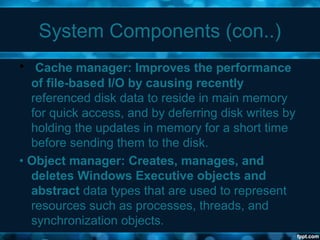
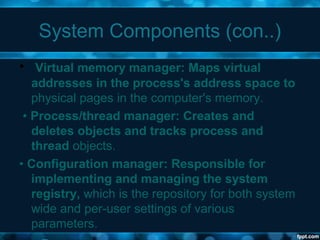
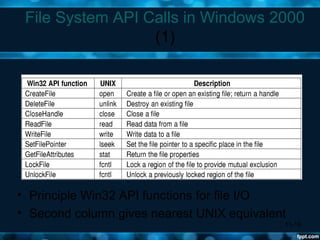
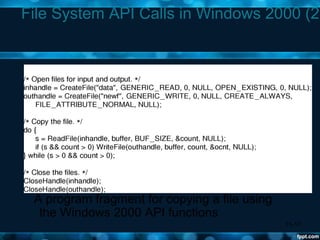
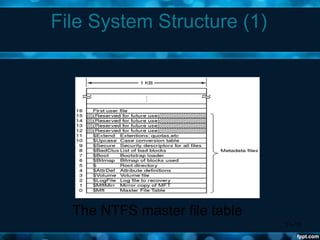
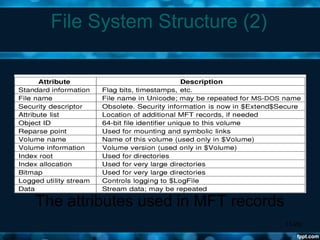
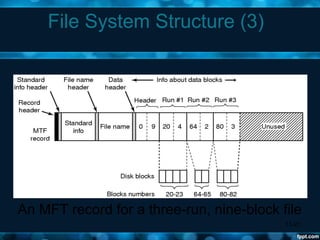
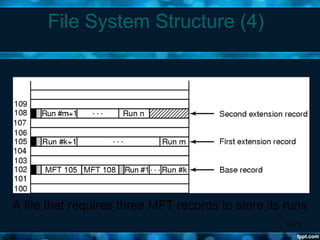
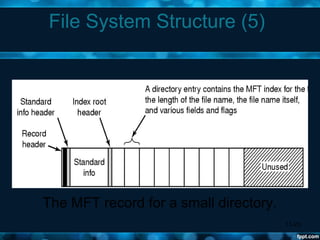
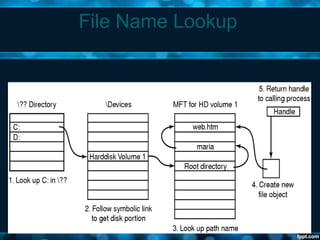
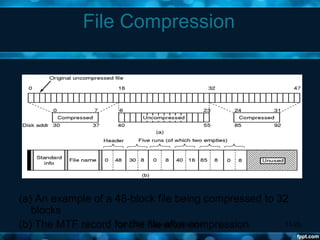
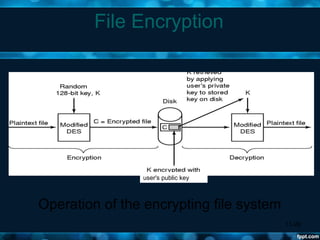
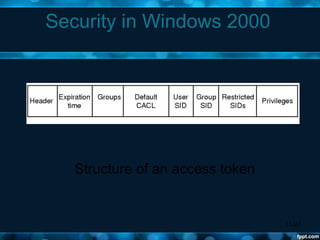
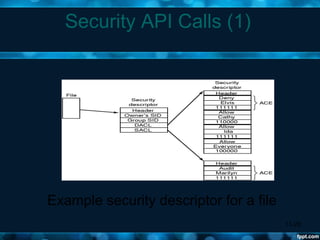
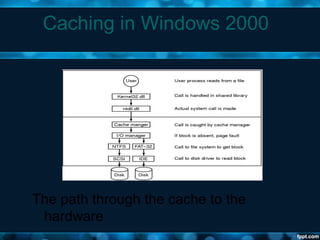
Windows 2000 aimed to improve extensibility, portability, reliability, compatibility, and performance over previous Windows versions. Its key components included the executive, kernel, hardware abstraction layer, device drivers, and windowing system. The executive contained core OS services like memory management, process/thread management, security, I/O, and inter-process communication. It also included modules for specific functions like I/O management, caching, object management, plug and play, power management, and security. The kernel handled lower-level tasks like scheduling, switching, and synchronization.