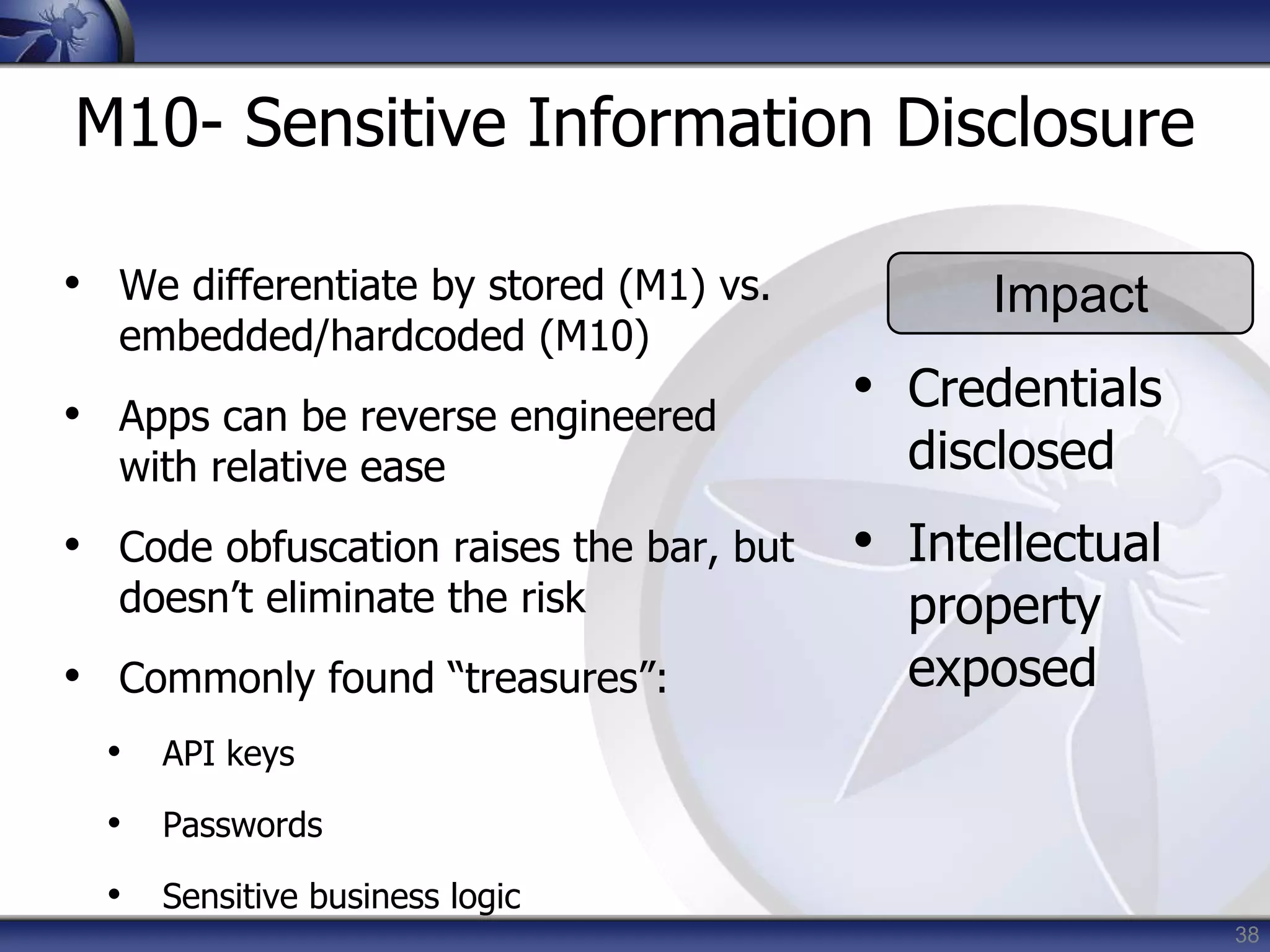
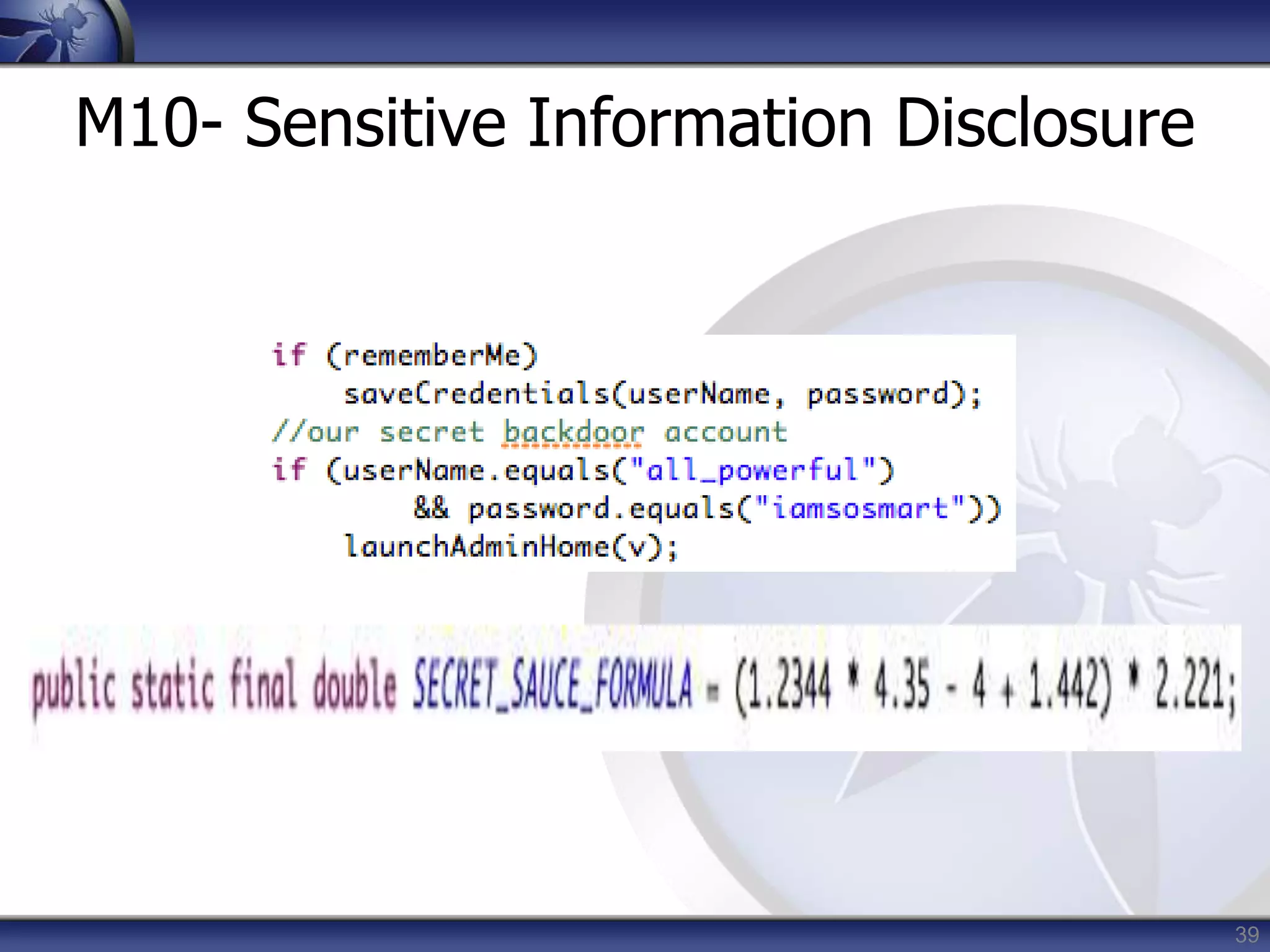
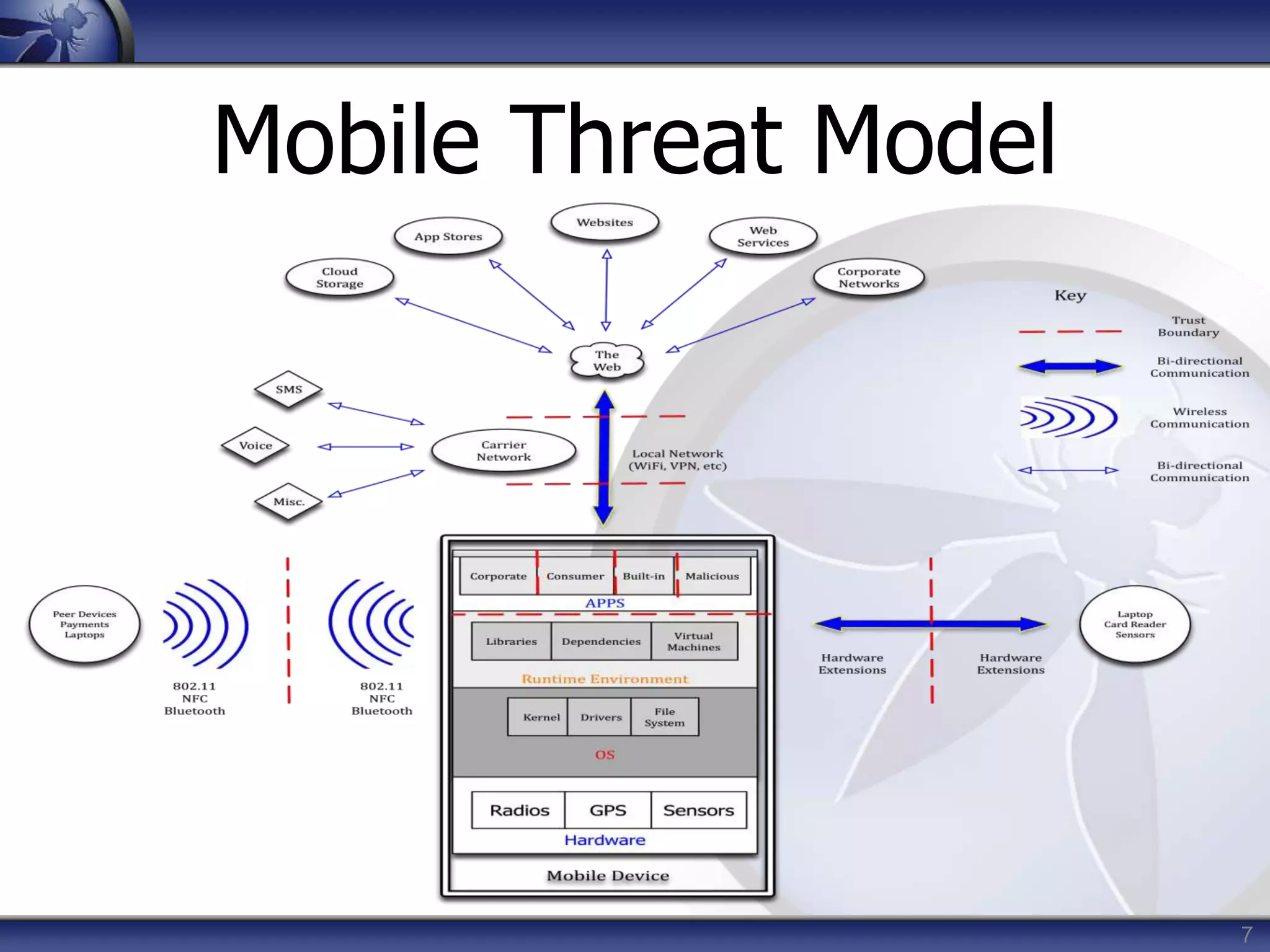
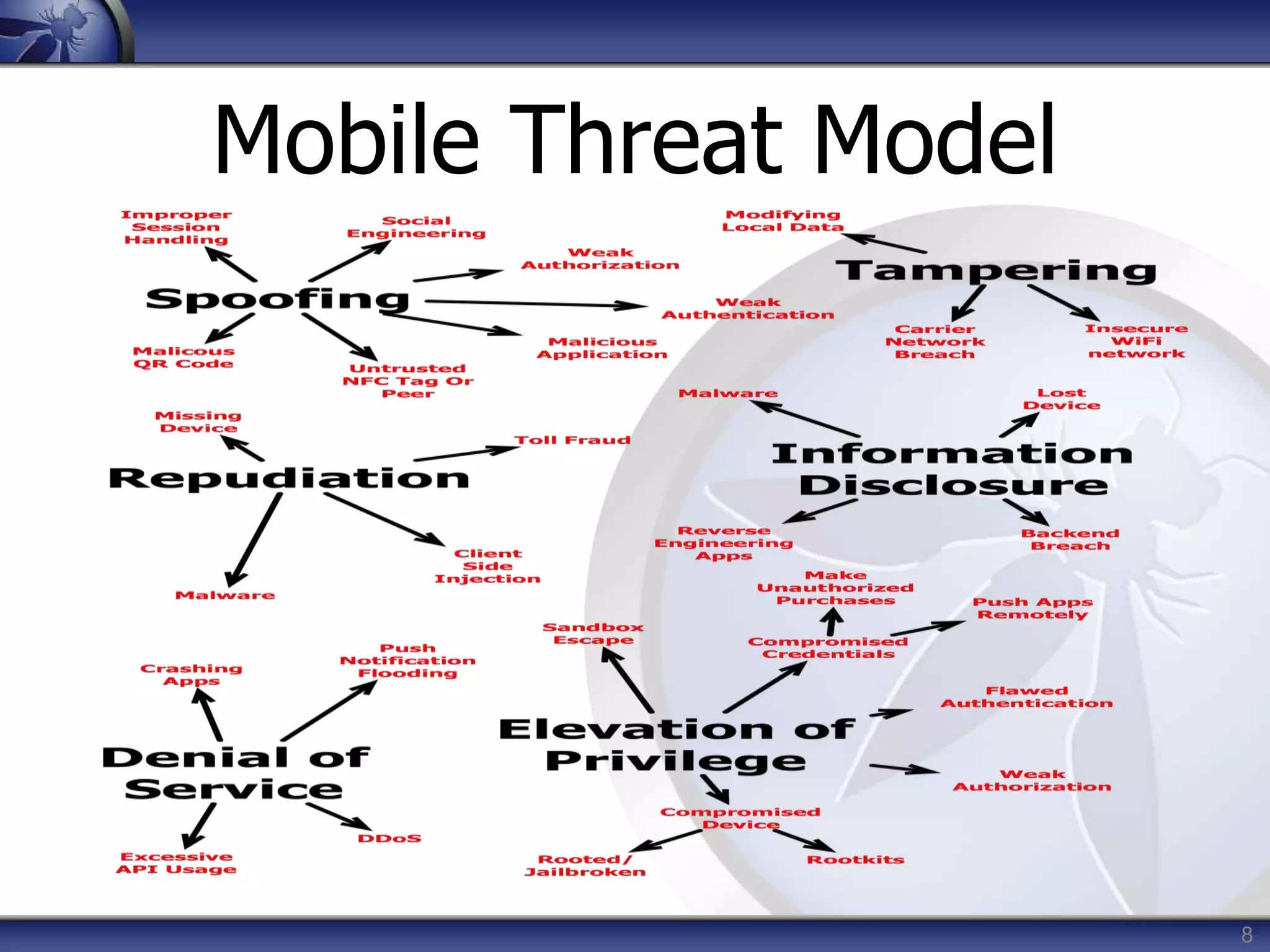
