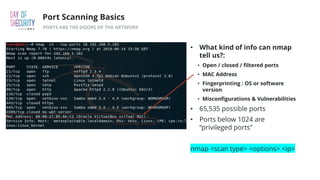
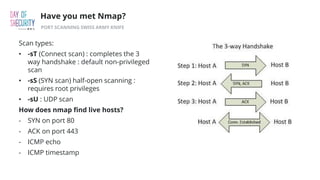
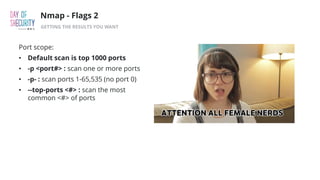
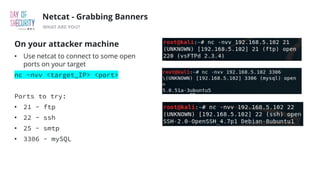
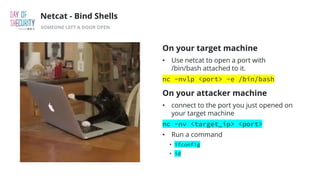
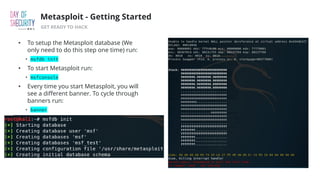
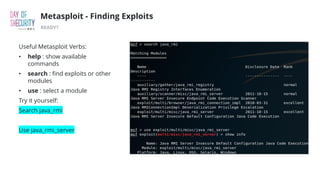
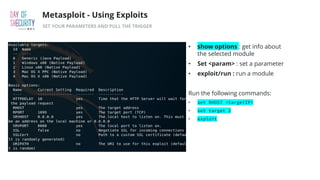
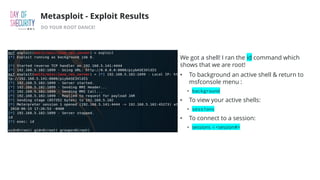
The document outlines the fundamentals of network penetration testing using tools like Nmap, Netcat, and Metasploit. It covers topics such as port scanning, shell types, and techniques for exploiting vulnerabilities. Additionally, it highlights exercises and command usage for each tool, providing a comprehensive introduction to network security practices.