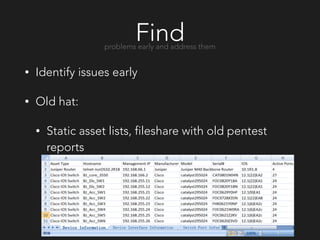
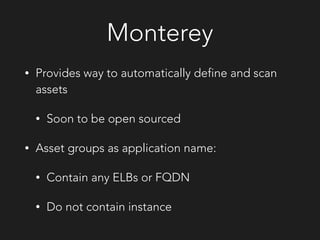
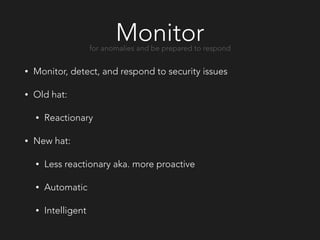
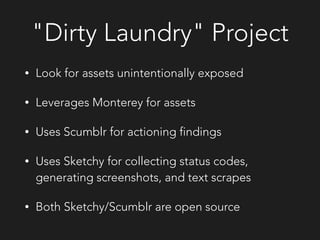
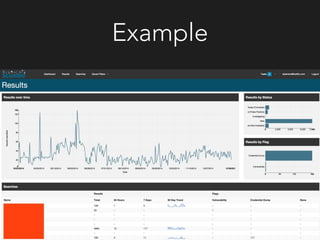
The document discusses Netflix's approach to proactive security. It outlines the challenges of securing a modern infrastructure with hundreds of applications and instances deploying code continuously. Netflix's solution is to implement proactive security controls that are integrated, automated, scalable and adaptive using tools like Monterey, Simian Army, Dirty Laundry, Security Monkey and Speedbump. The approach focuses on finding problems early, knowing weaknesses, monitoring for anomalies, collecting meaningful data, simplifying security for developers, reevaluating approaches, and sharing learnings with others.