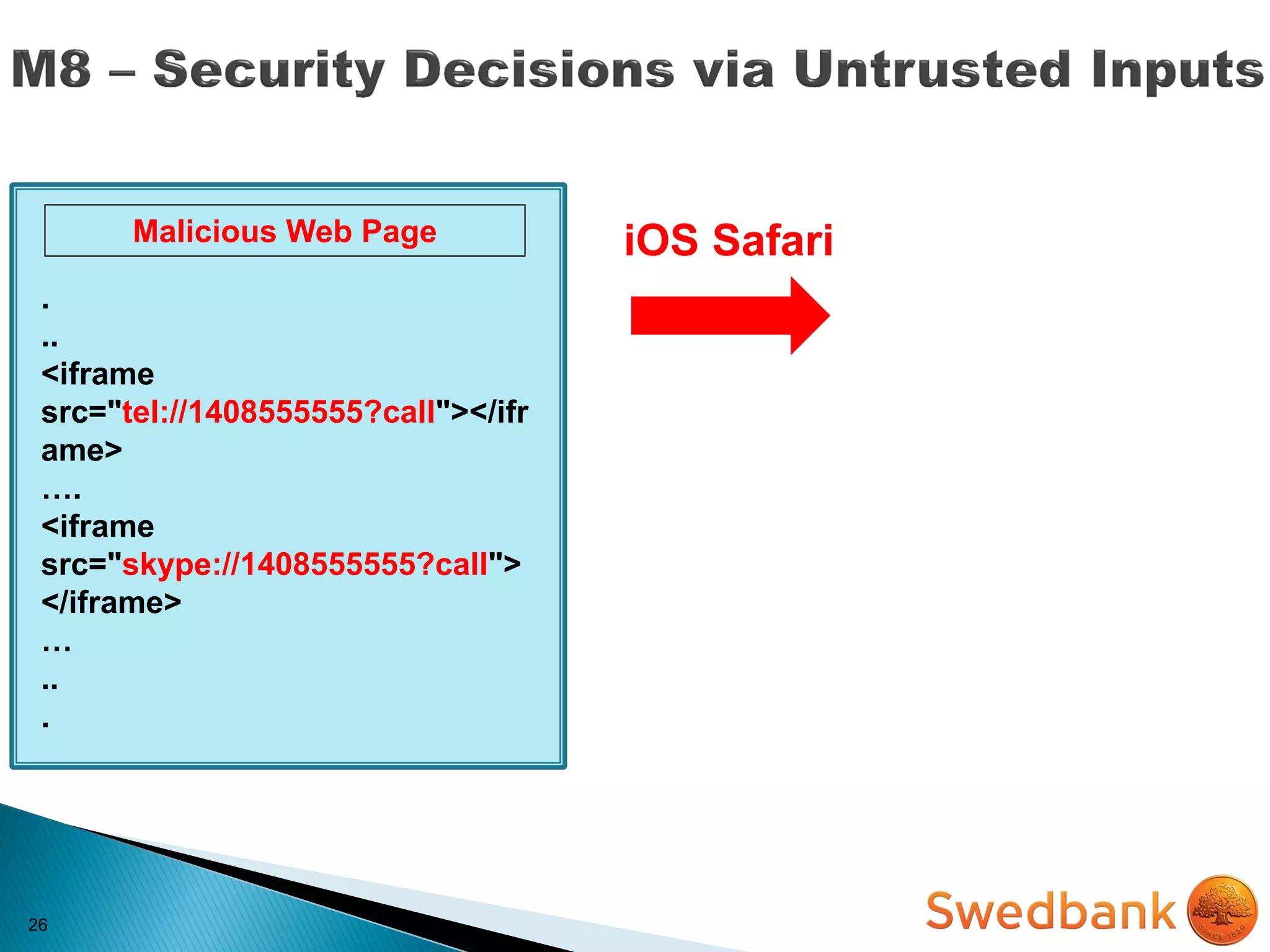
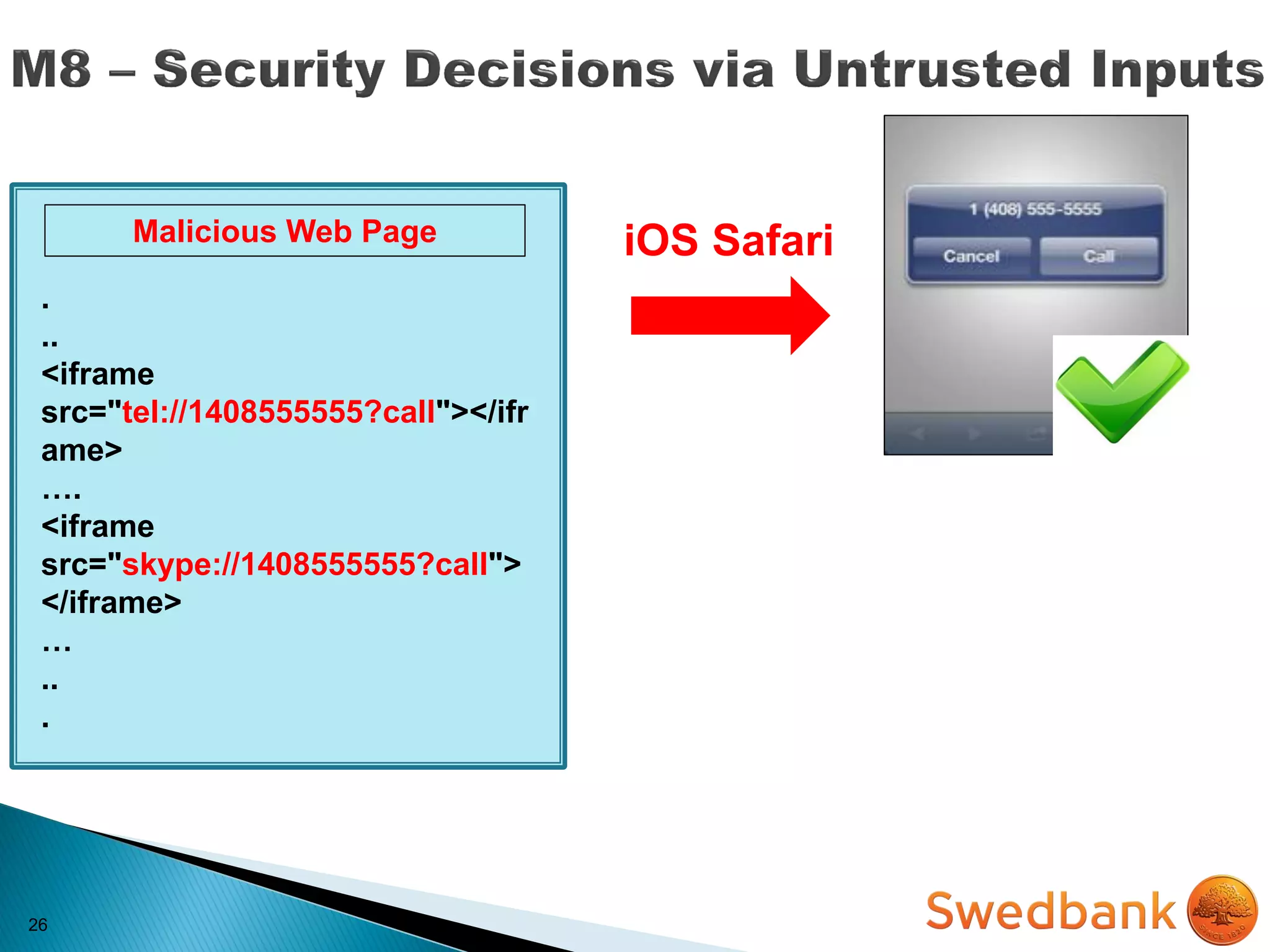
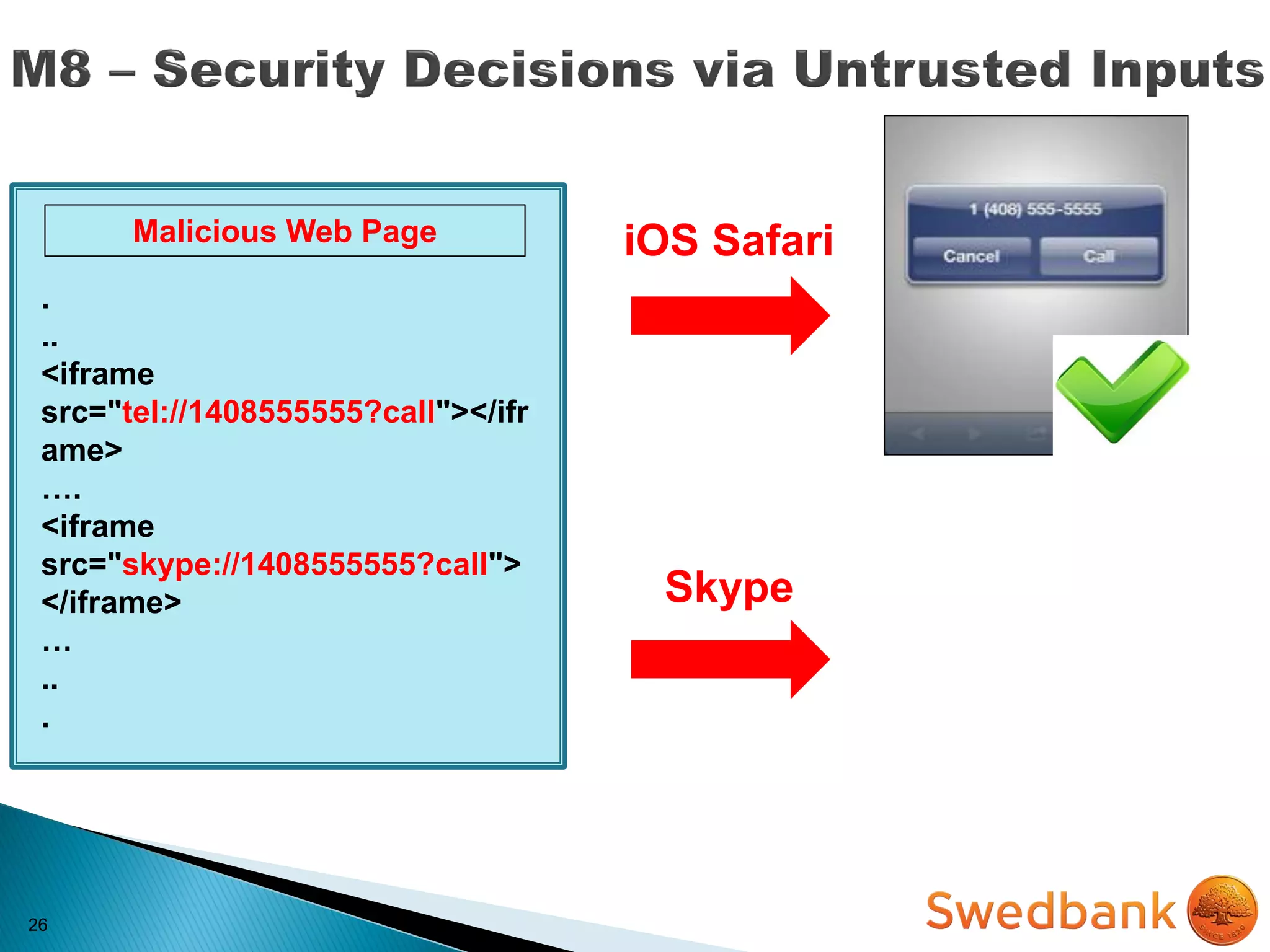
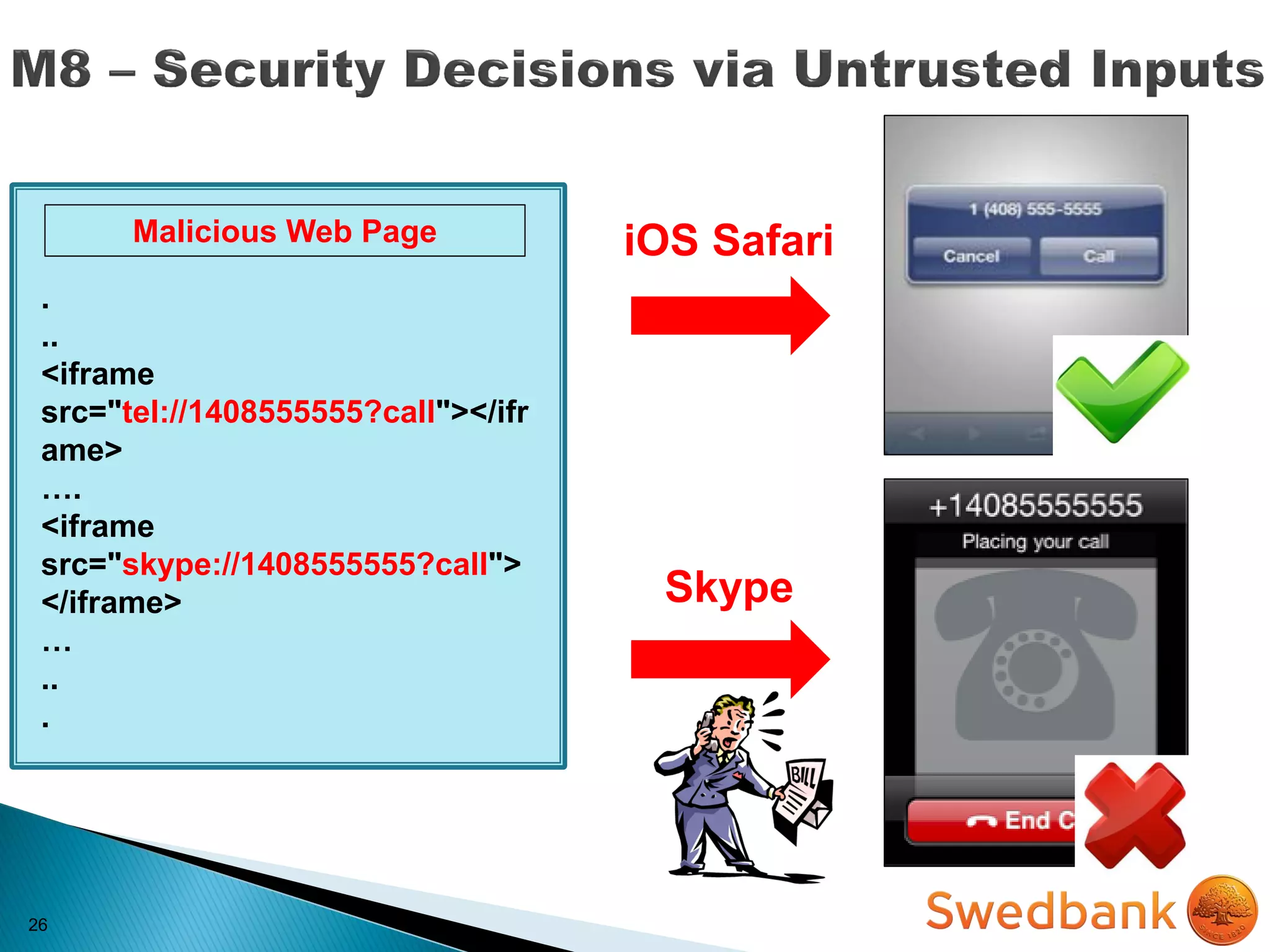
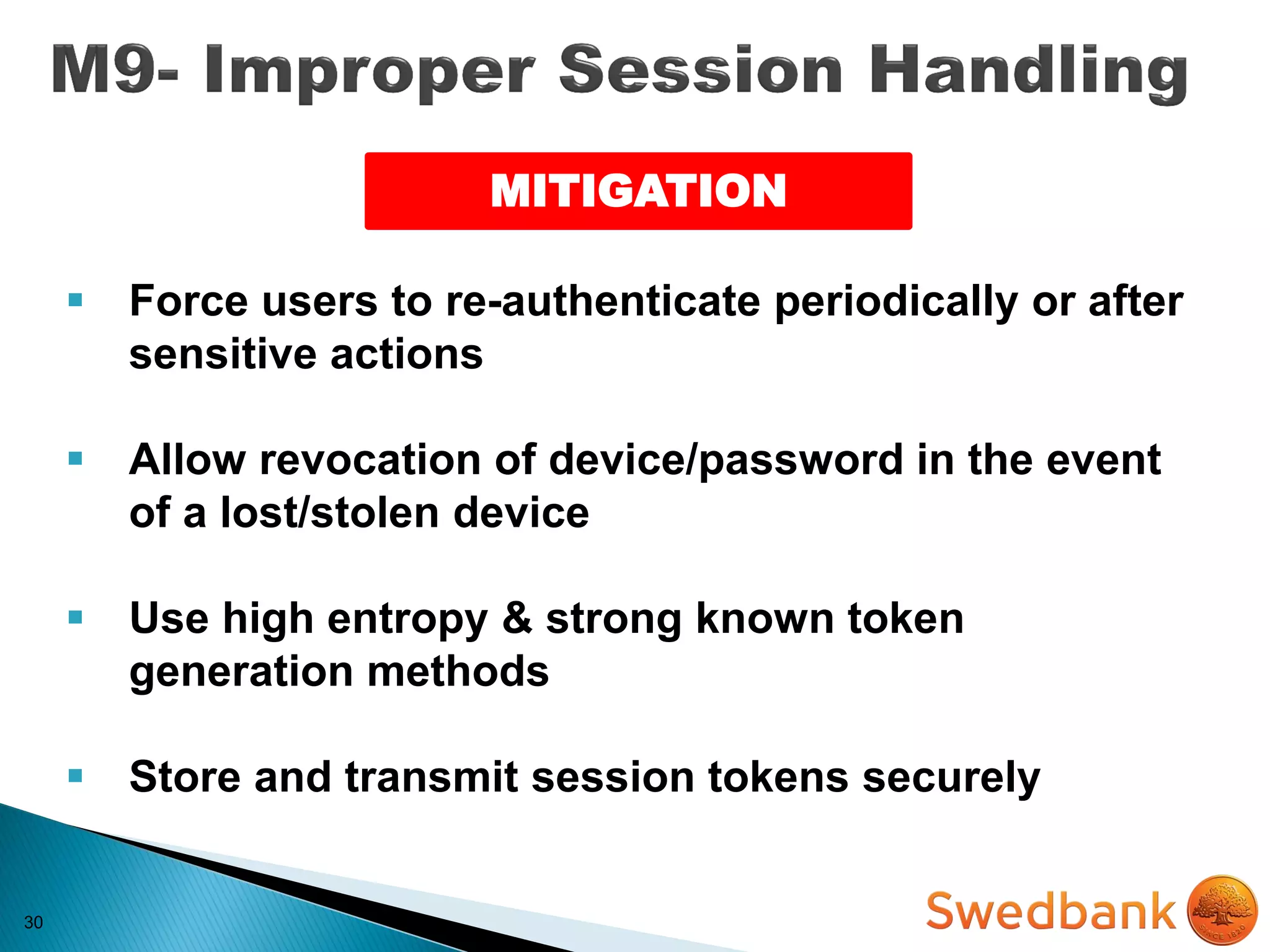
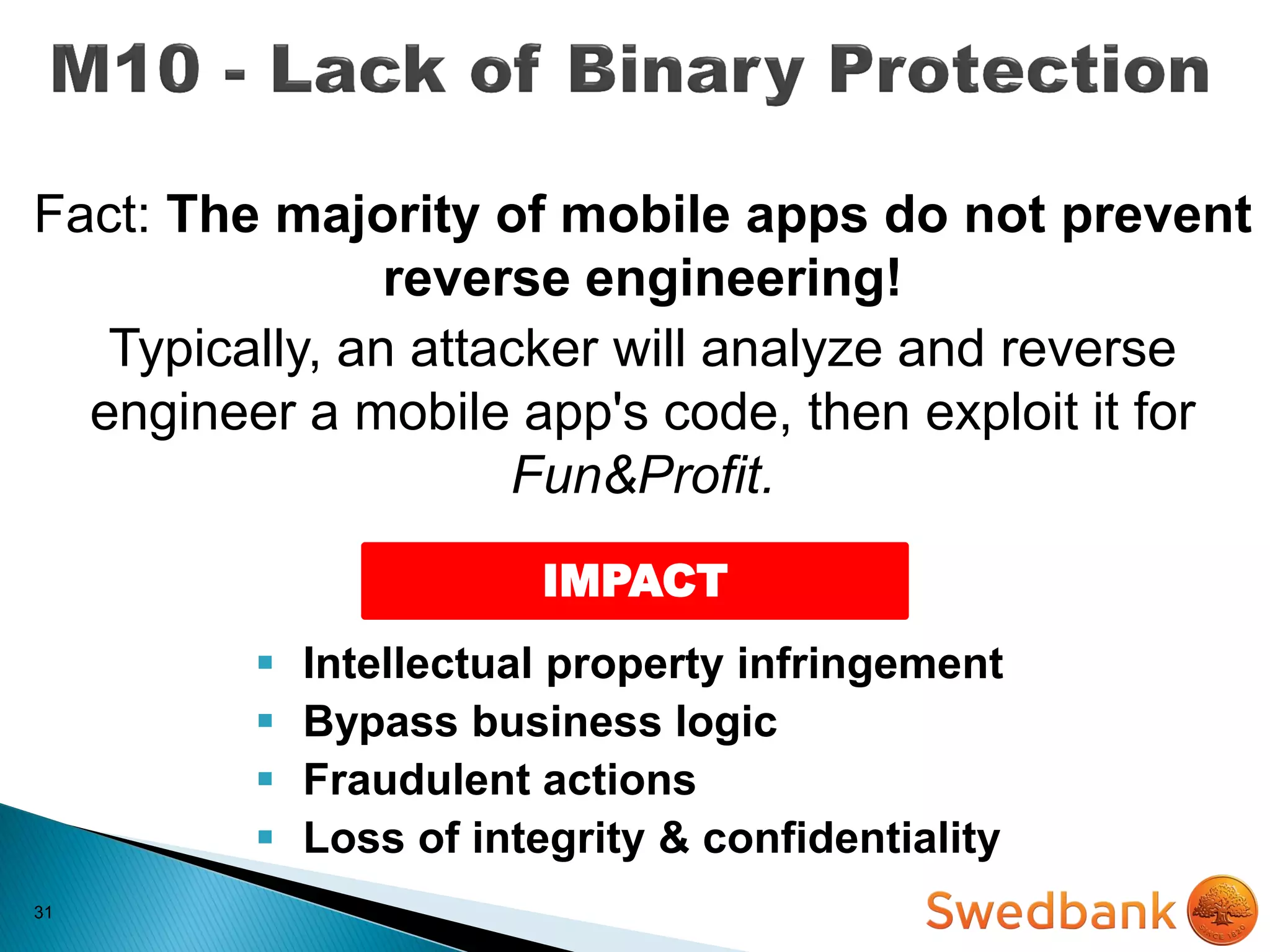
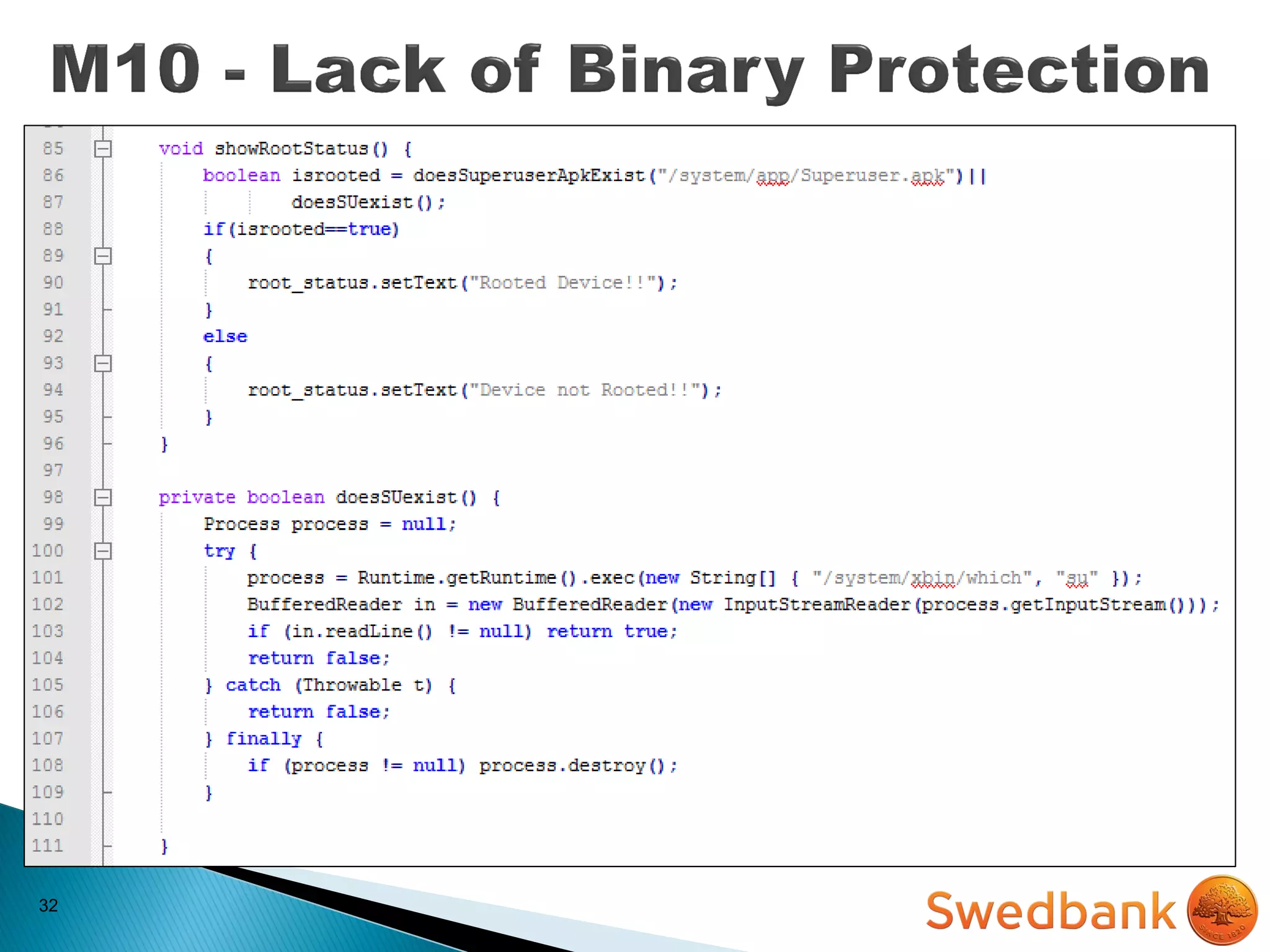
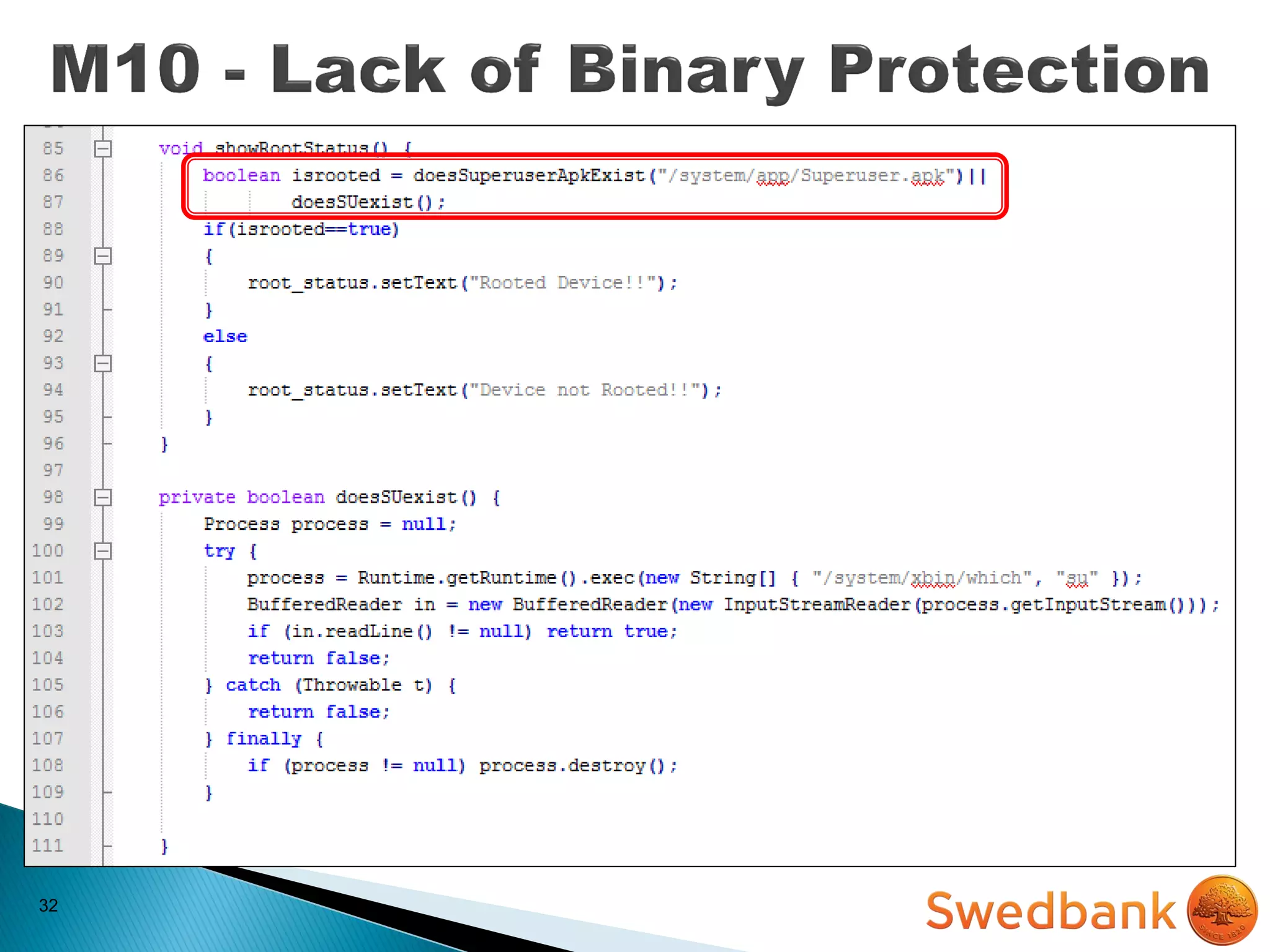
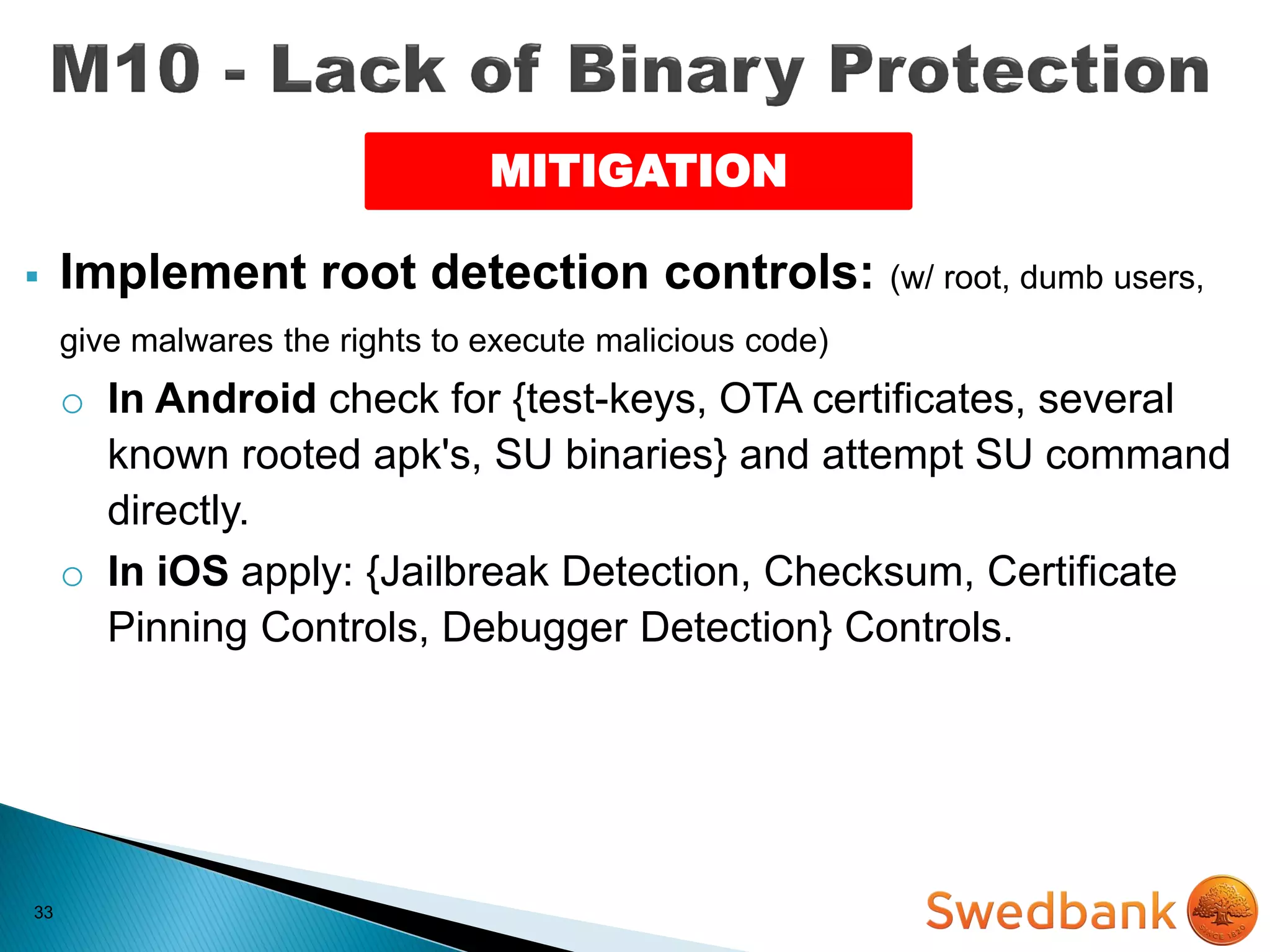
