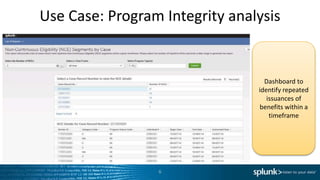
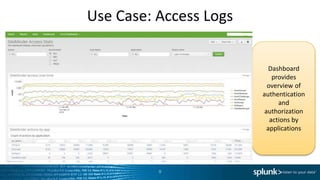
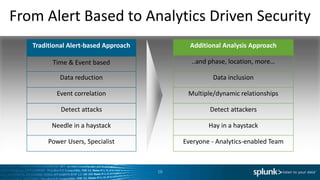
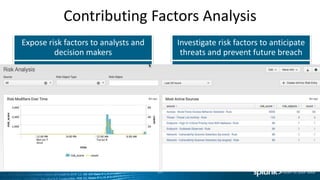
The document discusses the implementation of Splunk at a large state health and human services agency to improve security monitoring, compliance reporting, and program integrity detection. It highlights the agency's challenges with incident investigation, data correlation, and compliance reporting, demonstrating significant efficiency gains with Splunk compared to previous methods. The document also emphasizes the importance of adapting security operations to evolving threats and the integration of various technologies and processes.