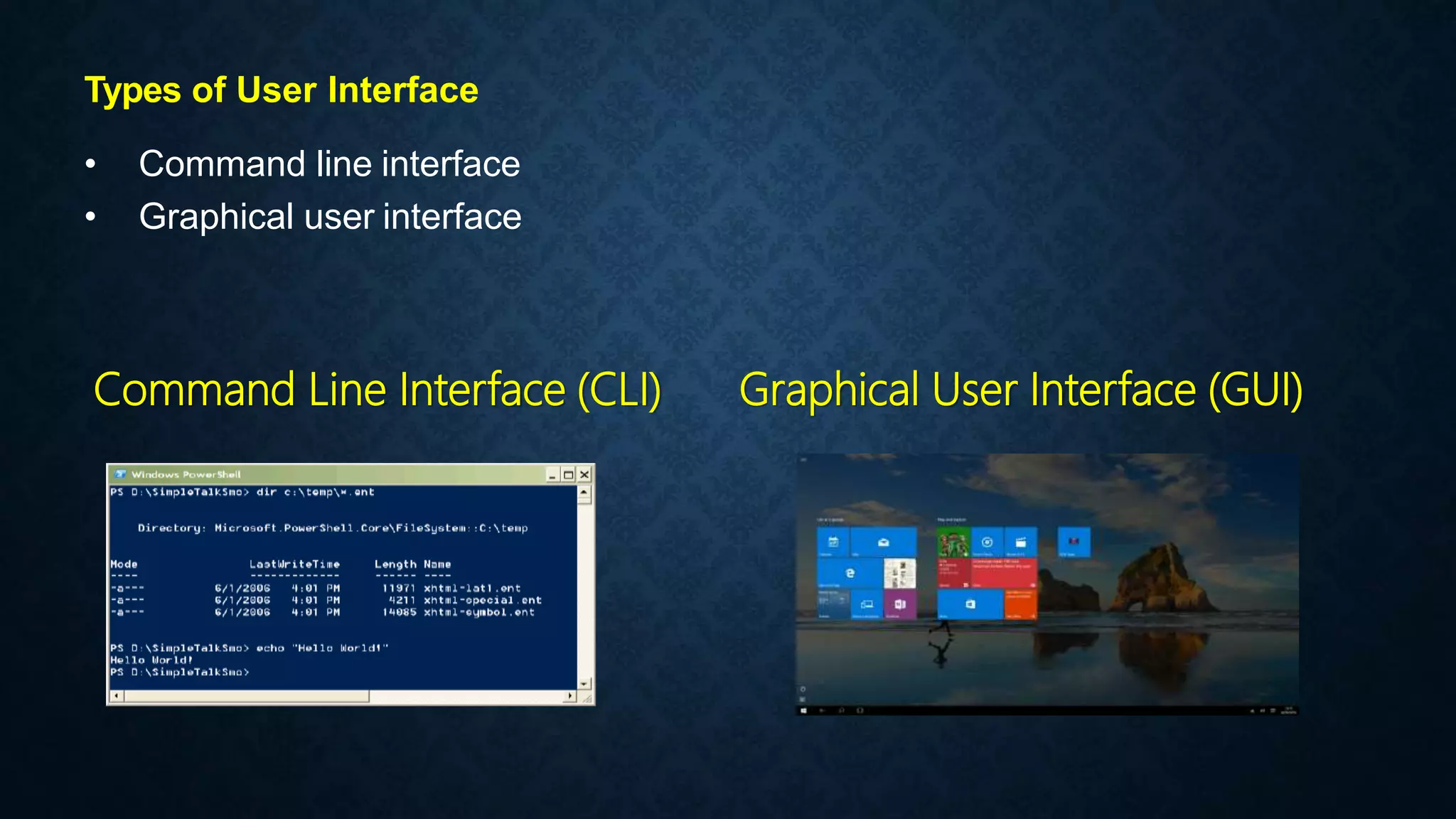
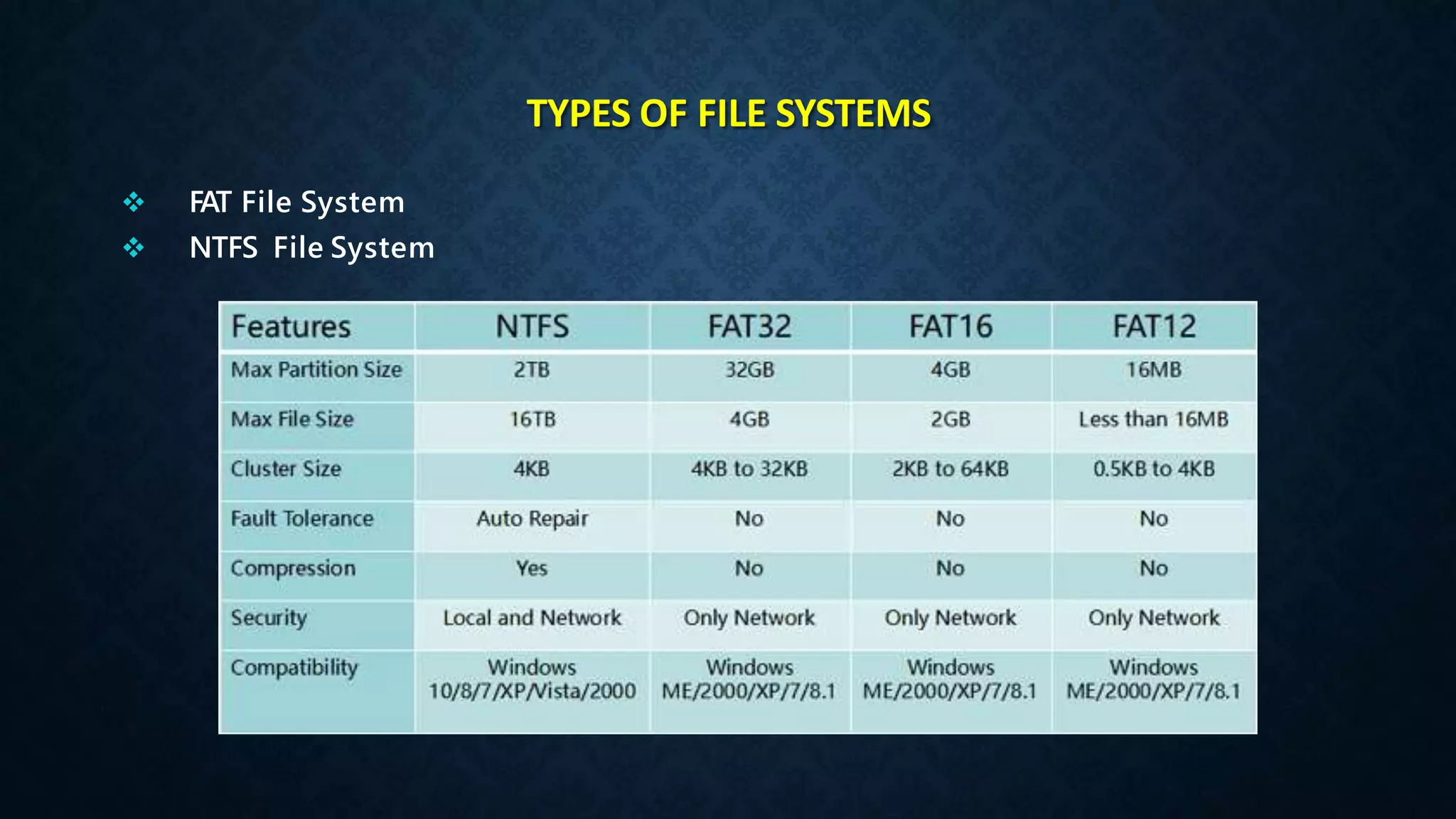
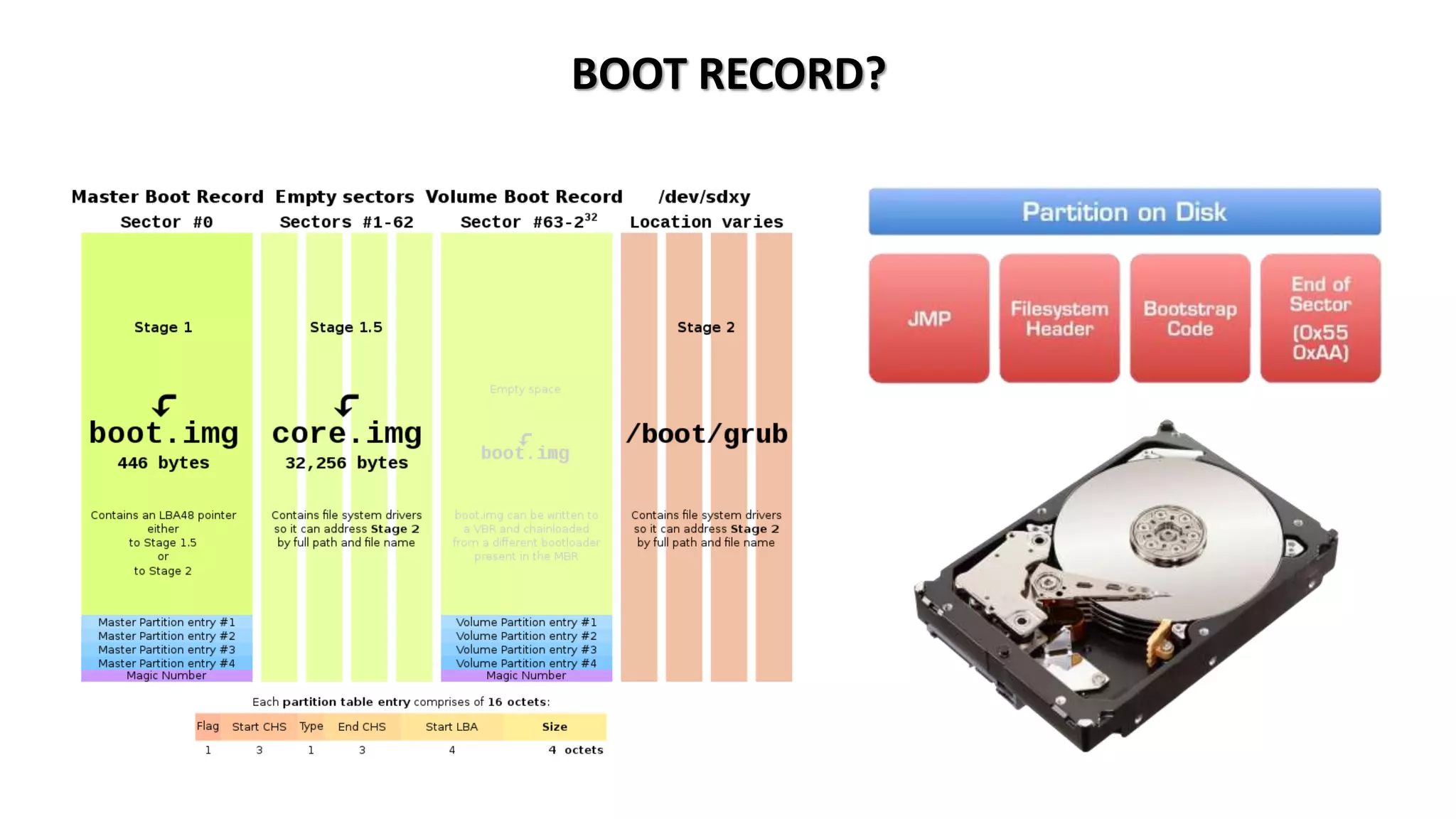
