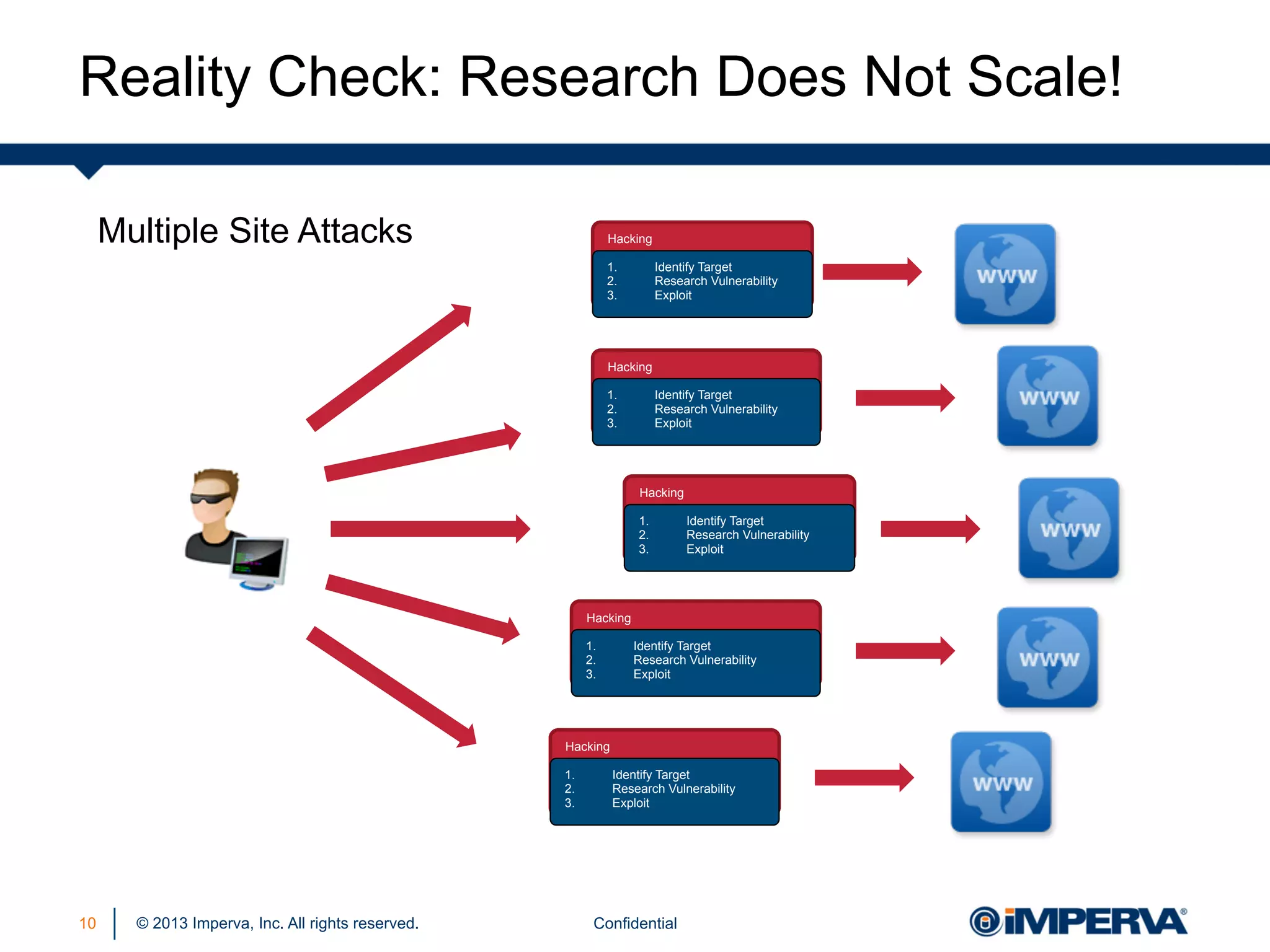
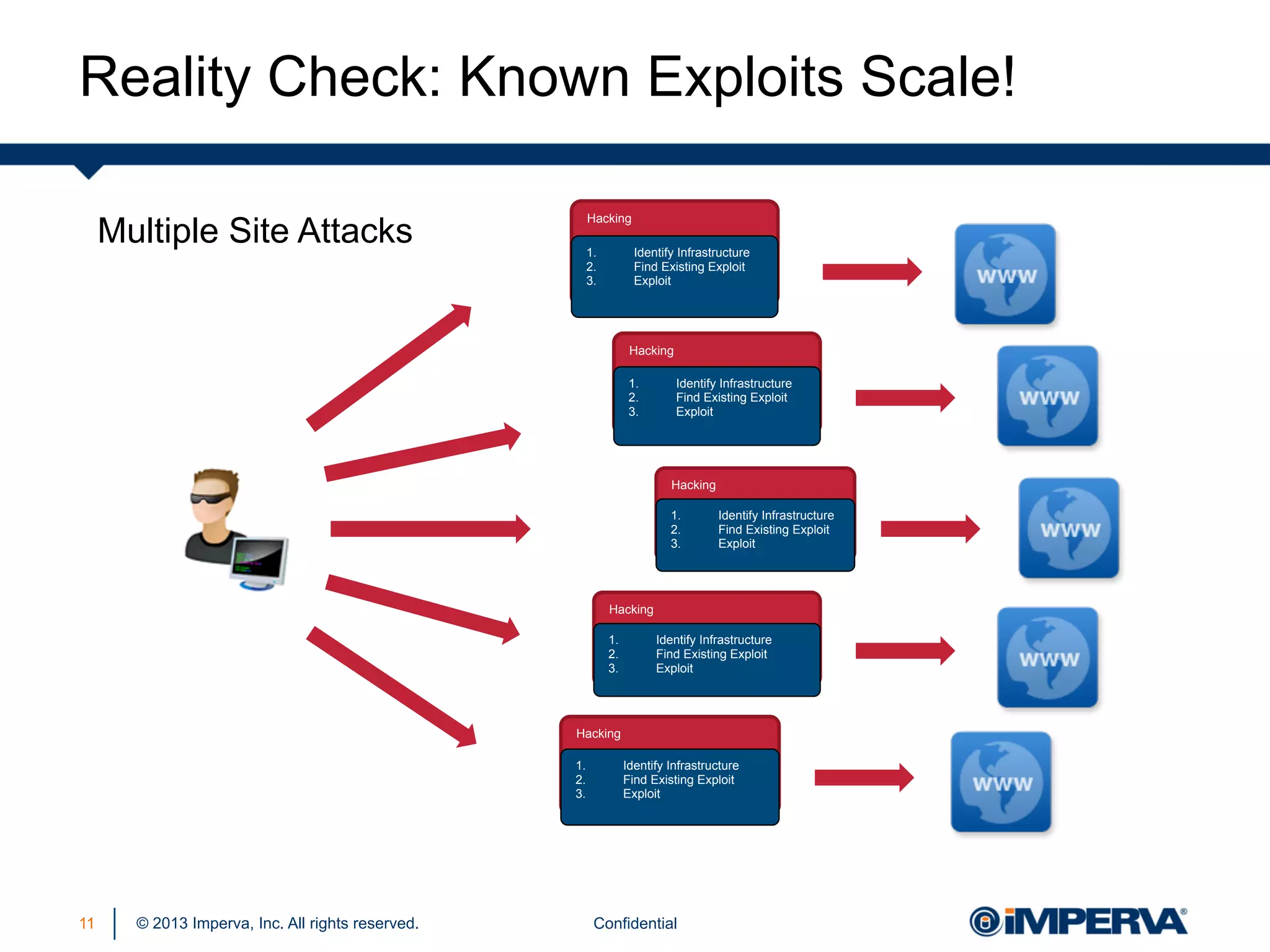
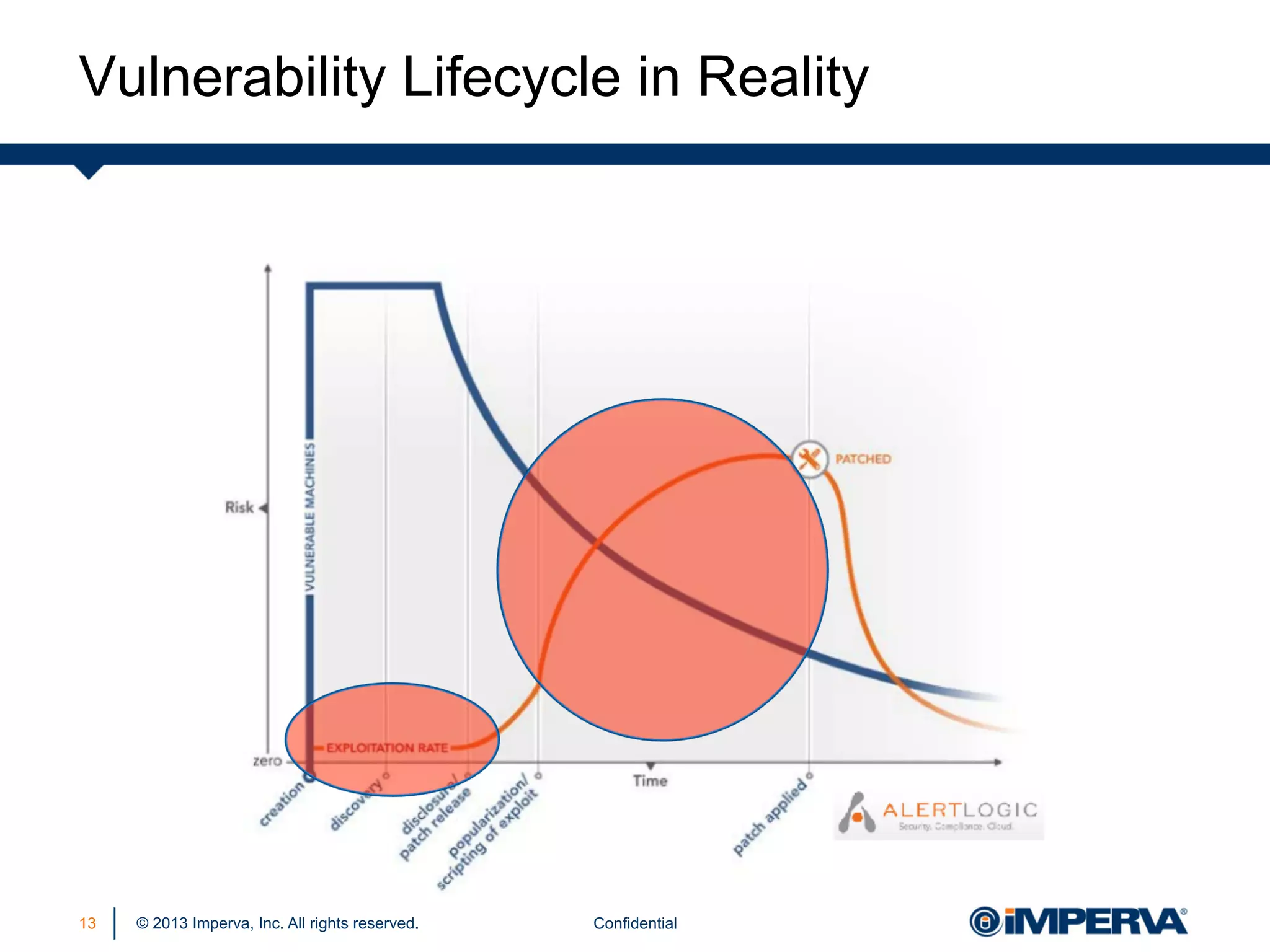