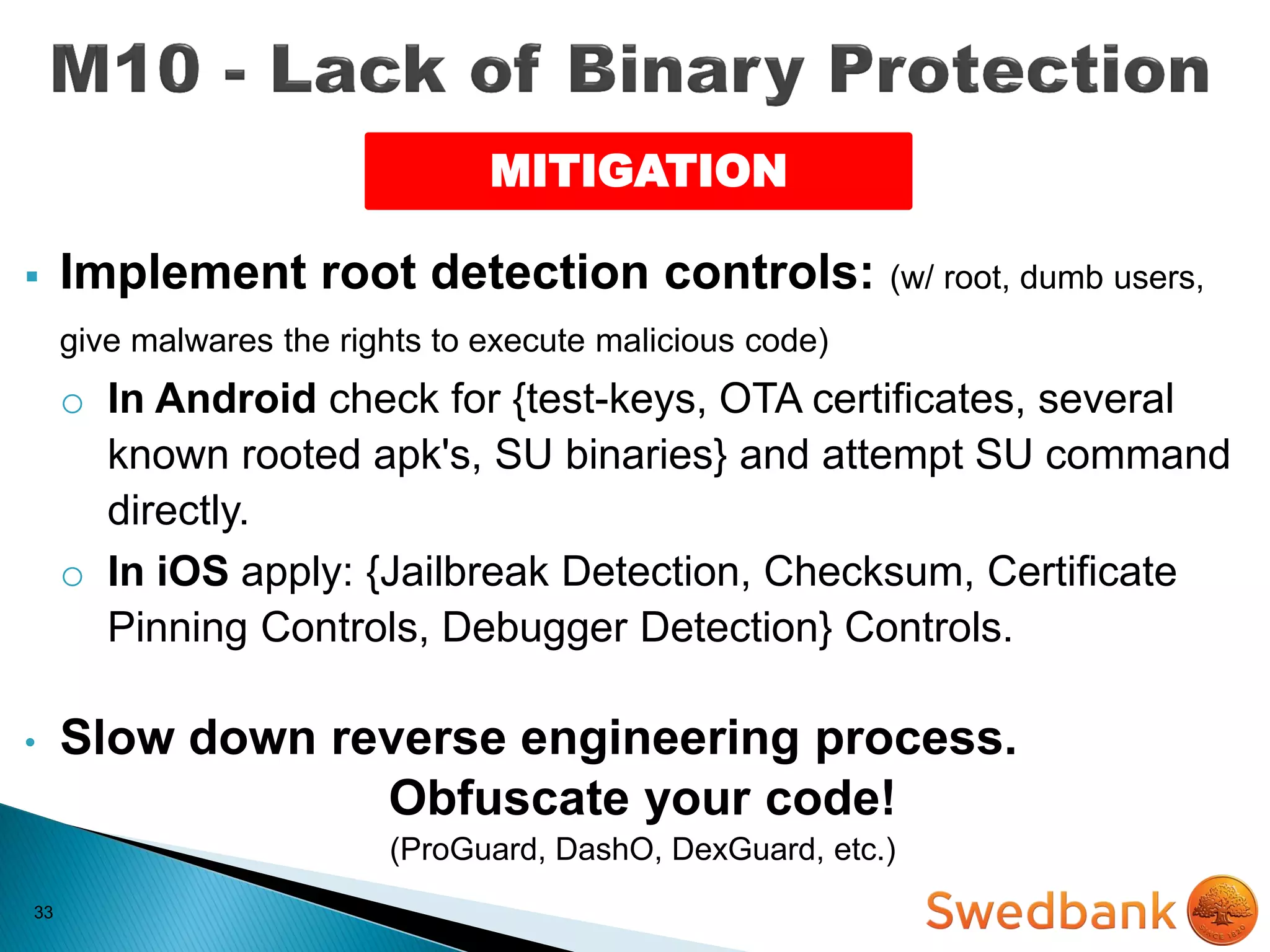
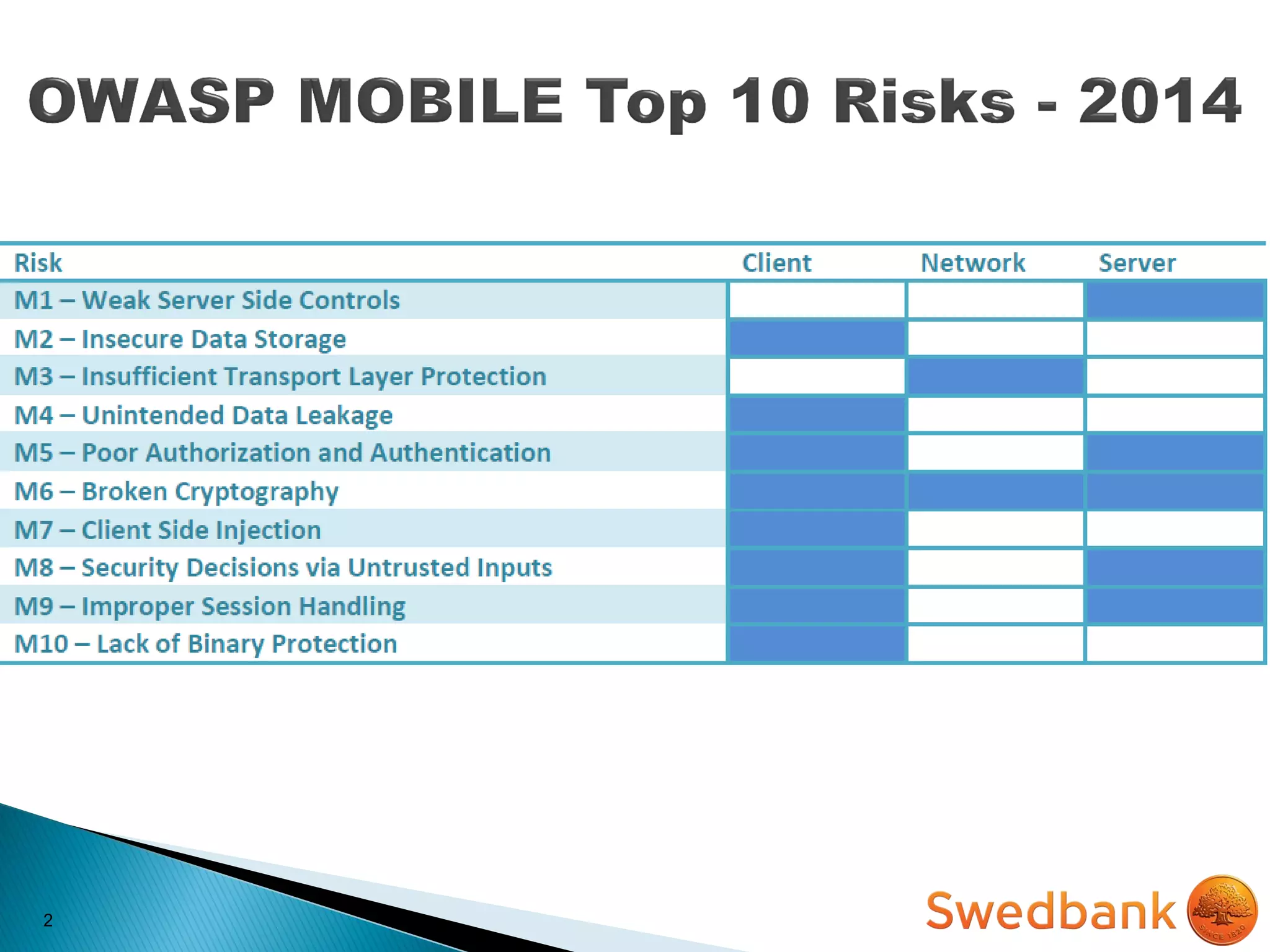
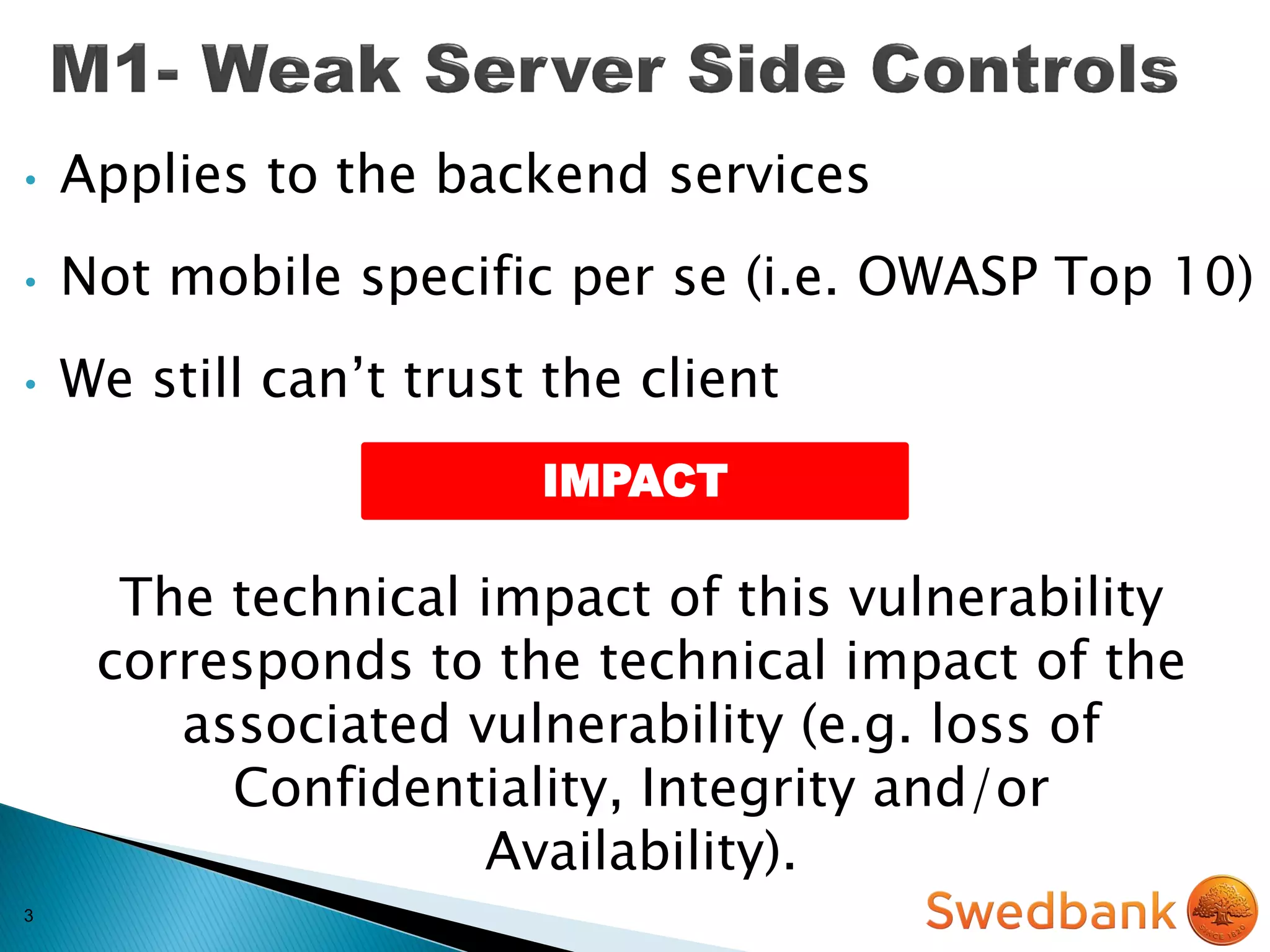
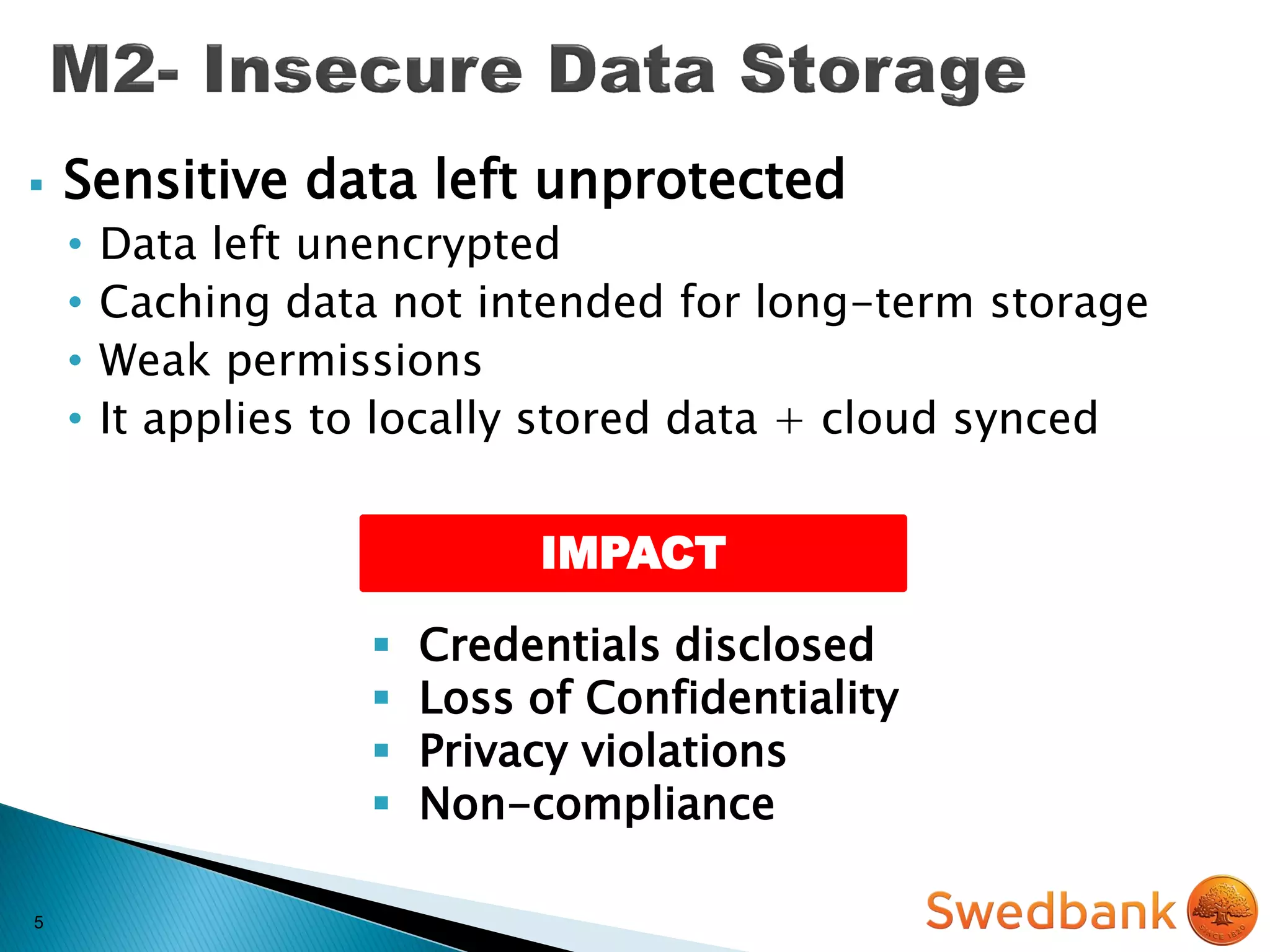
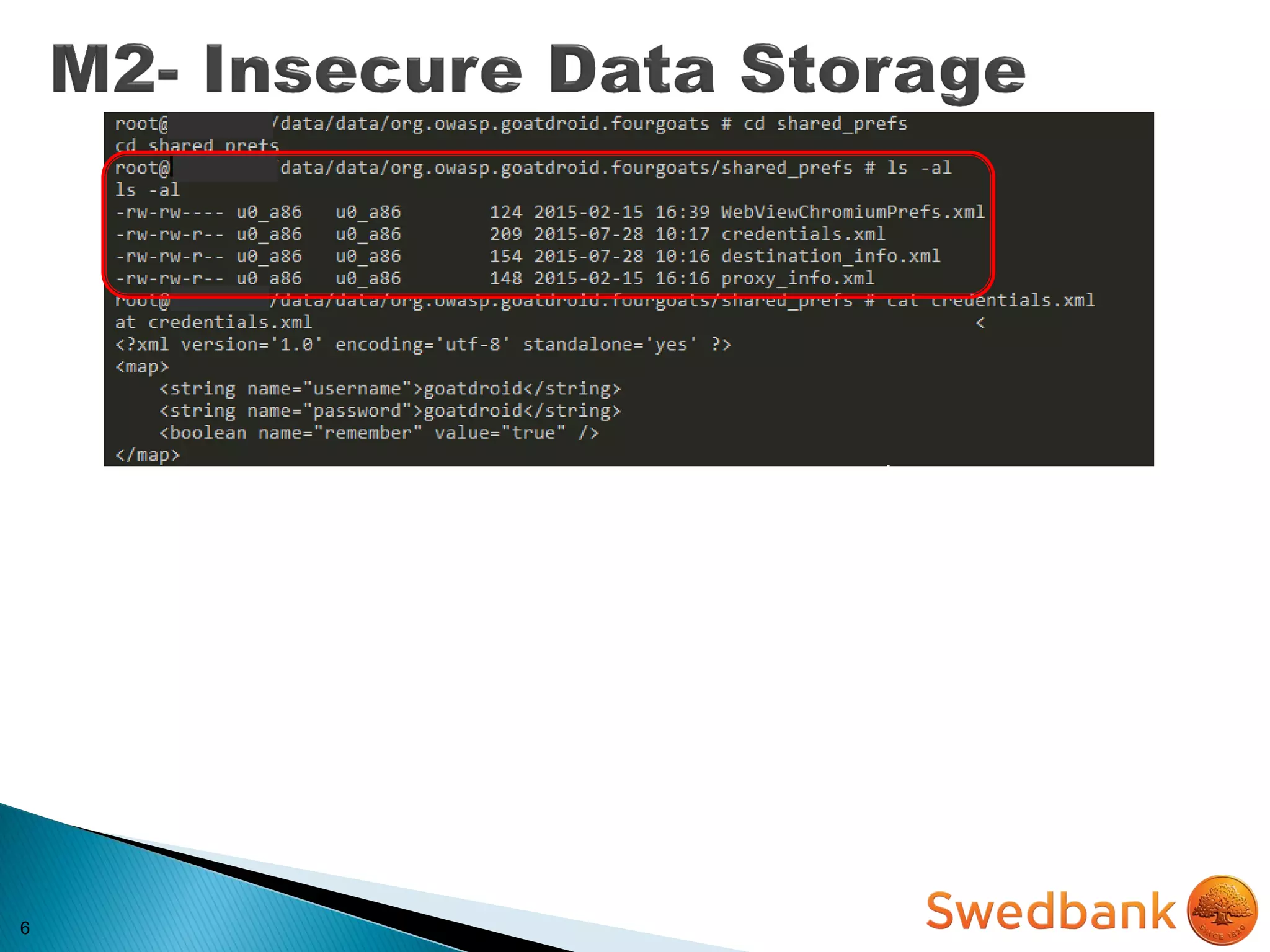
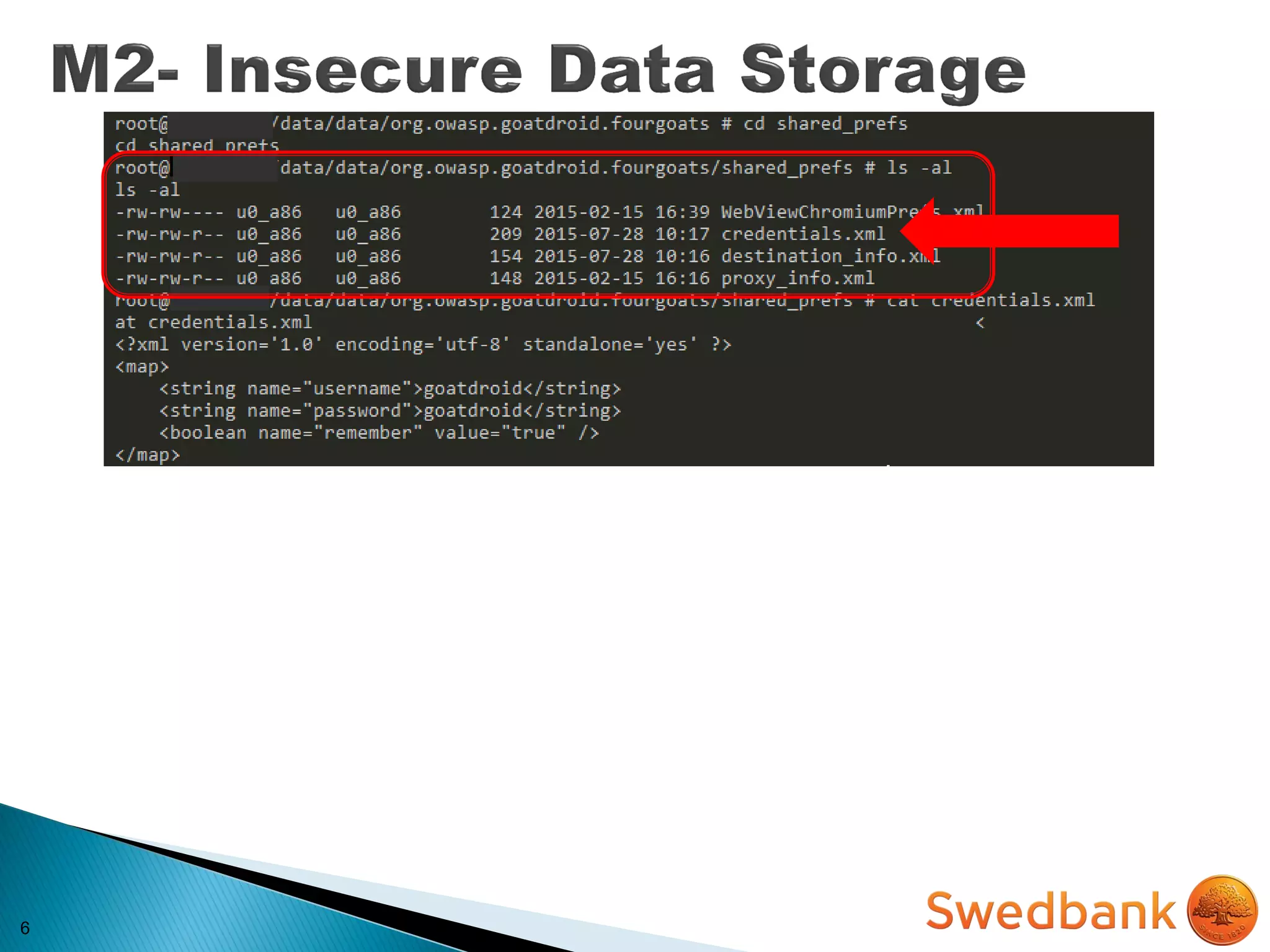
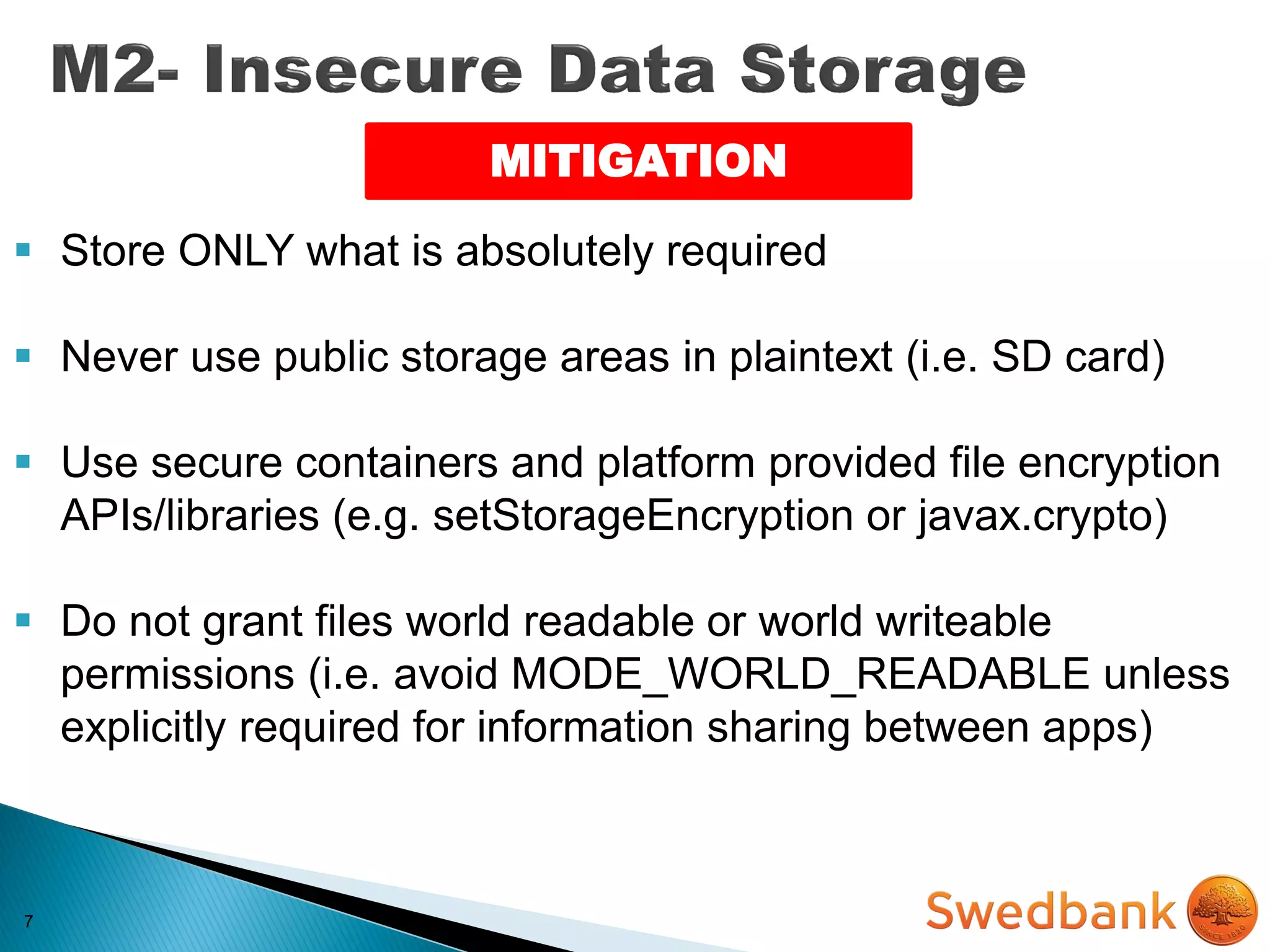
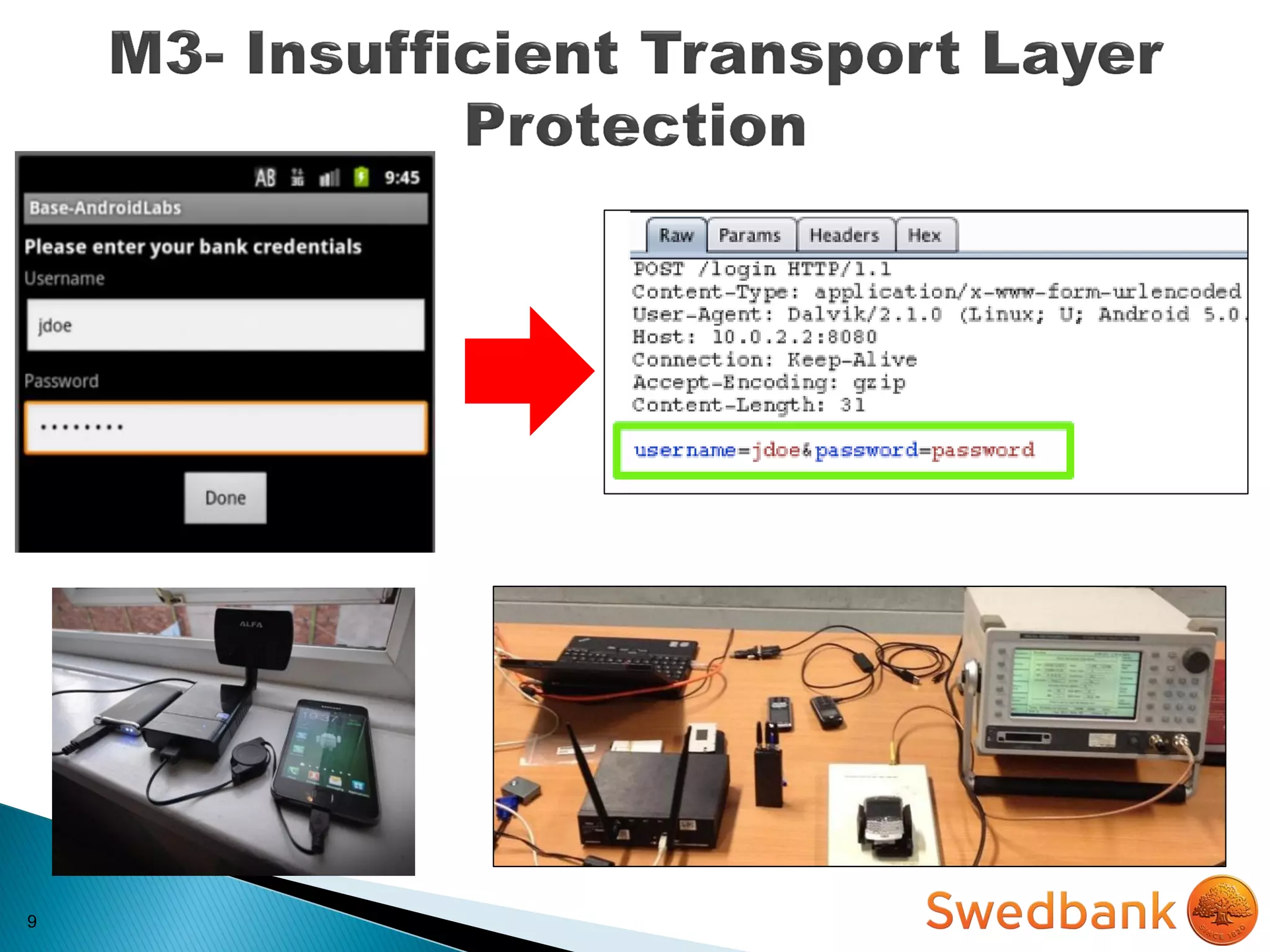
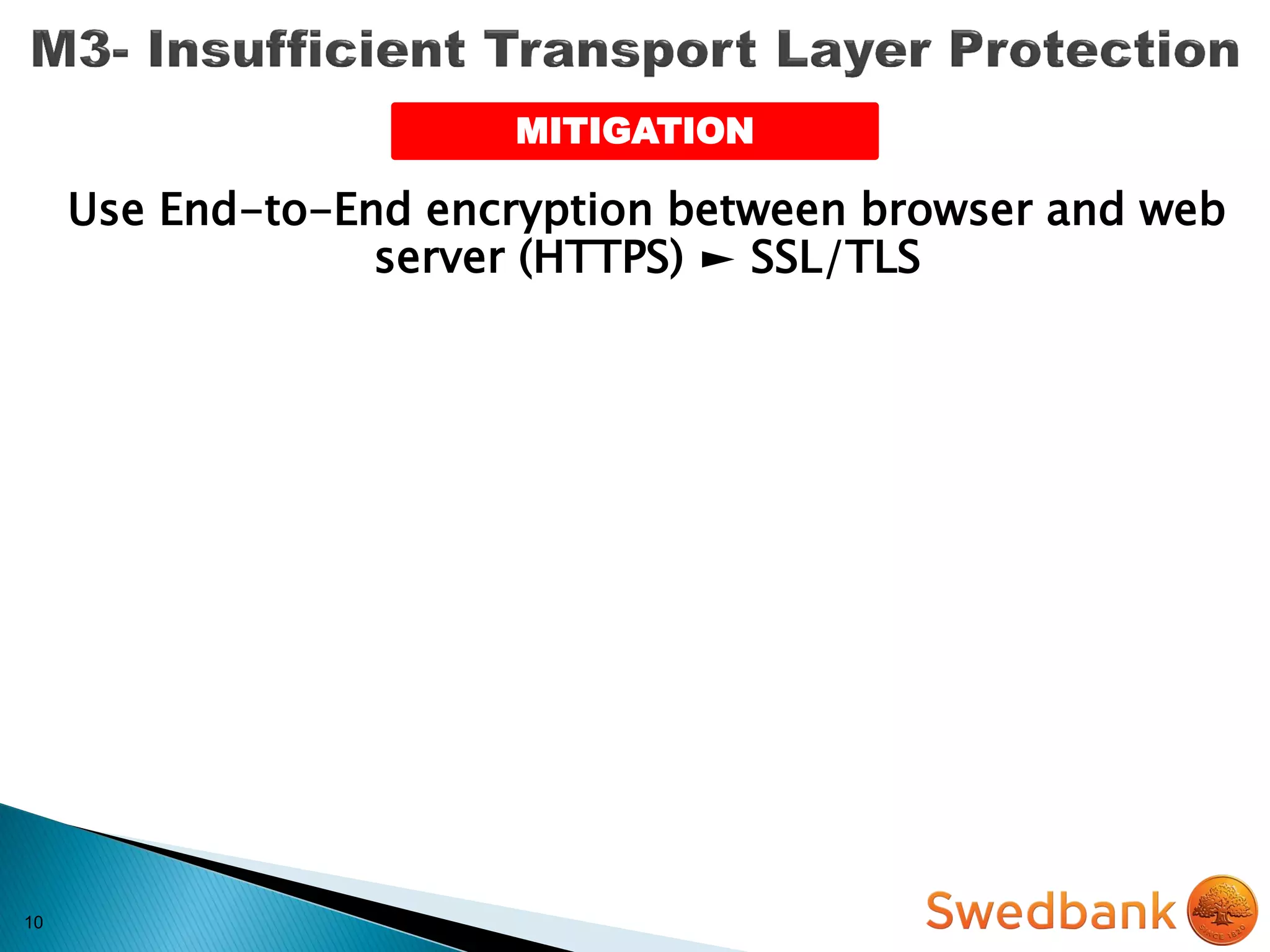
