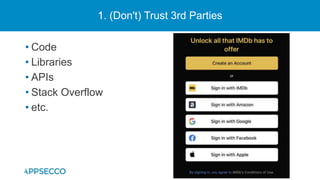
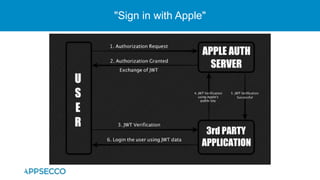
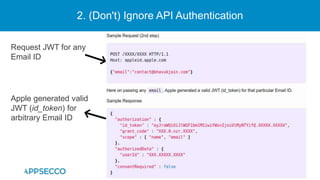
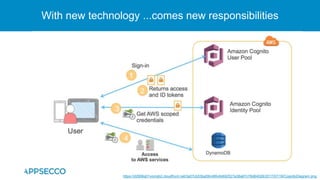
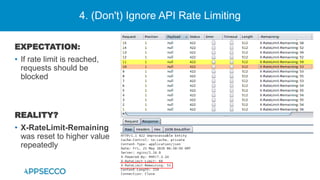
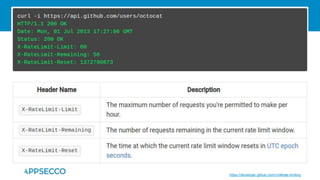
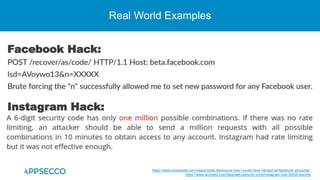
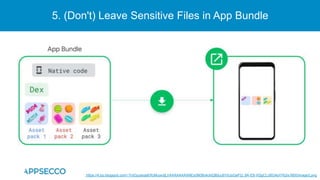
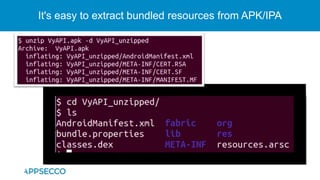
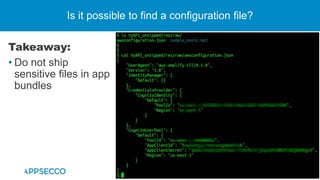
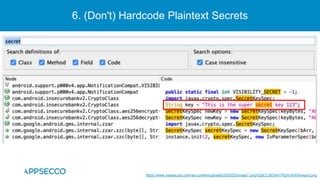
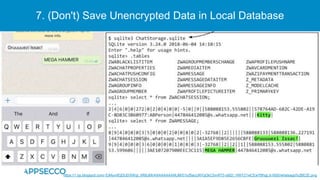
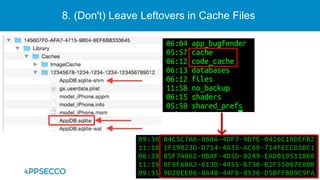
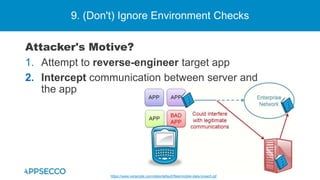
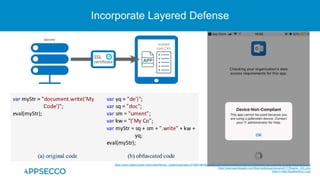
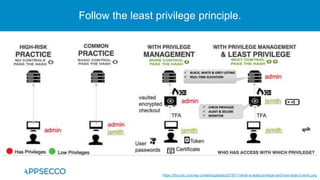
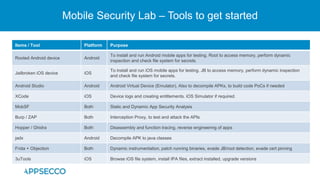
The document provides an overview of a discussion on mobile application security testing between Riddhi Shree and Riyaz Walikar of Appsecco. They discuss common weaknesses found during mobile app testing like trusting third parties, ignoring API authentication and authorization, and not implementing proper input validation. They also cover steps developers should take like verifying third party code, implementing layered defenses, and following secure development best practices around authentication, authorization, and least privilege. The discussion includes a bonus section on setting up a mobile security testing lab.