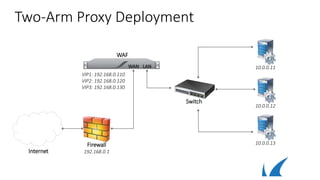
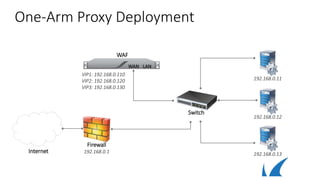
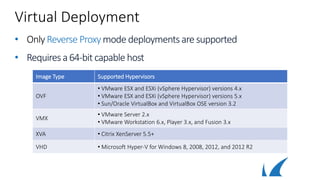
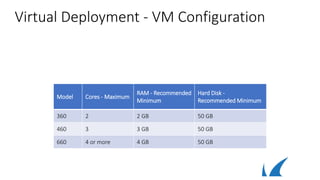
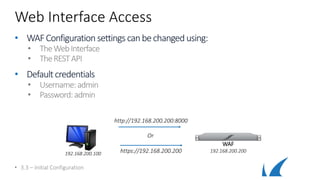
This document discusses different deployment options for a web application firewall (WAF). It covers physical appliance deployment, reverse proxy mode, bridge-path mode, virtual deployment, and public cloud hosting. It also provides information on initial WAF configuration steps like network settings, firmware updates, and activating subscriptions. Additionally, it outlines various service types that can be configured on the WAF like HTTP, HTTPS, FTP, and instant SSL services. Specific configuration examples are provided for SSL services and setting up HTTP and HTTPS services on the WAF.








![Instant SSL
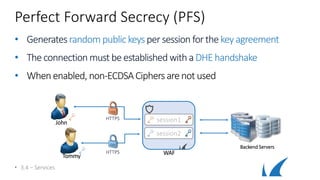
• Securesan HTTP webapplicationwith HTTPS
• Creates twoservices withsame VIP (HTTP[80] / HTTPS[443])
• RedirectsHTTP requeststo theHTTPS Service
• RewritesHTTP to HTTPS in response body
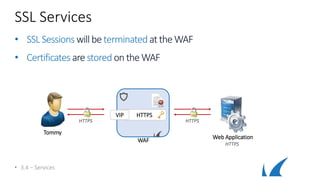
• 3.4 – Services
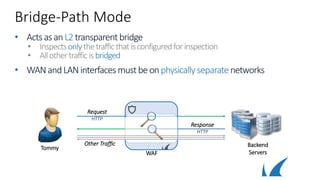
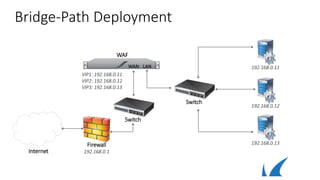
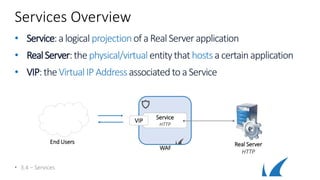
WAF
HTTP
HTTPS
VIP
Web Application
HTTP
Redirect to HTTPS
1st HTTP Request
HTTPWT
Response Rewrite
Tommy](https://image.slidesharecdn.com/3-180811073806/85/WAF-deployment-25-320.jpg)