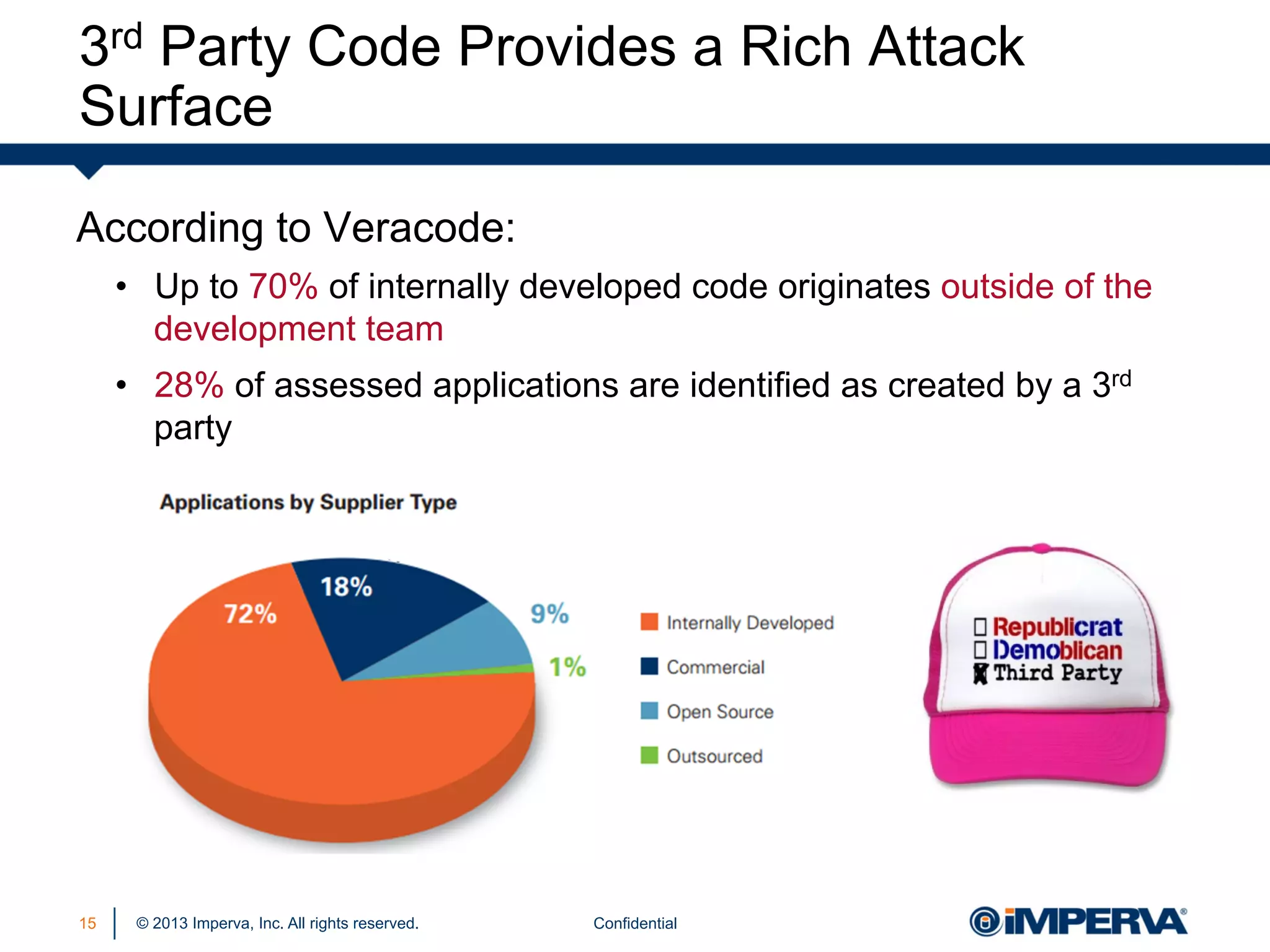
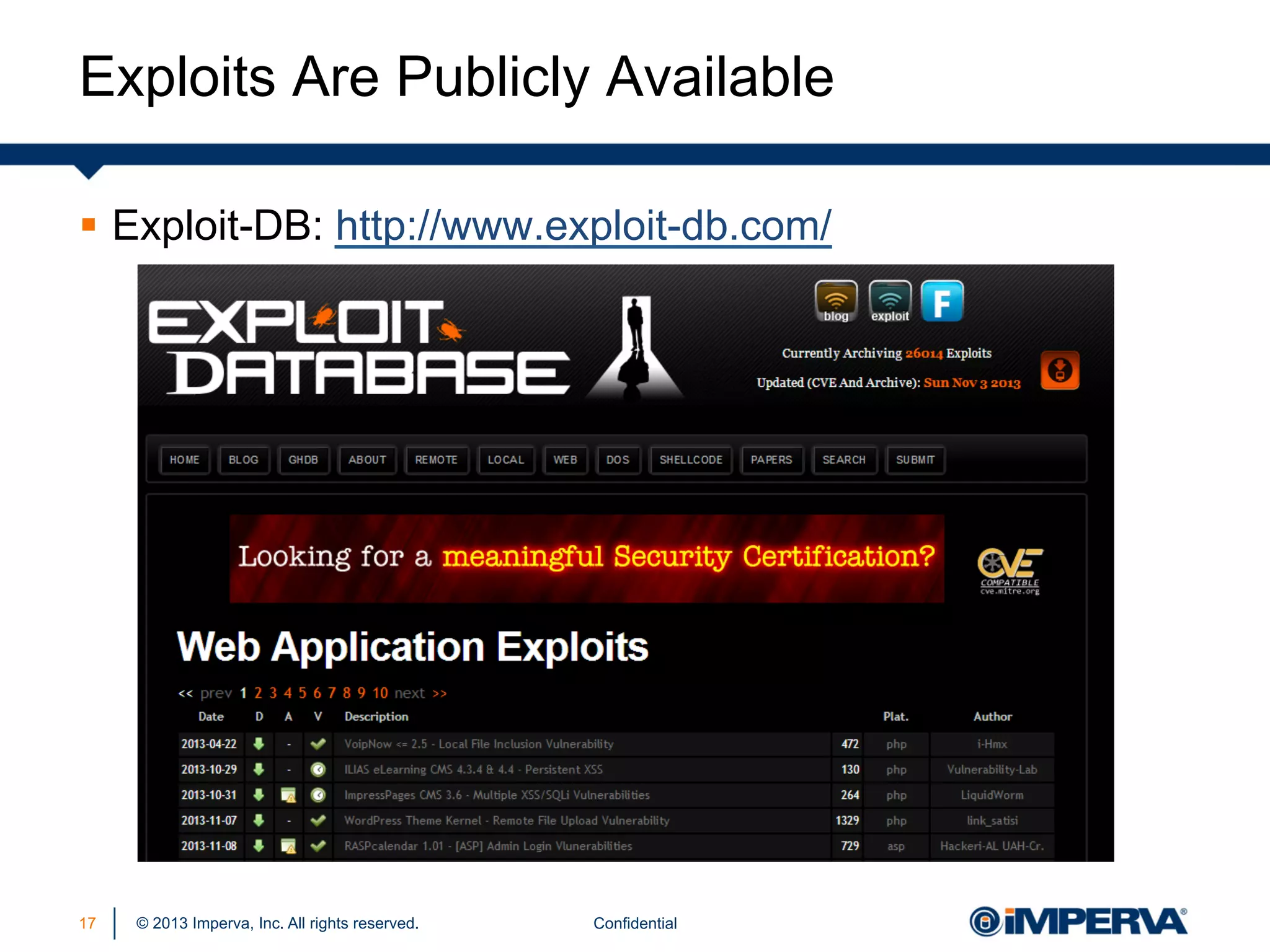
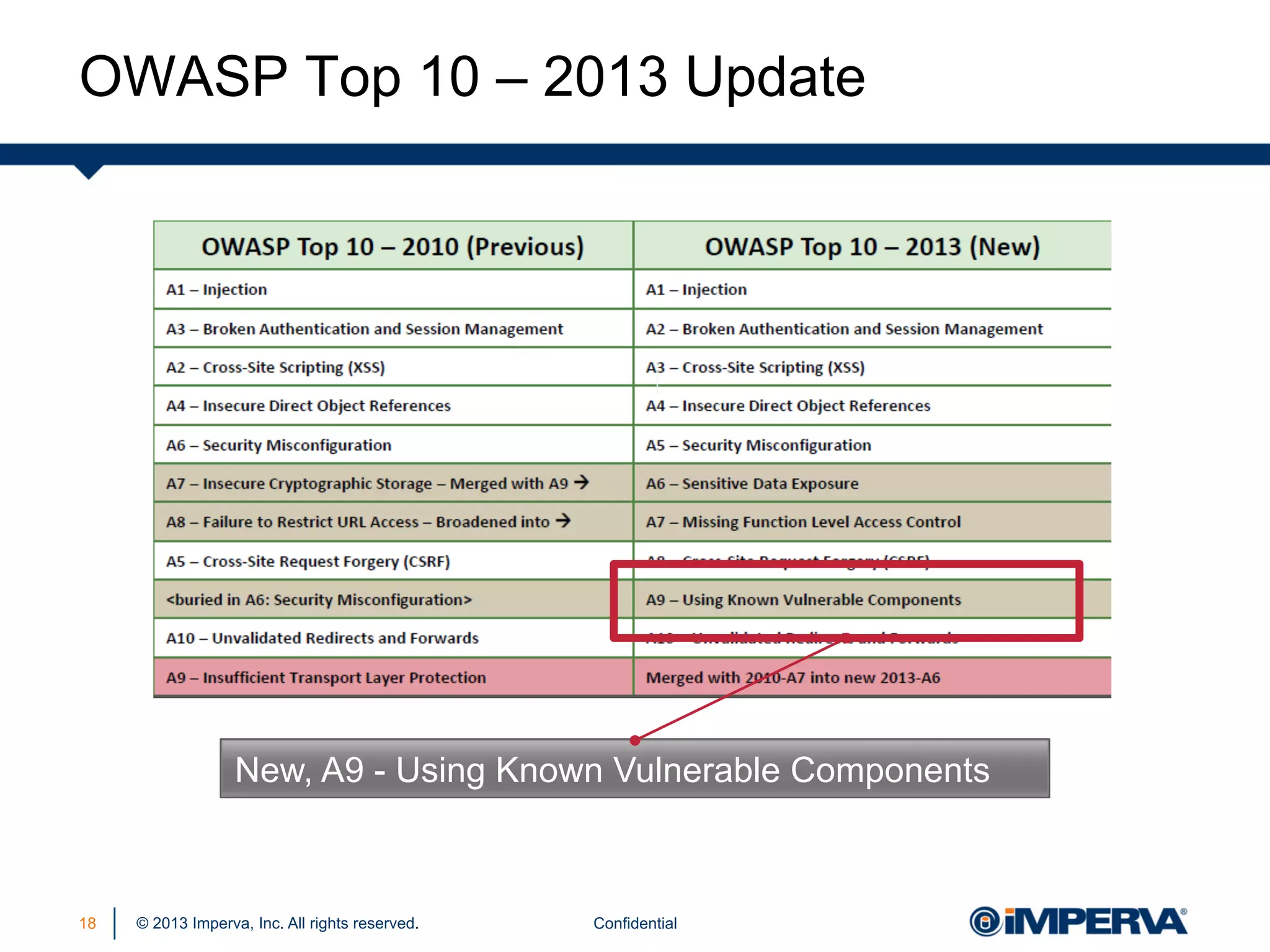
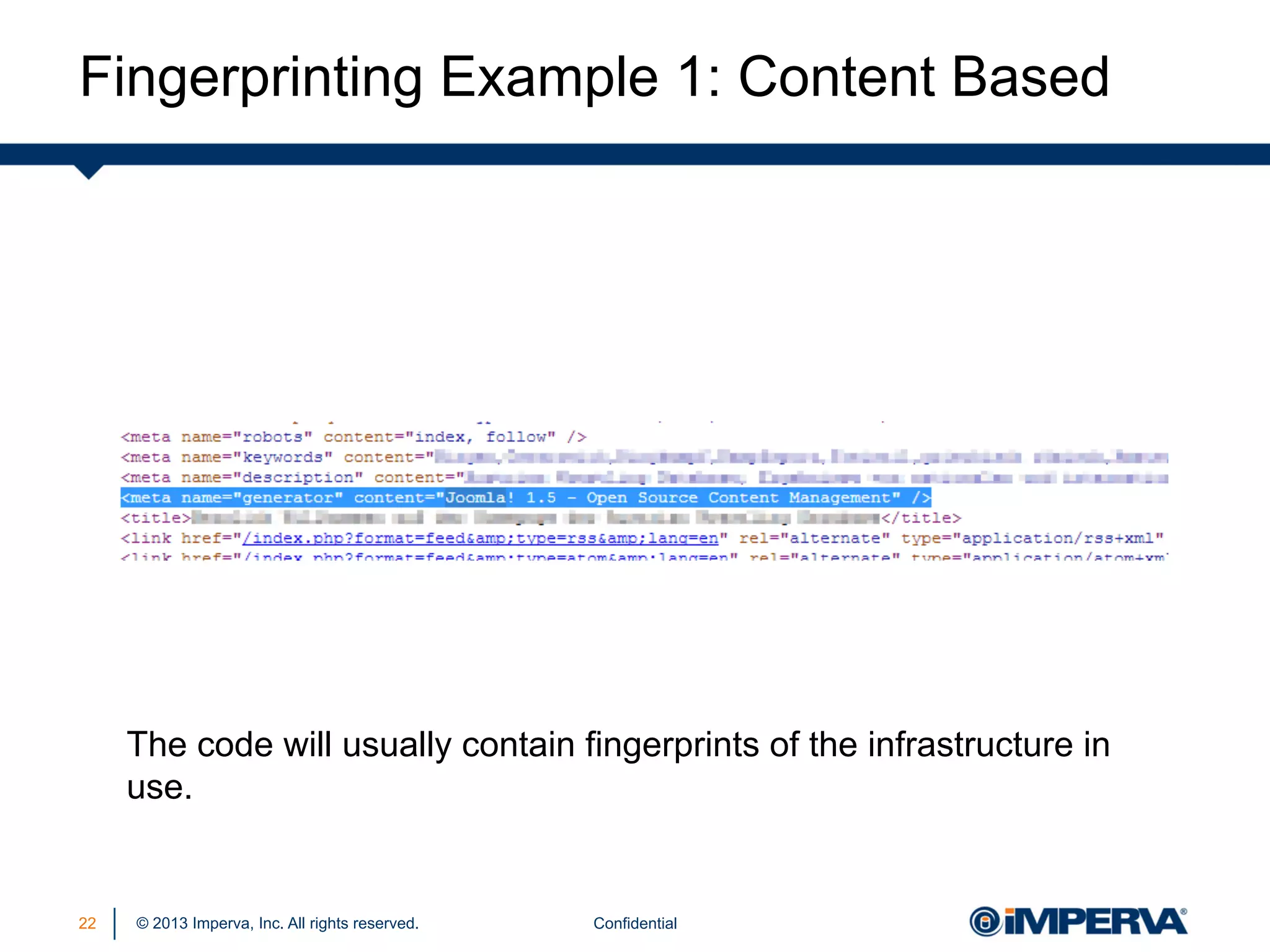