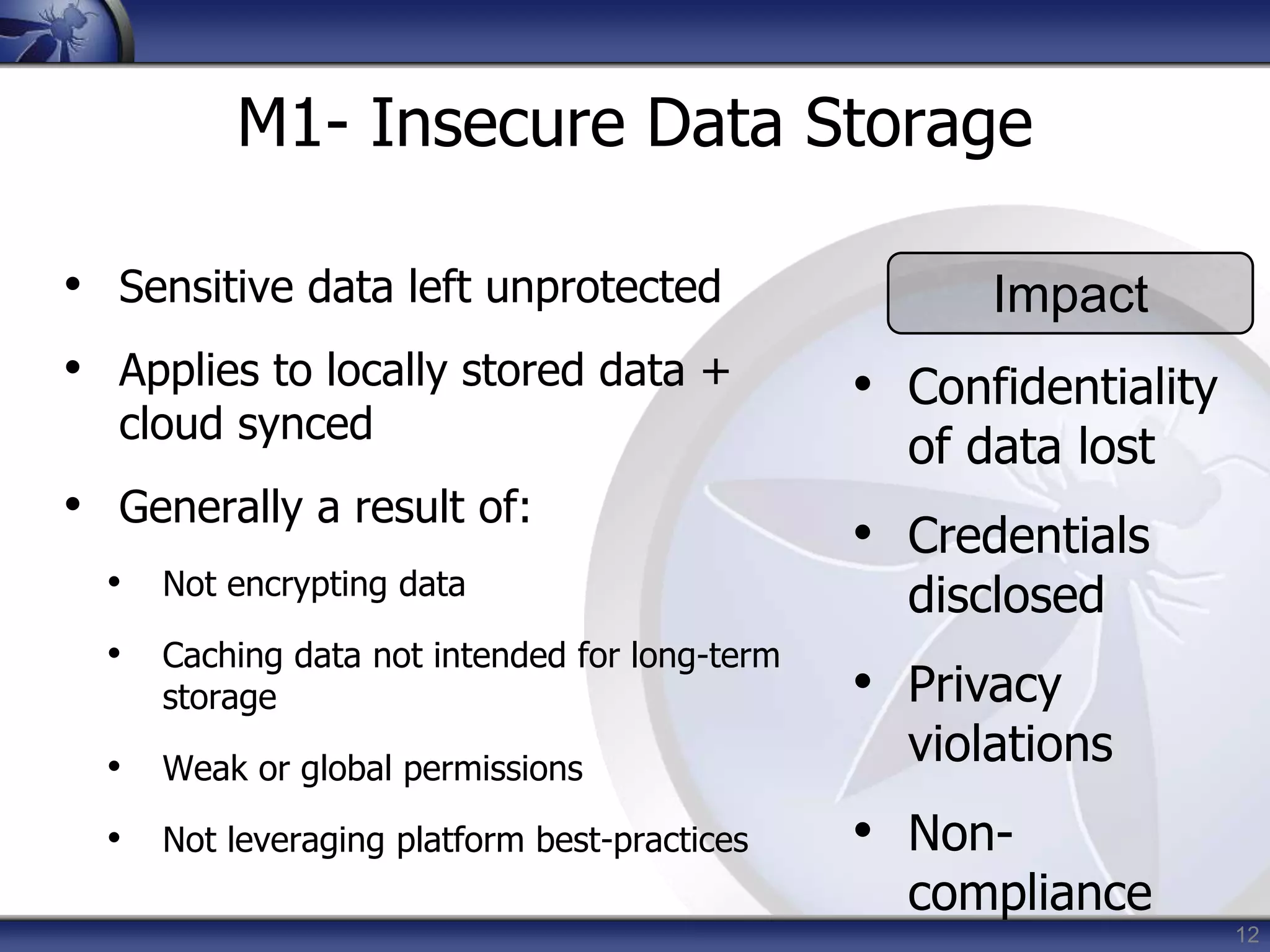
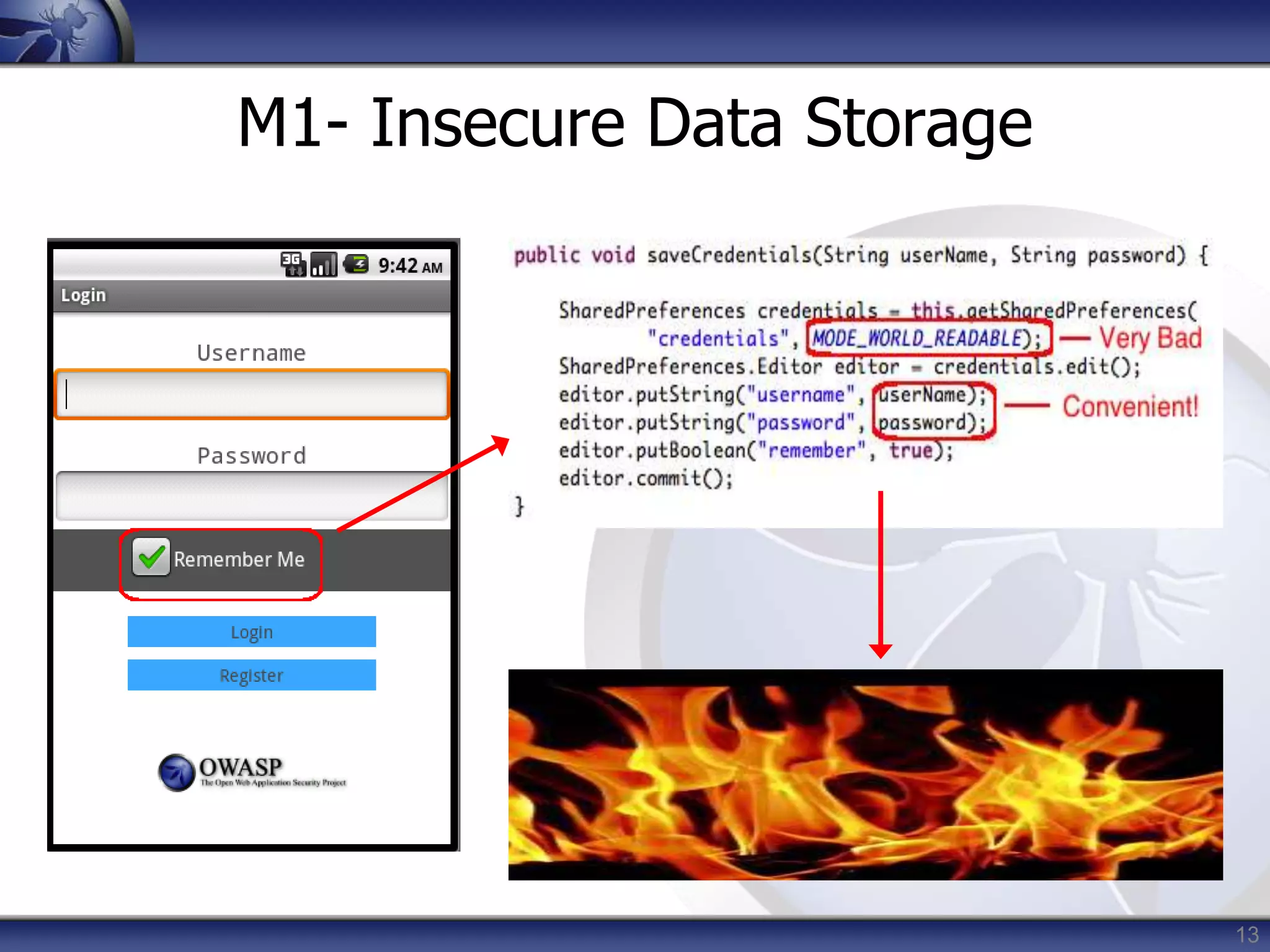
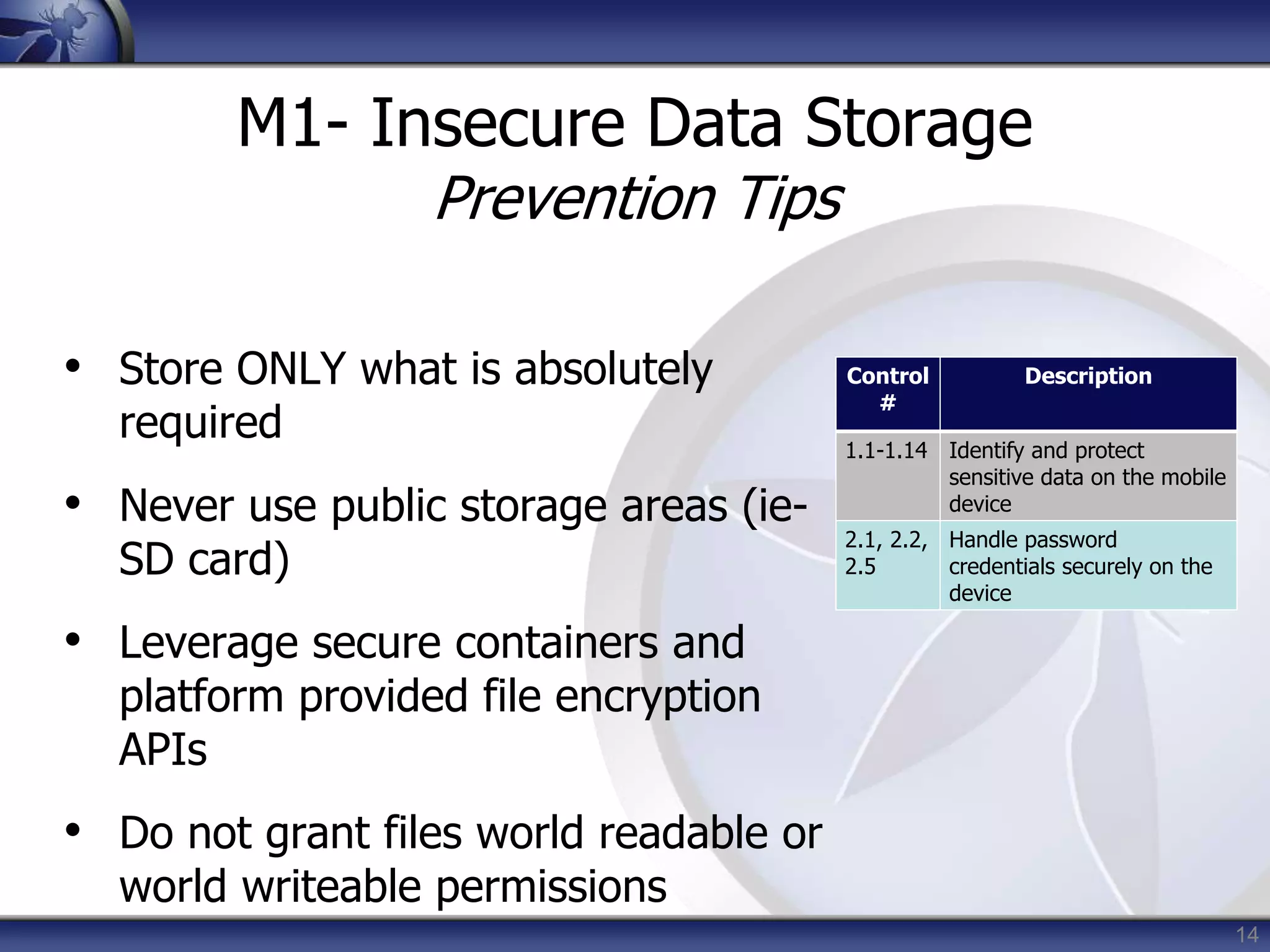
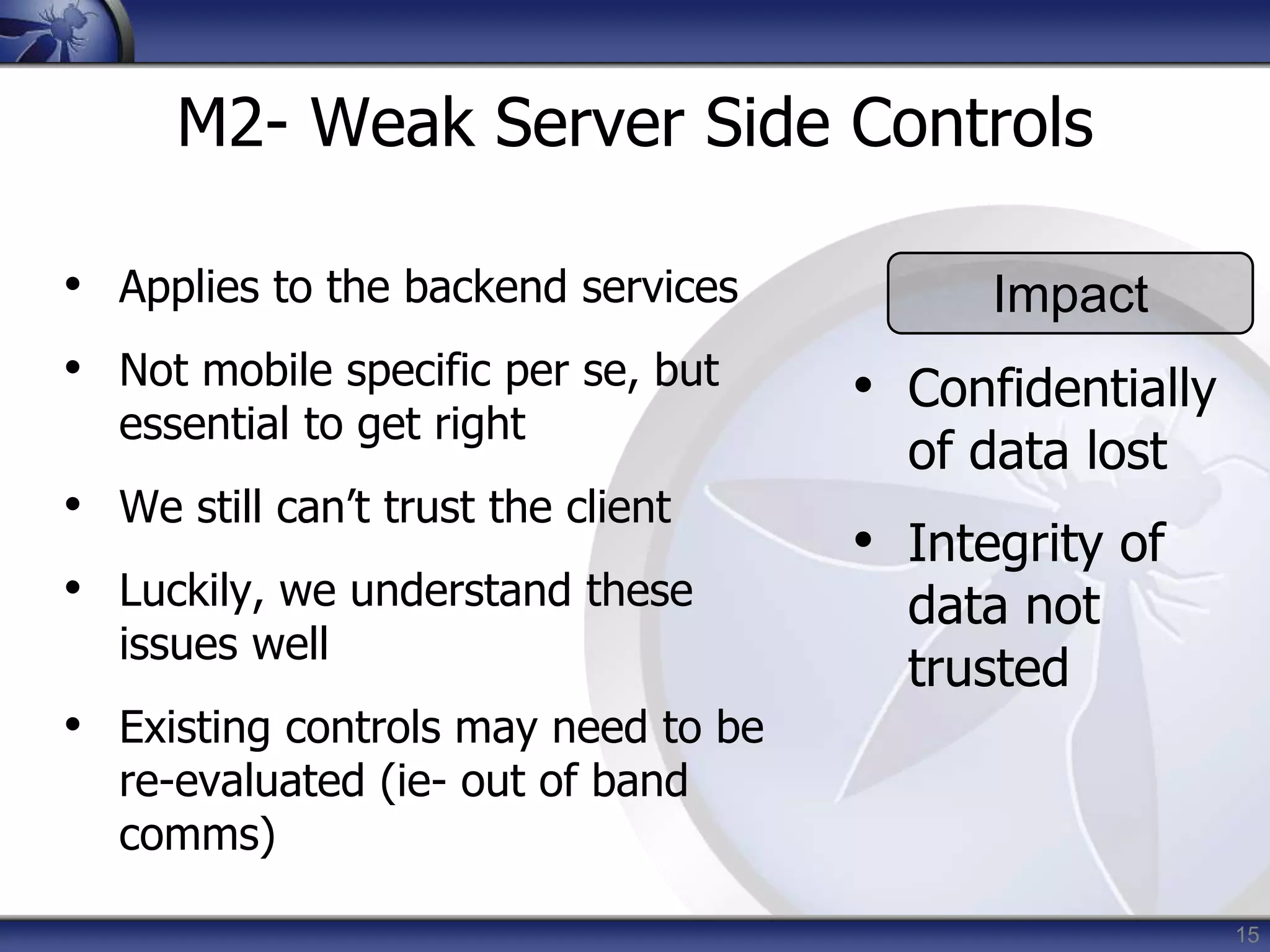
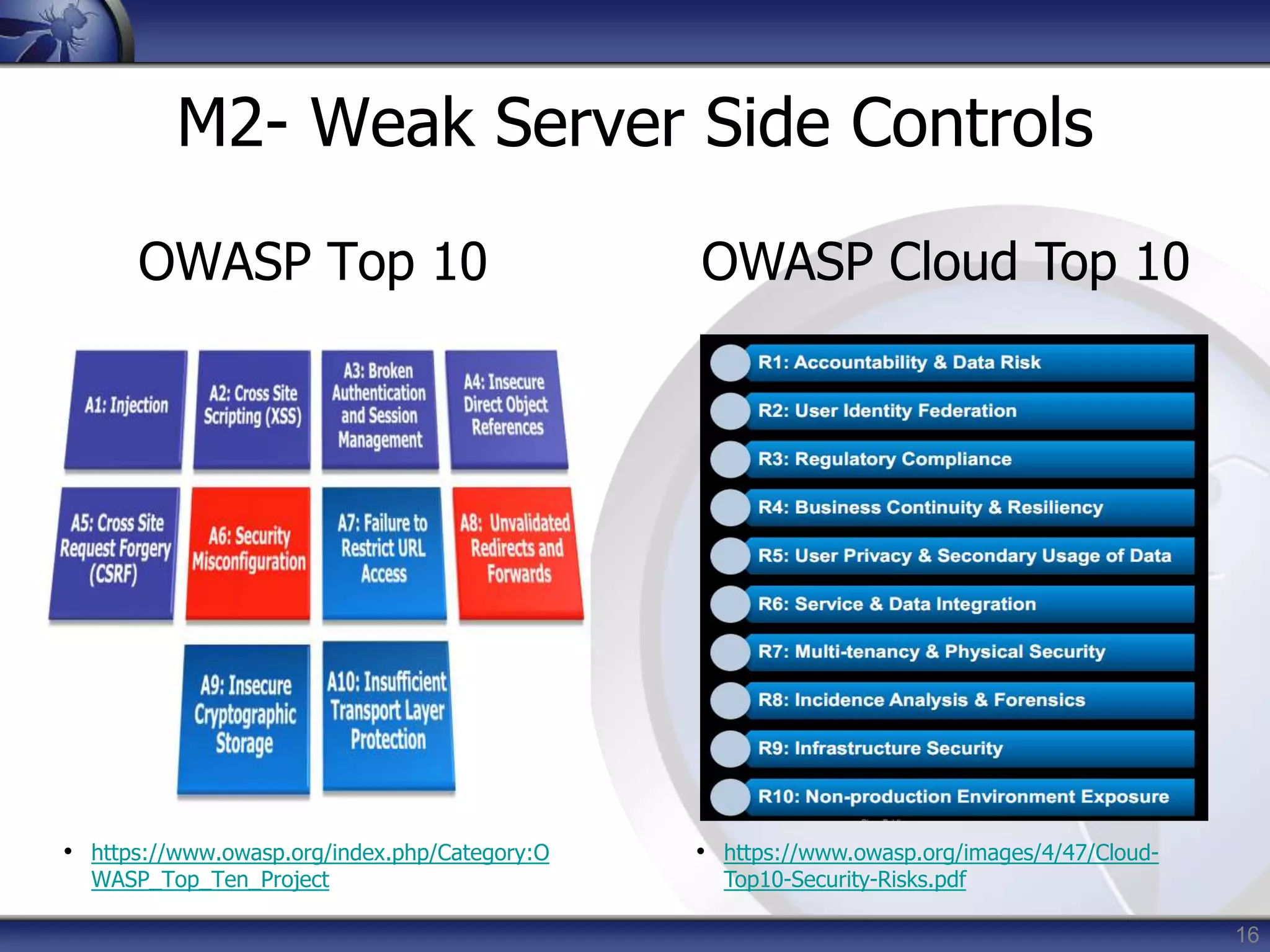