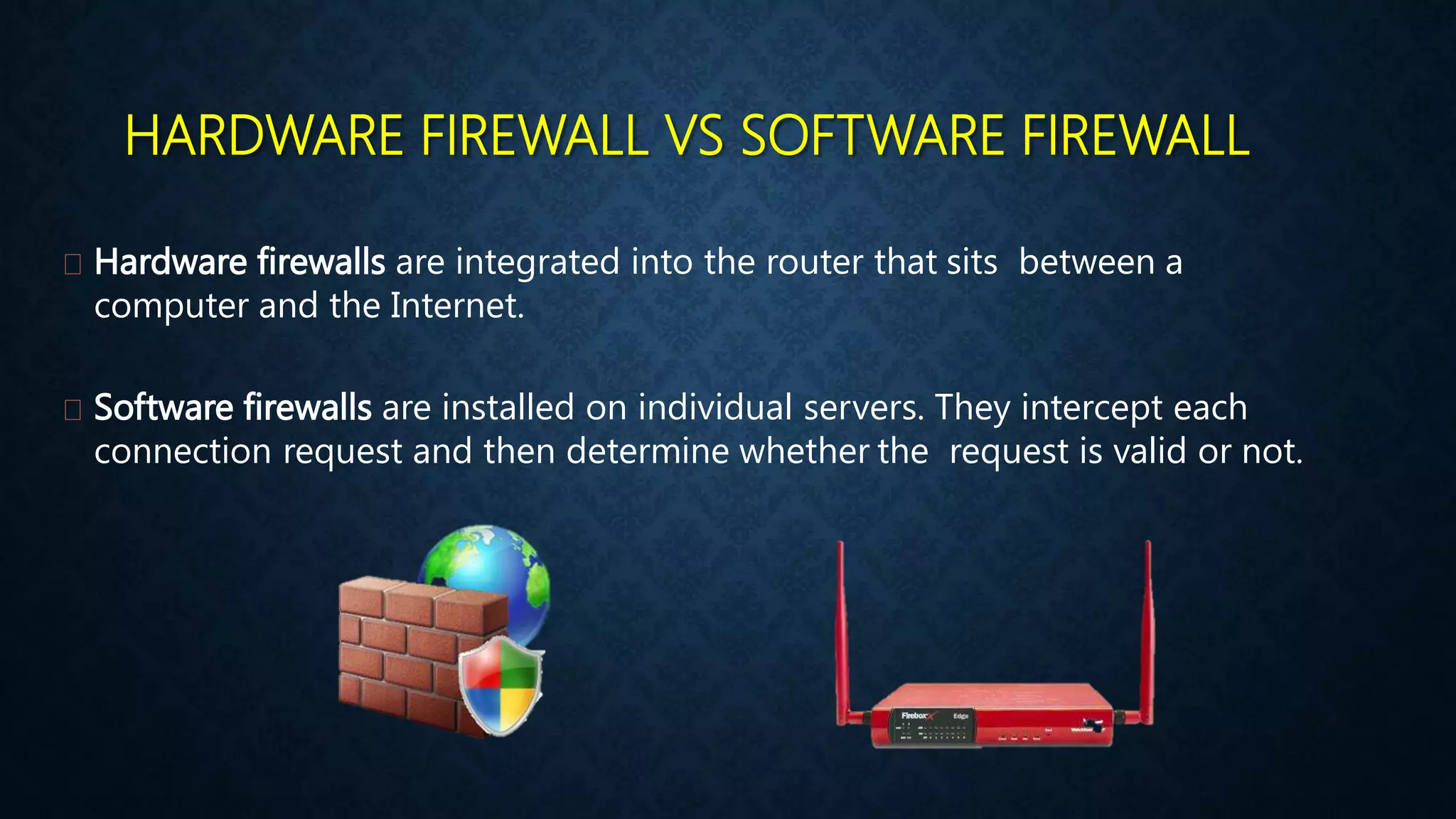
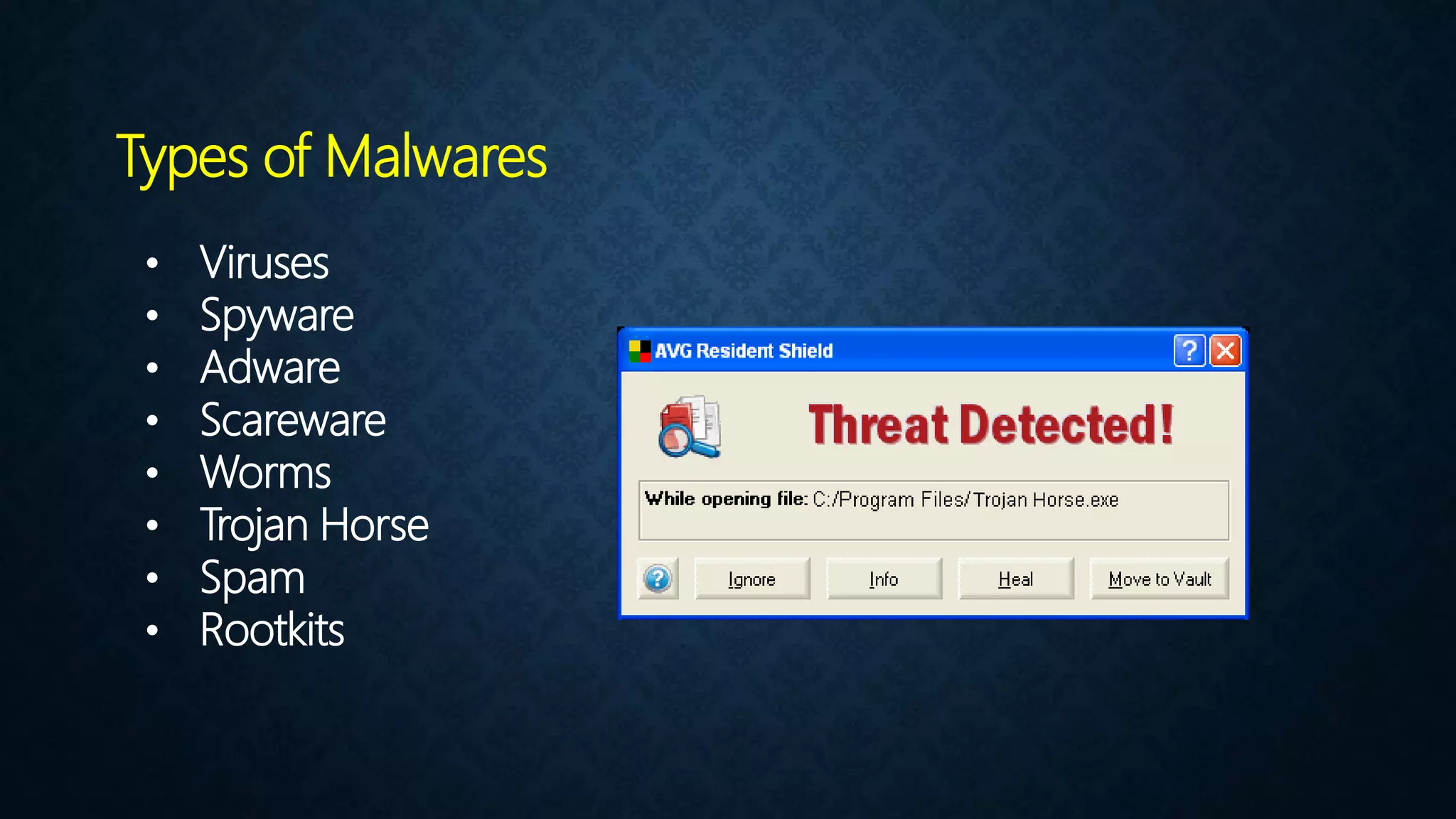
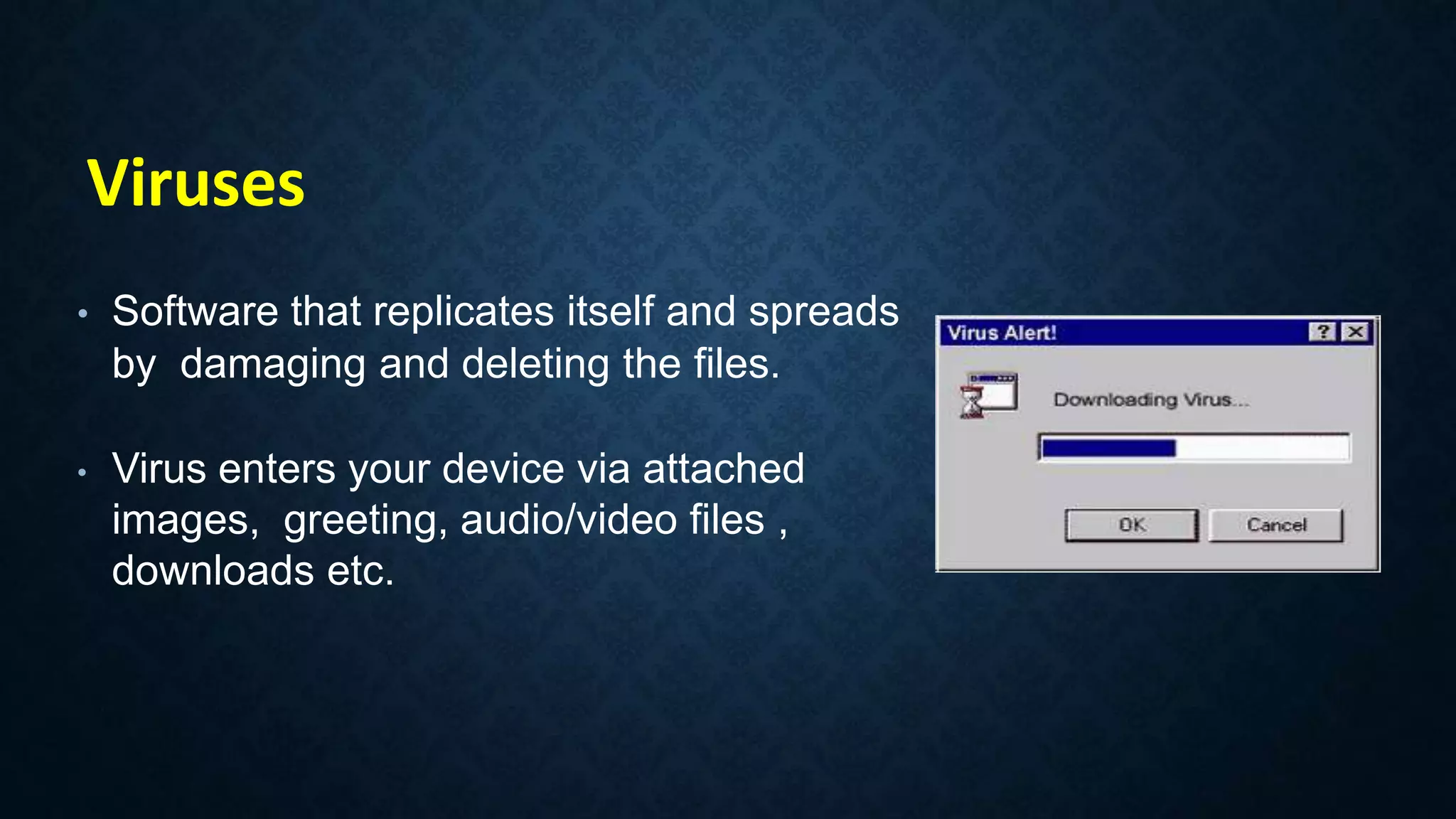
