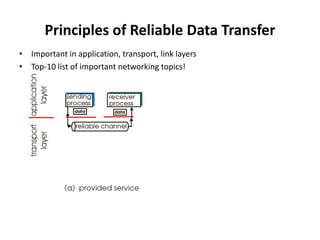
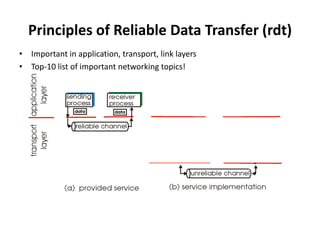
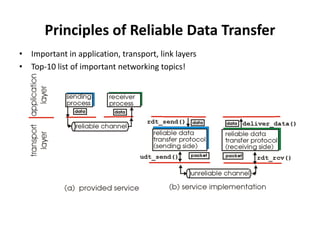
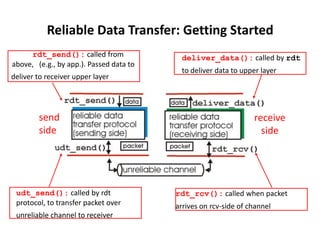
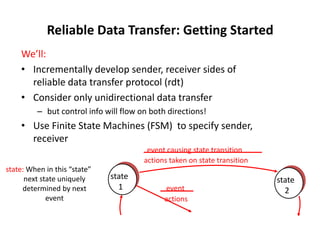
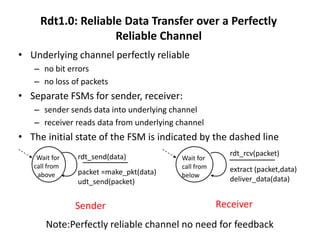
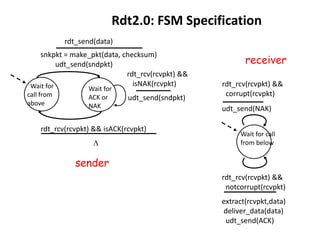
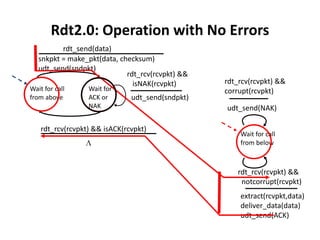
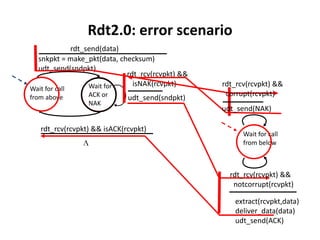
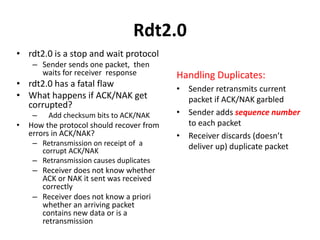
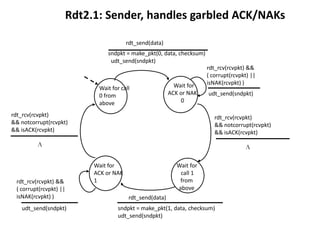
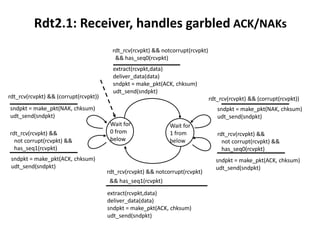
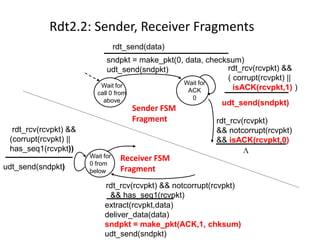
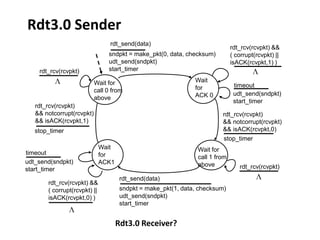
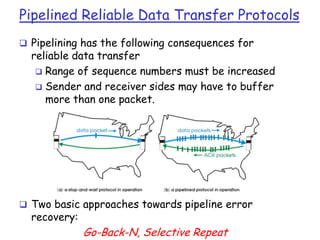
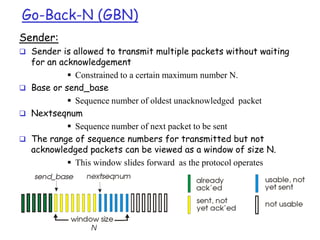
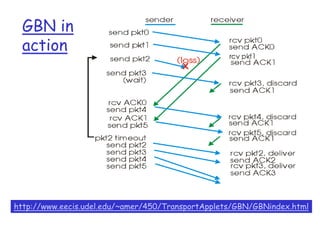
The document summarizes key concepts related to reliable data transfer over computer networks. It discusses principles of reliable data transfer including error detection, receiver feedback, and retransmission. It introduces stop-and-wait and sliding window protocols, specifically RDT 1.0, 2.0, 2.1, 2.2 and 3.0 which handle increasingly challenging scenarios like bit errors, lost packets, and pipelining. The final section summarizes the Go-Back-N sliding window protocol that allows limited in-flight packets to improve throughput compared to stop-and-wait protocols.