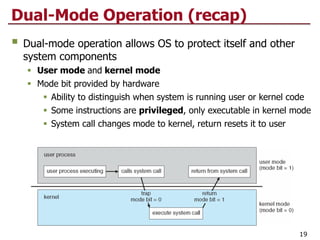
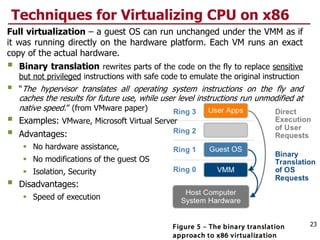
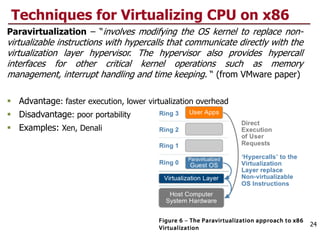
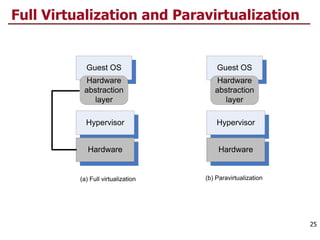
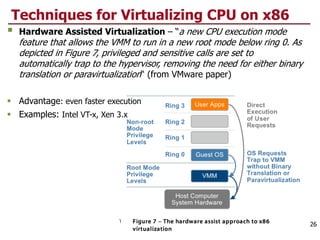
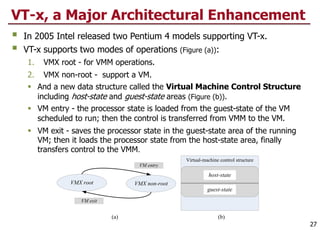
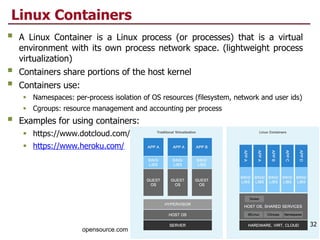
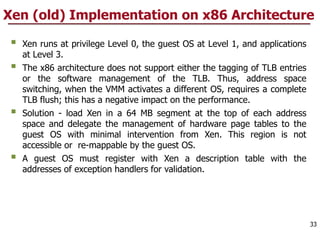
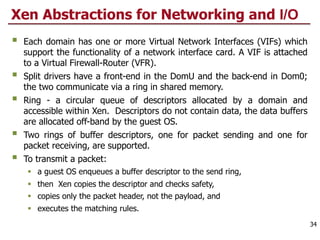
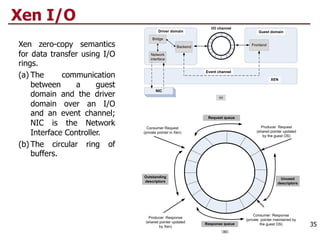
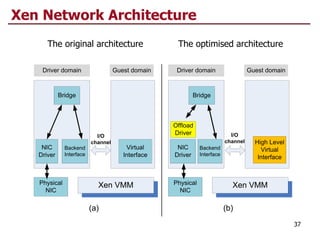
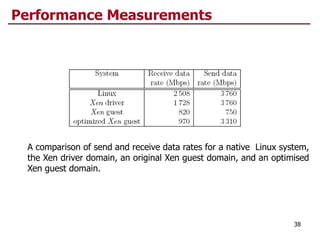
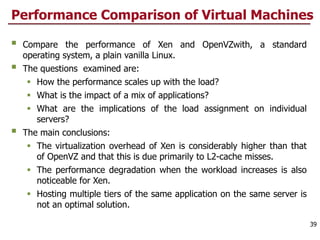
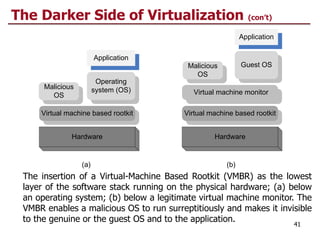
This document discusses virtualization and cloud computing. It begins by explaining the motivations for virtualization, such as managing resources more efficiently and allowing live migration of virtual machines. It then covers key concepts in virtualization like virtual machine monitors, full virtualization versus paravirtualization, and hardware assisted virtualization. Specific virtualization technologies are discussed like Xen, a popular open source hypervisor based on paravirtualization. The document also covers challenges in virtualizing the x86 CPU architecture.