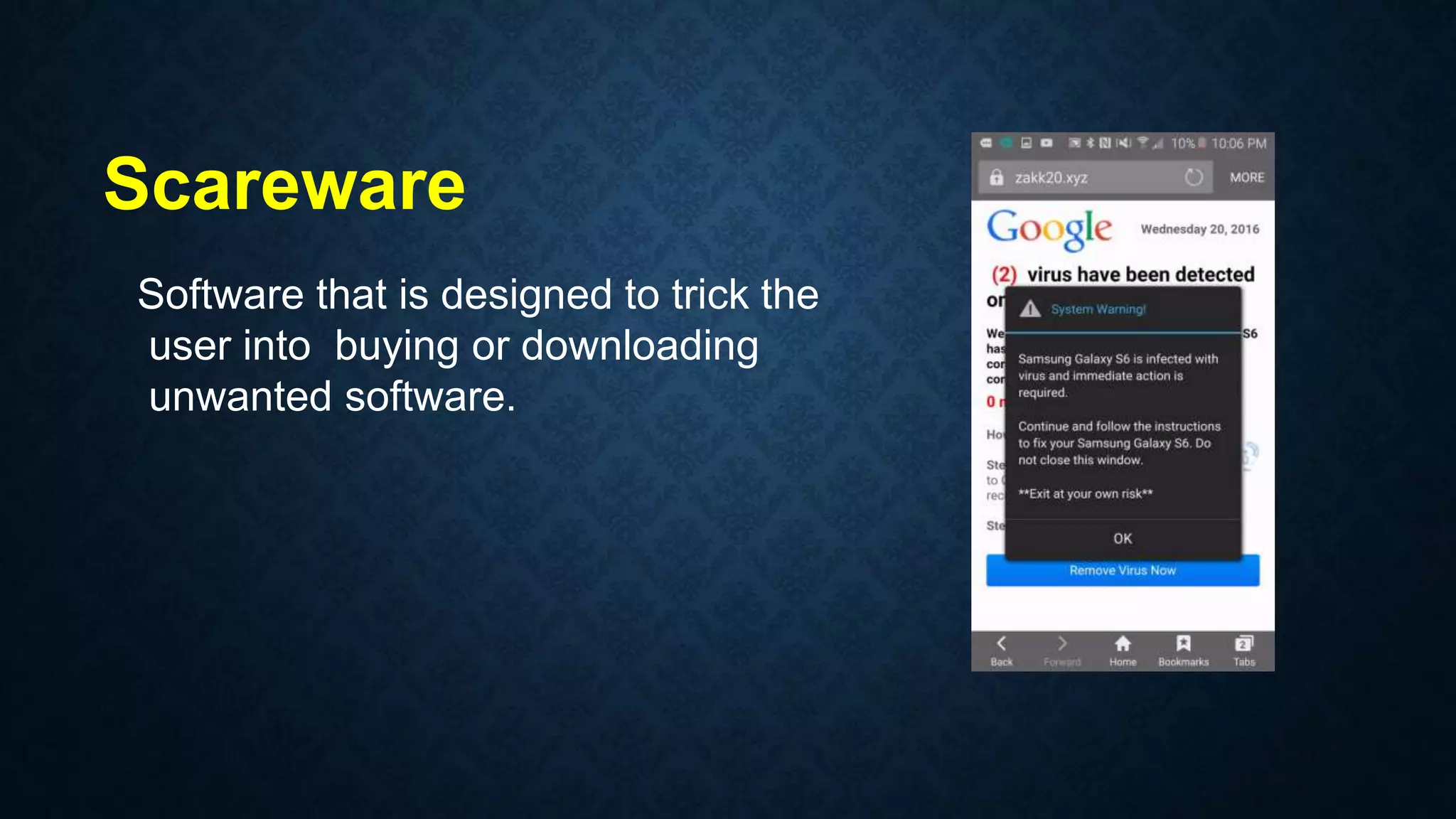
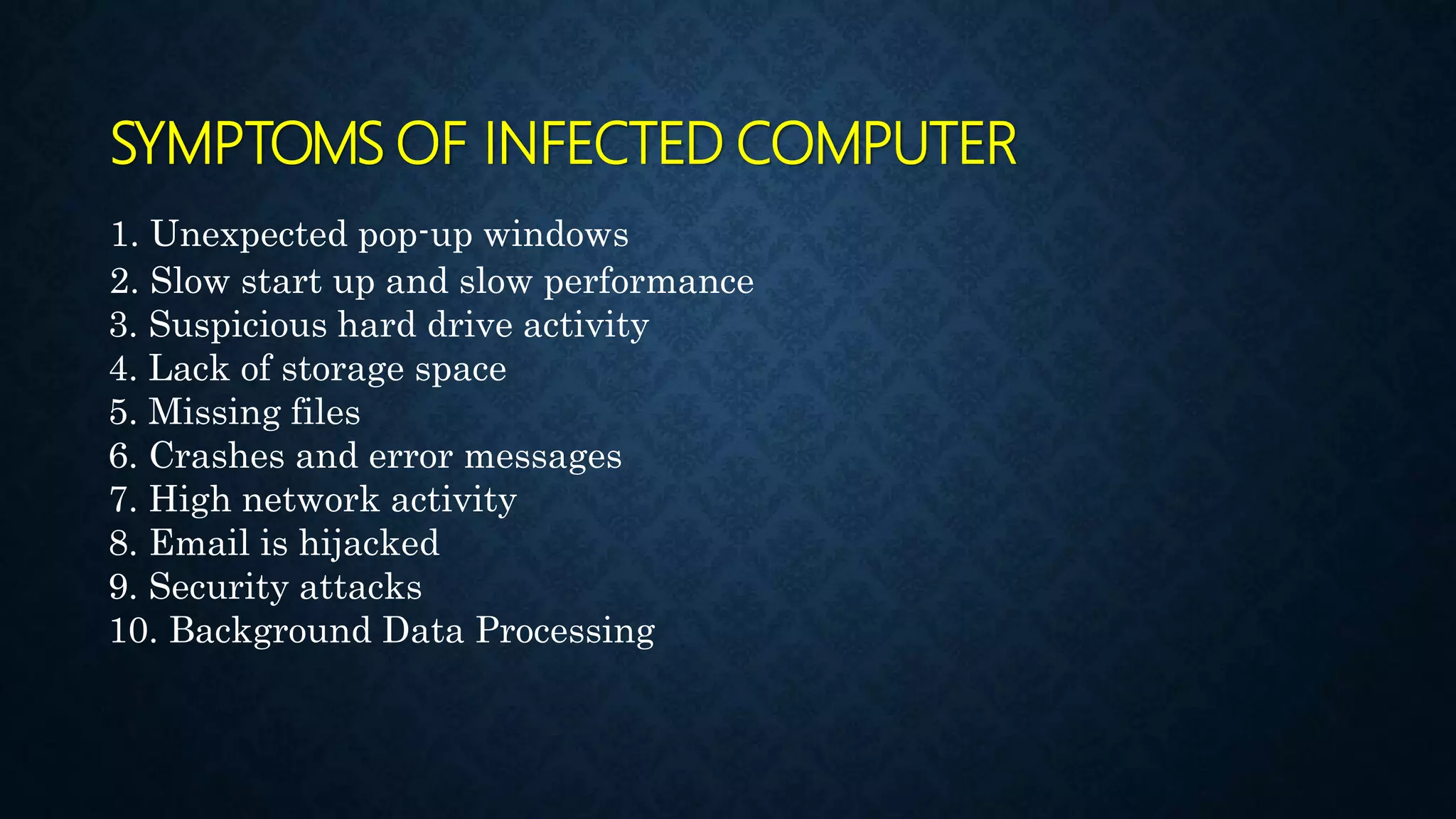
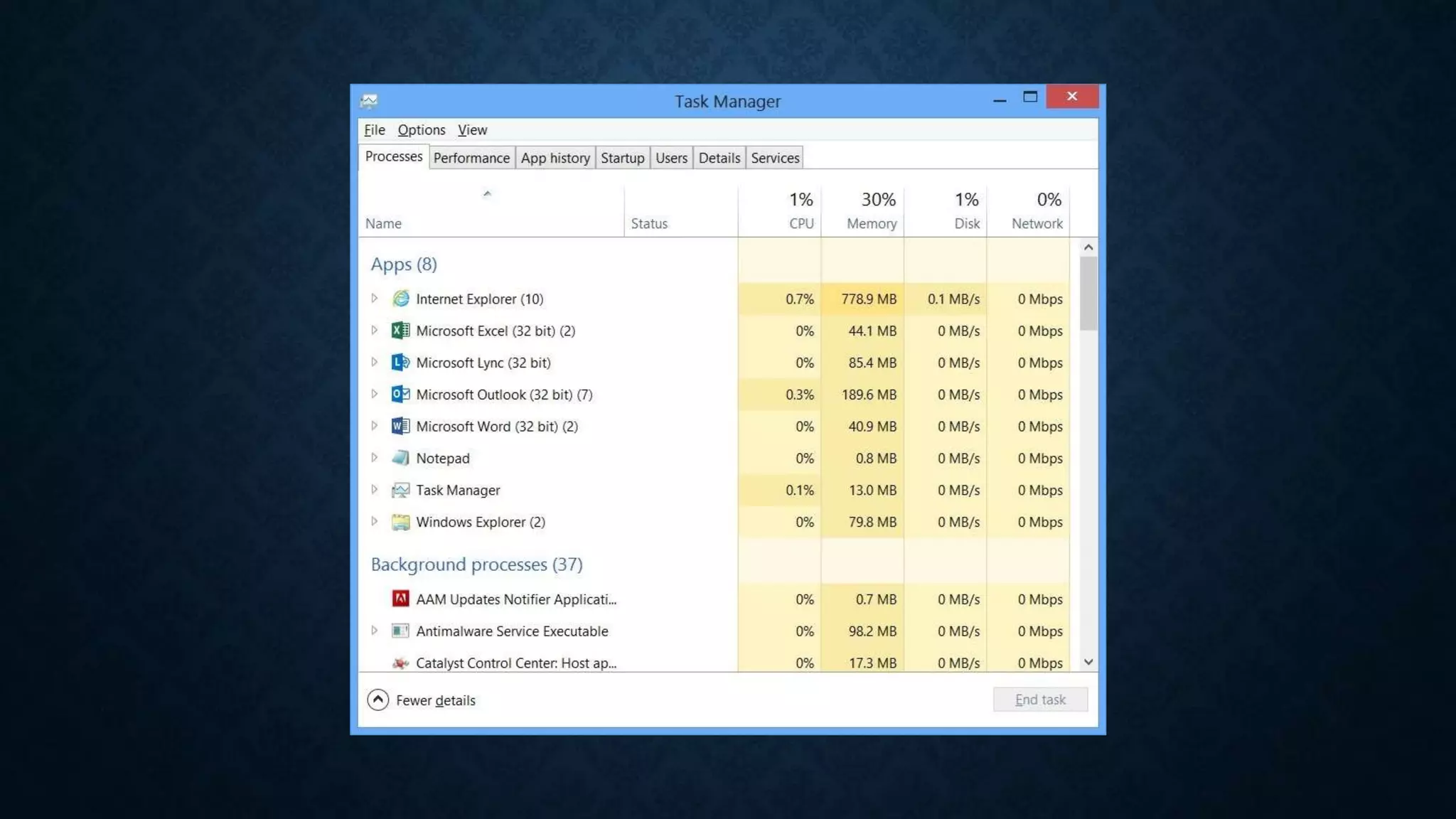
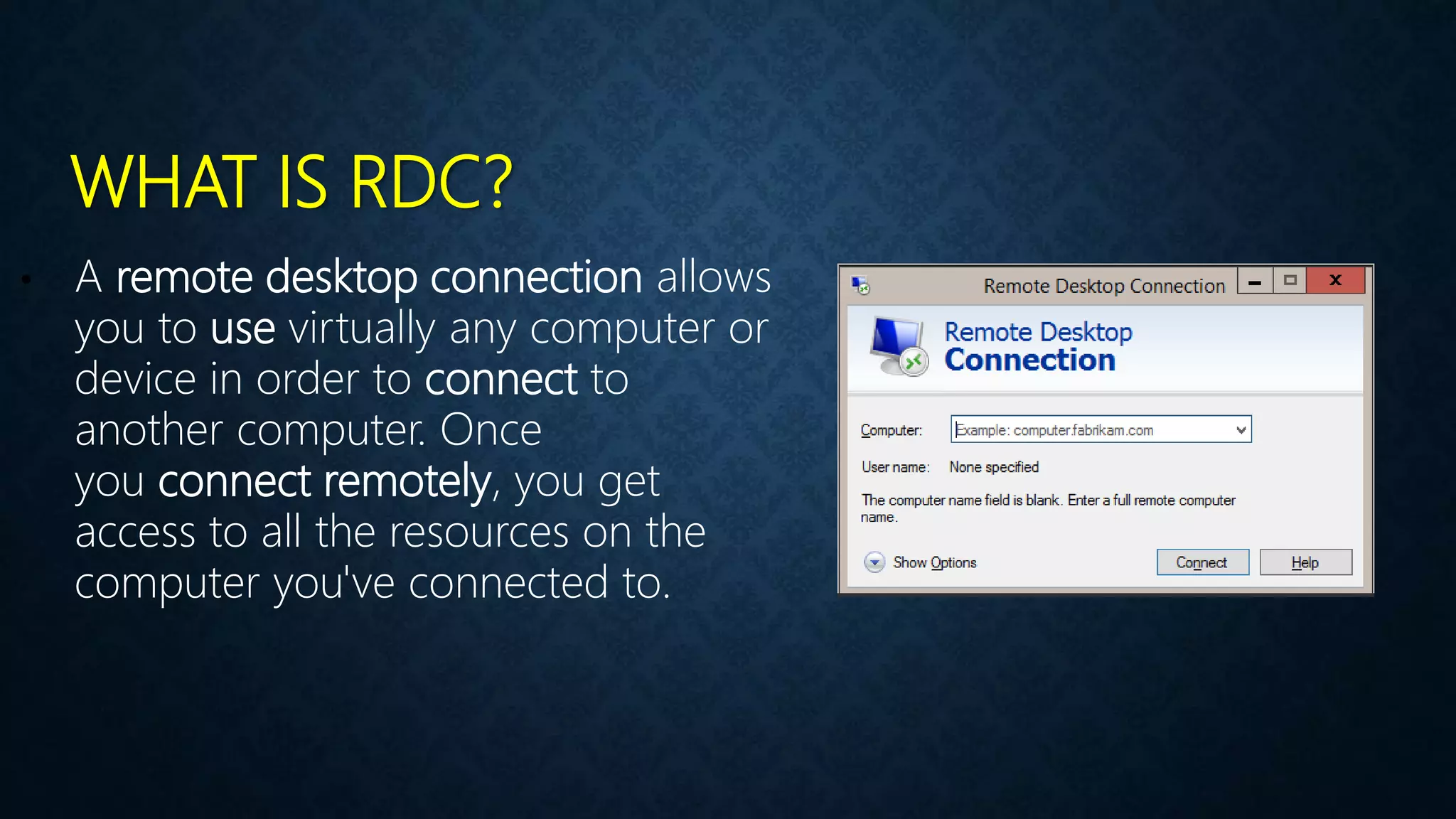