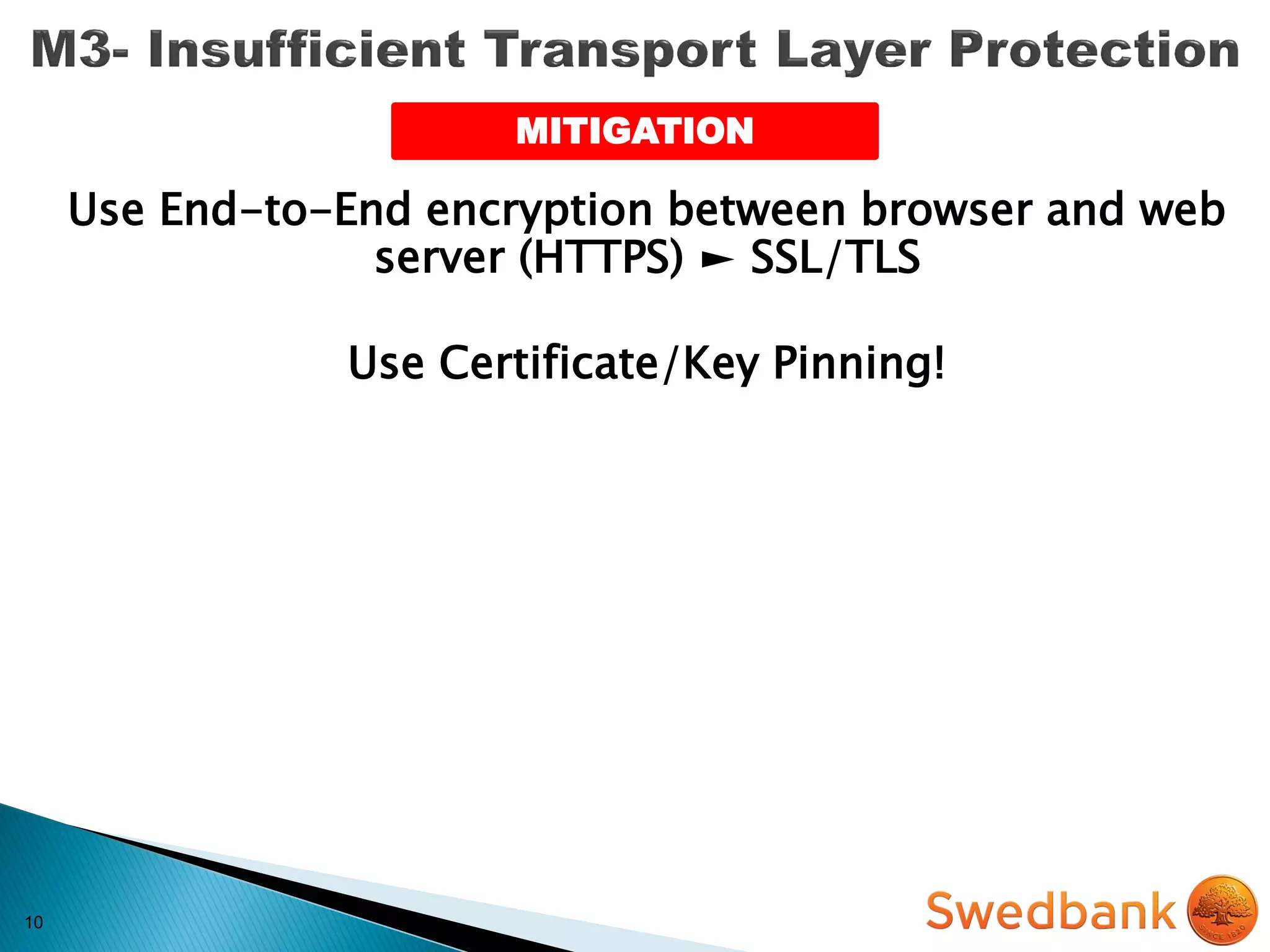
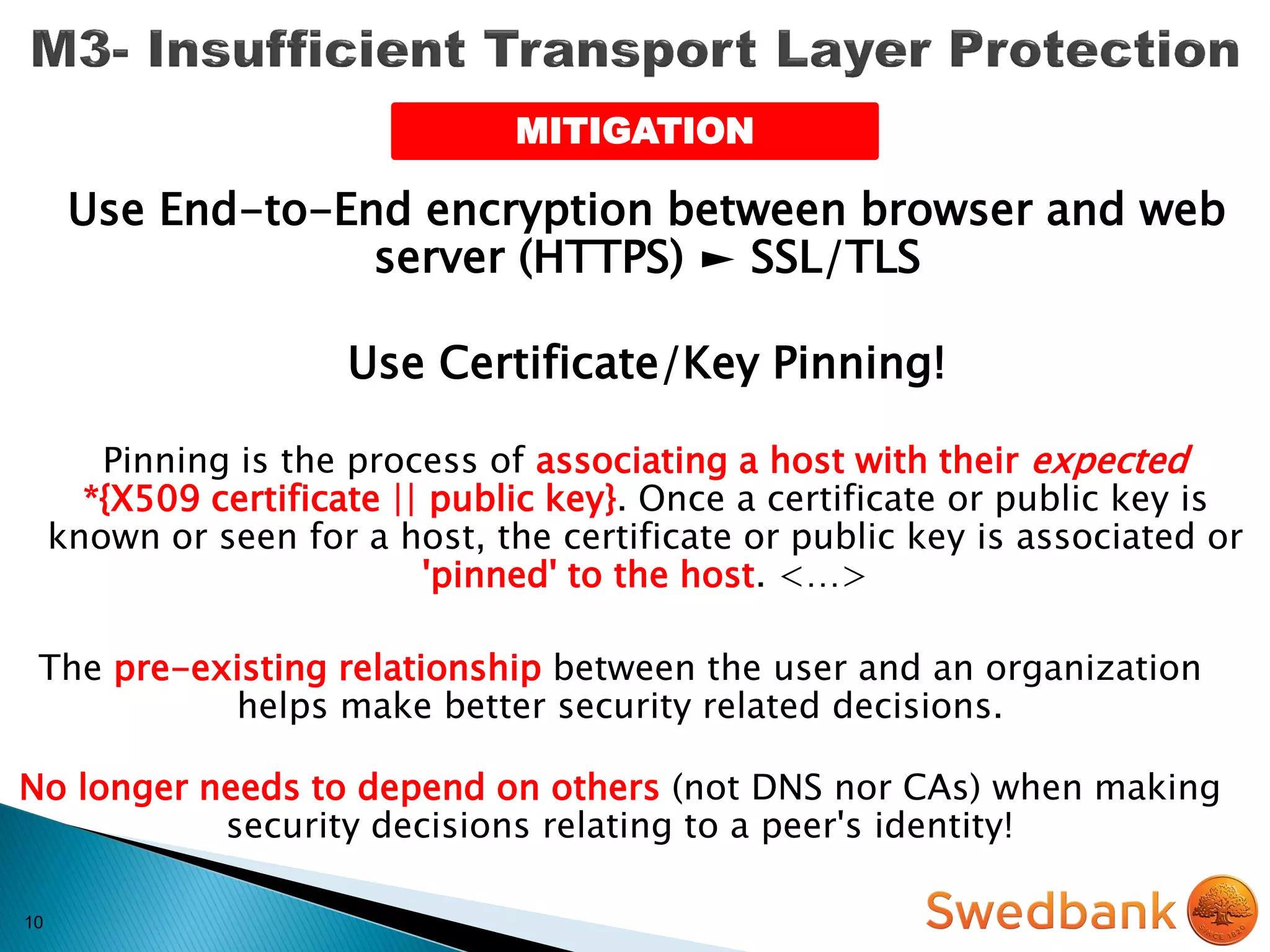
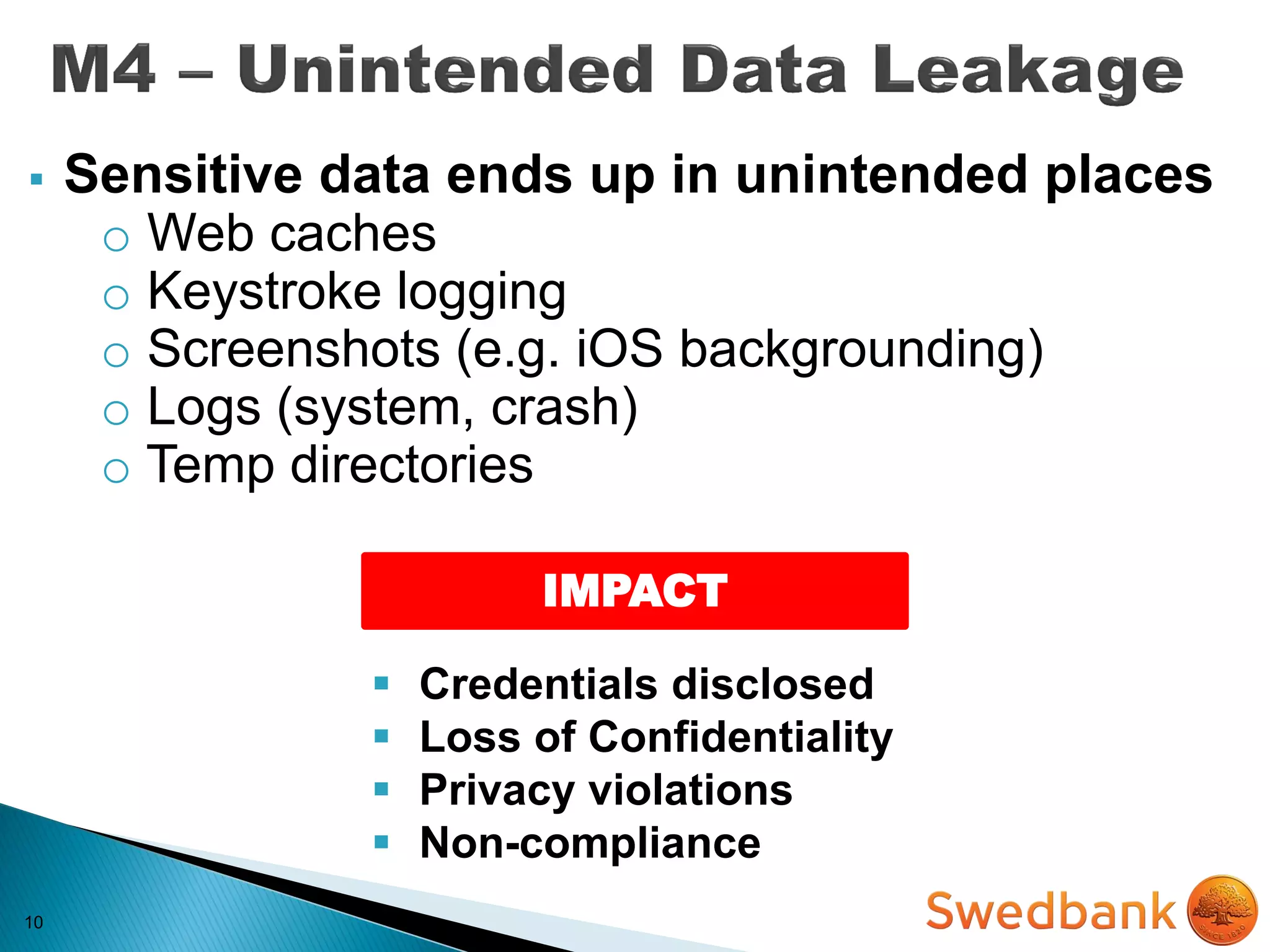
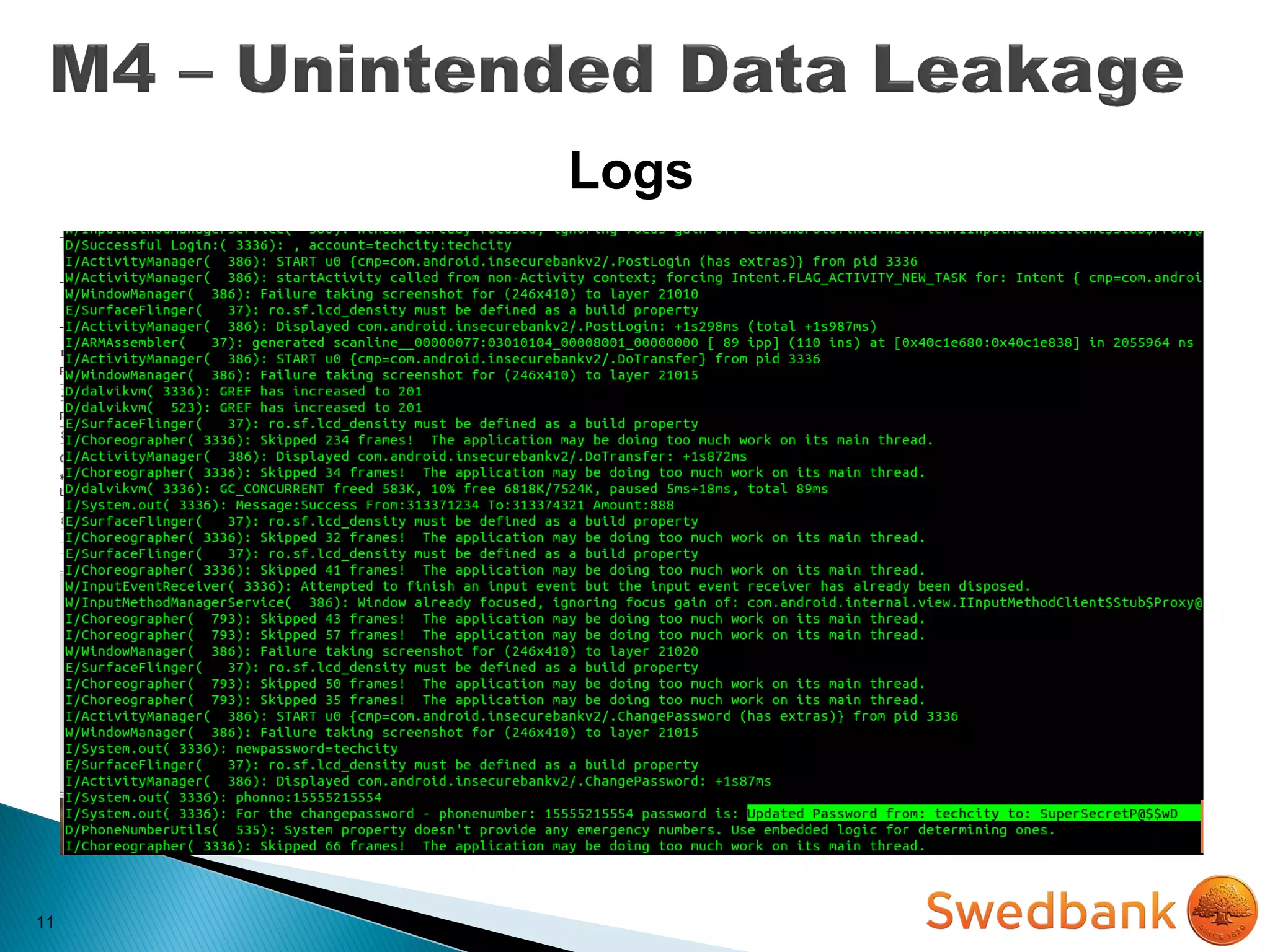
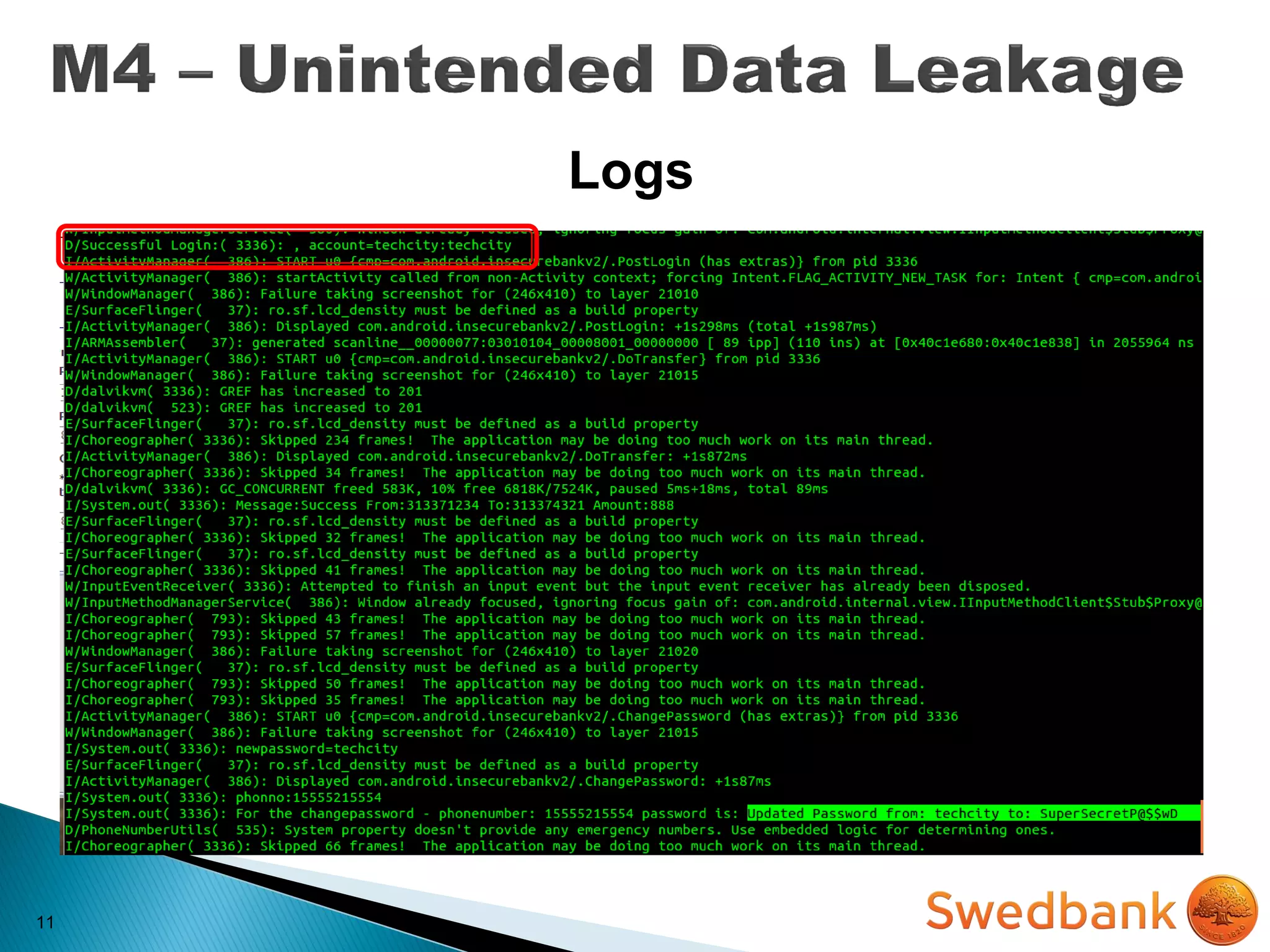
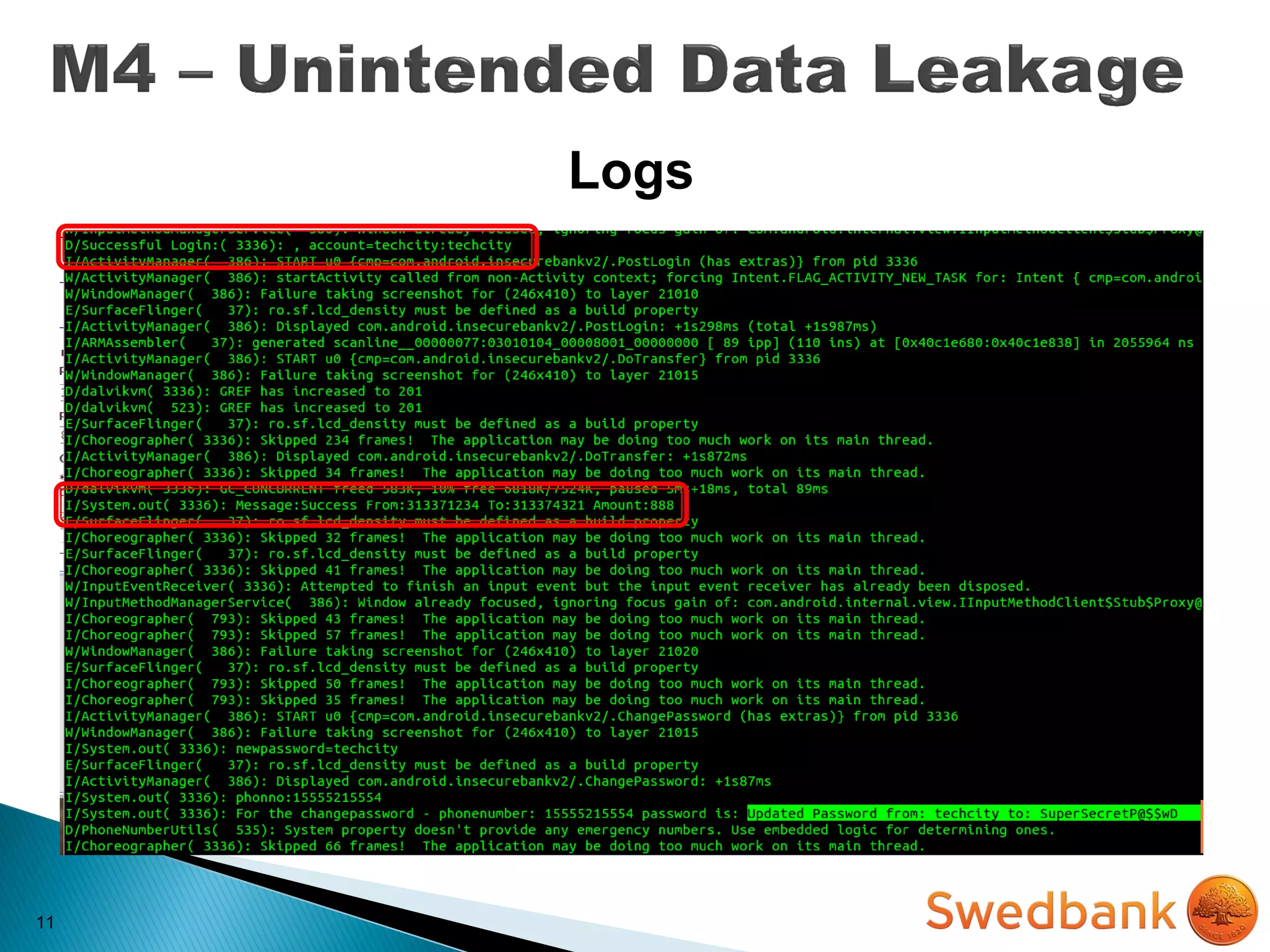
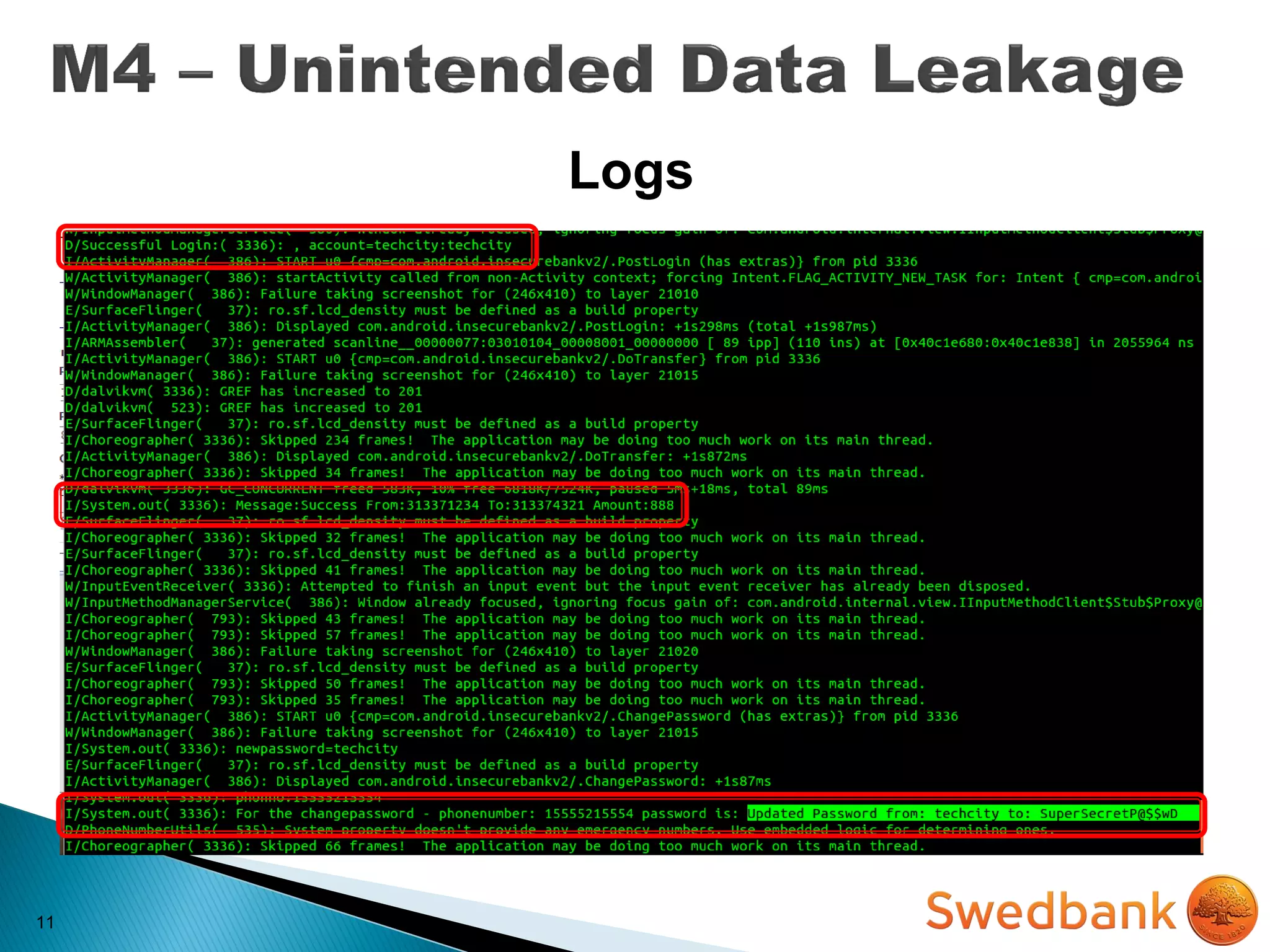
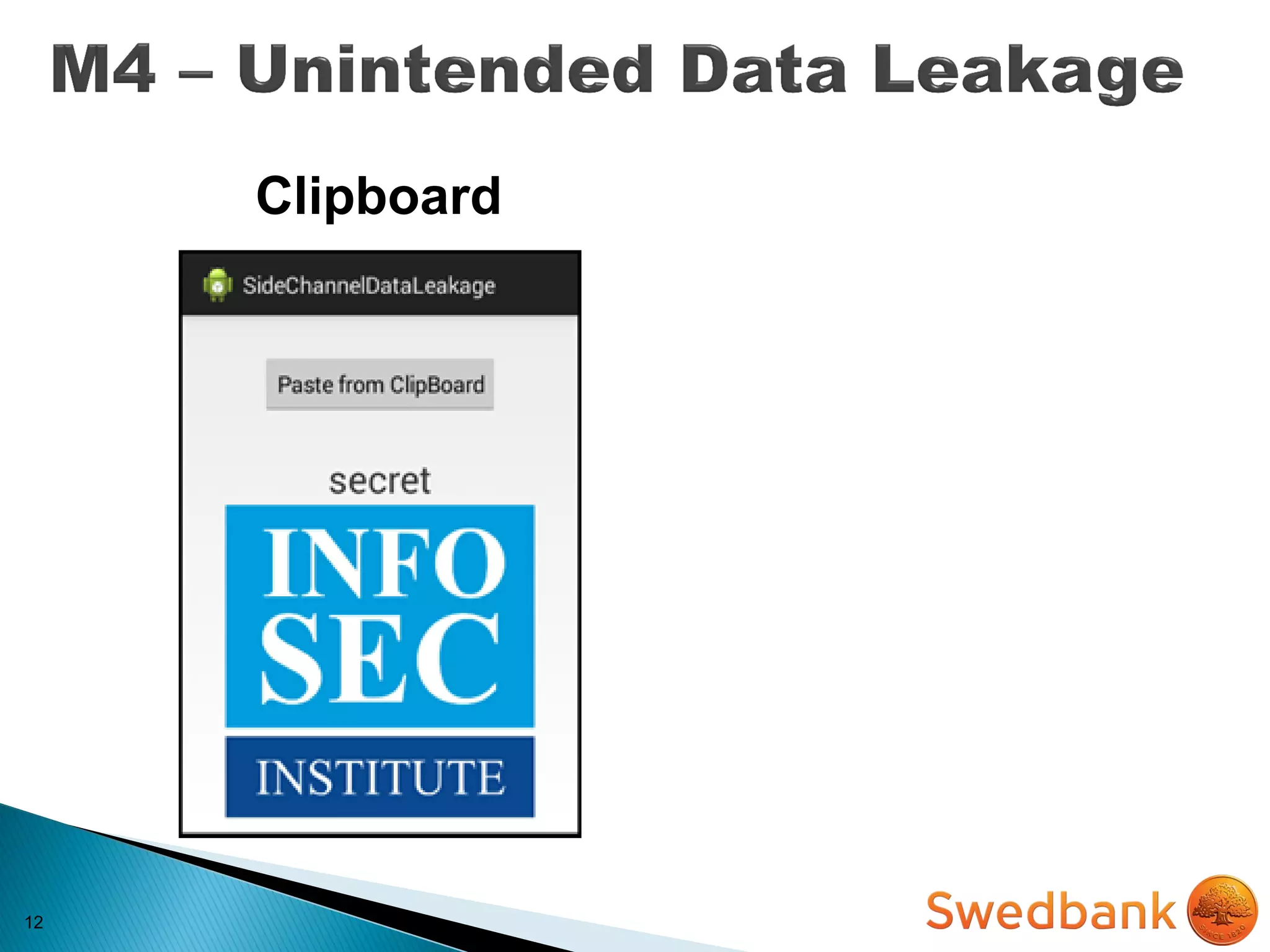
