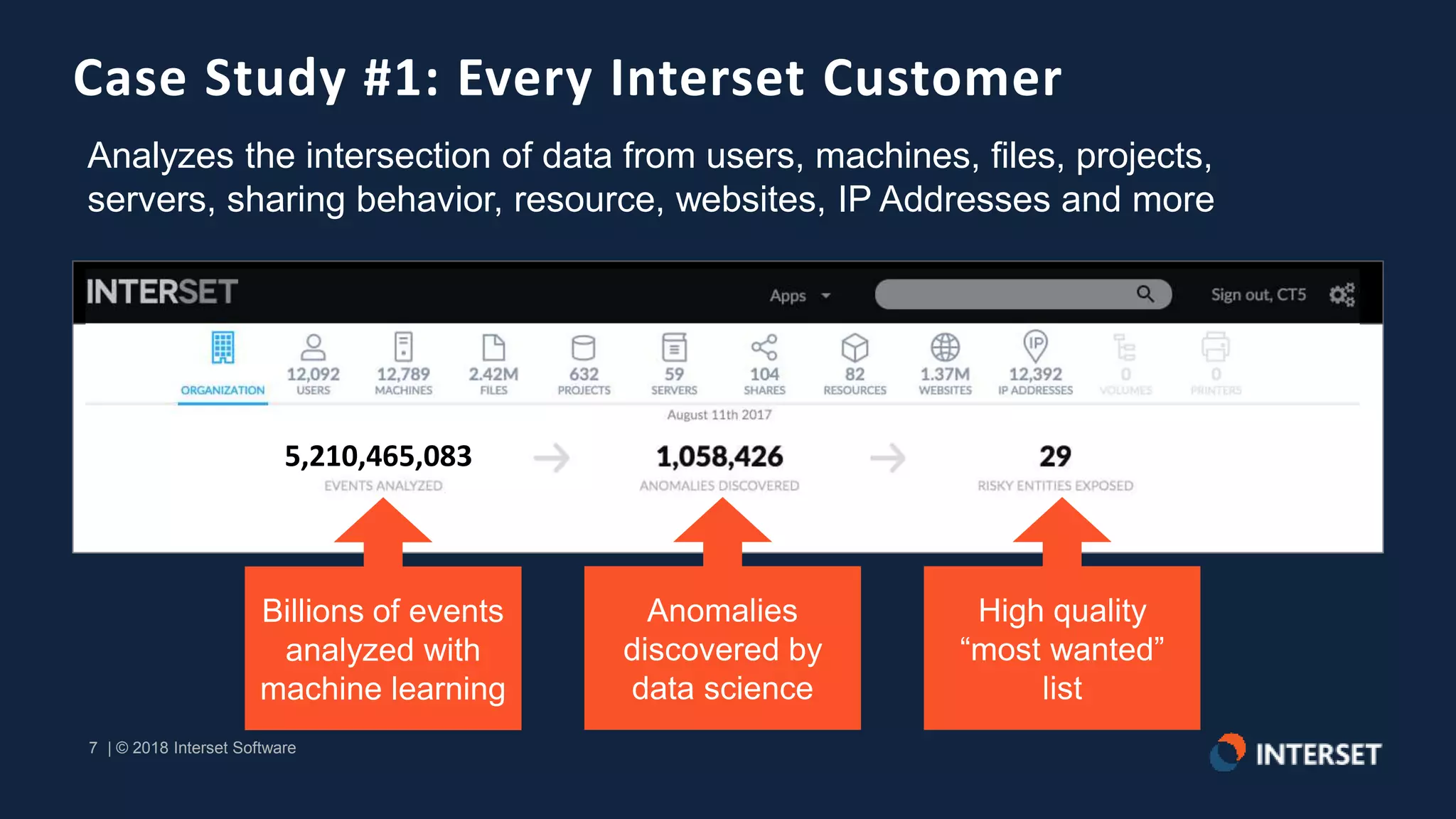
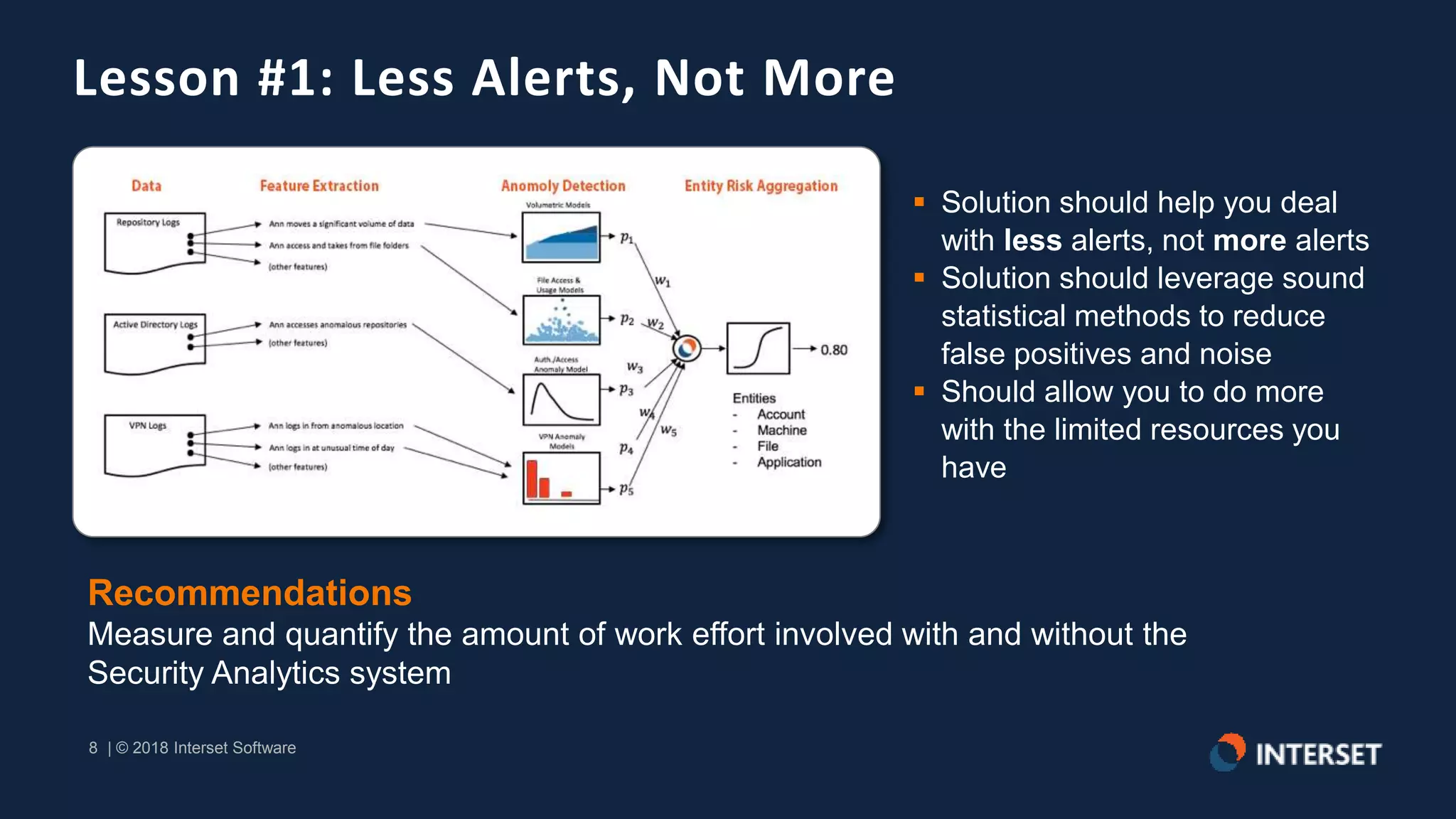
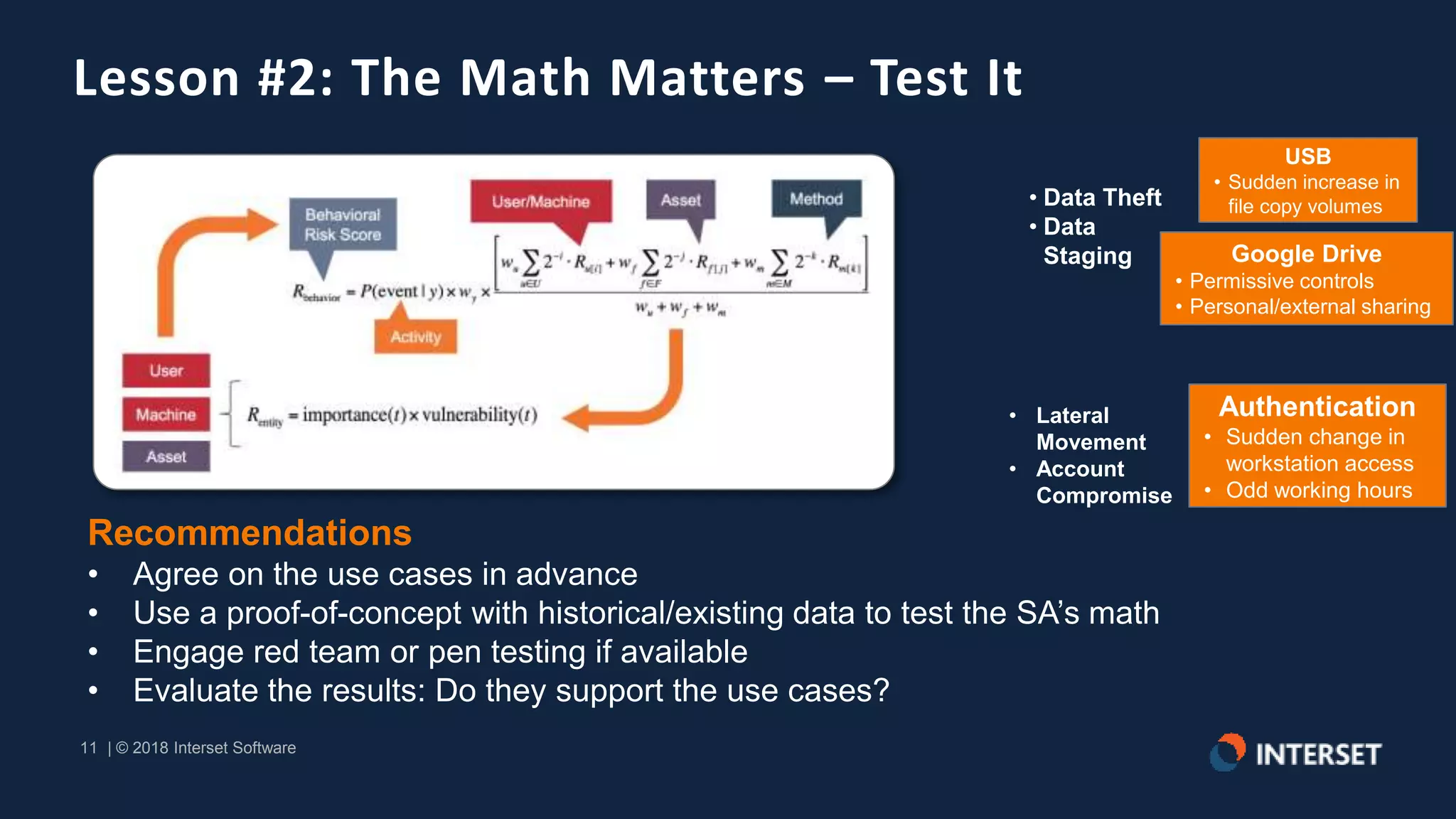
