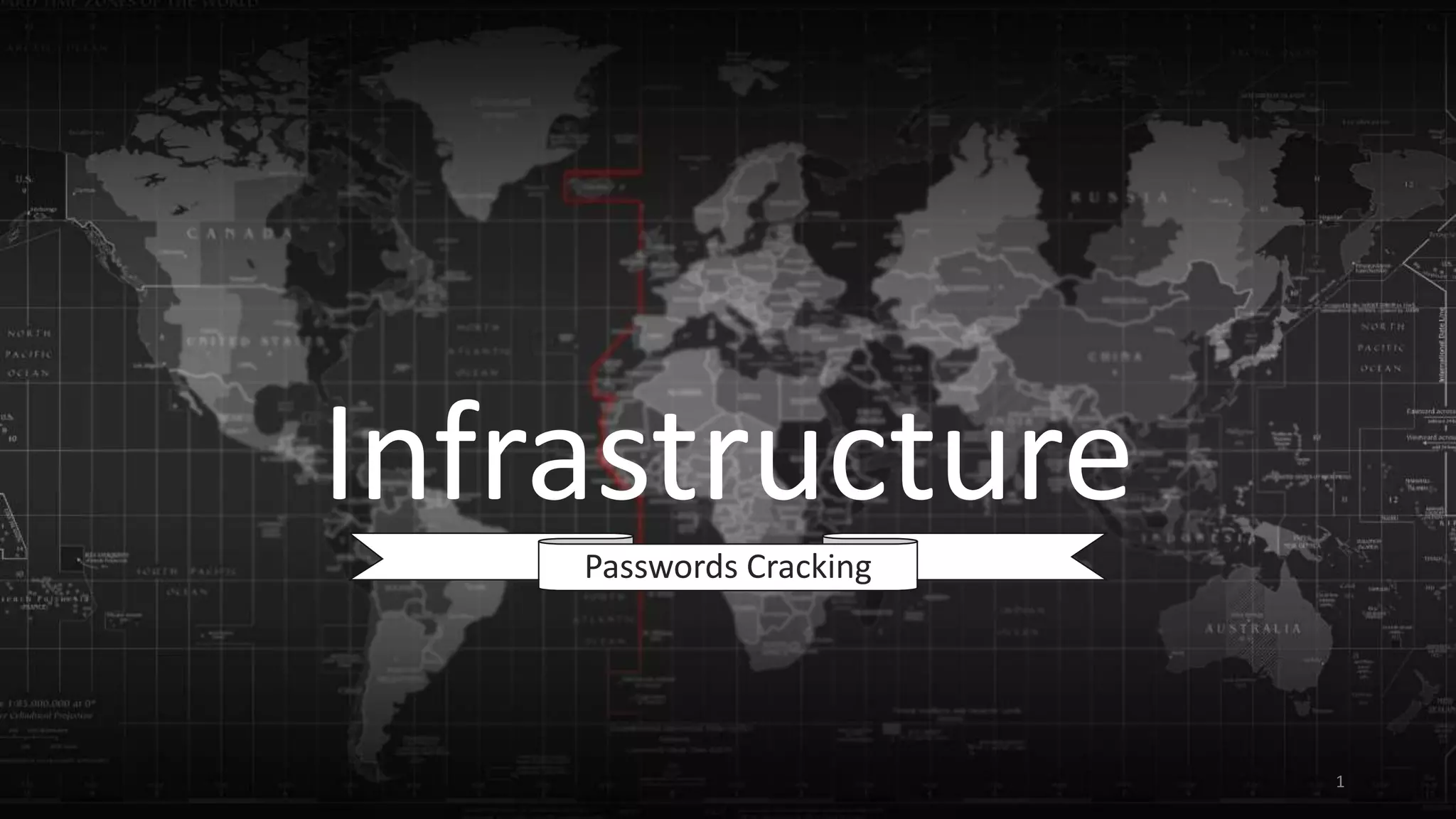
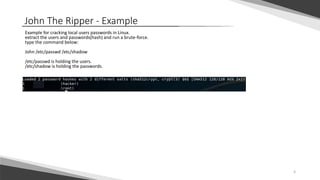
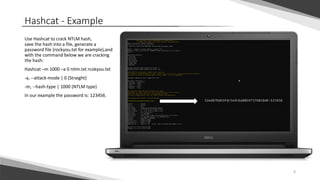
Password cracking is the process of exposing passwords from data stored on a computer or transmitted over a network. Common techniques include brute force attacks that try all possible password guesses against a cryptographic hash of the password. John the Ripper and Hashcat are popular password cracking tools that can perform brute force cracking of various hashed password formats from Linux, Windows, and other systems. The tools allow generating wordlists and combining techniques to improve cracking efficiency.