feedback to further improve the tool.