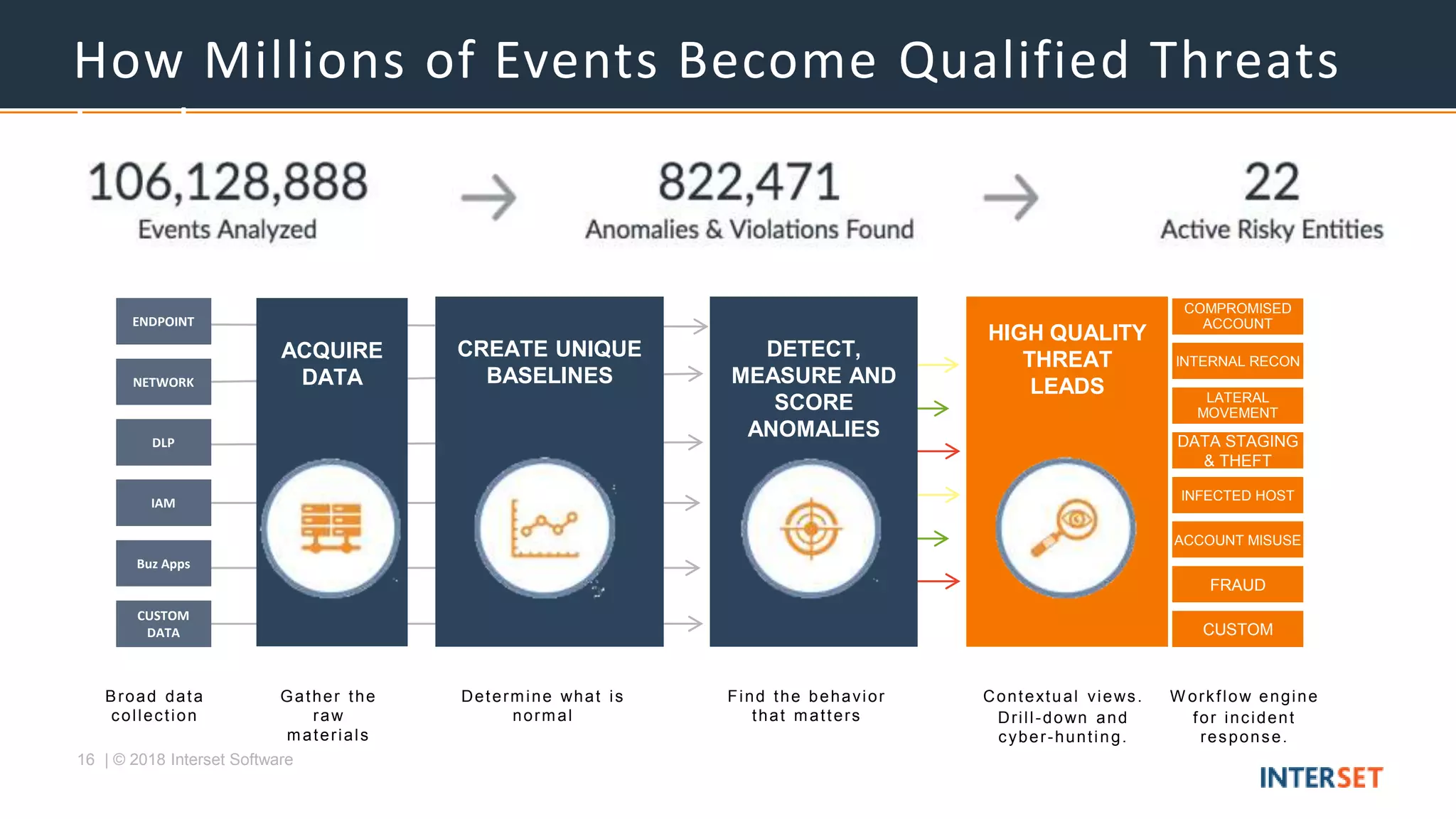
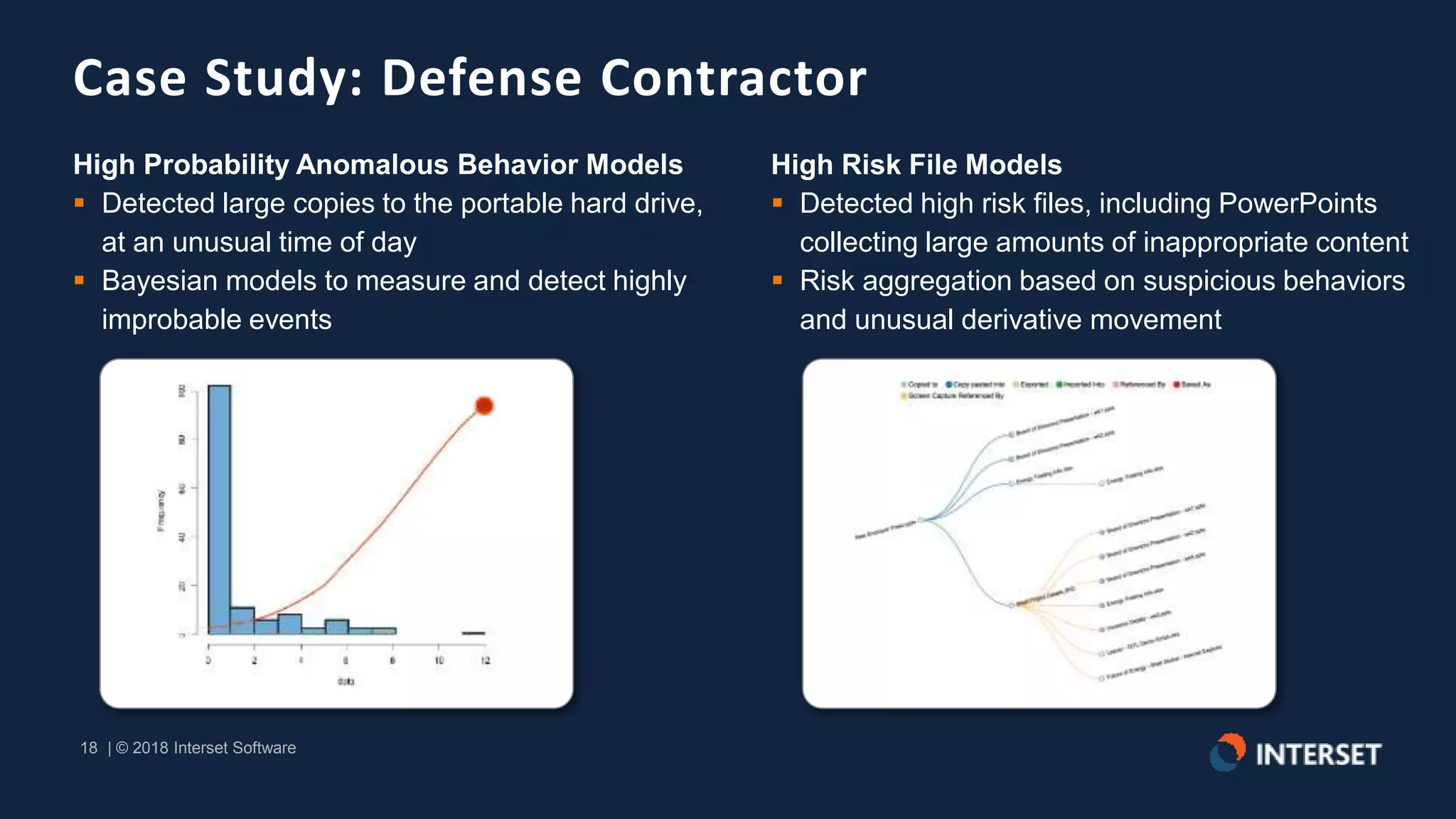
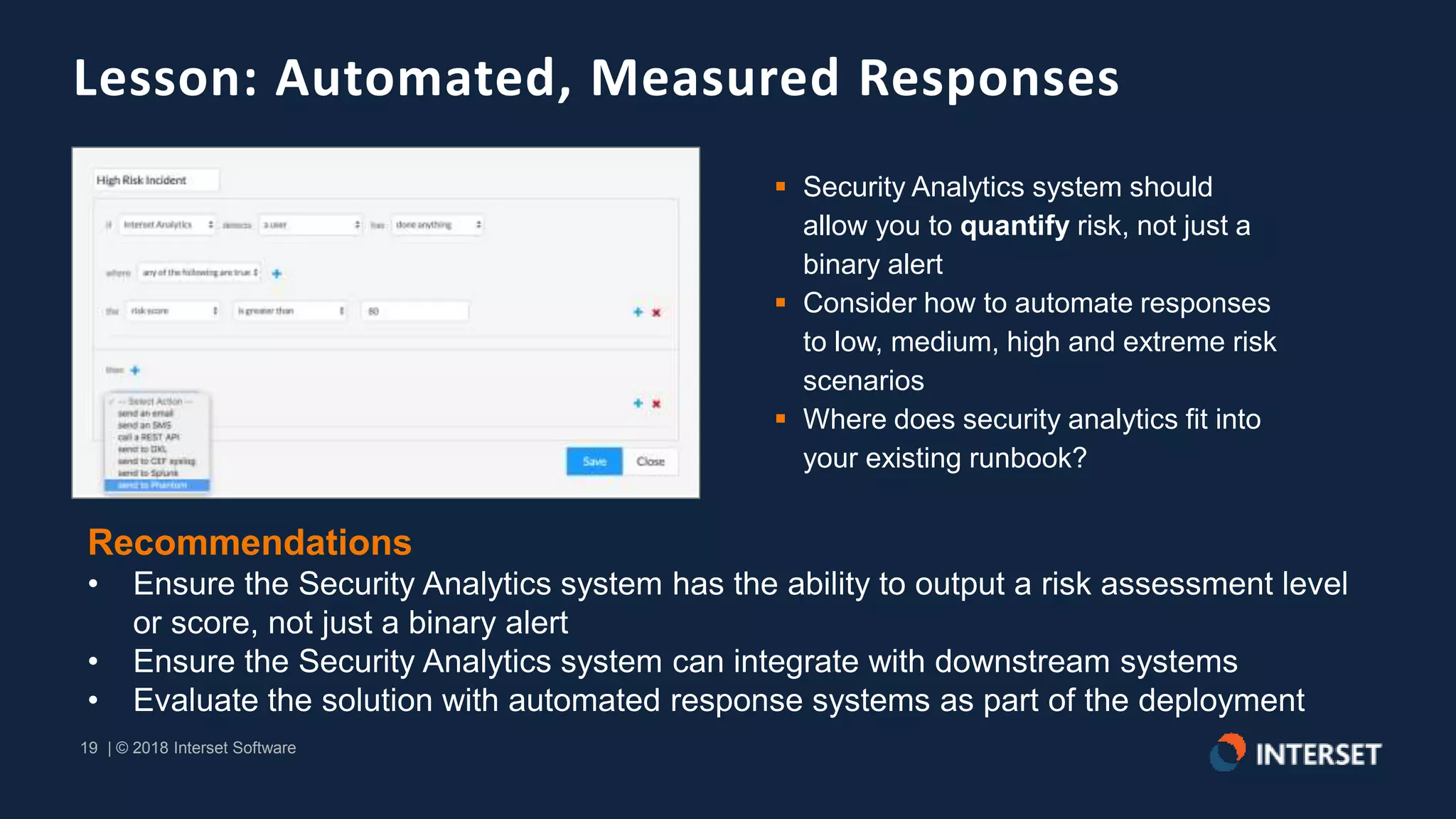
The document discusses the operationalization of big data security analytics, highlighting the integration of advanced analytics to enhance threat detection in cybersecurity. It presents multiple case studies demonstrating the effectiveness of machine learning in identifying anomalies and improving incident response, as well as lessons learned regarding alert management and meaningful metrics. Key recommendations include testing analytics systems, defining use cases, and ensuring automated and measured responses to threats.