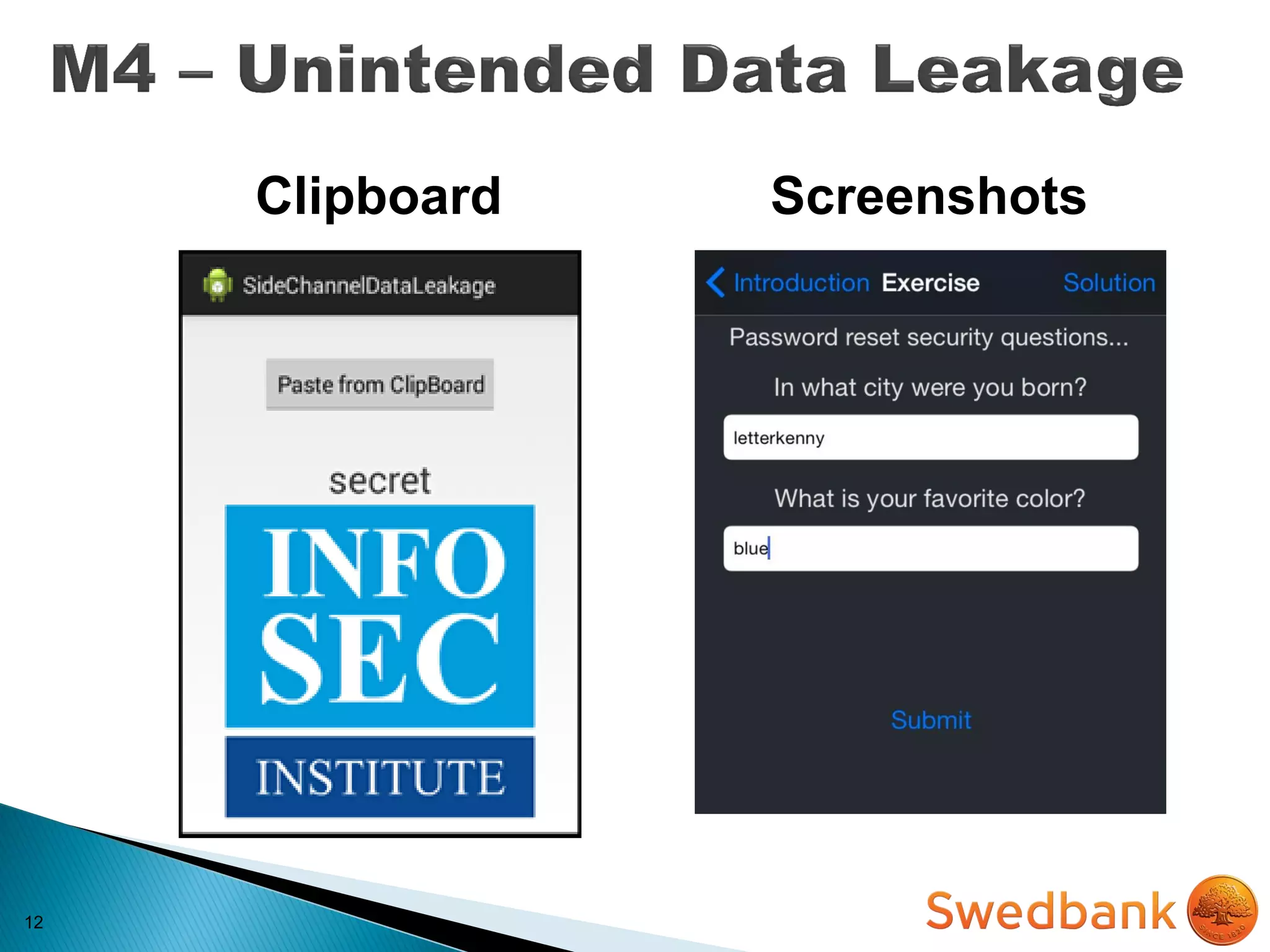
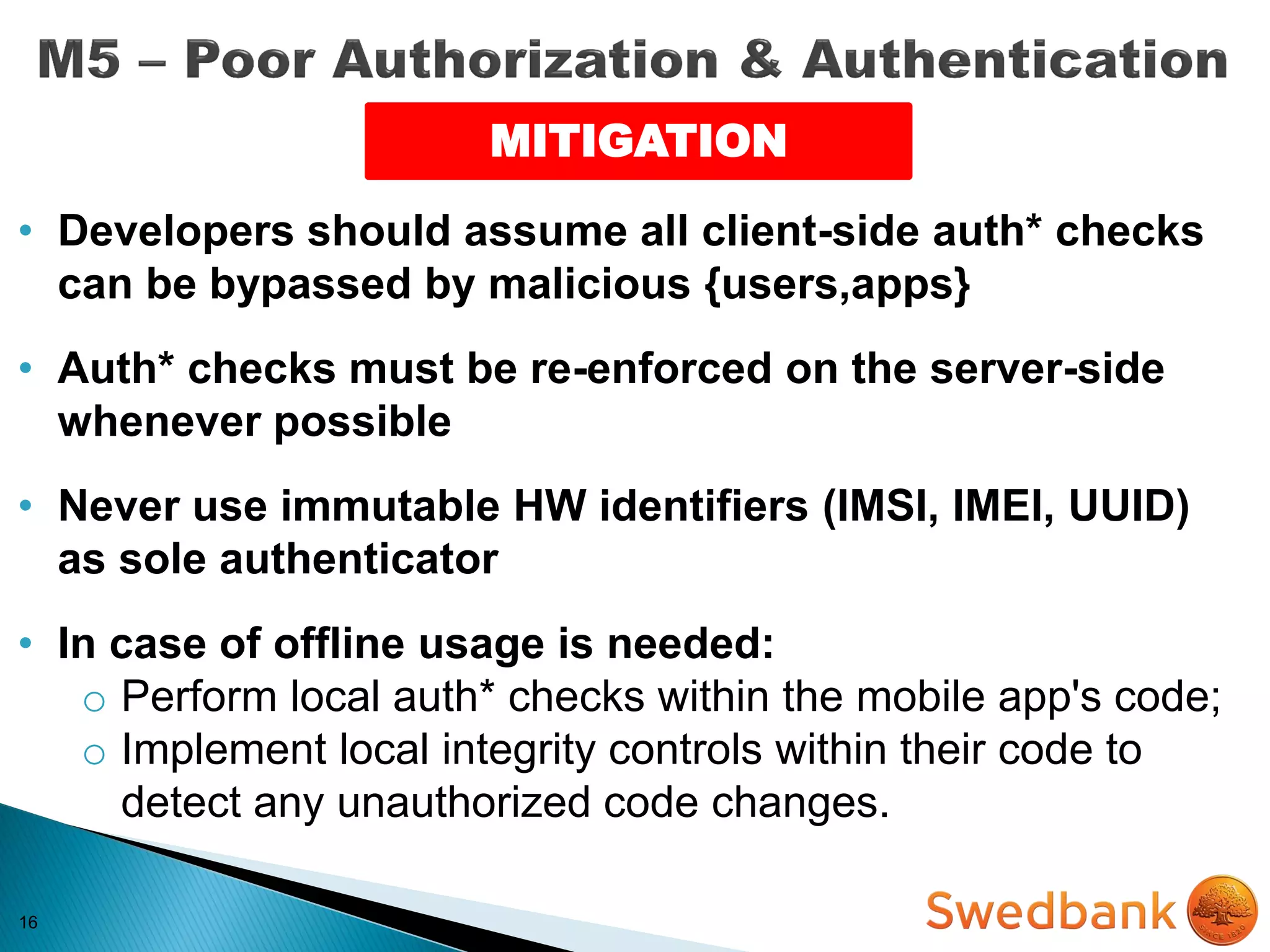
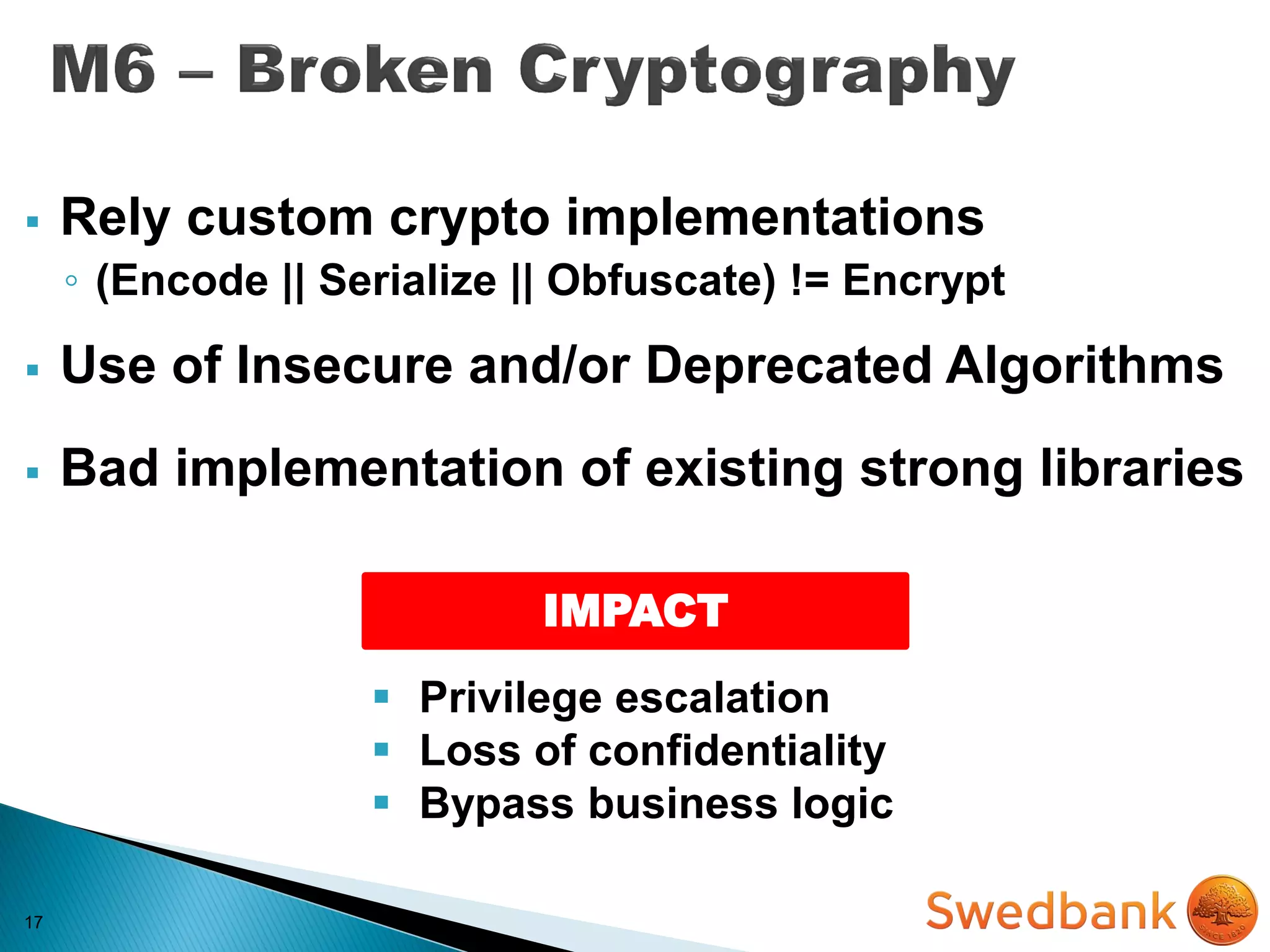
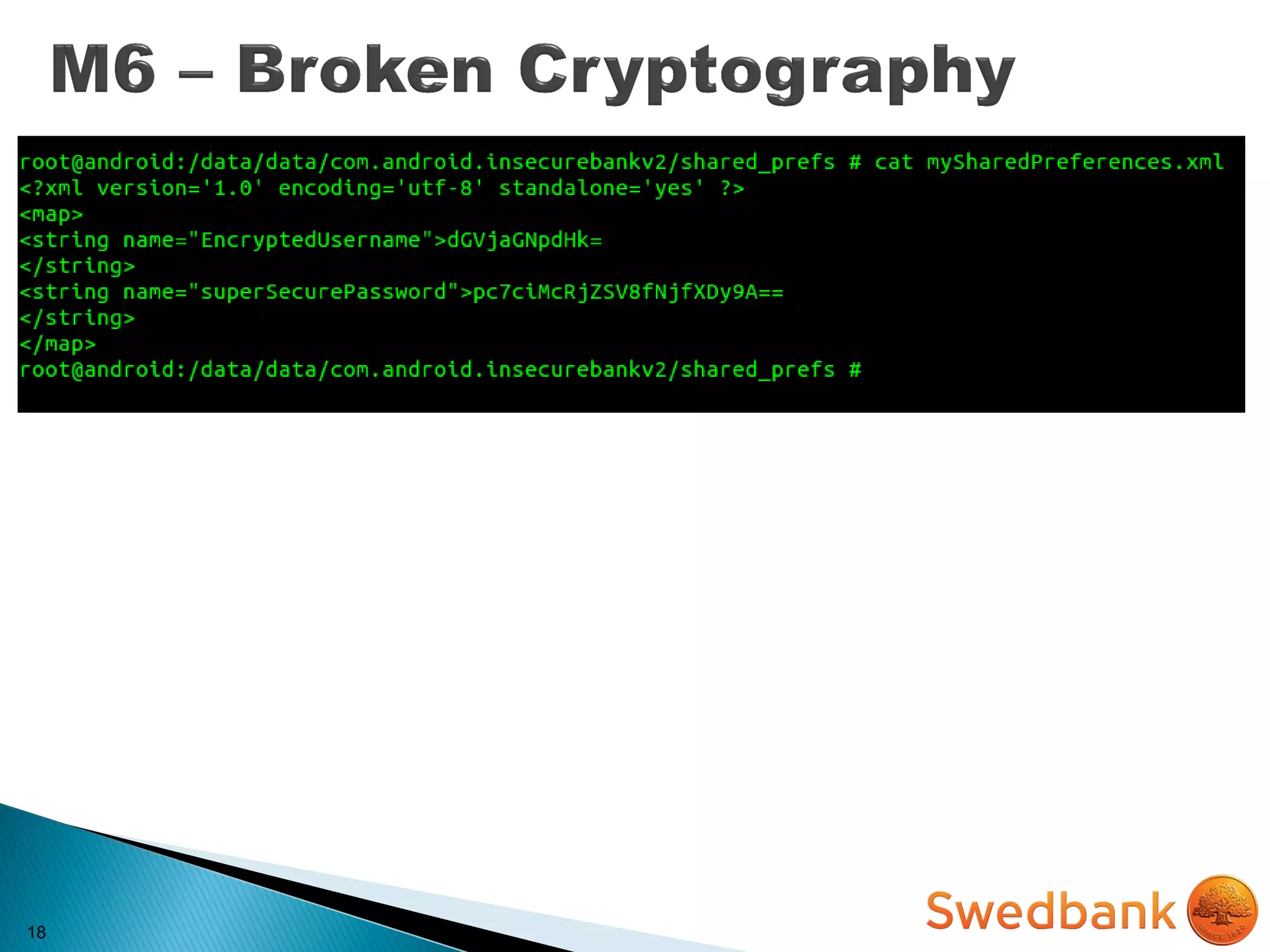
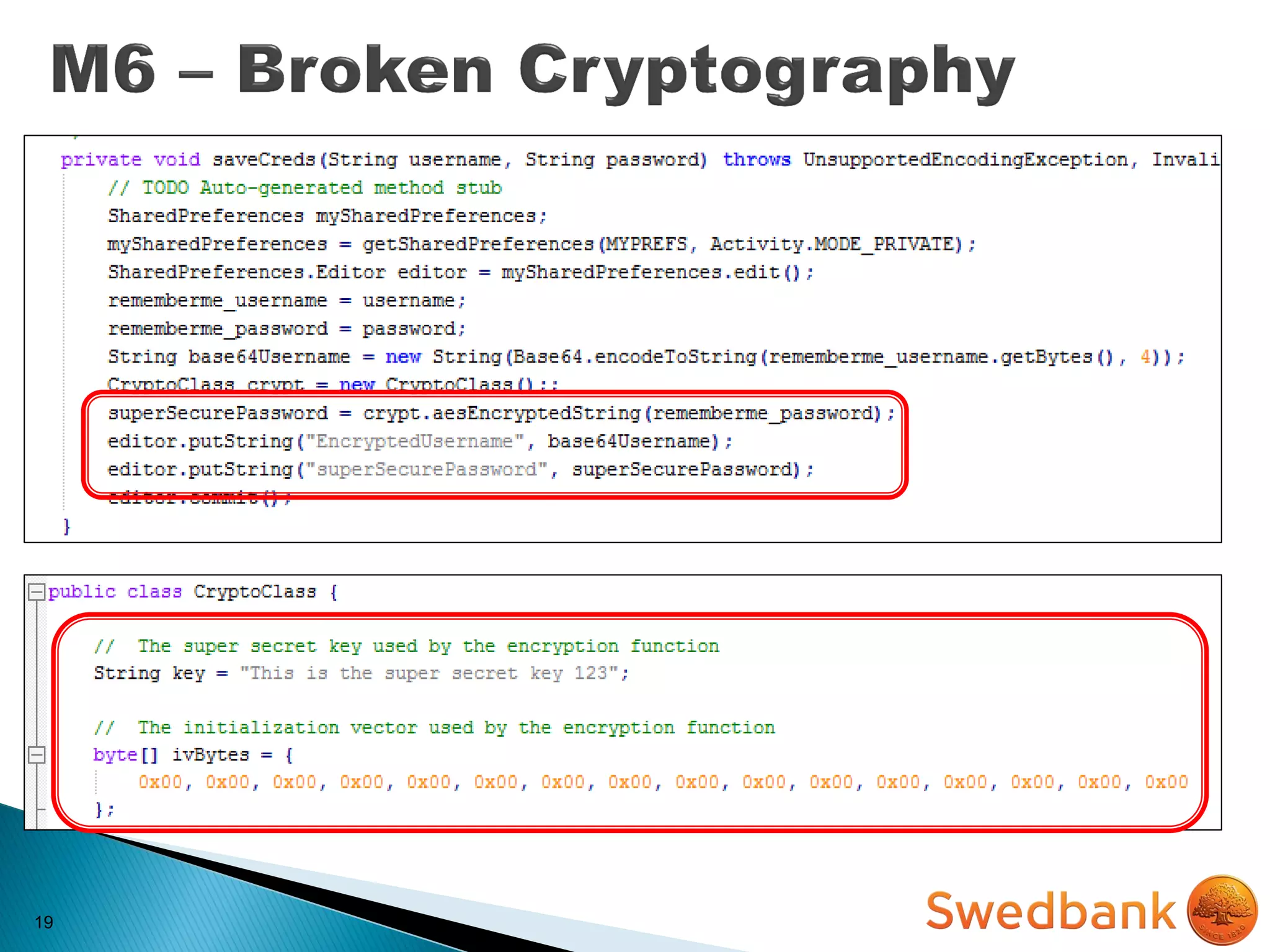
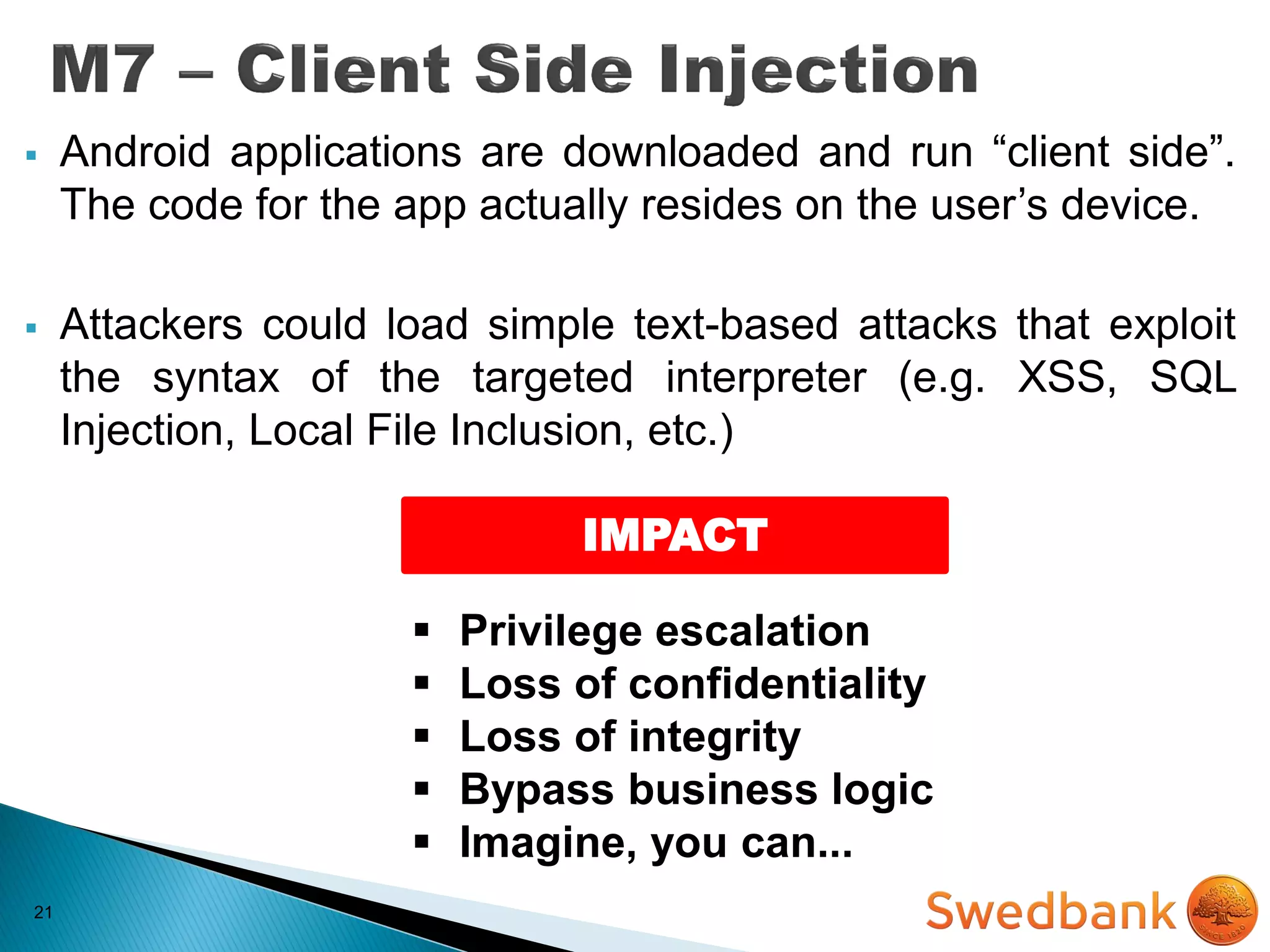
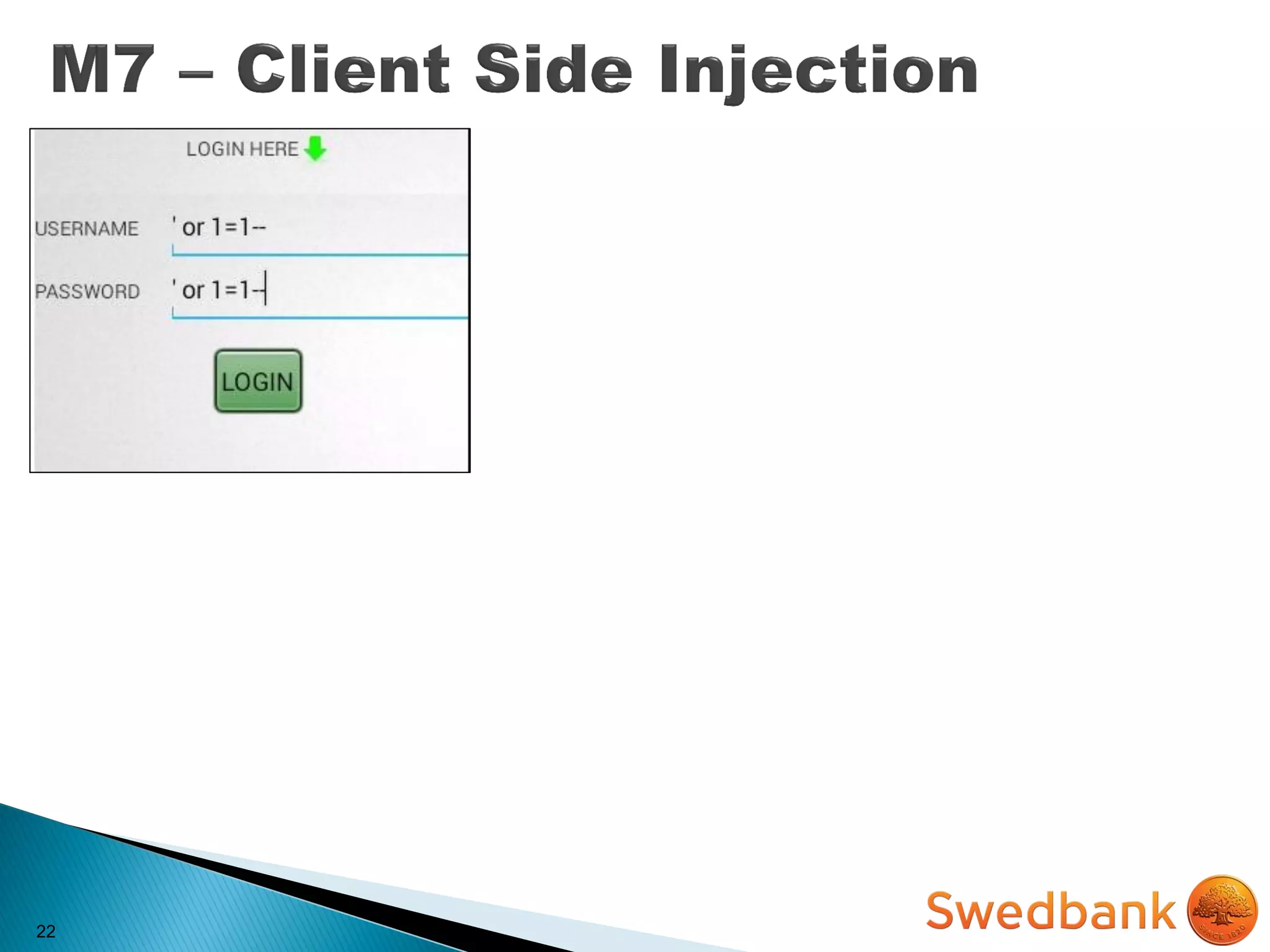
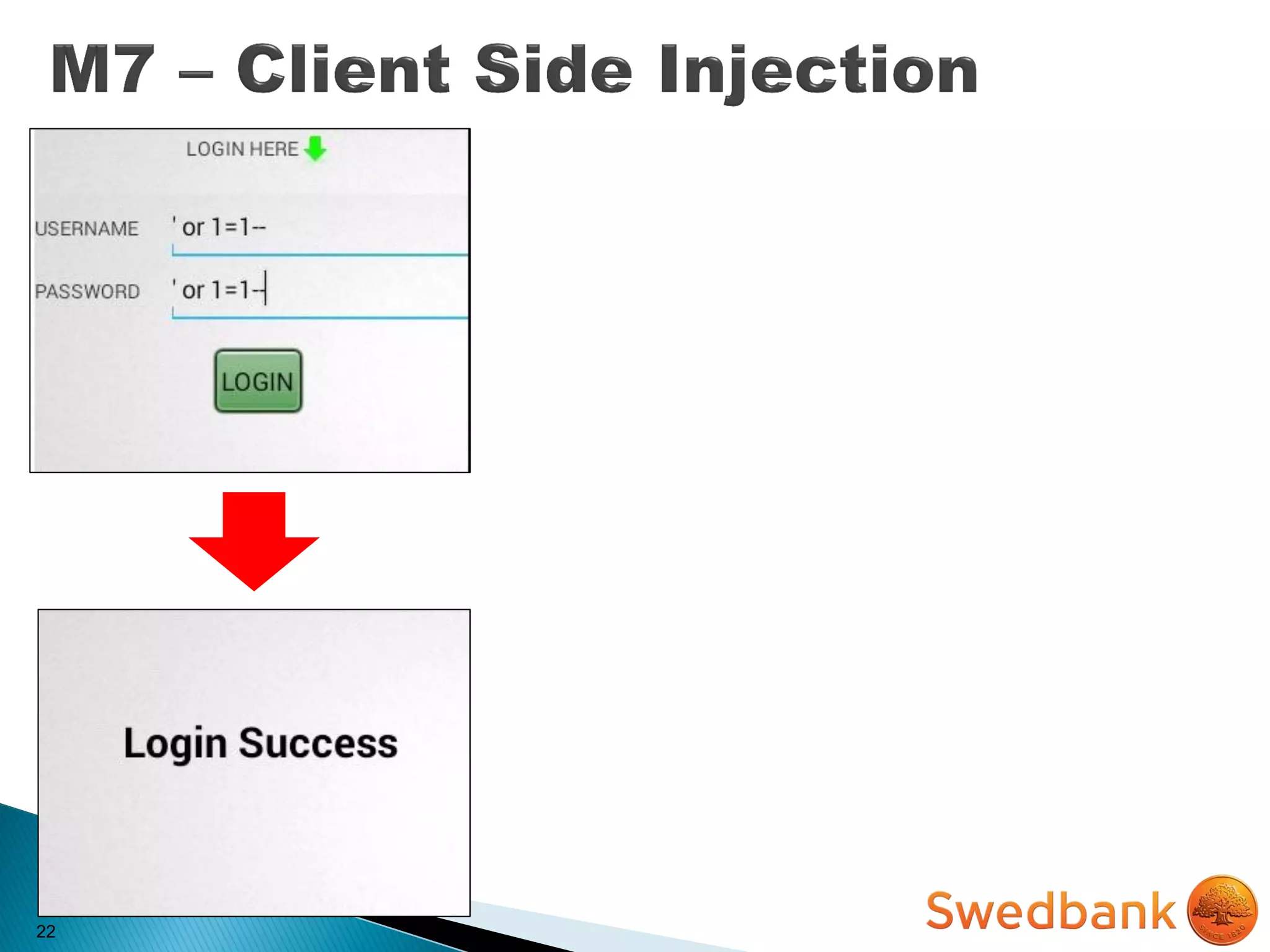
