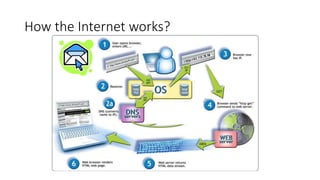
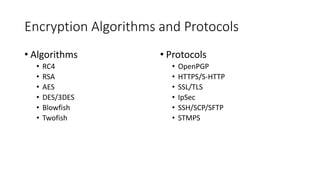
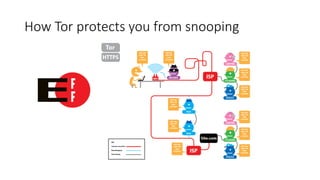
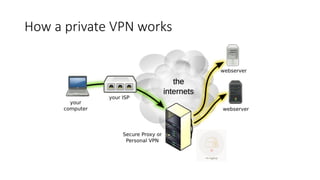
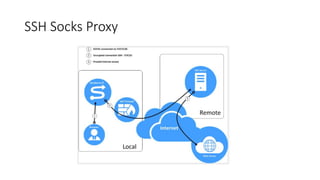
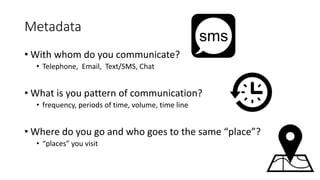
The document outlines the concept of a crypto party as a grassroots movement aimed at educating the public about practical cryptography tools and methods to enhance privacy and security online. It details various encryption practices, including symmetric and asymmetric encryption, hashing algorithms, and the importance of tools like VPNs and Tor for safeguarding user data. Additionally, it highlights potential vulnerabilities and emphasizes the significance of understanding metadata and online communication patterns.