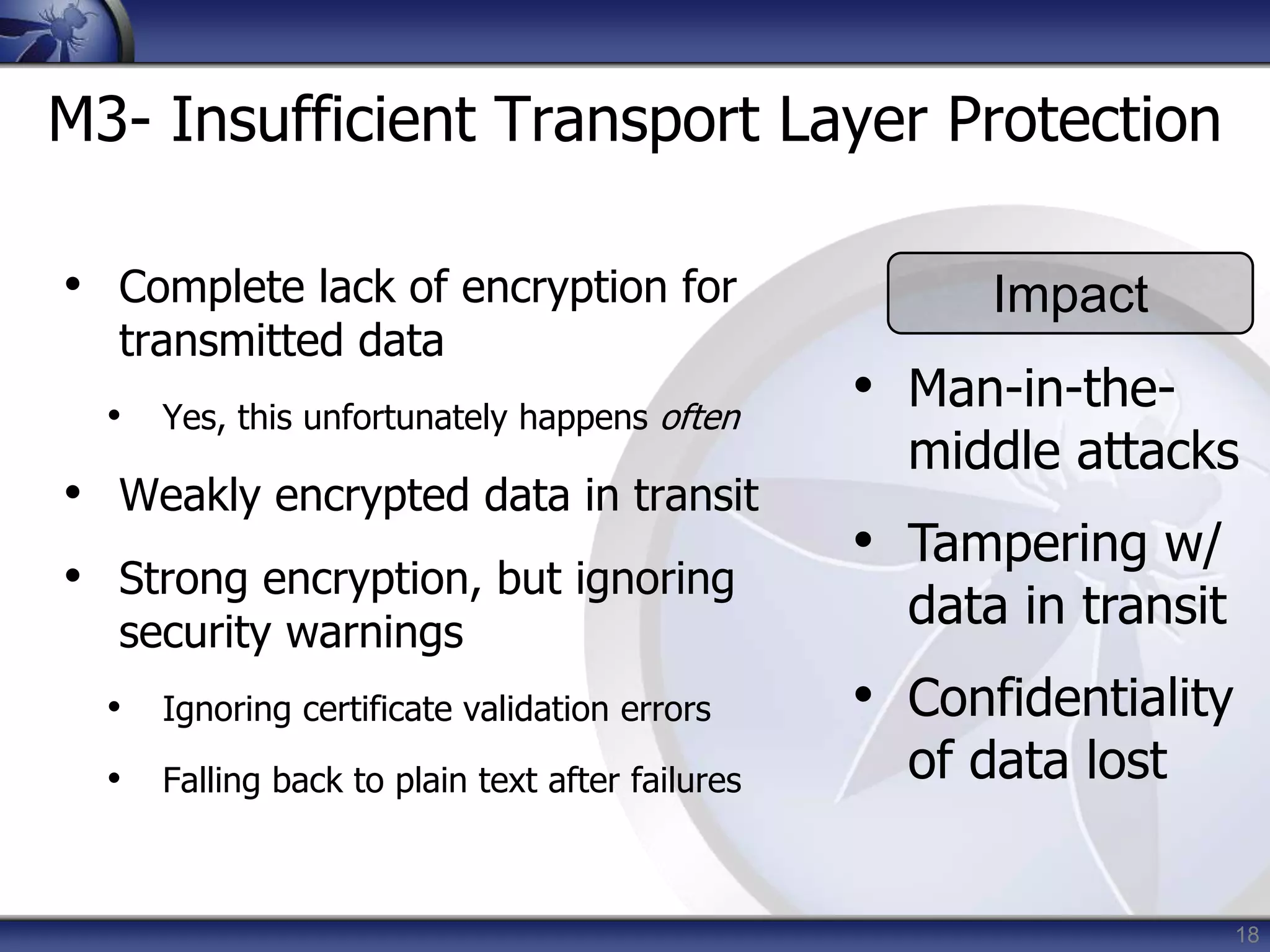
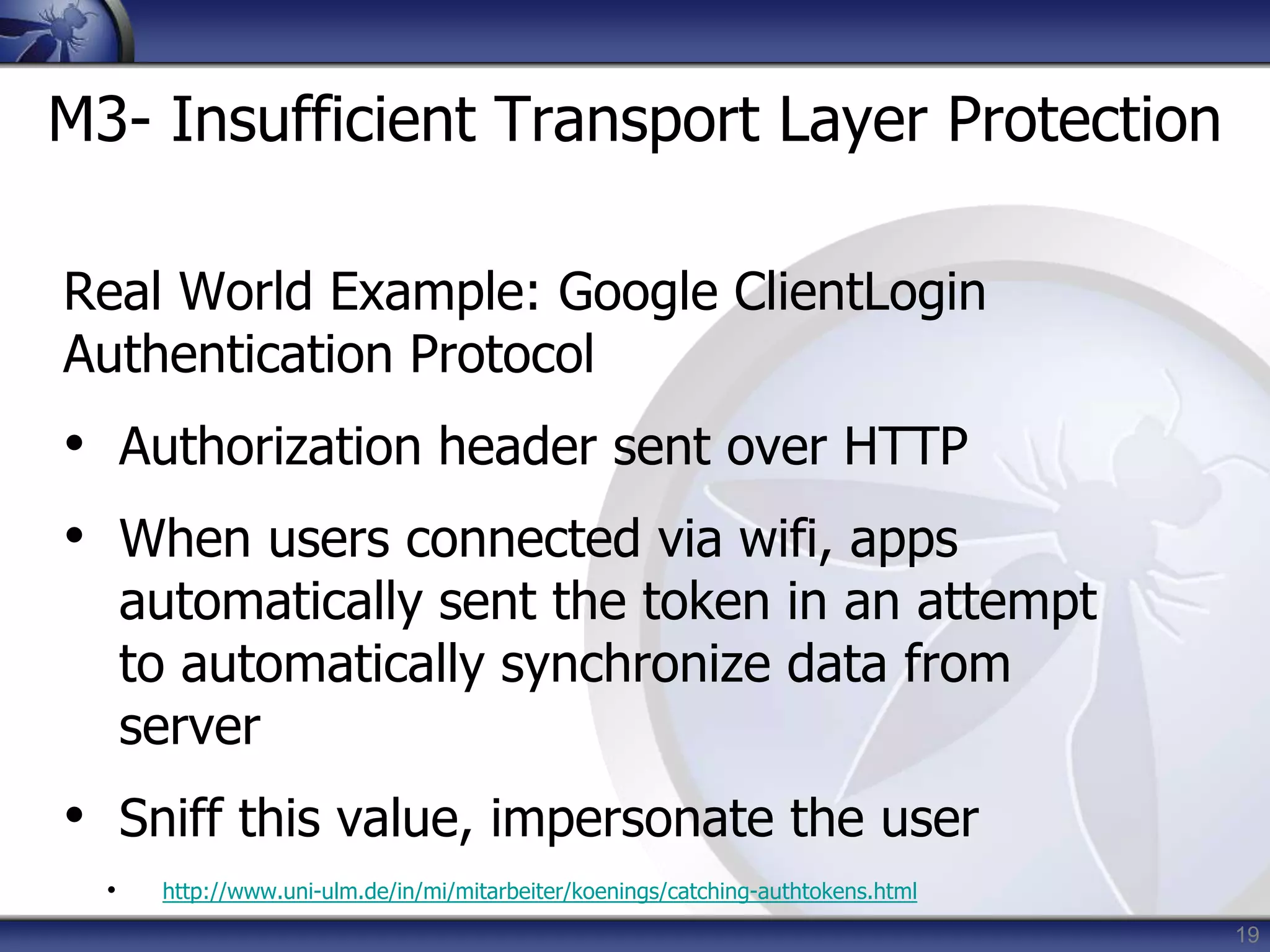
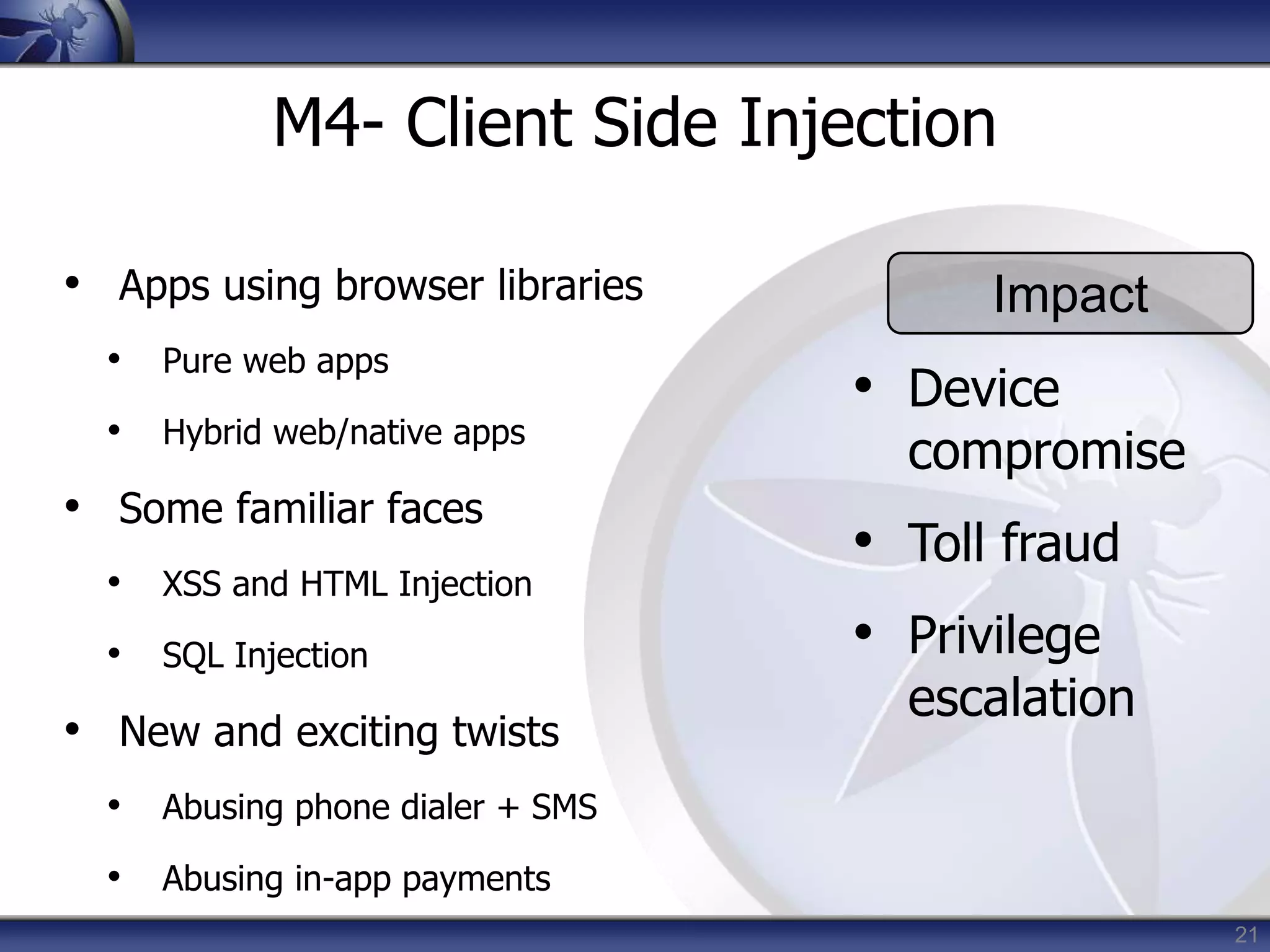
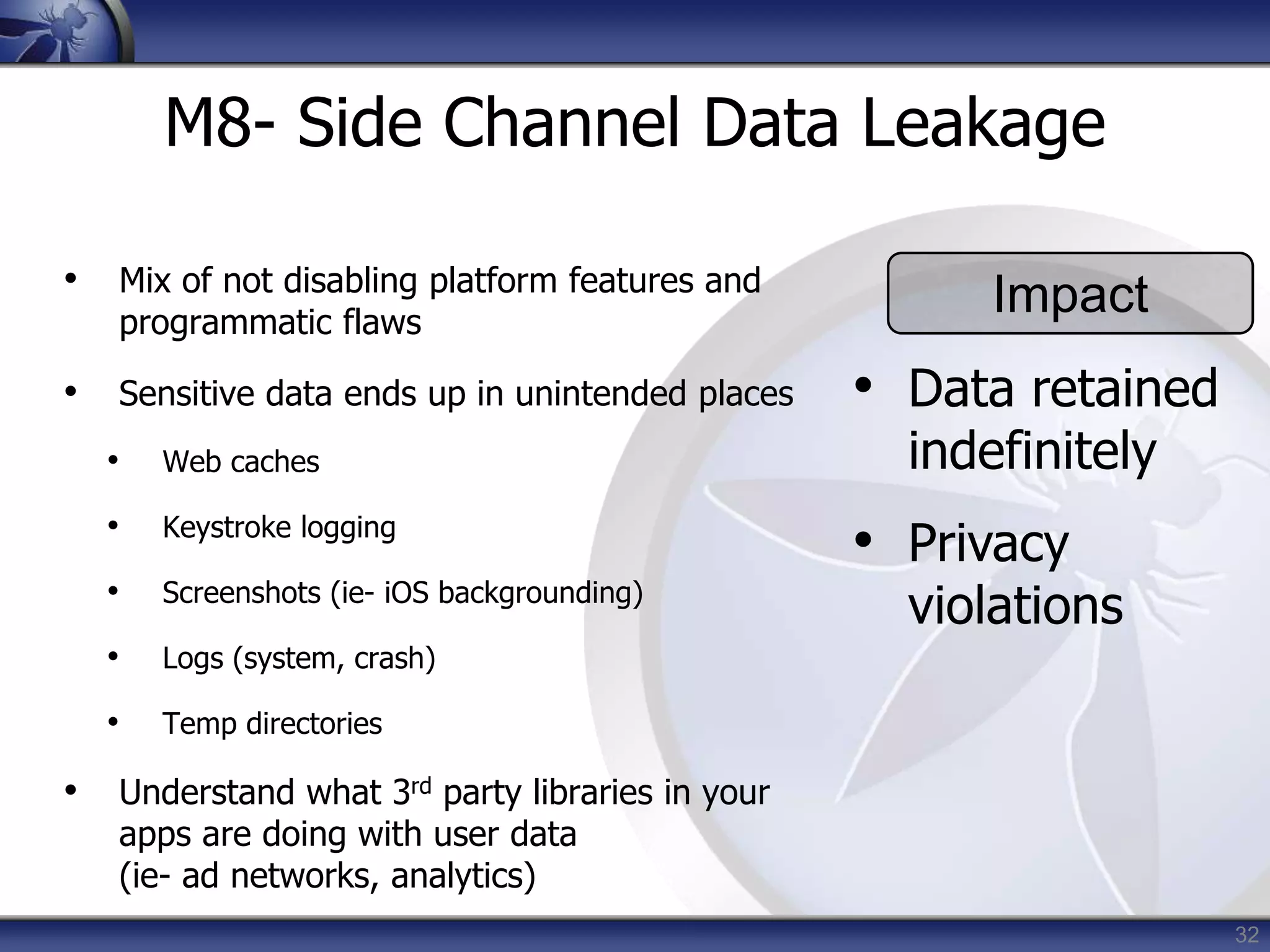
