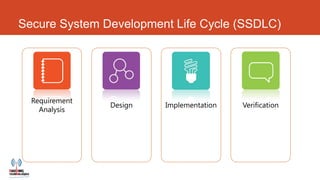
Meenu Dogra is a software engineer who specializes in secure coding and application development. She holds an Oracle Certified Associate certification and gives webinars on security topics. Her document discusses the importance of online security for businesses and developers. It introduces the Secure System Development Life Cycle (SSDLC) as a method to incorporate security at all stages of developing software systems, from requirements analysis to verification. The SSDLC aims to address vulnerabilities that could otherwise pose risks to an organization's online operations and security.