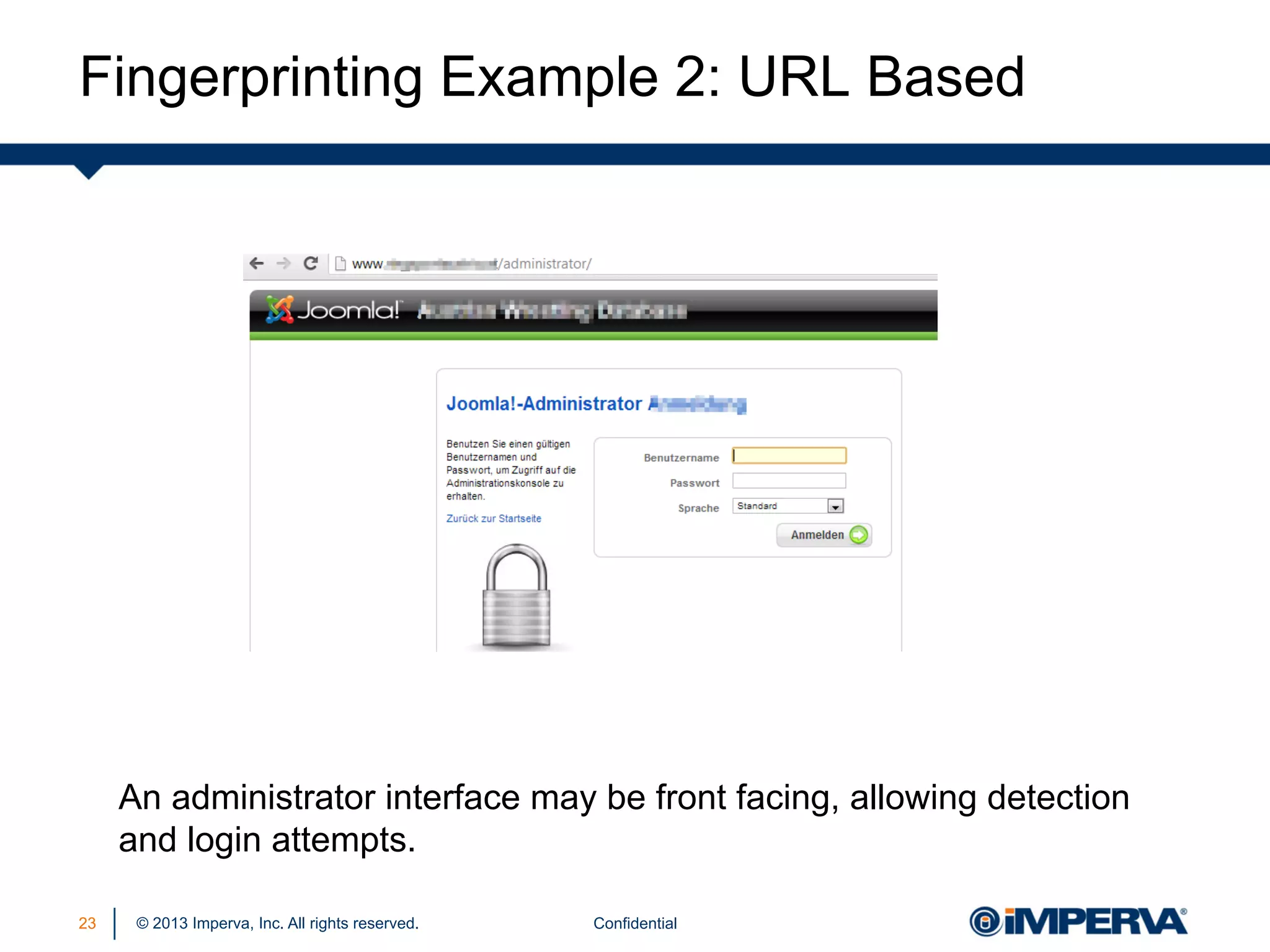
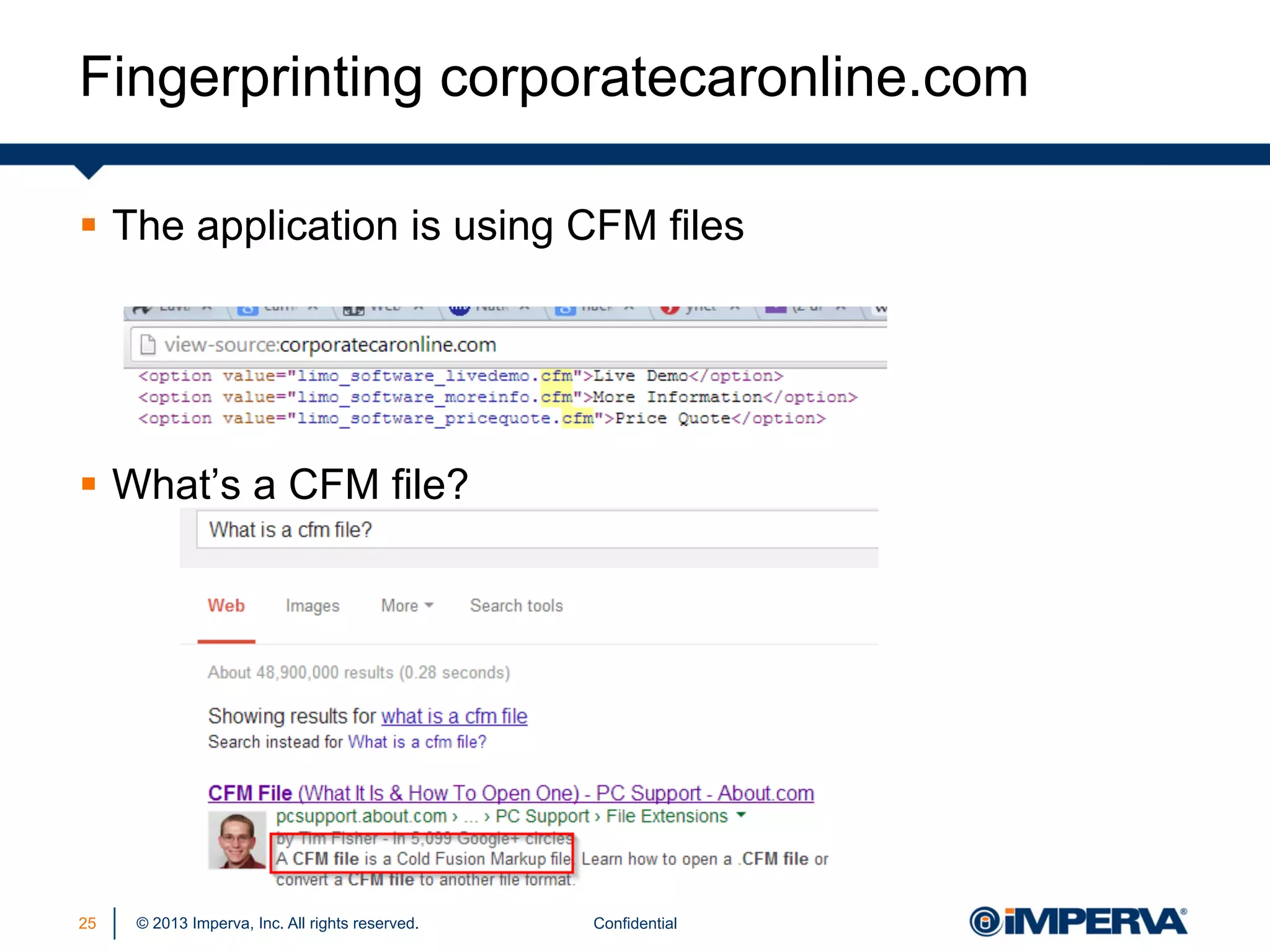
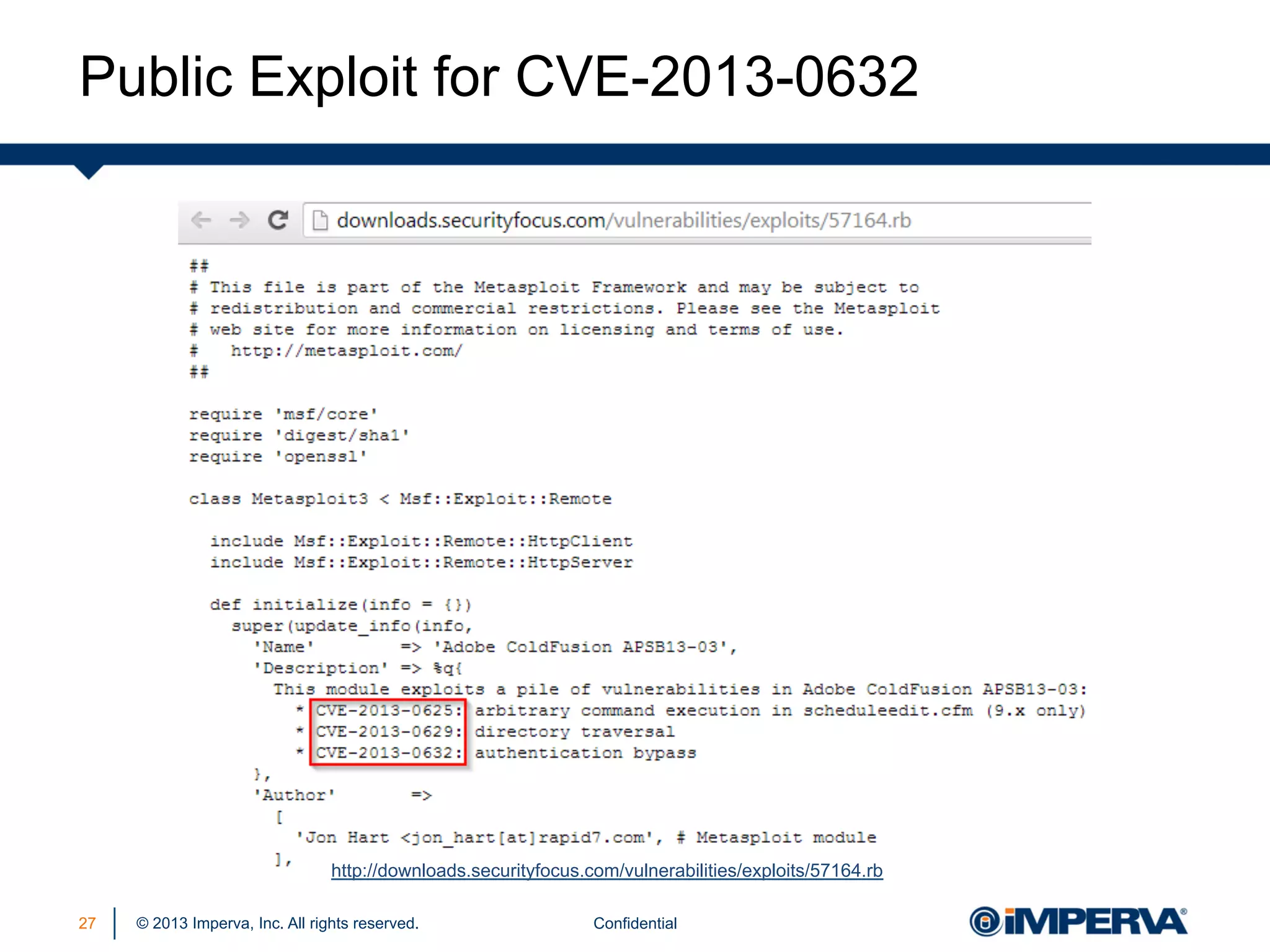
