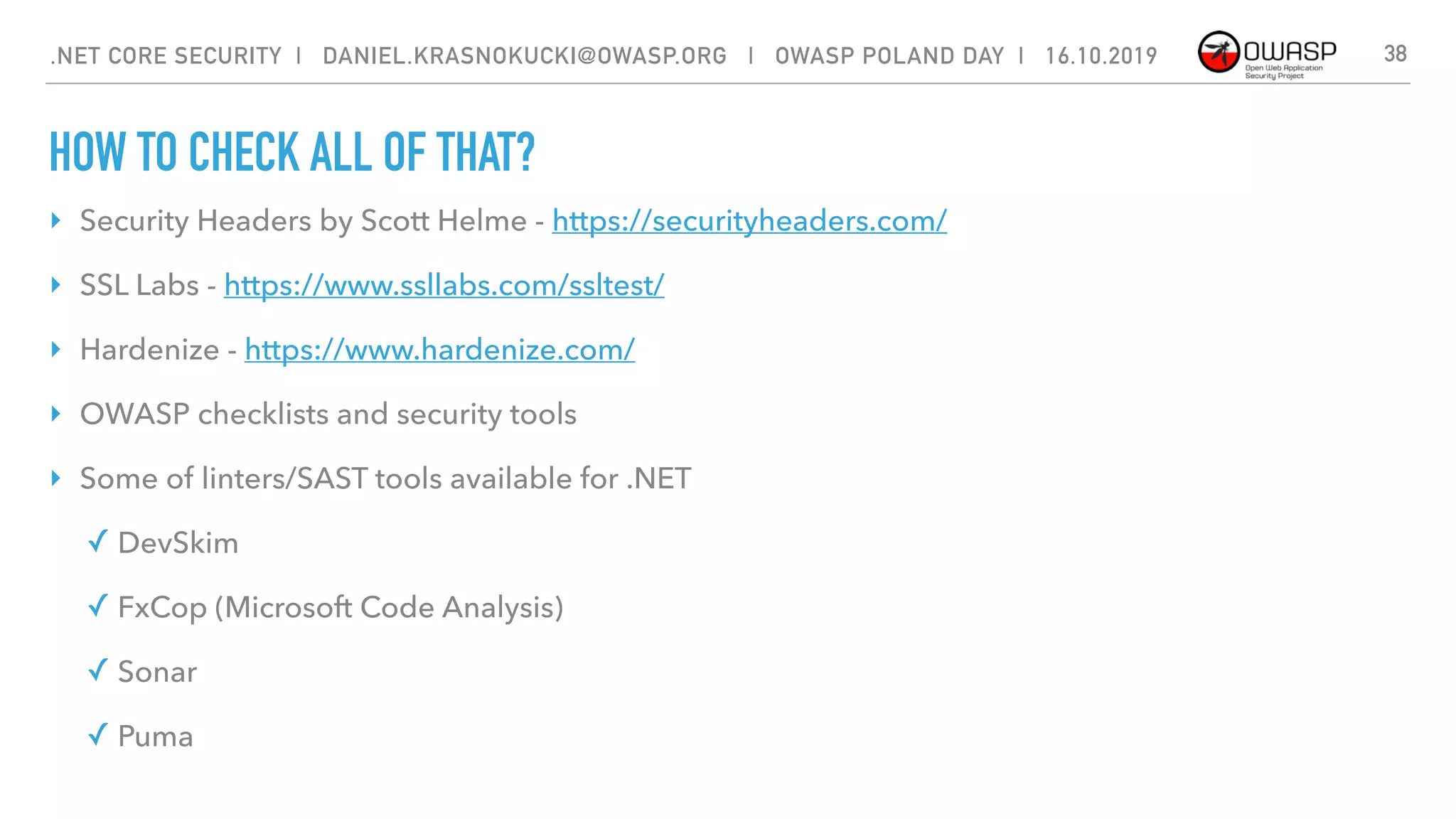
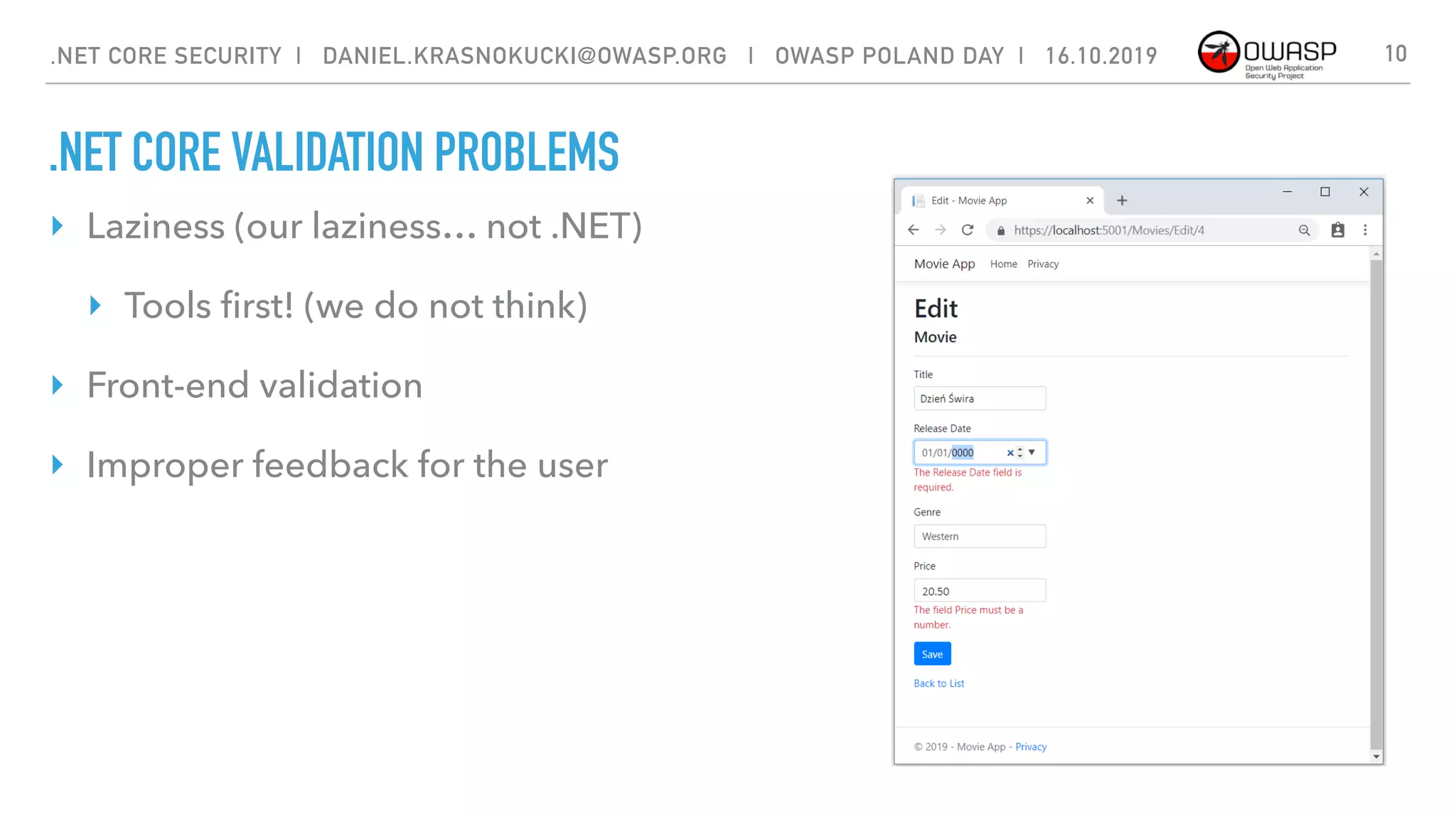
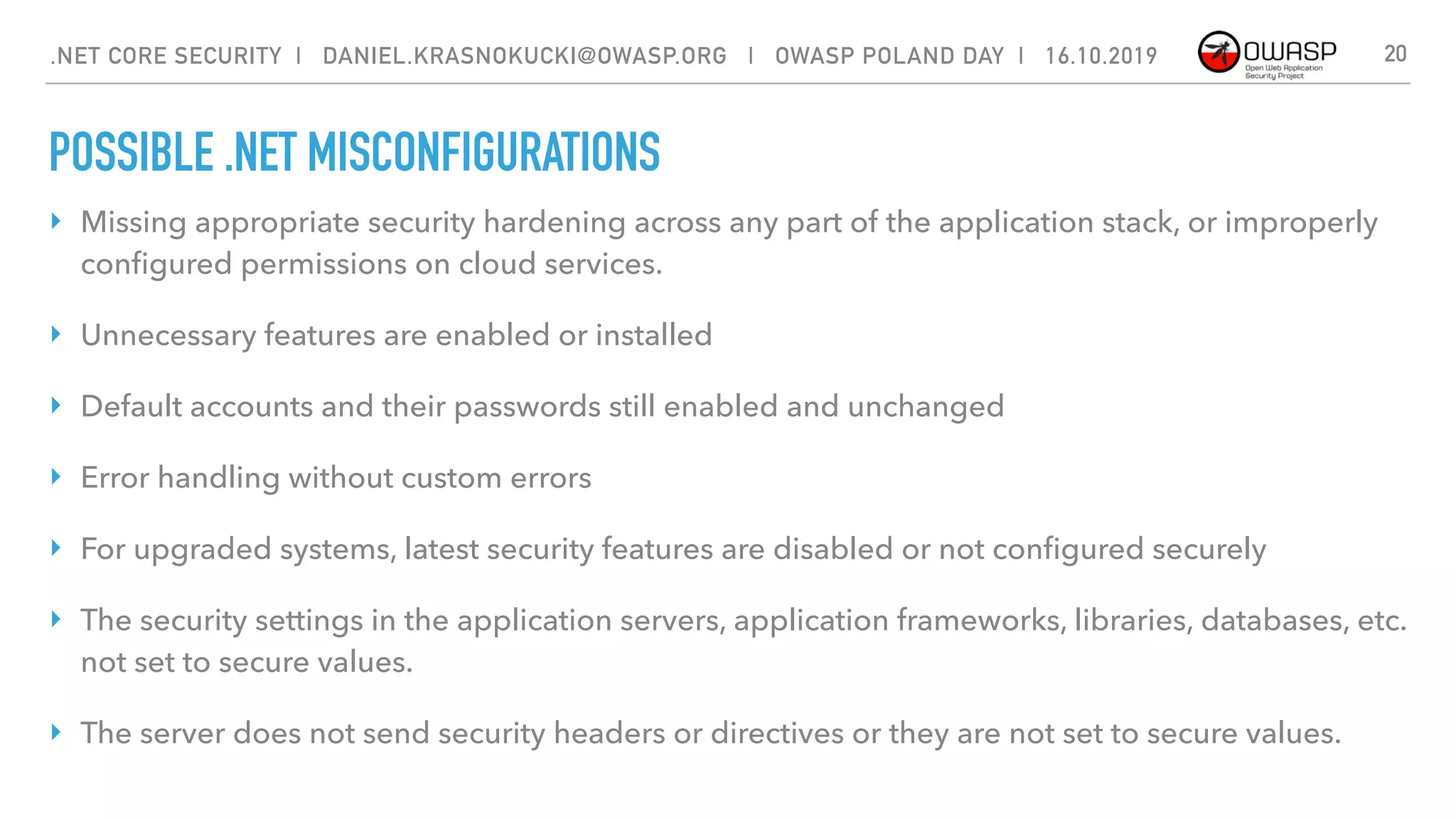
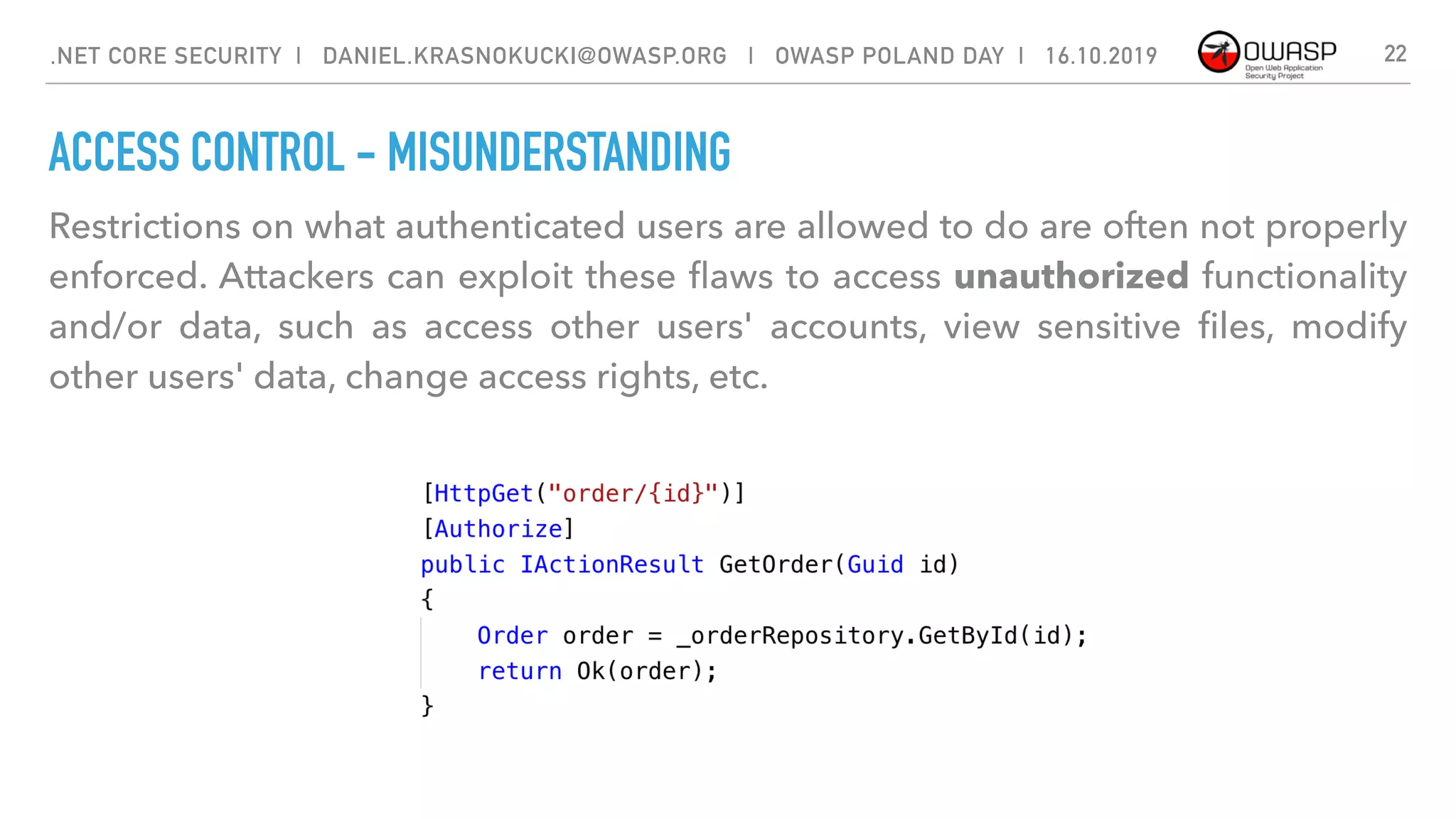
