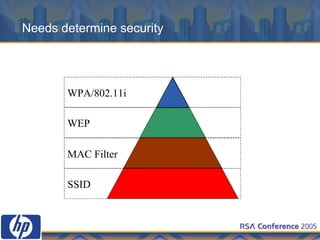
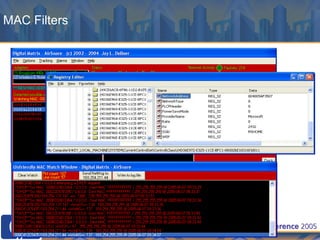
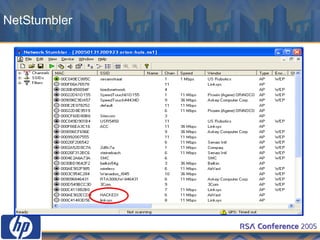
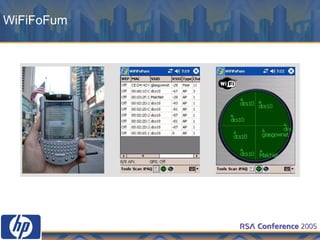
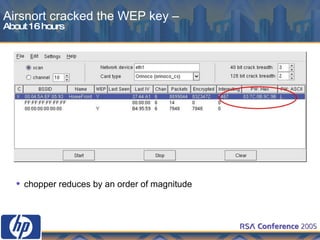
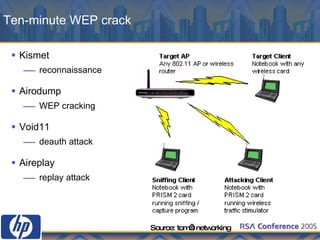
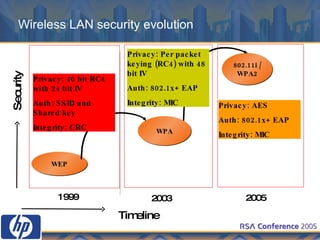
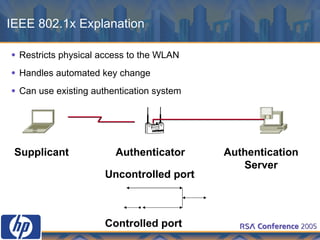
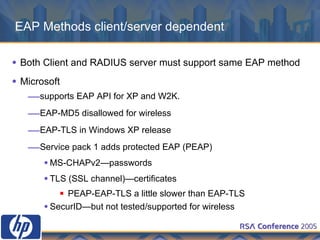
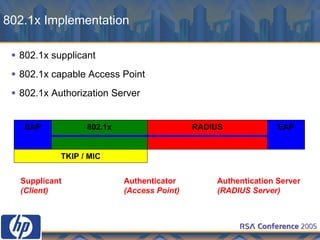
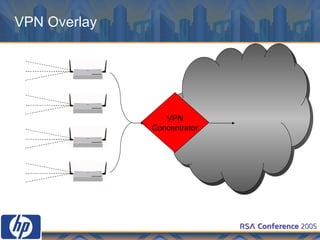
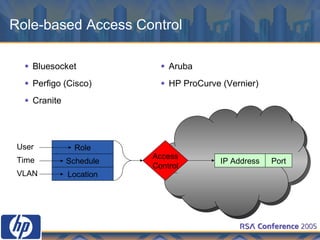
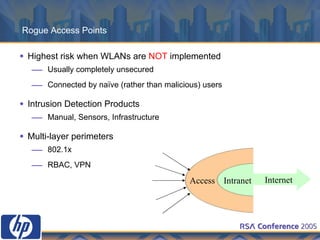
This document discusses WLAN security threats and countermeasures. It describes vulnerabilities in early security standards like WEP. It then outlines improved security mechanisms in WPA and 802.11i like AES encryption and 802.1x authentication. Finally, it recommends a multi-layered approach using tools like VPN, firewalls, and rogue AP detection to securely manage enterprise WLAN access.













![Send mail to: [email_address]](https://image.slidesharecdn.com/rsa-wlanhacking-090520074822-phpapp02/85/RSA-WLAN-Hacking-27-320.jpg)