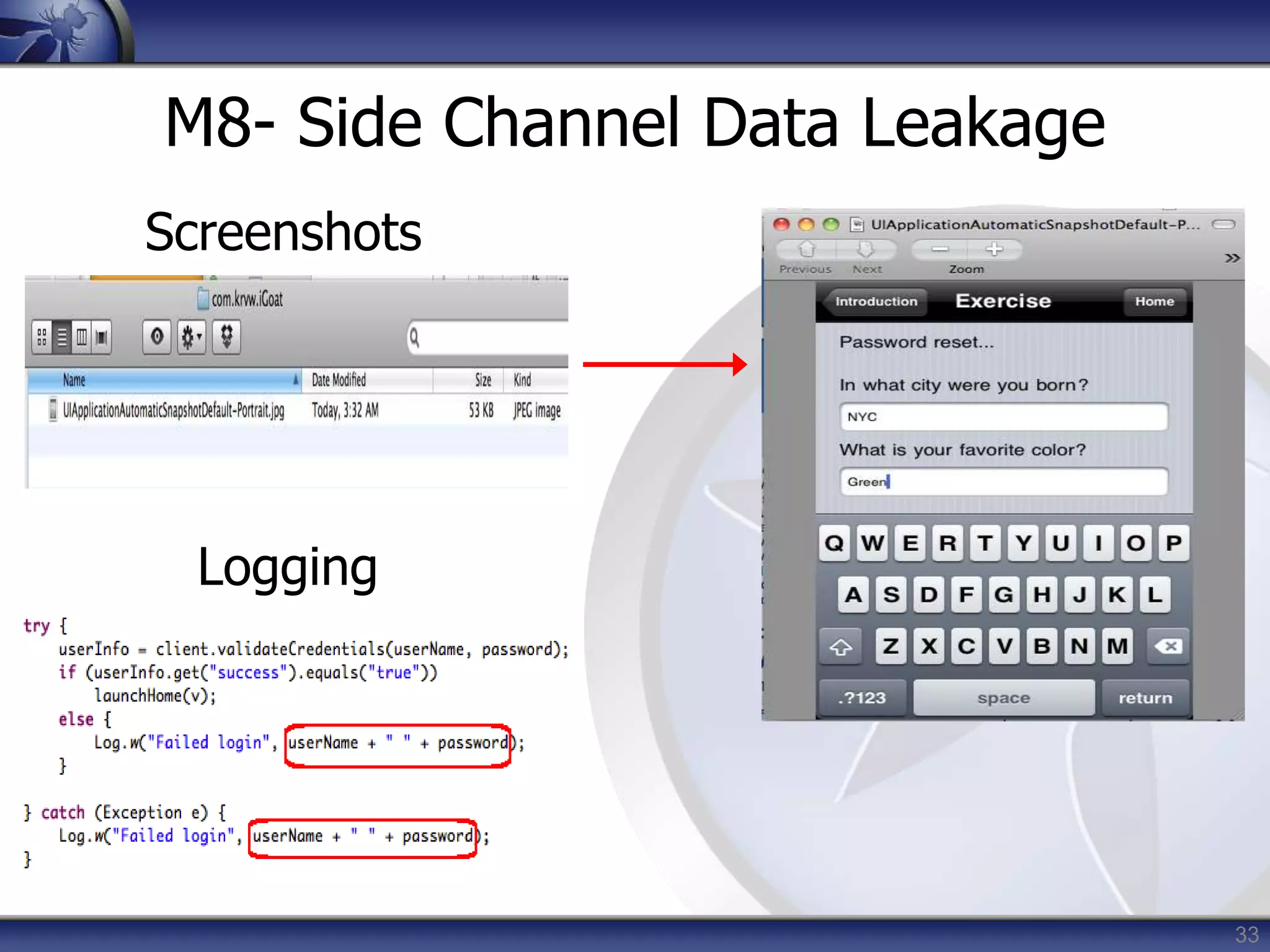
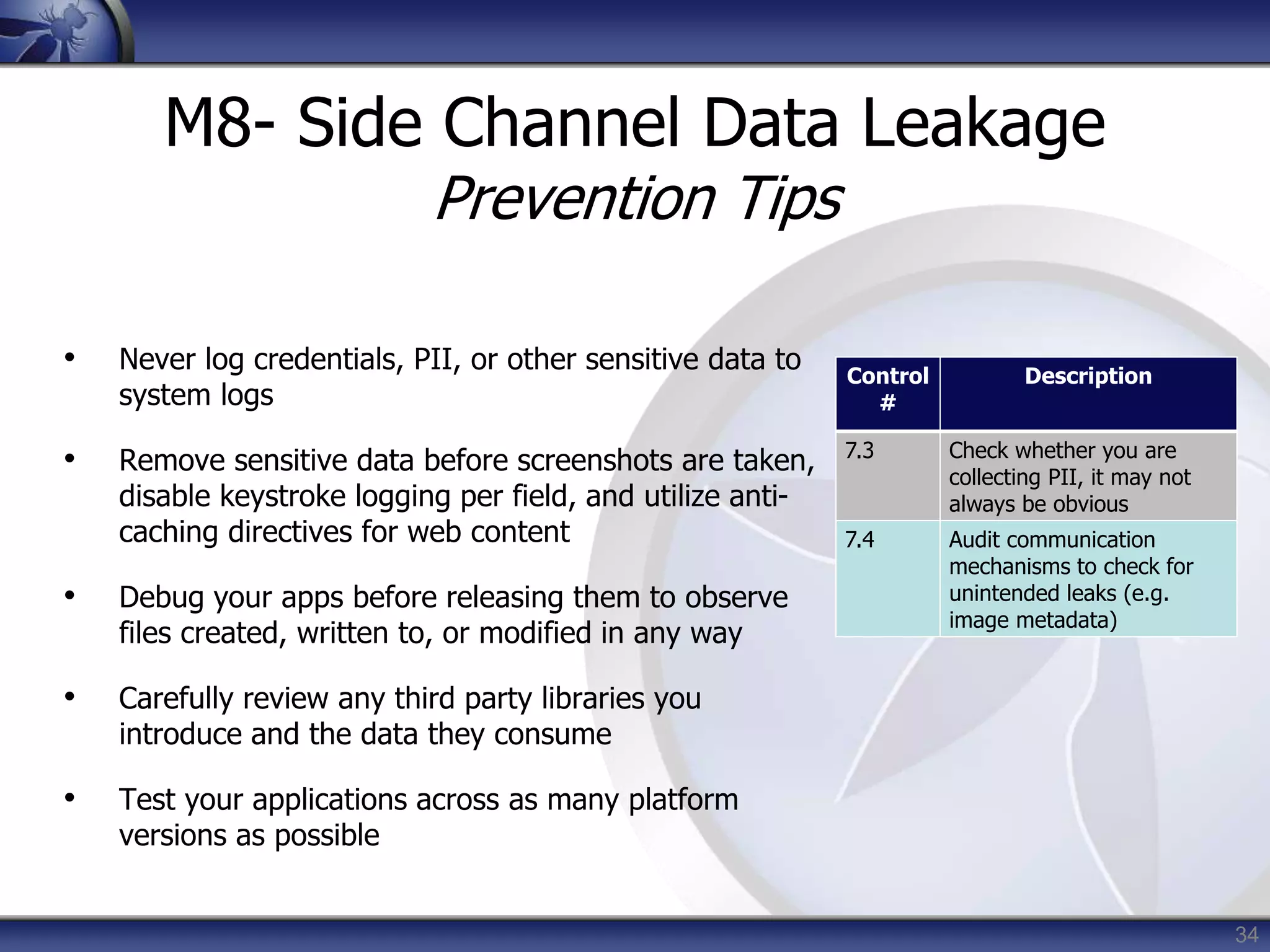
This document summarizes a presentation on mobile application security risks given by Mennouchi Islam Azeddine. The presentation covered the OWASP Mobile Security Project, a mobile threat model, and the top 10 mobile risks. It discussed each risk in the top 10 list, including insecure data storage, weak server-side controls, insufficient transport layer protection, client-side injection, poor authorization and authentication, improper session handling, security decisions via untrusted inputs, side channel data leakage, broken cryptography, and sensitive information disclosure. For each risk, examples were provided and prevention tips were outlined.