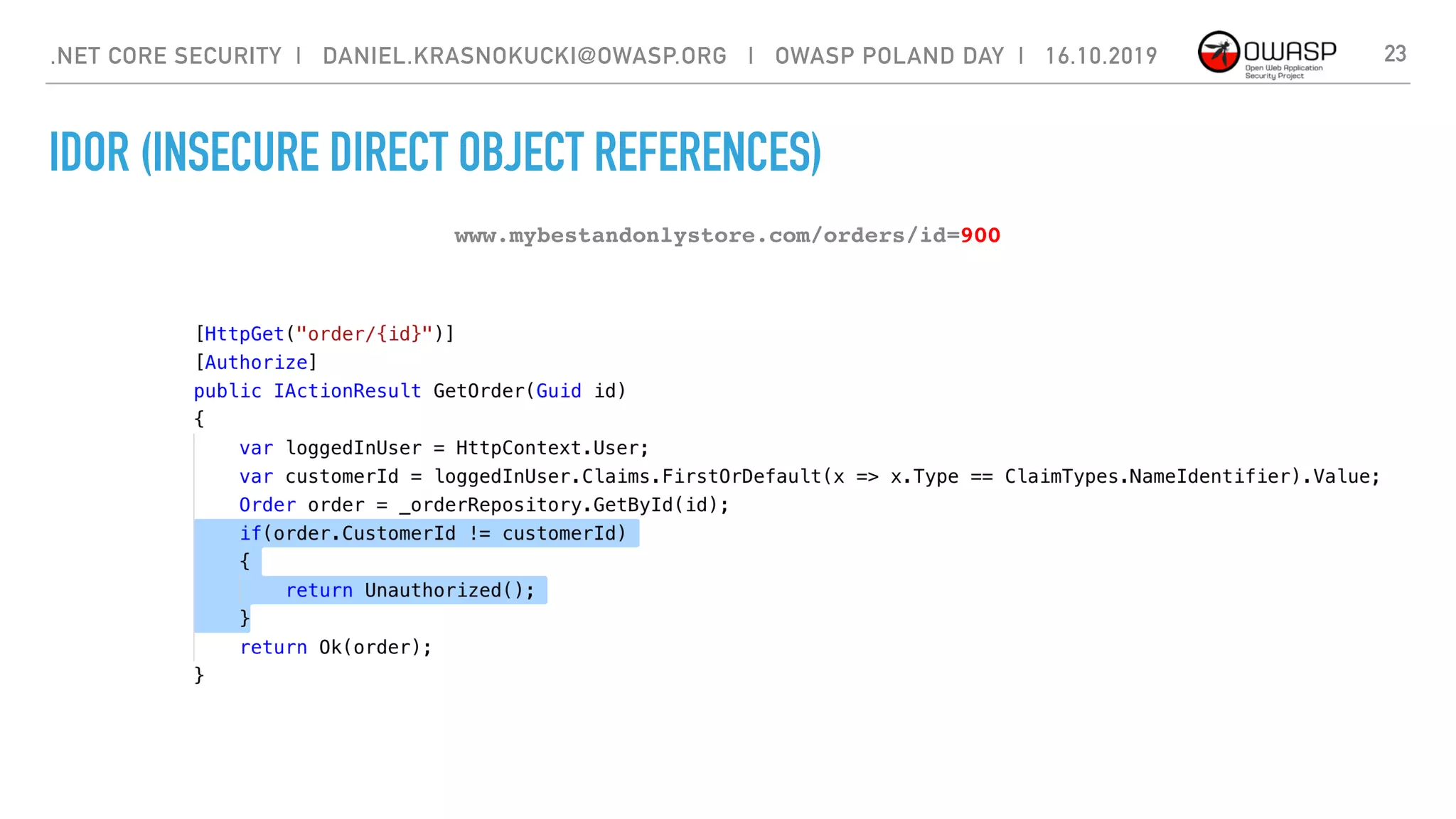
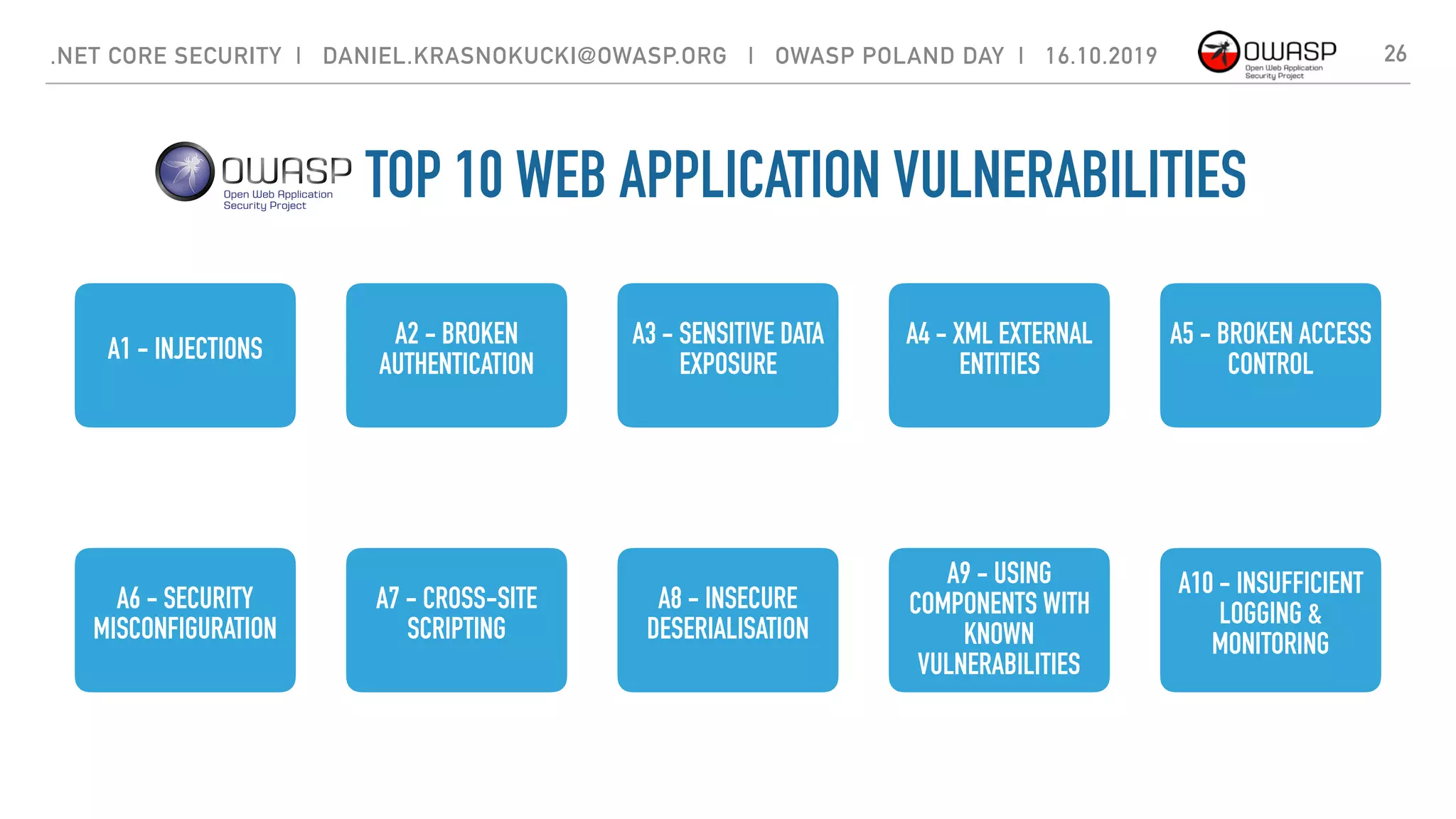
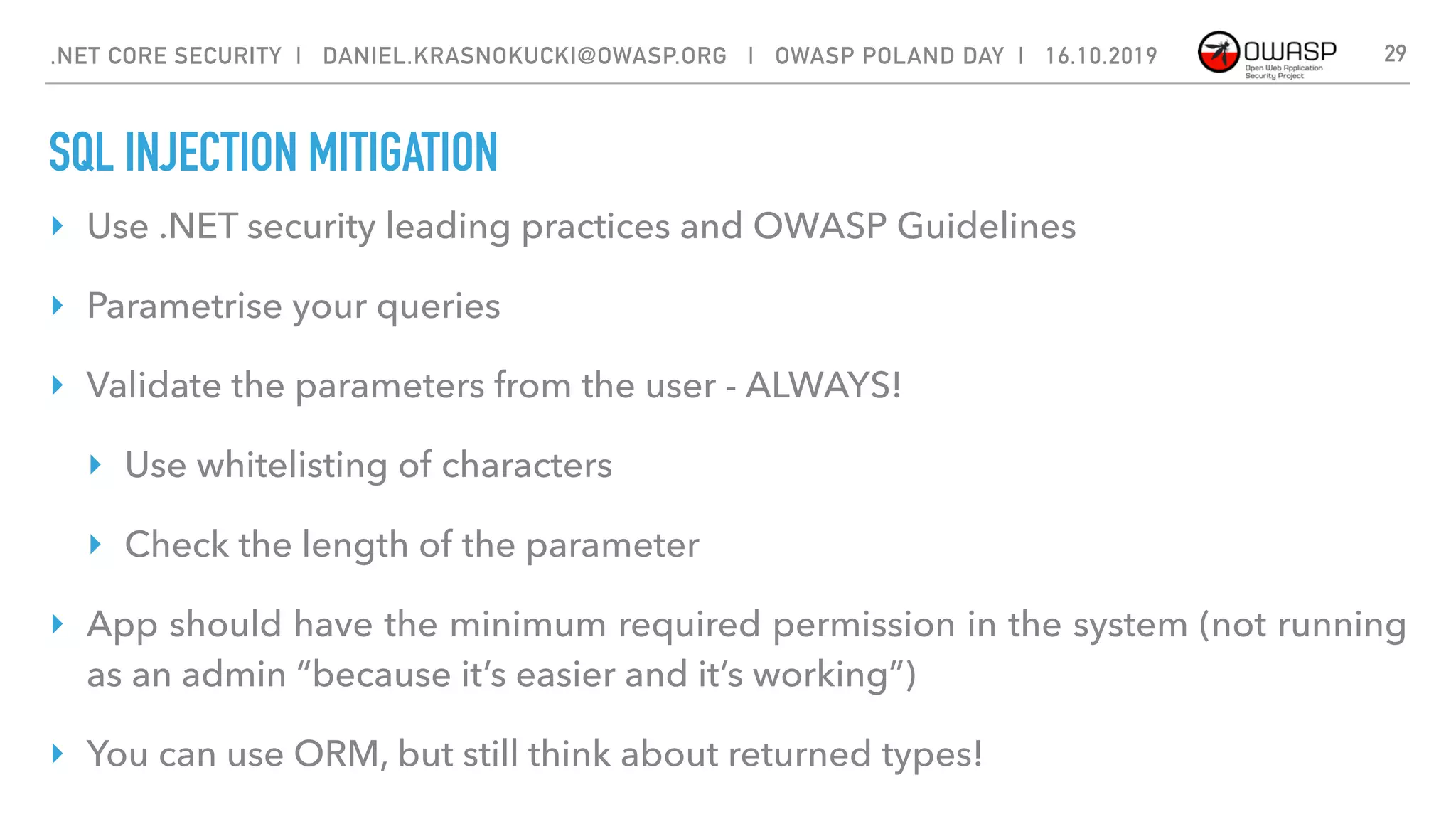
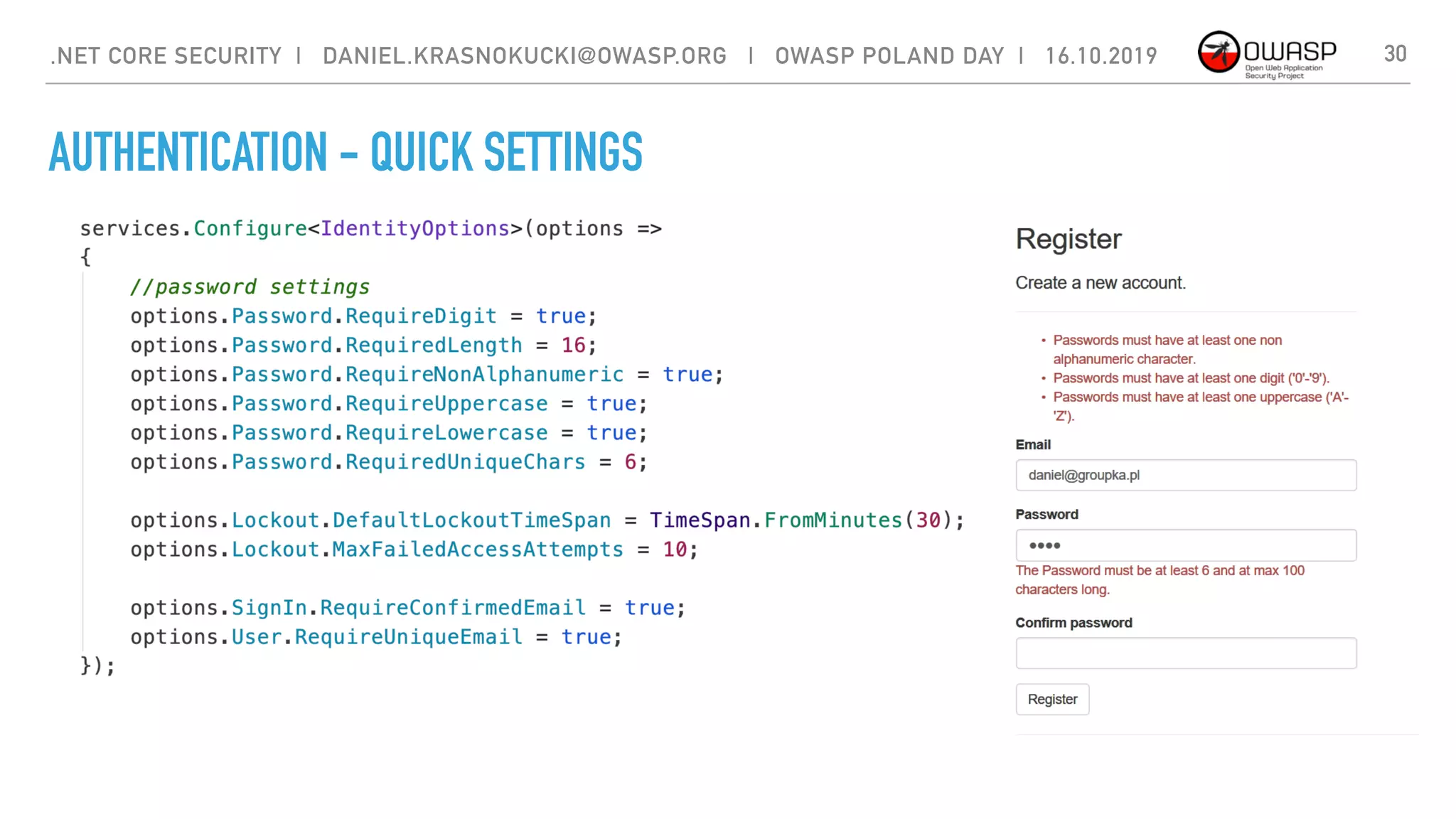
