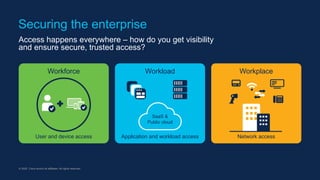
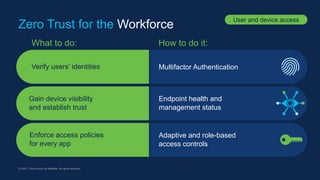
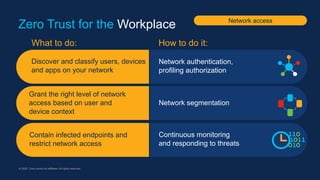
The document outlines the concept of Zero Trust architecture and its importance in enhancing cybersecurity by ensuring that all access to services is authenticated, authorized, and encrypted regardless of network location. It emphasizes the need for strong user and device identities, dynamic authentication, and continuous monitoring to protect enterprise resources. The document also discusses practical steps for implementing Zero Trust across user access, application workloads, and network security.