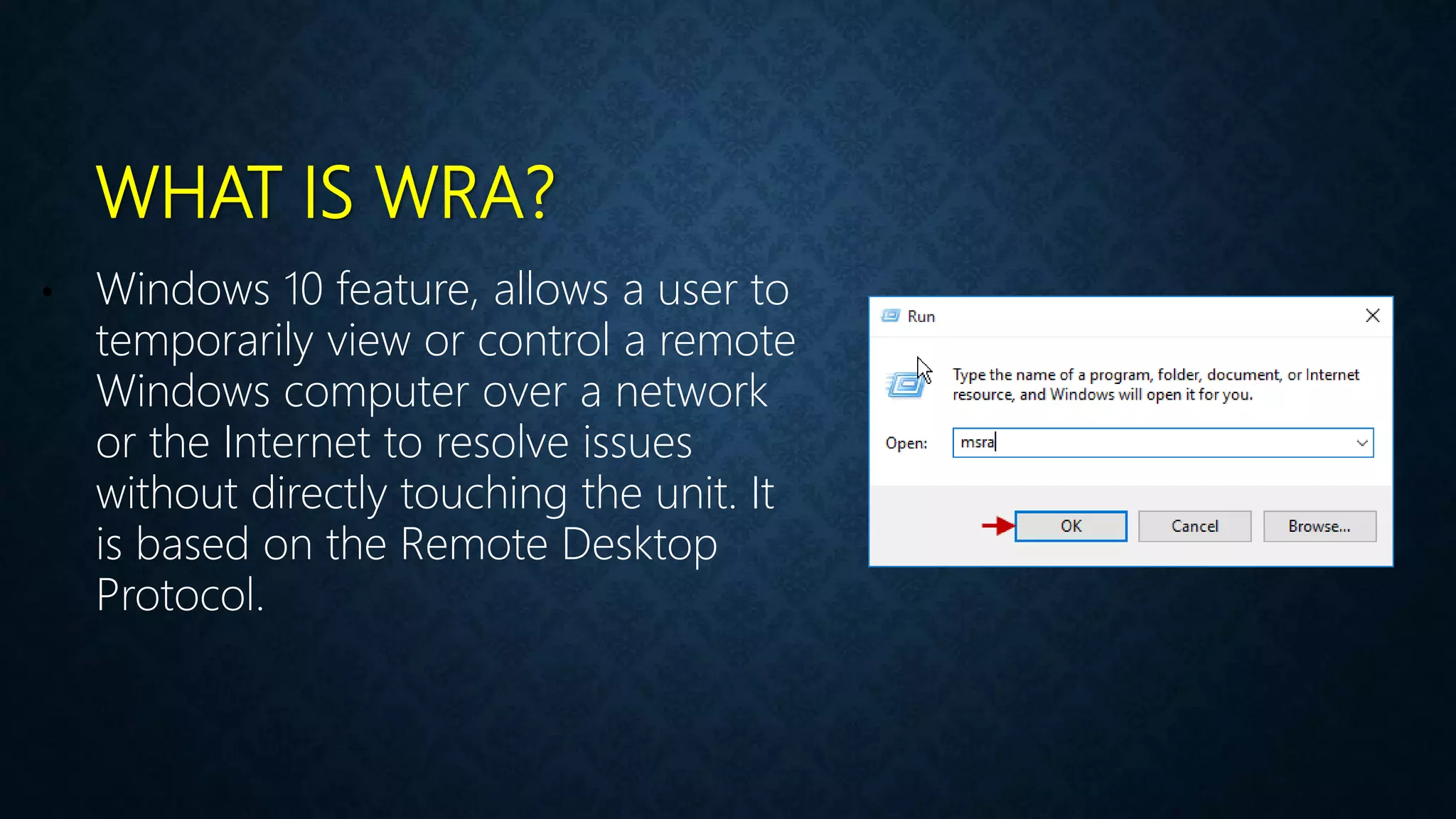
This document provides an overview of an operating system course for beginners to experts. It covers 20 topics related to the Windows 10 operating system, including installation, interface basics, user management, partitions, file systems, security features like Windows Firewall and Defender, command line terminals, utilities, the registry editor, antivirus software, policies, services, the task manager, connecting to networks and the internet, remote access, computer terms, and backup and restore. The course aims to provide a comprehensive guide to using and managing the Windows 10 operating system.