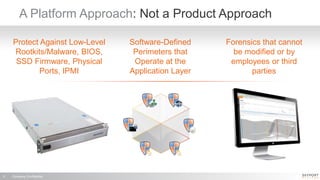
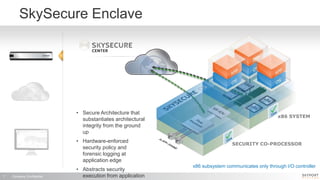
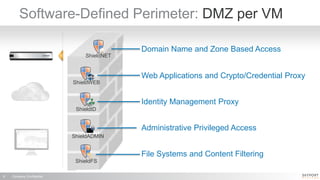
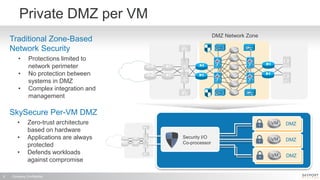
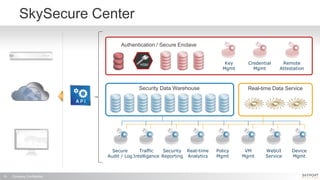
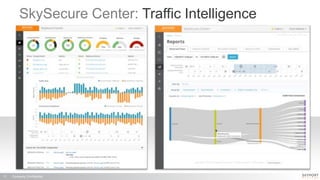
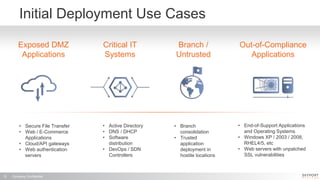
The document outlines a high-performance, secure enterprise platform by Skyport Systems, which employs a software-defined perimeter approach to enhance security against various threats. It emphasizes the integration of trusted hardware, a hardened software stack, and a no-performance-compromise design tailored for hostile environments while defining a zero-trust architecture. Use cases include secure file transfer and web applications in compliance-suspect scenarios, demonstrating the platform's effectiveness in protecting workloads and applications.