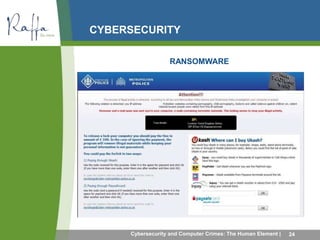
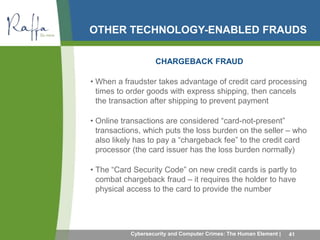
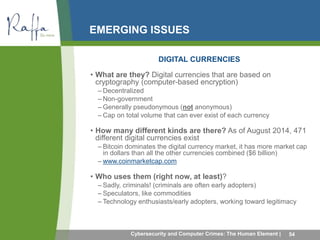
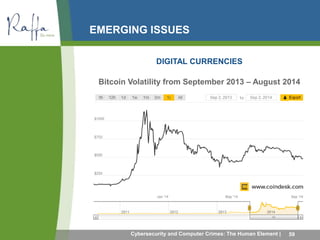
This document summarizes common computer crimes and cybersecurity issues. It discusses how computer crimes are defined and prosecuted, as well as types of computer-aided fraud such as manipulating computer inputs, programs, and outputs. Cybersecurity topics covered include firewalls, intrusion detection, denial of service attacks, dictionary attacks, and different types of malware like viruses, worms, Trojan horses, rootkits, botnets, and ransomware. The document also discusses social engineering frauds like pretexting and various forms of phishing.