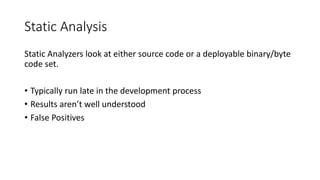
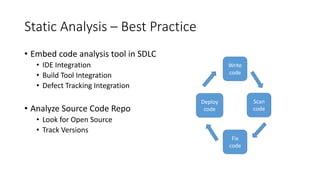
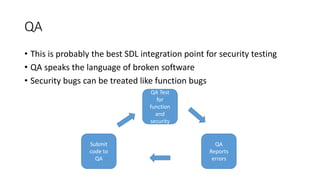
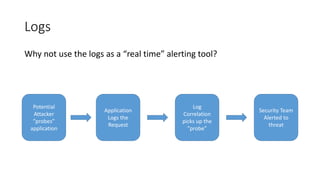
The document discusses improving application security without reliance on additional tools by integrating existing resources like dynamic and static analysis. It emphasizes the importance of collaboration between security tools and development processes, encouraging practices like continuous integration and effective QA testing. Key takeaways include implementing dynamic scanning for security configurations and best practices for static analysis to identify vulnerabilities early in the development lifecycle.







![Dynamic Scanning – WAF Tuning
• Most DAST vendors output XML
• WAF vendors usually work with the DAST vendor
• ModSecurity WAF rule generator (Commercial Version)
Dynamic Scan
?name=<script
>alert({token})
</script>
WAF
param name
{'/^[a-zA-Z]+$/’}
Application
server
XML Data stream](https://image.slidesharecdn.com/kentjason-infosecsummit-160408011414/85/Jason-Kent-AppSec-Without-Additional-Tools-9-320.jpg)