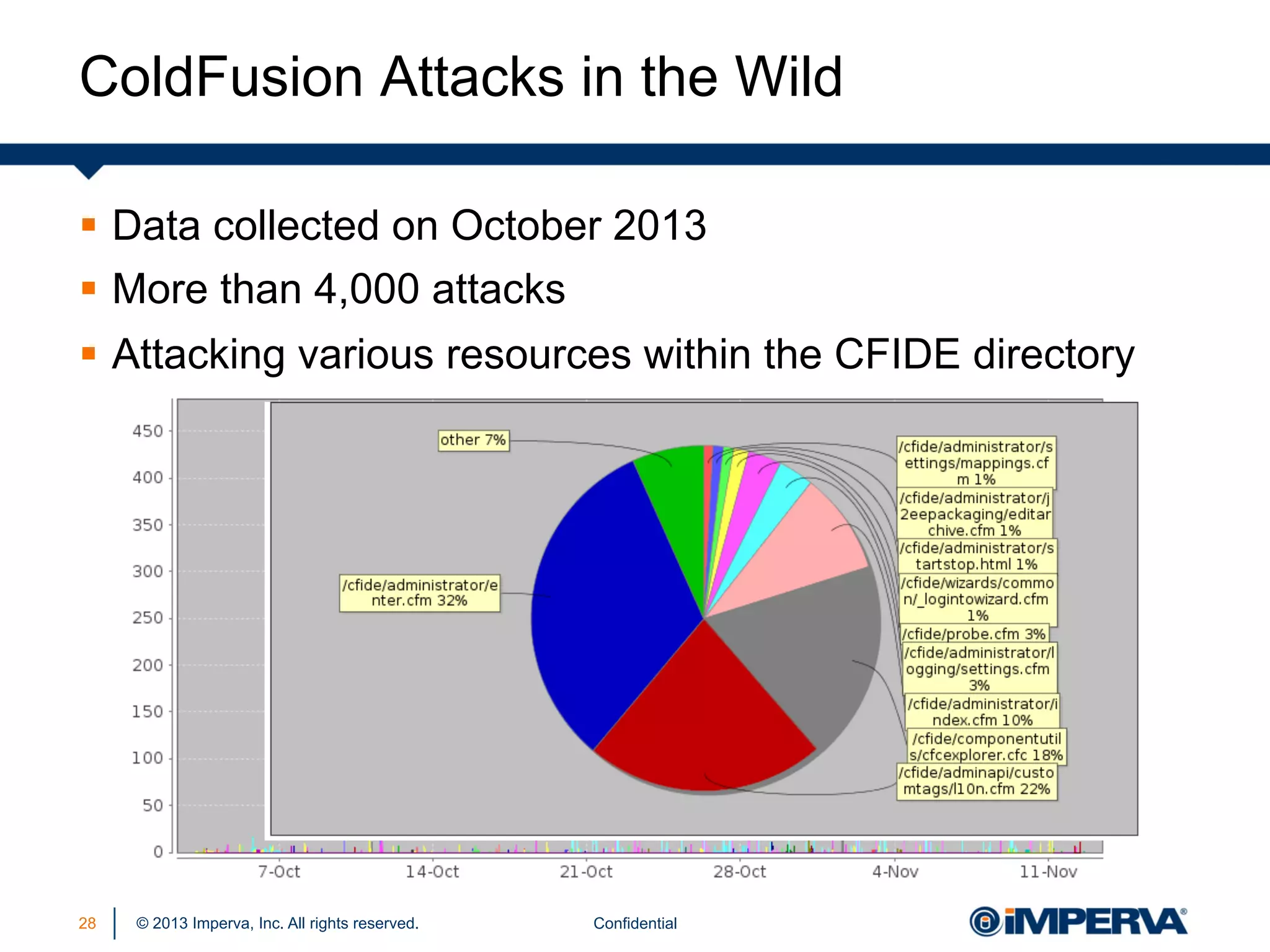
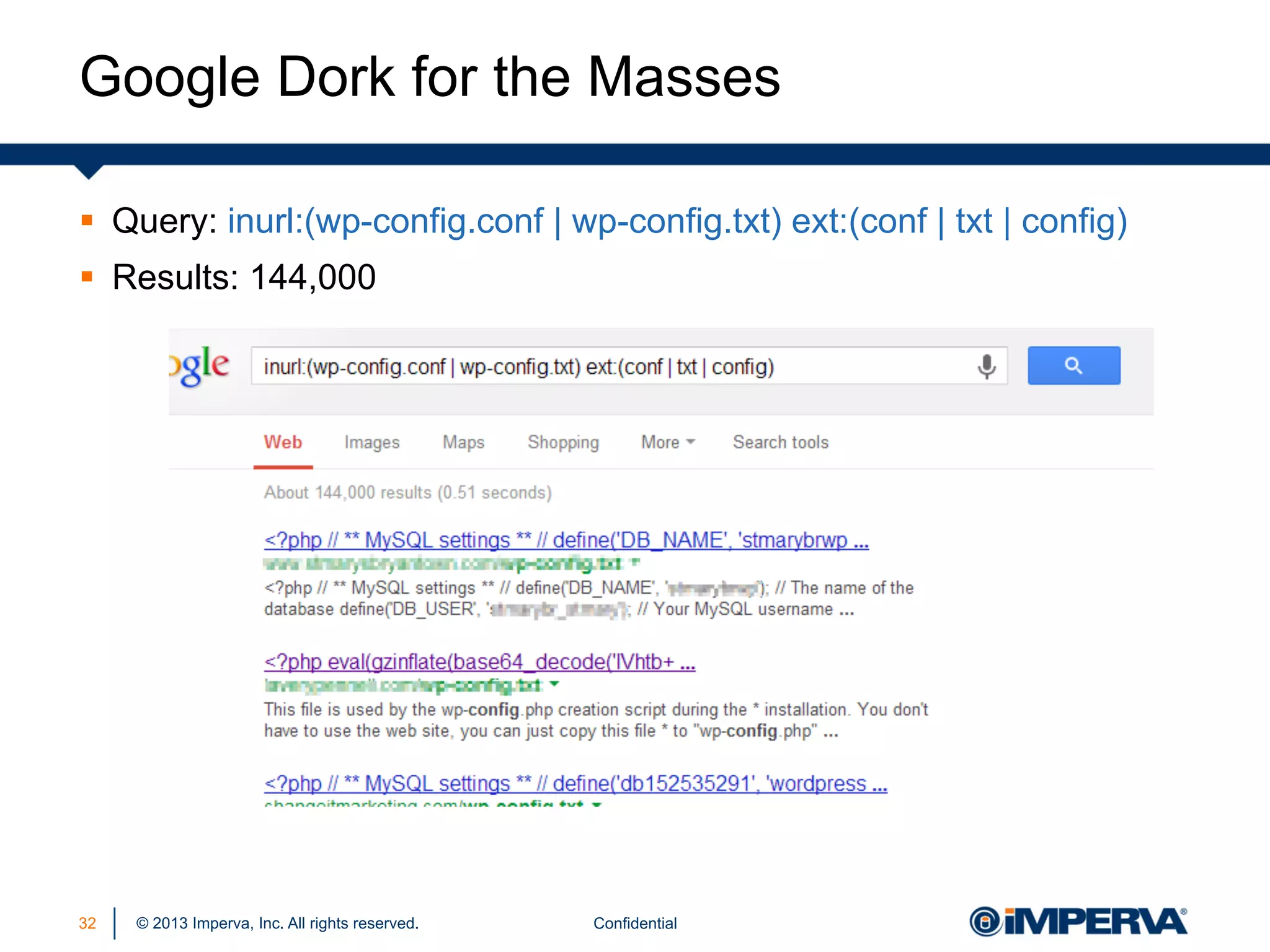
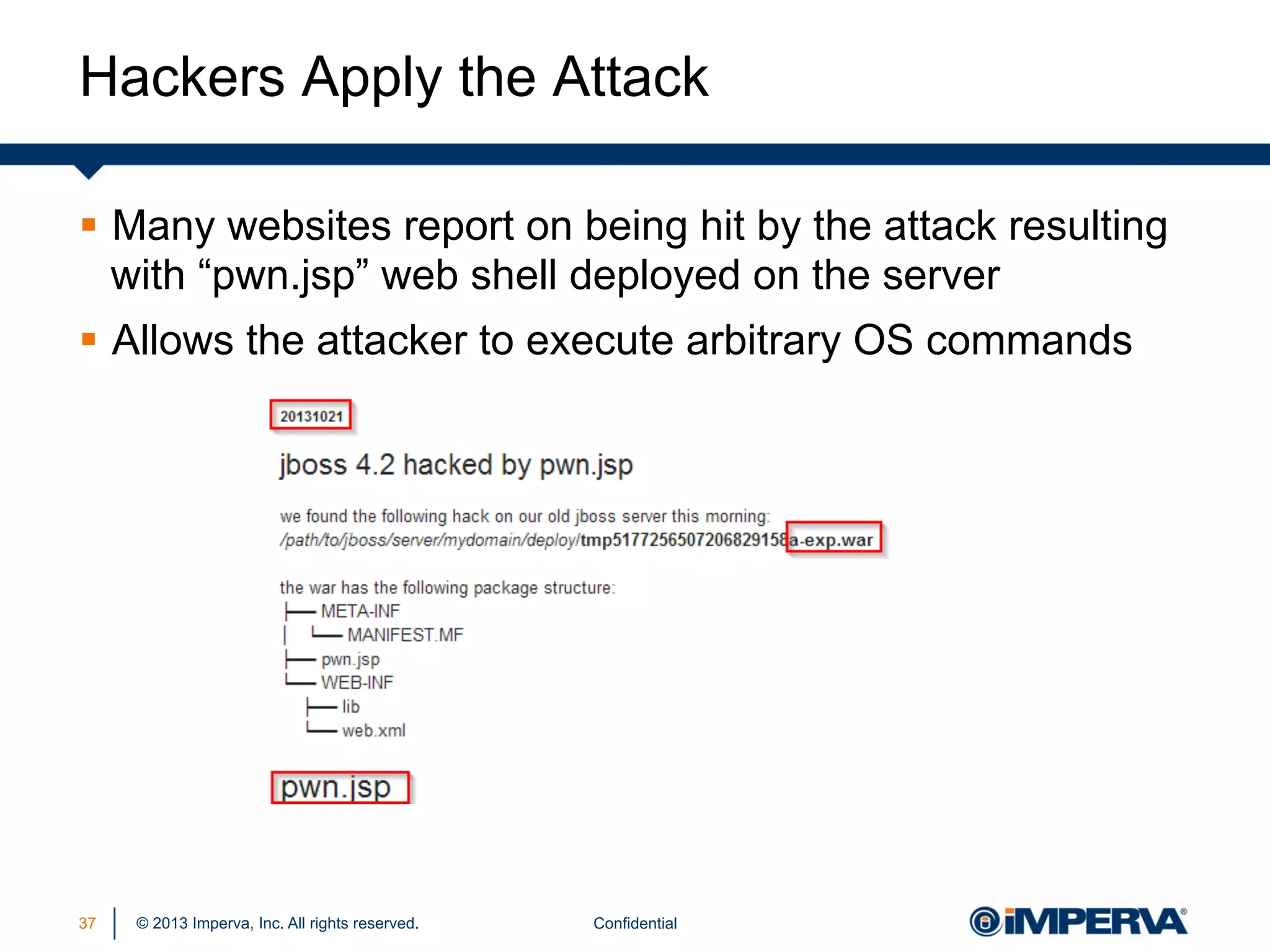
The document discusses the threat posed by known vulnerabilities in web applications, emphasizing that while zero-day exploits receive significant attention, known vulnerabilities are frequently exploited due to their prevalence and the ease of access to exploit codes. It outlines the anatomy of attacks targeting both specific and multiple victims, revealing the importance of understanding the vulnerability lifecycle and implementing robust security measures. Recommendations include proactive monitoring, third-party code assessments, and virtual patching to mitigate risks from existing vulnerabilities.