The document discusses various mobile application security vulnerabilities. It covers topics like insecure data storage, lack of encryption for network traffic, authentication issues, insecure session management, and risks from unintended data exposure. Mitigation strategies are provided for each vulnerability, which generally involve following secure coding best practices, leveraging encryption properly, validating all inputs, and deploying defenses in depth with checks on both the client and server sides.



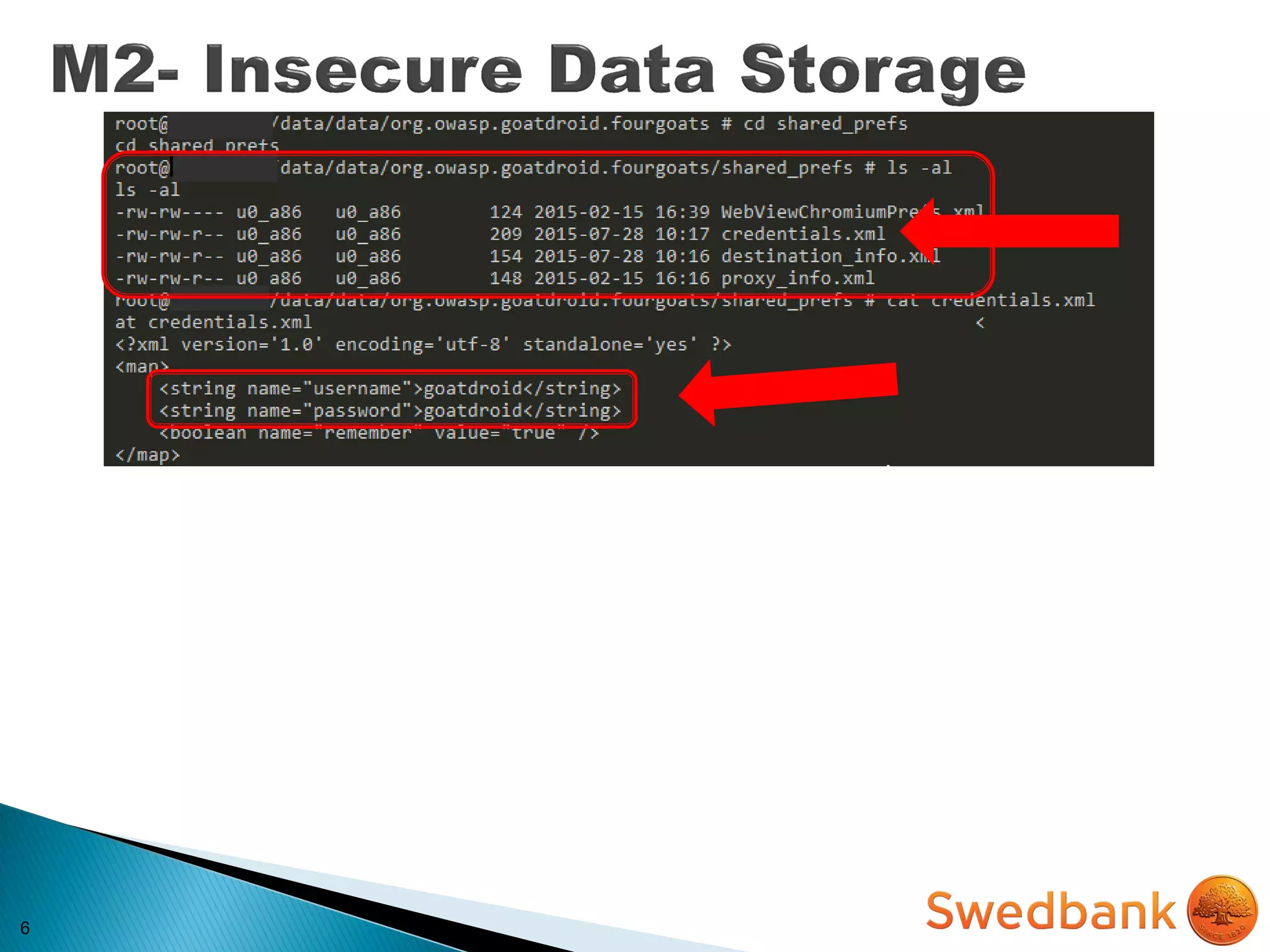
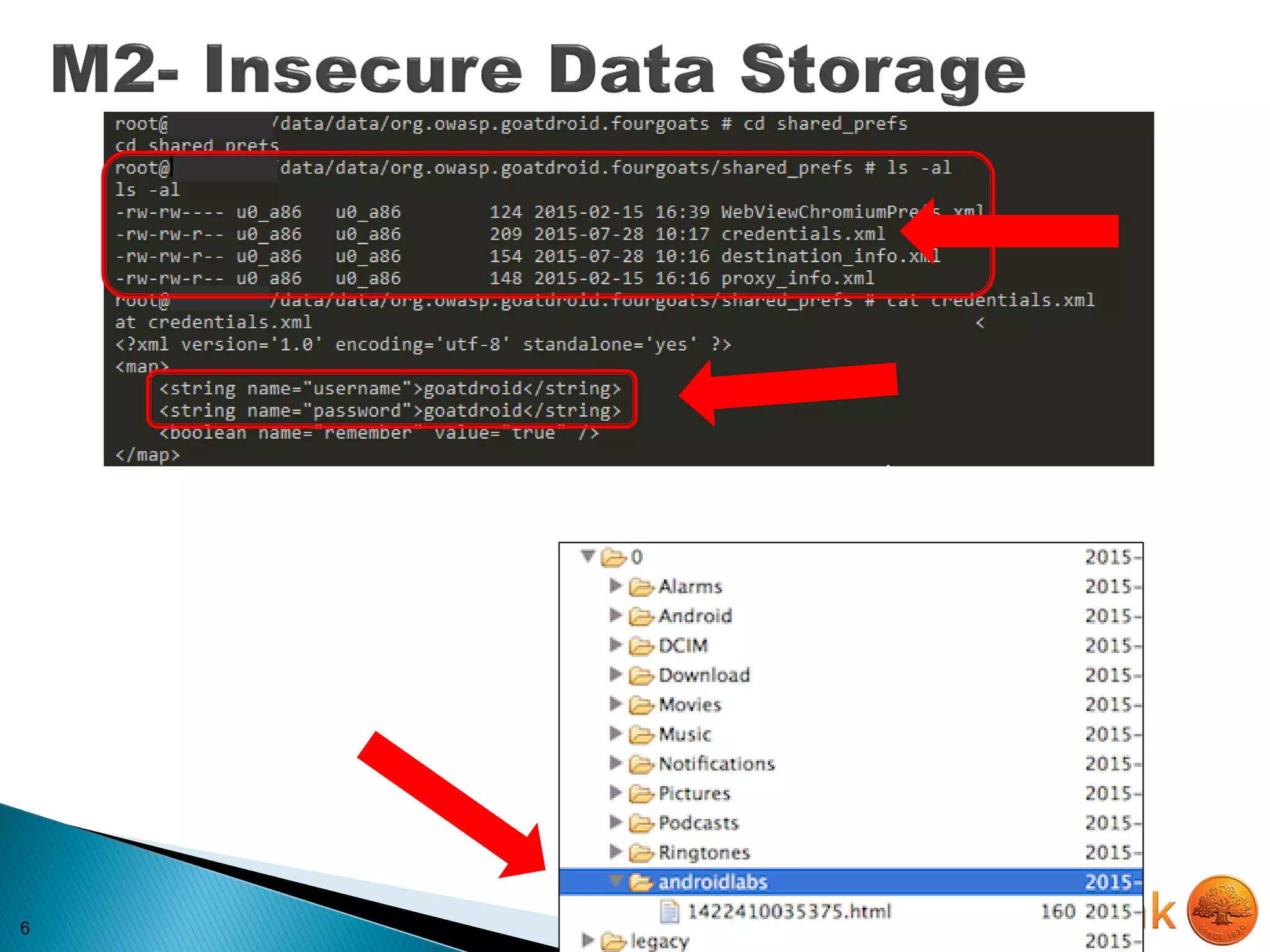
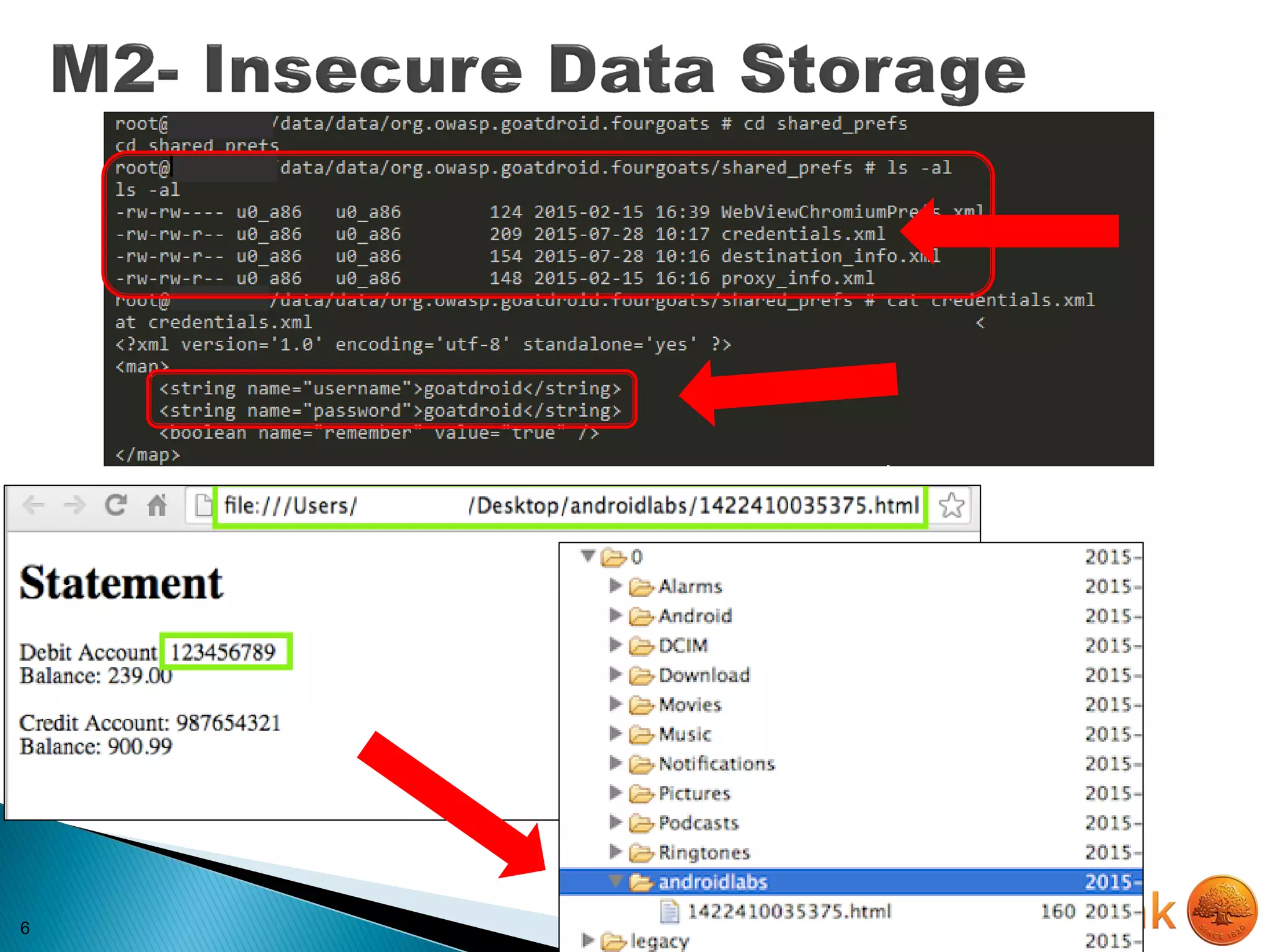









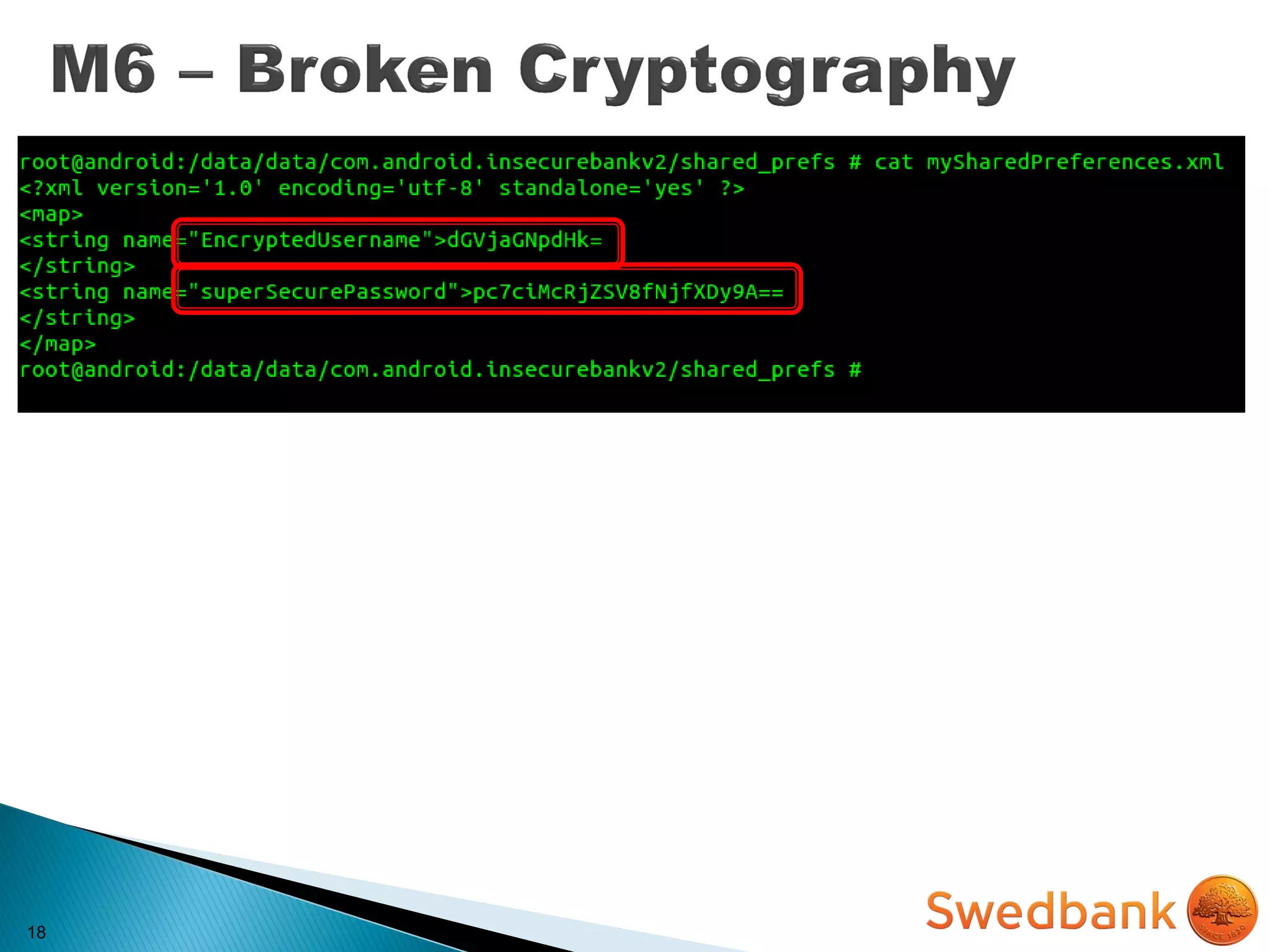
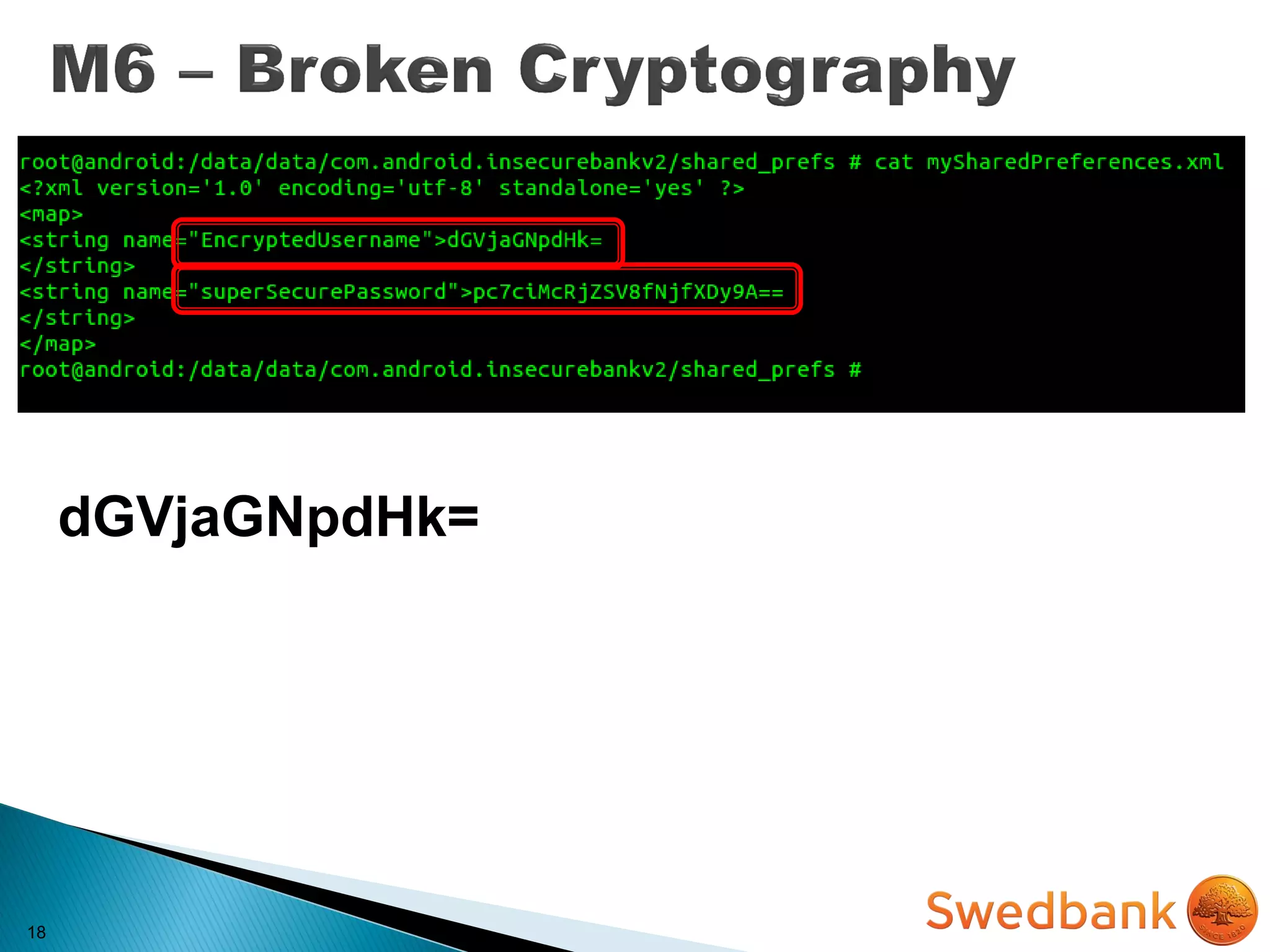
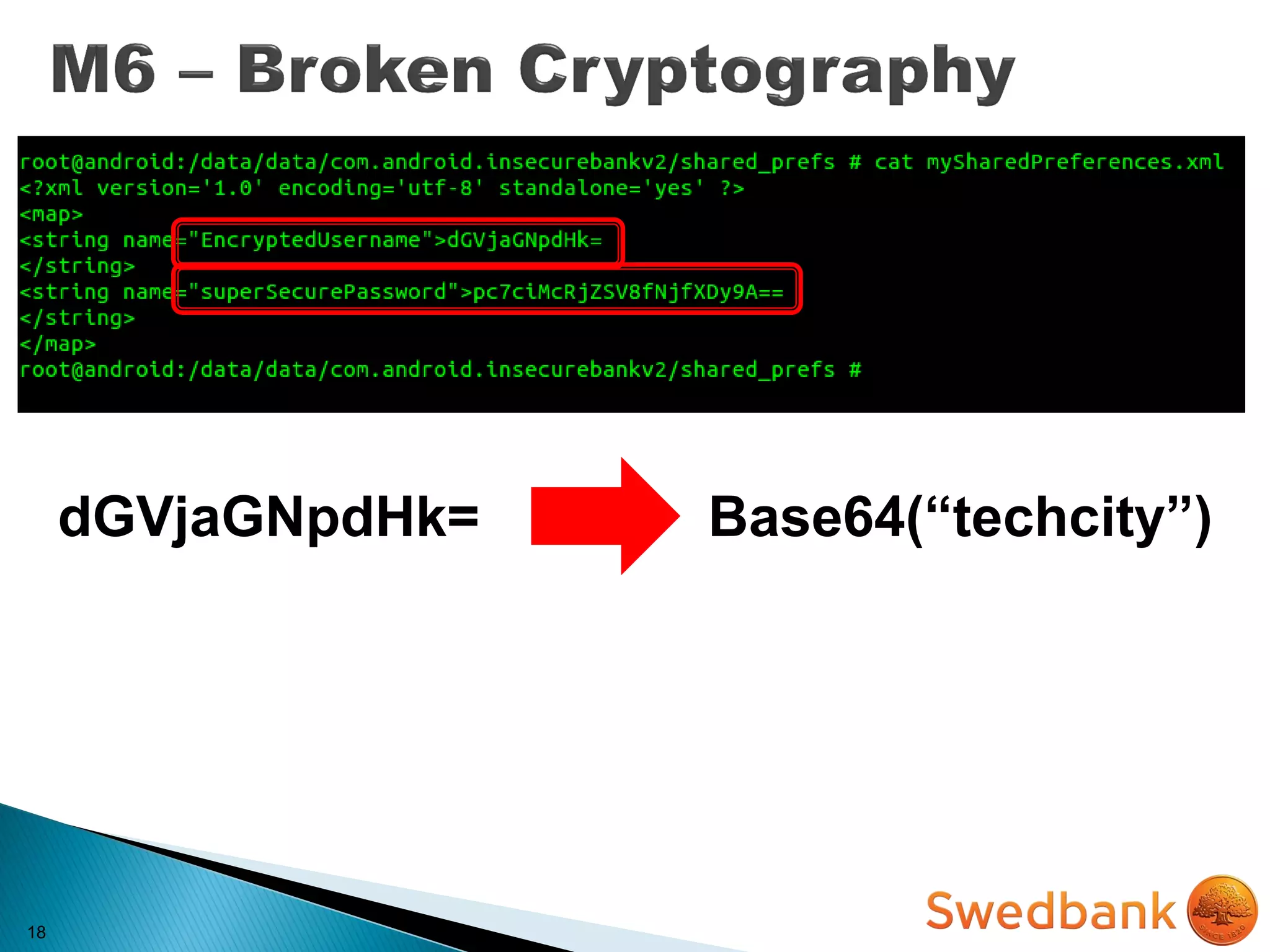
