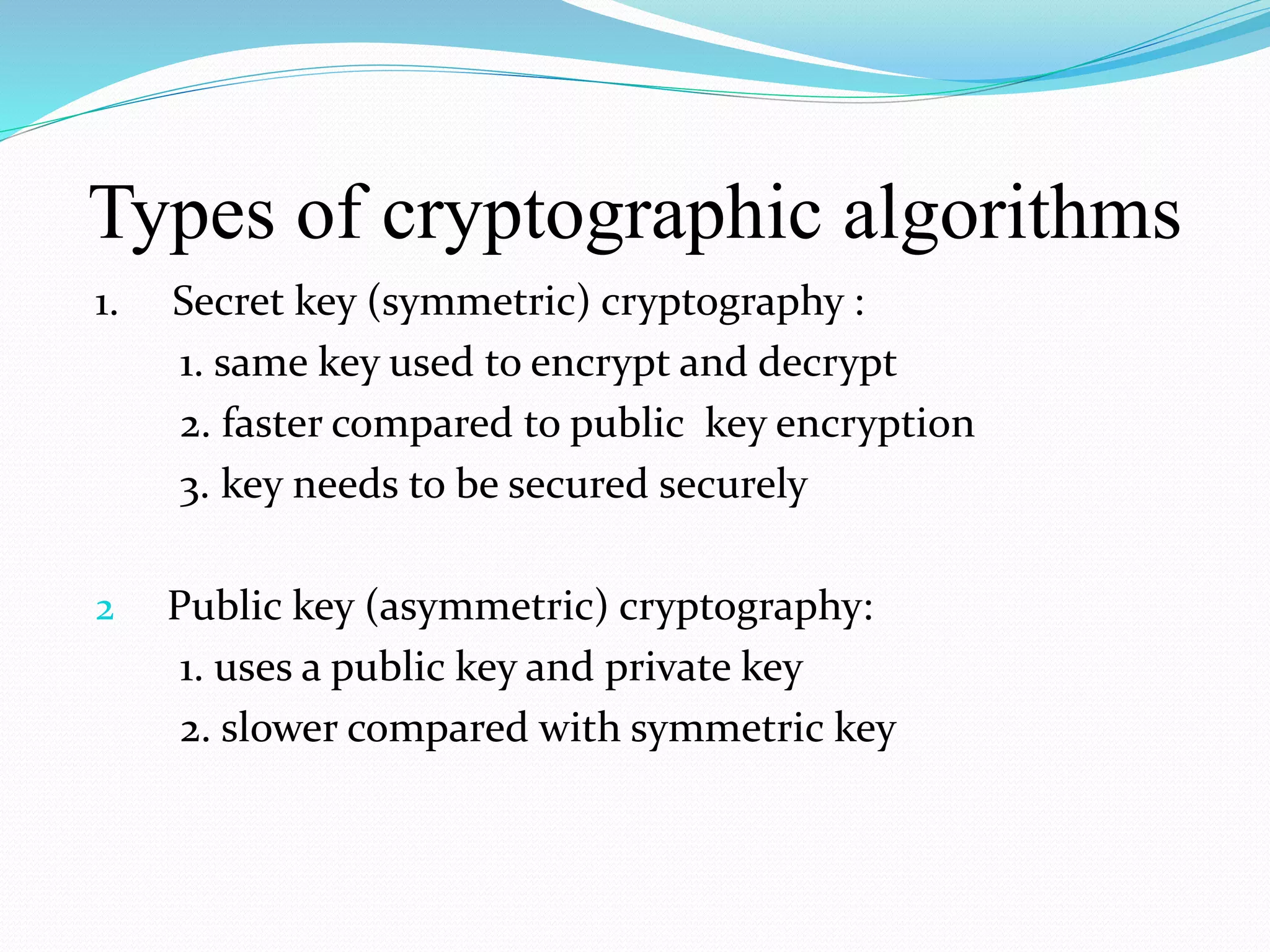
This document provides an introduction to cryptography. It defines cryptography as the practice of hiding information and discusses its importance for secure communication. The document outlines the basic components of cryptography including plaintext, encryption, ciphertext, decryption, and keys. It also describes different types of cryptographic algorithms like the Caesar cipher and symmetric and asymmetric key cryptography. The document concludes by emphasizing the importance of implementing cryptography for network security.