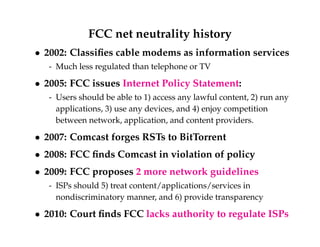
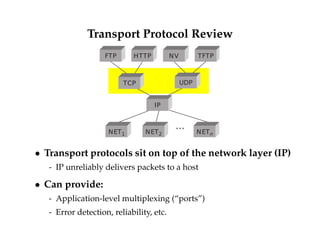
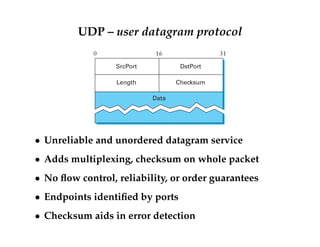
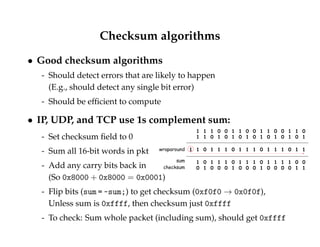
This document discusses transport layer protocols and reliability in computer networks. It begins with an overview of the end-to-end model, UDP, and TCP. It then discusses the end-to-end argument that functions should be implemented at endpoints rather than in the network. Link-level reliability is not sufficient and TCP provides end-to-end reliability with sequenced packets, acknowledgments, and retransmissions. TCP also provides flow control using advertised window sizes.




![Strong End-to-End
The network’s job is to transmit datagrams as
efficiently and flexibly as possible. Everything
else should be done at the fringes. . .
– [RFC 1958]
Why?](https://image.slidesharecdn.com/computernetwork11-140901161655-phpapp02/85/Computer-network-11-5-320.jpg)




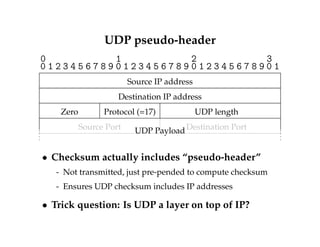

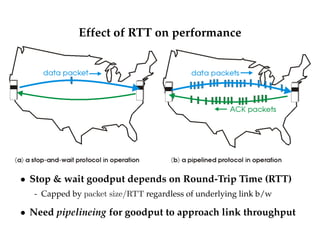
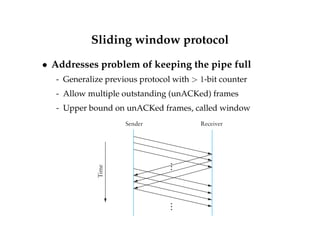
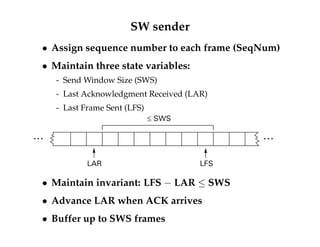
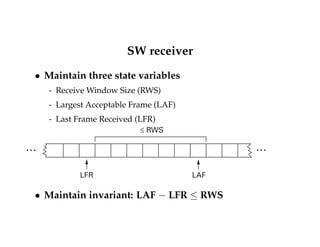


![High-level view of TCP
Application process
Write
bytes
TCP
Send buffer
Segment Segment Segment
Transmit segments
Application process
Read
bytes
TCP
Receive buffer
…
…
…
Full duplex, connection-oriented byte stream
Flow control
- If one end stops reading, writes at other eventually block/fail
Congestion control
- Keeps sender from overrunning network [more in lecture 5]](https://image.slidesharecdn.com/computernetwork11-140901161655-phpapp02/85/Computer-network-11-22-320.jpg)
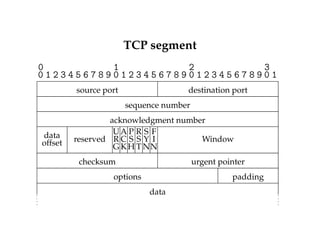





![State summary [RFC 793]
CLOSED
LISTEN
Active open/SYN
SYN_RCVD SYN_SENT
ESTABLISHED
CLOSE_WAIT
Close/FIN
CLOSING LAST_ACK
TIME_WAIT
FIN_WAIT_1
FIN_WAIT_2
Passive open Close
Send/SYN
SYN/SYN + ACK
SYN + ACK/ACK
SYN/SYN + ACK
ACK
Close/FIN
Close/FIN FIN/ACK
FIN/ACK
ACK + FIN/ACK
Timeout after two
segment lifetimes
FIN/ACK
ACK
ACK
ACK
Close
CLOSED](https://image.slidesharecdn.com/computernetwork11-140901161655-phpapp02/85/Computer-network-11-31-320.jpg)

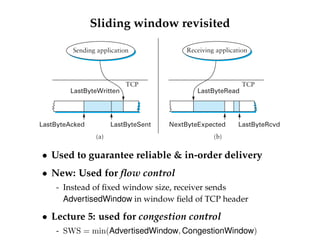
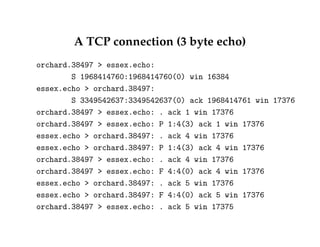


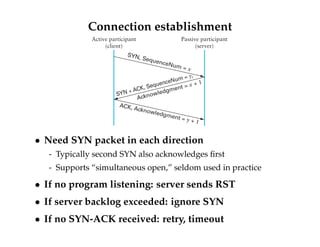
![Other details
Persist timer
- Sender can block because of 0-sized receive window
- Receiver may open window, but ACK message lost
- Sender keeps probing (sending one byte beyond window)
Keep-alives [RFC 1122]
- Detect dead connection even when no data to send
- E.g., remote login server, and client rebooted
- Solution: Send “illegal” segments with no data and already
acknowledged sequence number (SND.NXT-1)
- Or can include one byte of garbage data
- Remote side will RST (if rebooted), or timeout (if crashed)](https://image.slidesharecdn.com/computernetwork11-140901161655-phpapp02/85/Computer-network-11-37-320.jpg)
