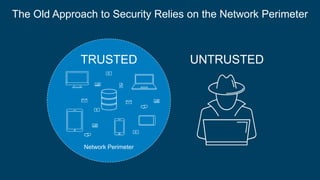
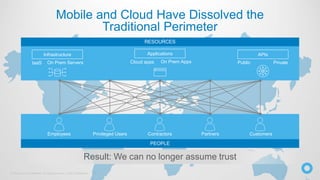
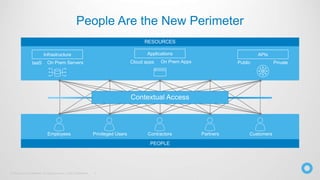
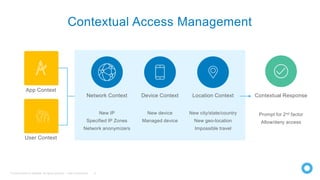
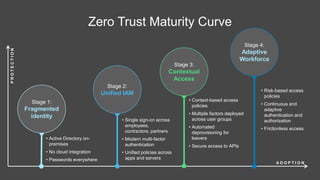
The document discusses the critical role of identity within a zero trust security strategy, emphasizing that traditional network perimeters are no longer reliable due to the dissolution of boundaries in modern infrastructure. It outlines the need for contextual access management, where identity becomes essential in managing the right access to resources for users based on their context. The zero trust journey begins with identity and involves adopting modern access management practices to advance maturity in security posture.