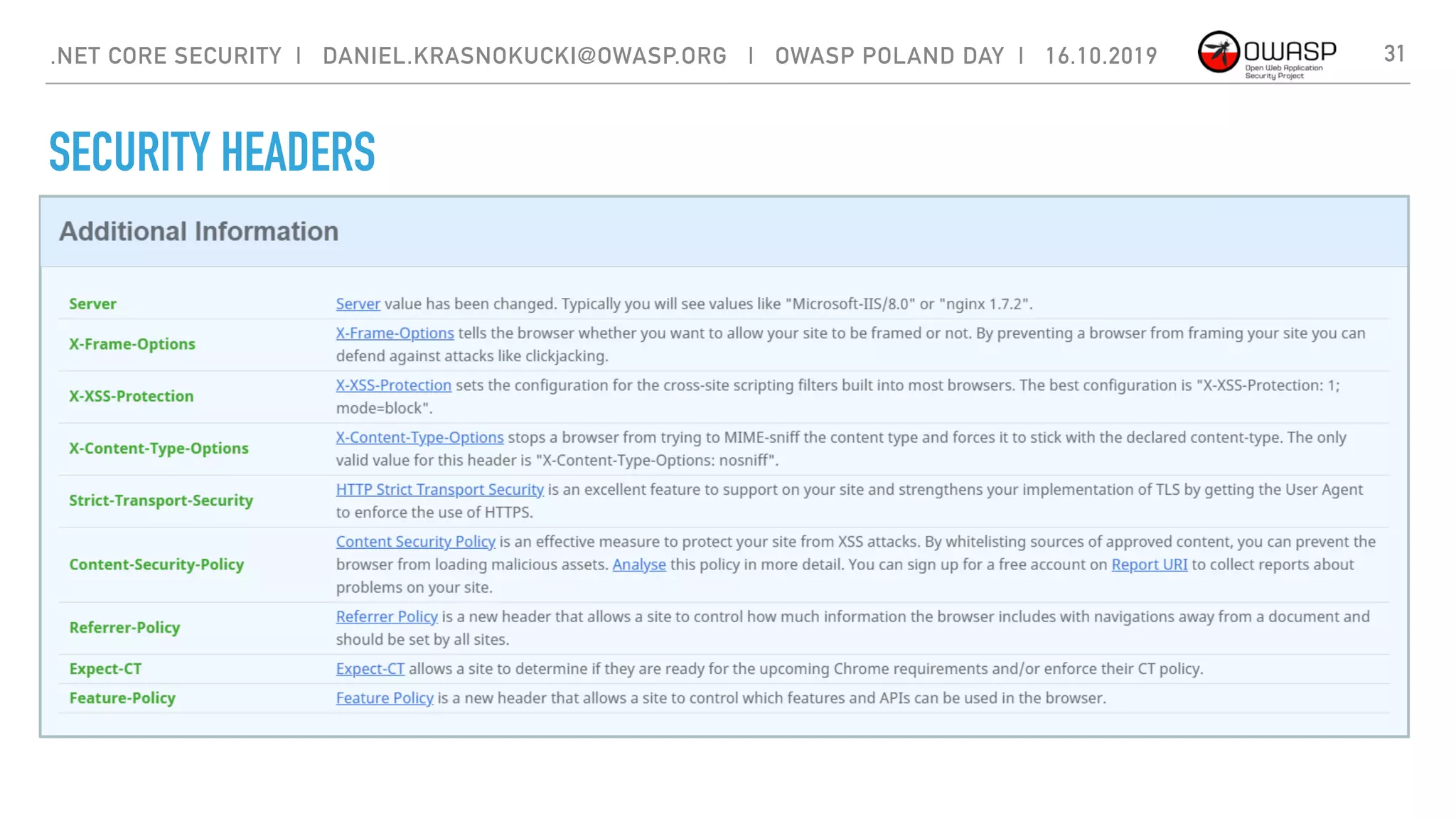
The document discusses security best practices for .NET Core applications. It covers topics like common mistakes made when using .NET Core like security misconfiguration, SQL injection, and insecure deserialization. It also outlines security risks with .NET Core like validation problems and information disclosure. Additionally, it recommends security practices like input validation, output encoding, using security headers, and avoiding direct object references.





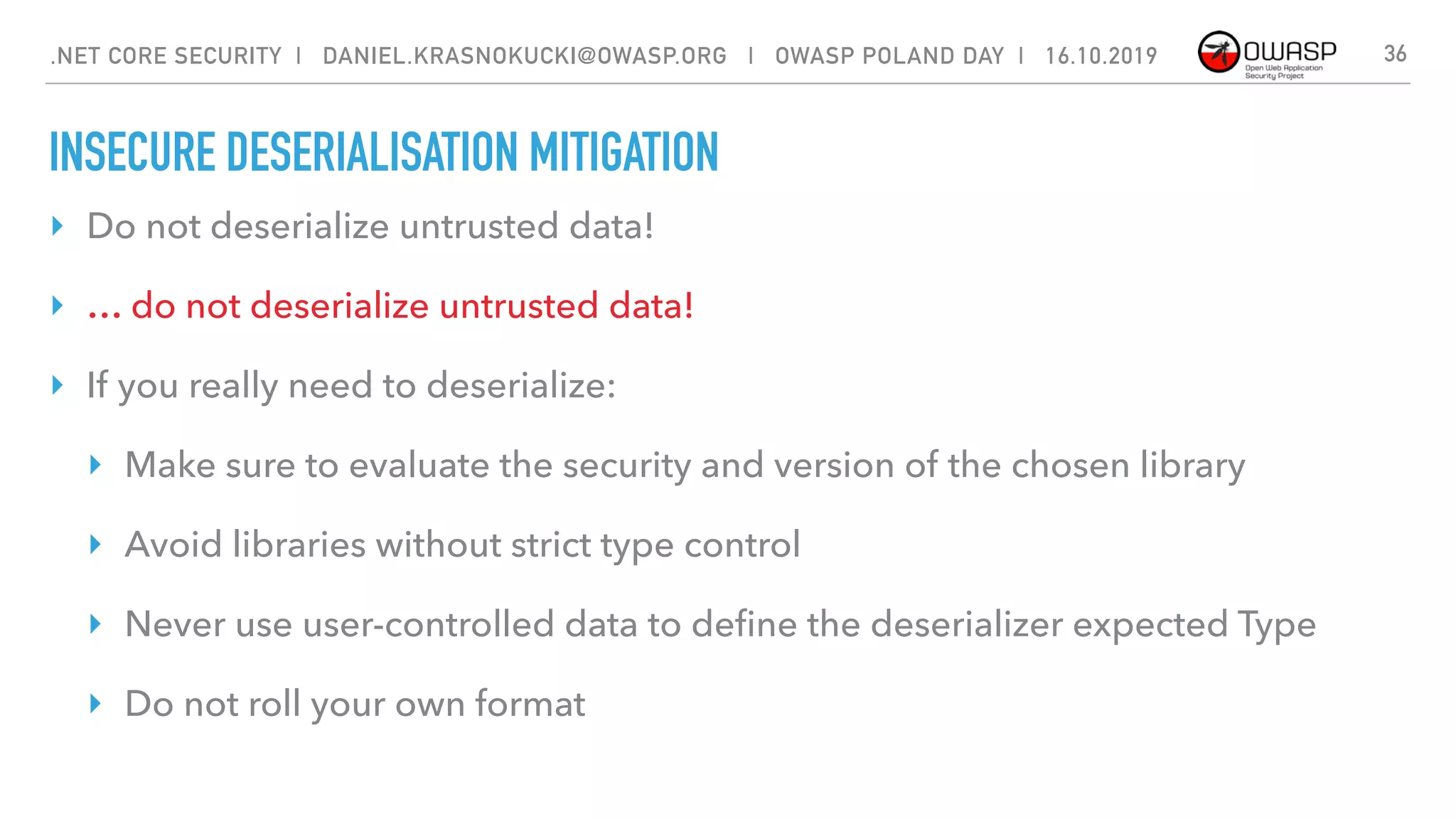
![INSECURE DESERIALISATION
Insecure deserialization often leads to remote code execution. Even if
deserialization flaws do not result in remote code execution, they can be used to
perform attacks, including replay attacks, injection attacks, and privilege
escalation attacks.
