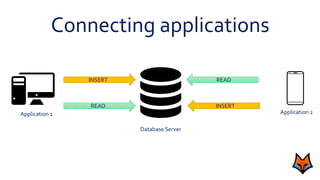
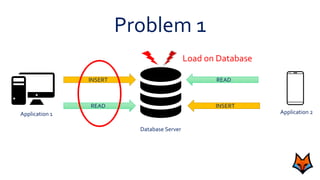
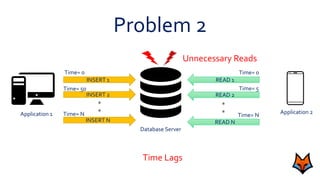
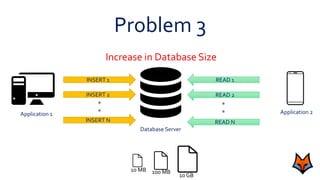
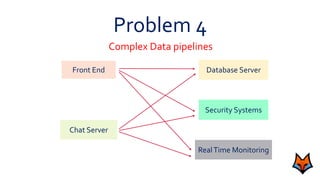
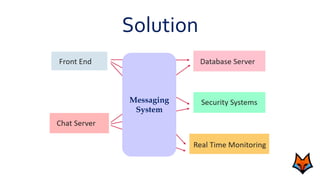
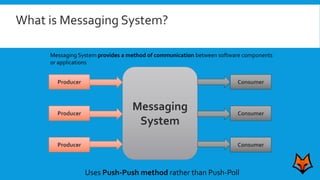
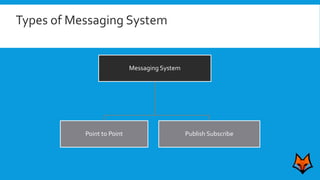
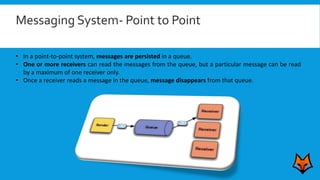
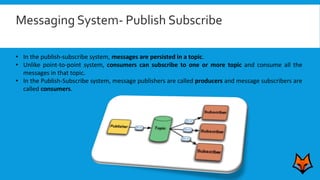
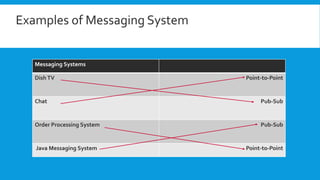
This document discusses the need for a messaging system to address problems that arise without one, such as increased load on databases, unnecessary reads, and time lags. It defines a messaging system as a method of asynchronous communication between applications using a producer-consumer model. There are two main types: point-to-point systems with message queues and publish-subscribe systems with topics. Examples of each type are provided.