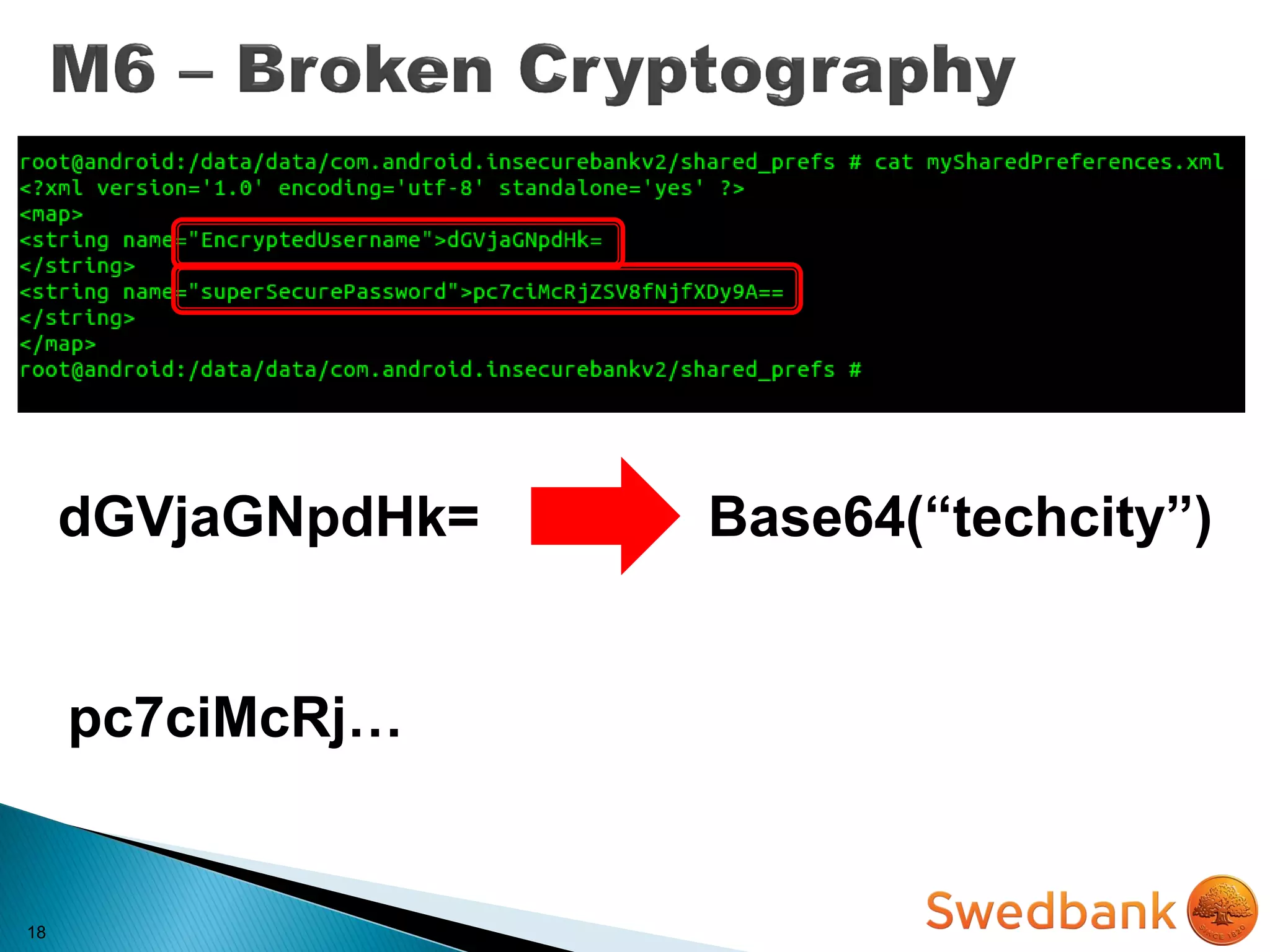







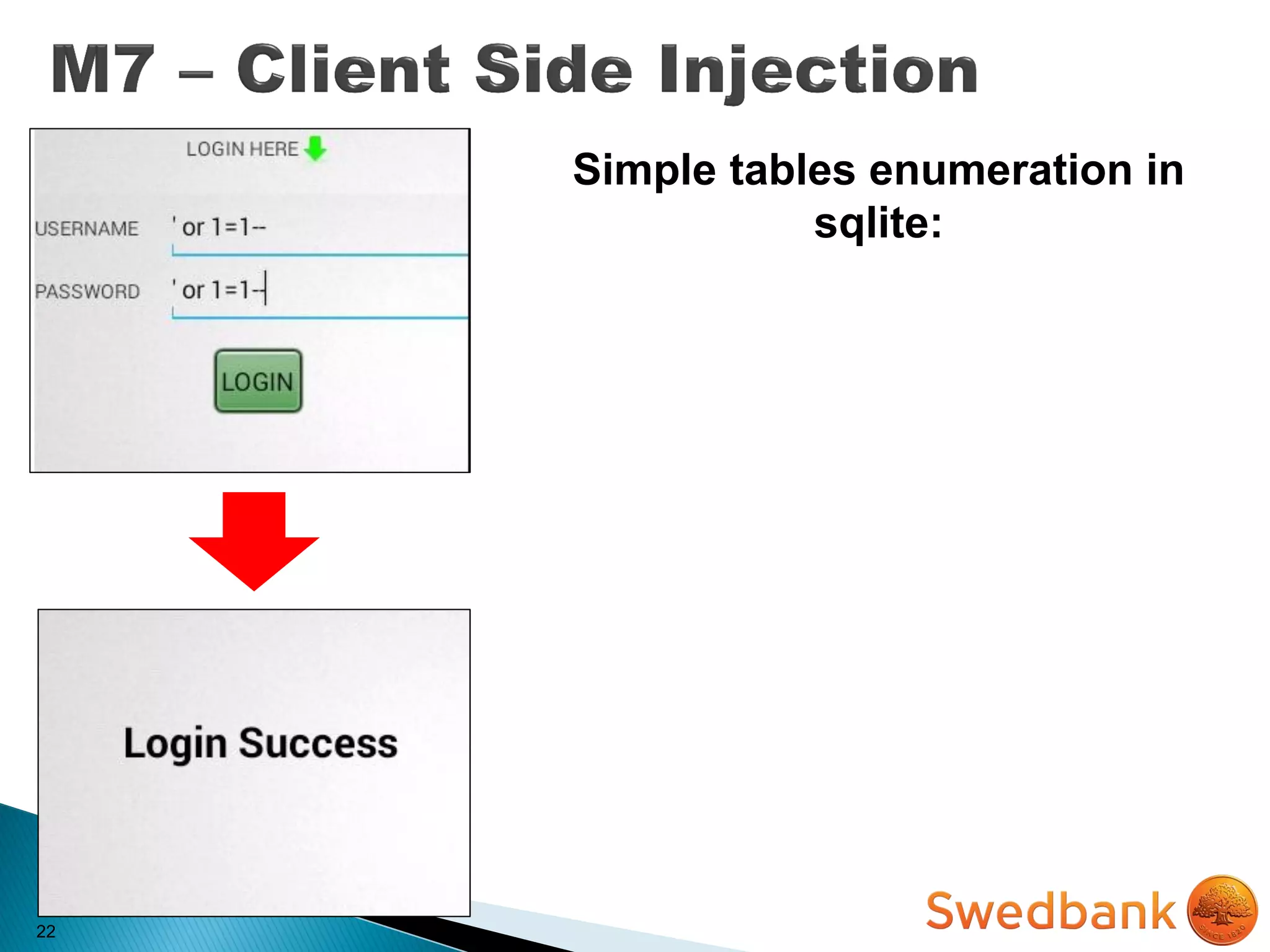
![22
Simple tables enumeration in
sqlite:
dz> run app.provider.query
[URI] –selection “1=1) union
select 1,2,tbl_name from
sqlite_master where (1=1”](https://image.slidesharecdn.com/techcityswedbanksplitv-150910123612-lva1-app6891/75/Introduction-to-Mobile-Application-Security-Techcity-2015-Vilnius-75-2048.jpg)
![22
Simple tables enumeration in
sqlite:
dz> run app.provider.query
[URI] –selection “1=1) union
select 1,2,tbl_name from
sqlite_master where (1=1”](https://image.slidesharecdn.com/techcityswedbanksplitv-150910123612-lva1-app6891/75/Introduction-to-Mobile-Application-Security-Techcity-2015-Vilnius-76-2048.jpg)