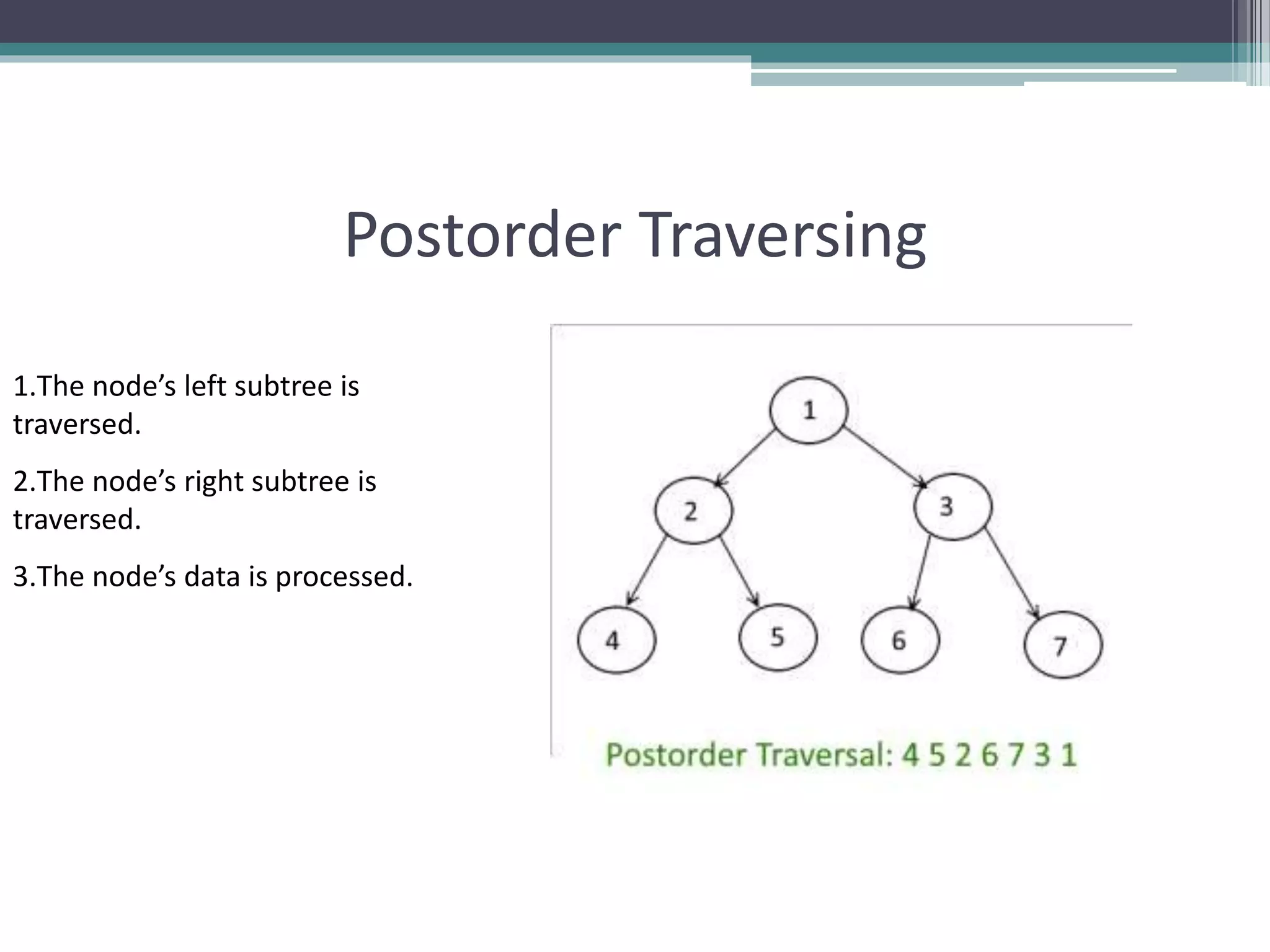
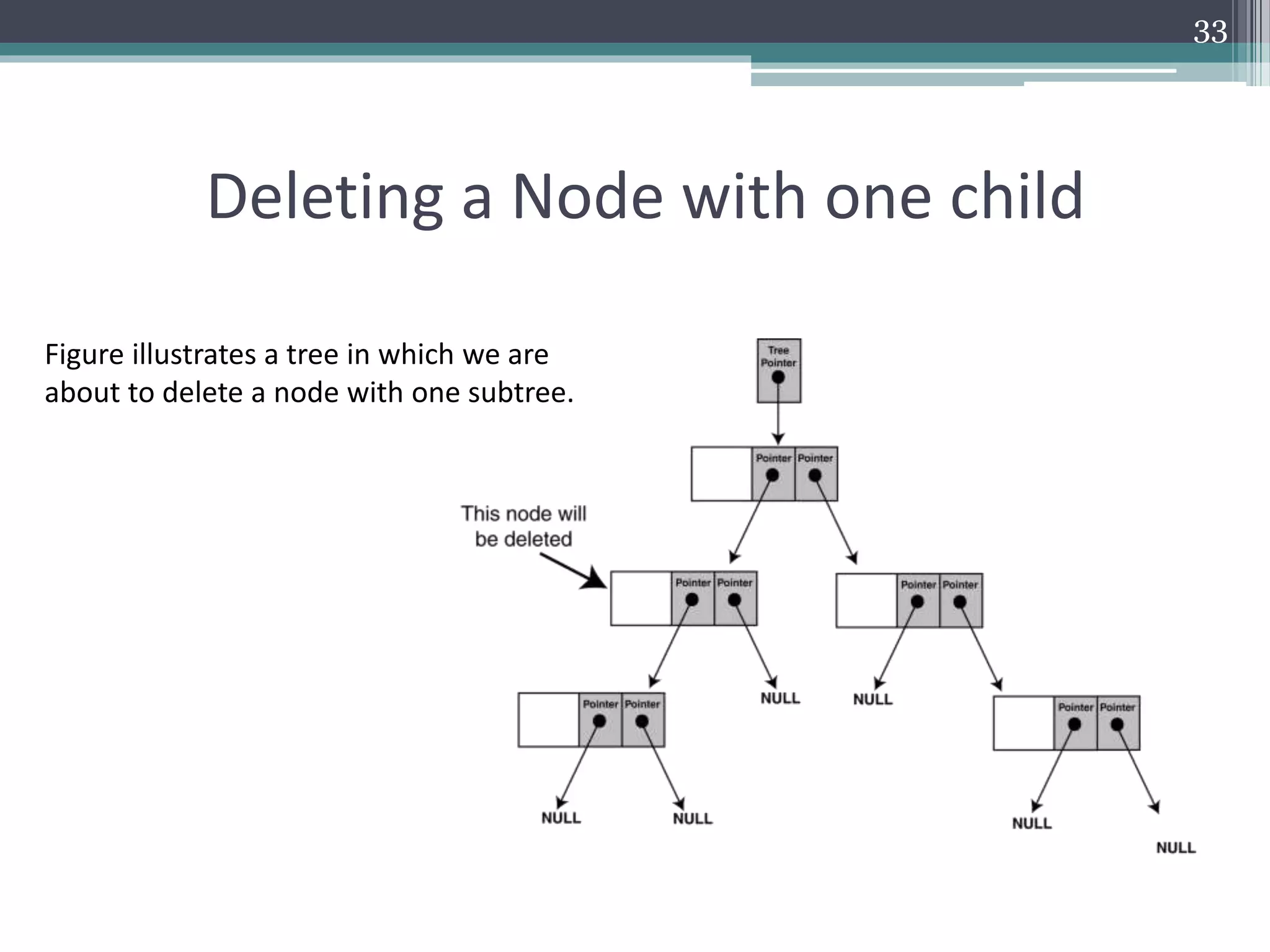
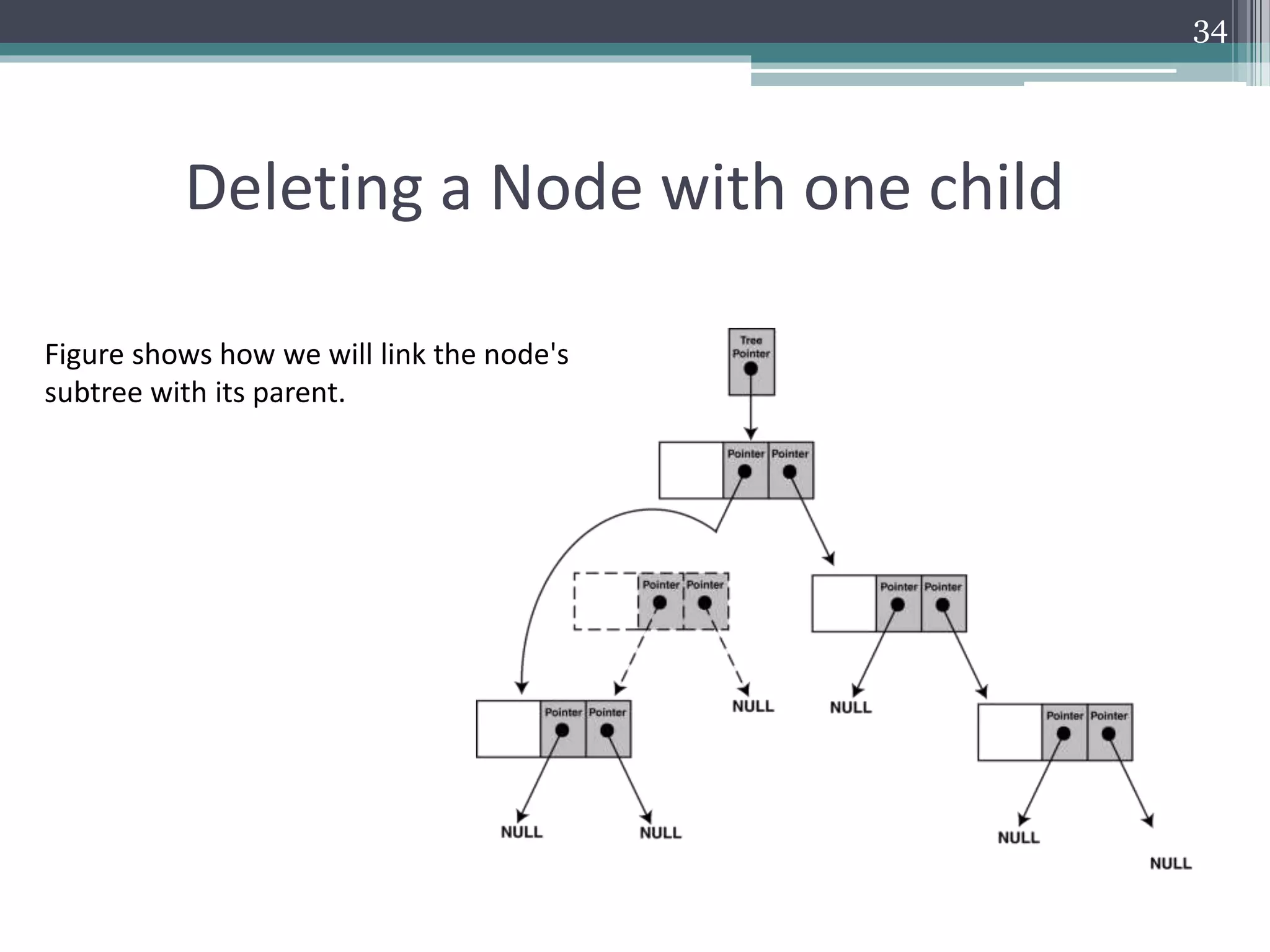
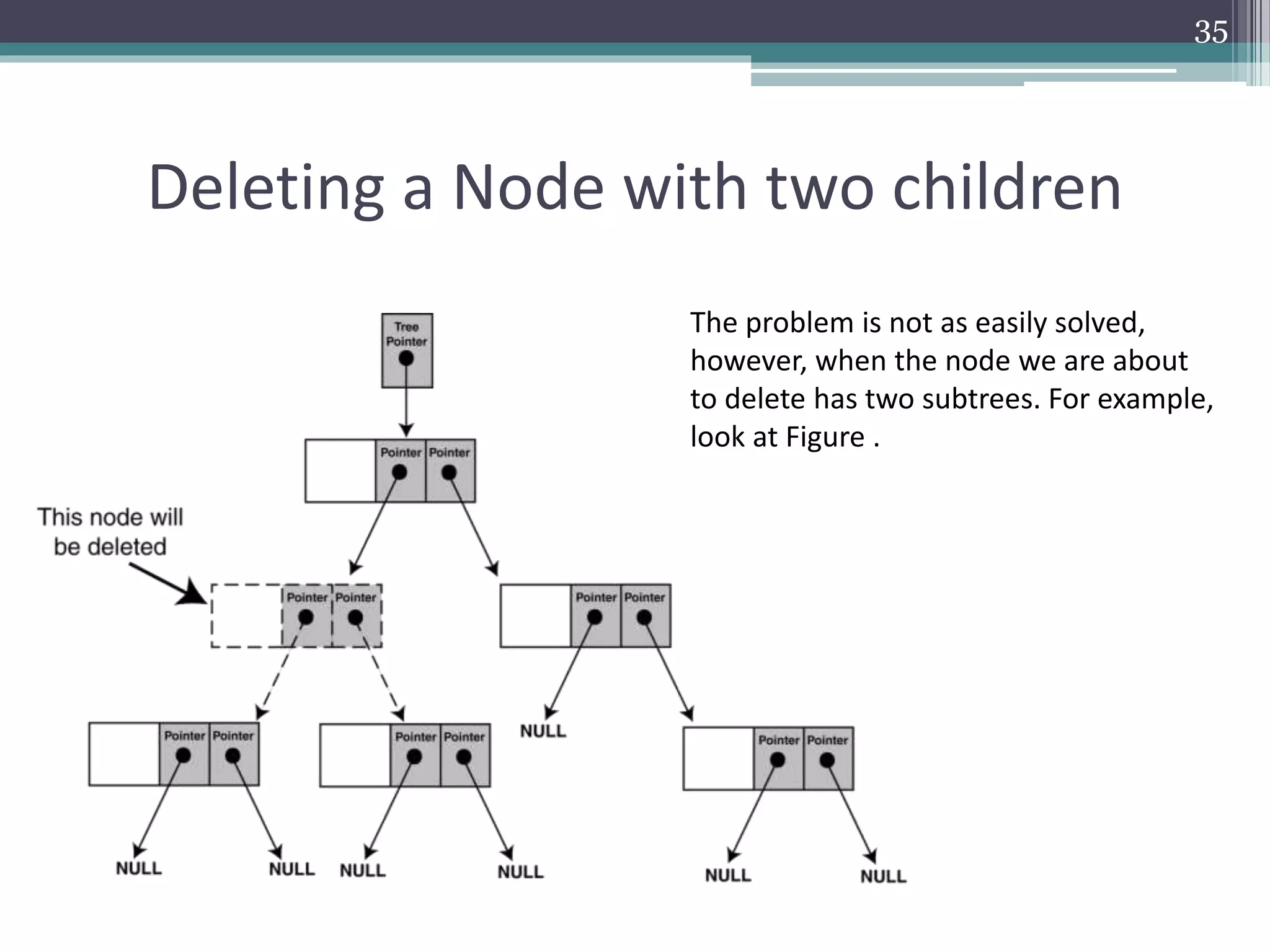
The document provides a comprehensive overview of binary trees, covering their structure, operations, and various traversal methods such as in-order, pre-order, and post-order. It also details explicit algorithms for inserting and deleting nodes in a binary search tree, as well as searching for elements within the tree. Additionally, it discusses special tree types including strictly binary trees and complete binary trees, offering a foundational understanding for programming applications.