![36
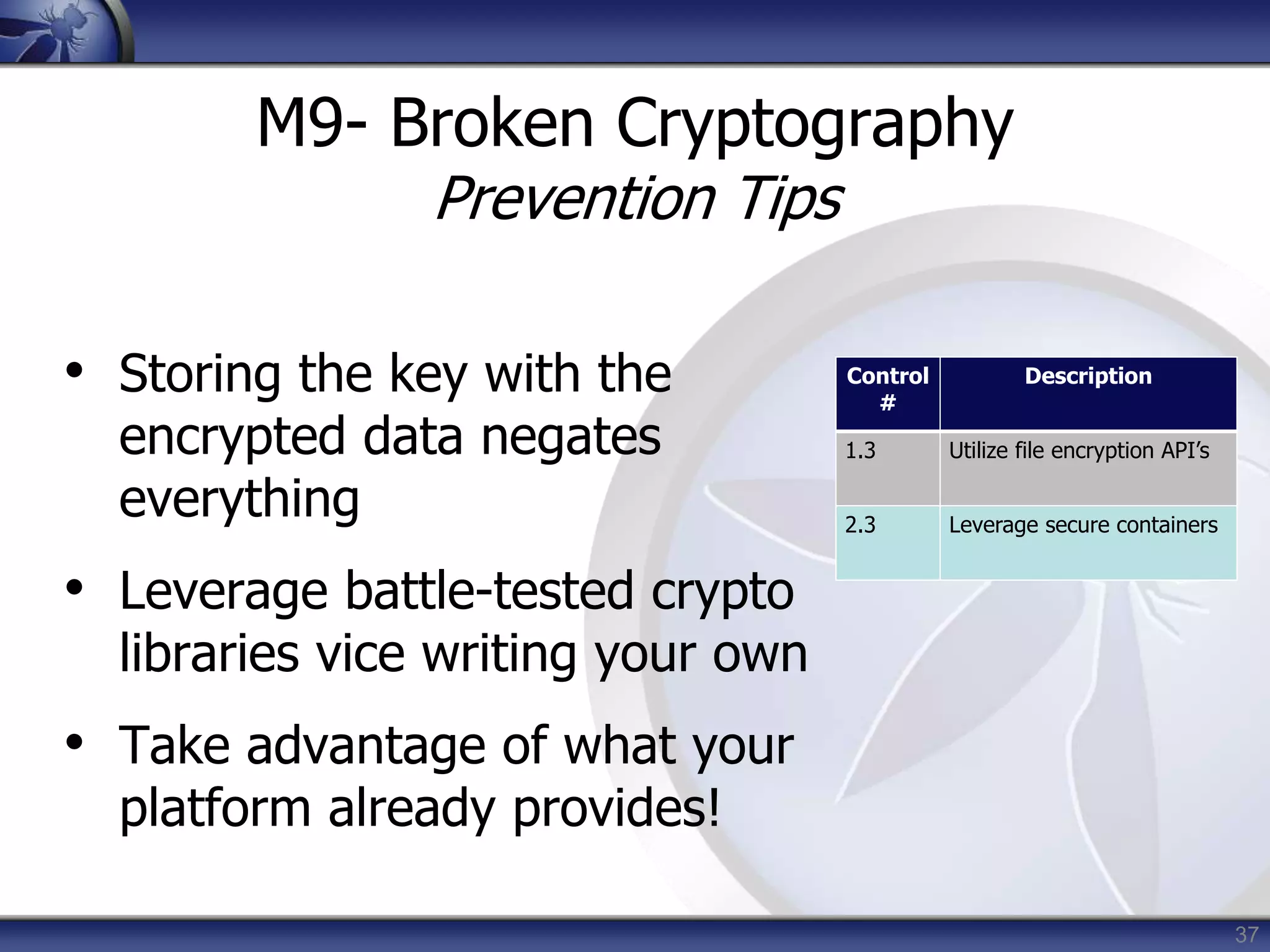
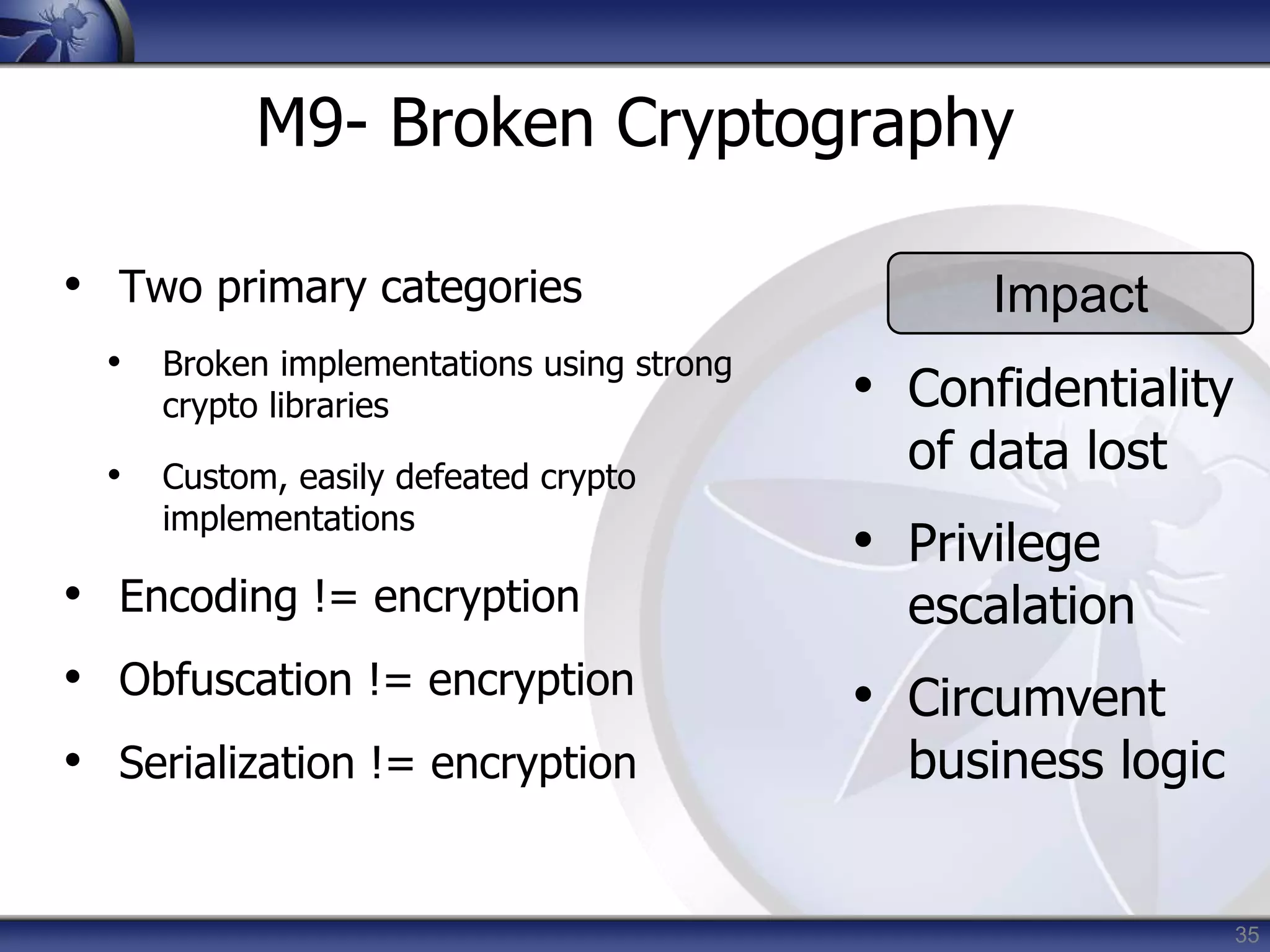
M9- Broken Cryptography
ldc literal_876:"QlVtT0JoVmY2N2E=”
invokestatic byte[] decode( java.lang.String )
invokespecial_lib java.lang.String.<init> //
pc=2
astore 8
private final byte[]
com.picuploader.BizProcess.SendRequest.routine_
12998
(com.picuploader.BizProcess.SendRequest,
byte[], byte[] );
{
enter
new_lib
net.rim.device.api.crypto.TripleDESKey](https://image.slidesharecdn.com/webdaysblida-mobiletop10risks-140310095703-phpapp01/75/Webdays-blida-mobile-top-10-risks-36-2048.jpg)