{
"$type": "System.Windows.Data.ObjectDataProvider, PresentationFramework",
“ObjectInstance": {
"$type":"System.Diagnostics.Process, System”},
"MethodParameters":{
"$type":"System.Collections.ArrayList, mscorlib",
"$values":["calc"]},
"MethodName":"Start"
}
.NET CORE SECURITY | DANIEL.KRASNOKUCKI@OWASP.ORG | OWASP POLAND DAY | 16.10.2019 11](https://image.slidesharecdn.com/dotnetcoresecurity1-191022061850/75/OPD-2019-NET-Core-Security-11-2048.jpg)






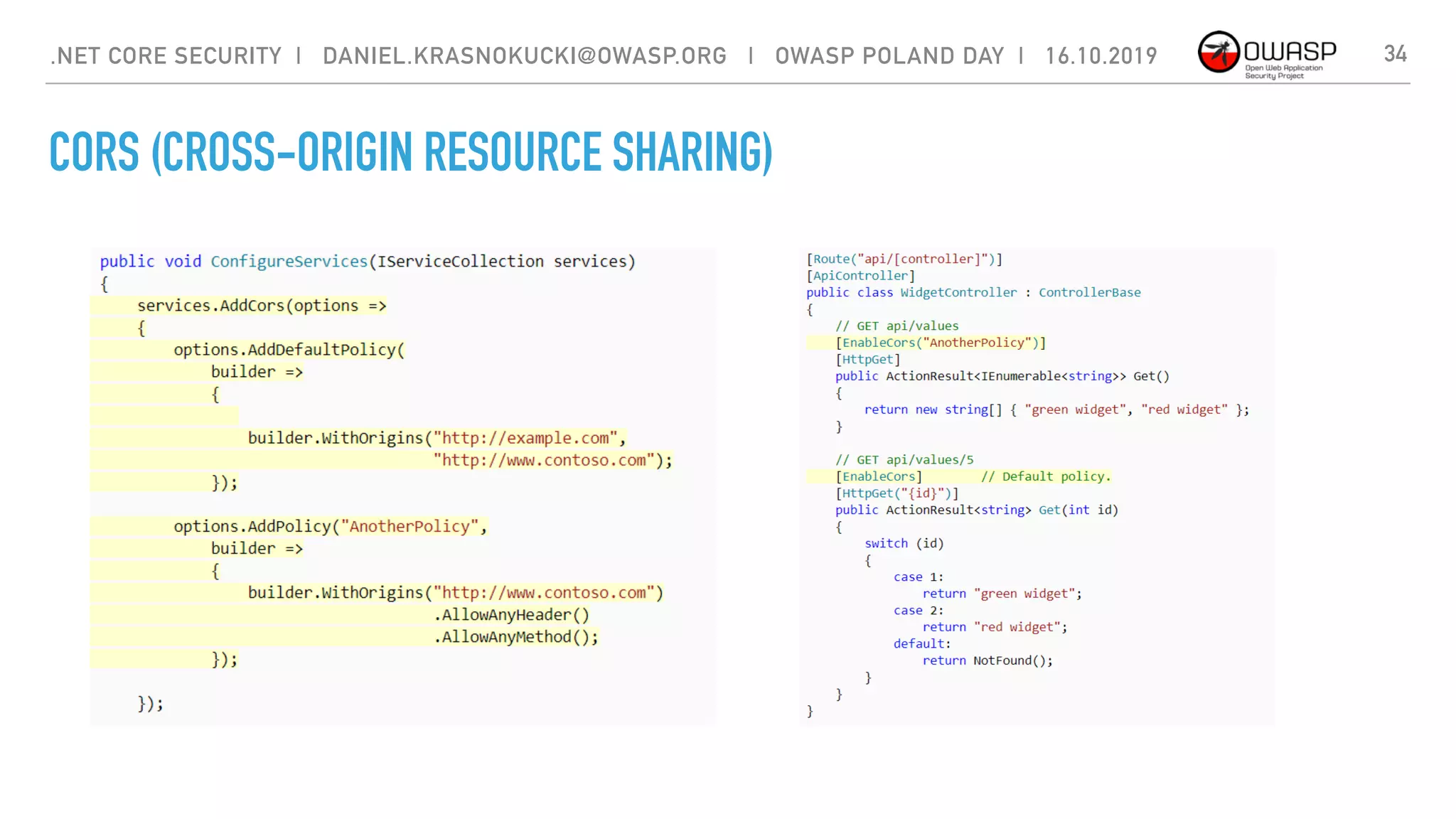
![CORS (CROSS-ORIGIN RESOURCE SHARING)
33.NET CORE SECURITY | DANIEL.KRASNOKUCKI@OWASP.ORG | OWASP POLAND DAY | 16.10.2019
A mechanism that allows restricted resources on a web page to be requested
from another domain outside the domain from which the first resource was
served.
A web page may freely embed cross-origin images, stylesheets, scripts, iframes,
and videos.[2] Certain "cross-domain" requests, notably Ajax requests, are
forbidden by default by the same-origin security policy.](https://image.slidesharecdn.com/dotnetcoresecurity1-191022061850/75/OPD-2019-NET-Core-Security-33-2048.jpg)