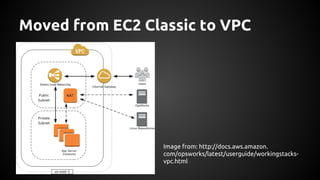
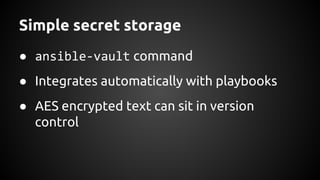
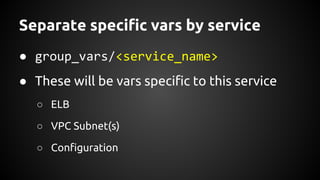
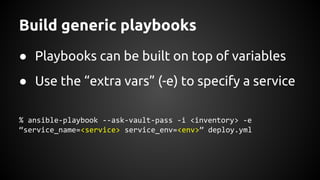
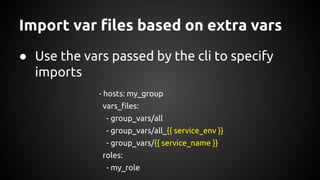
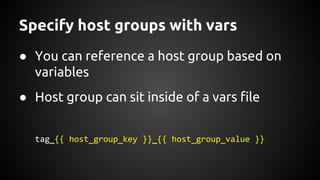
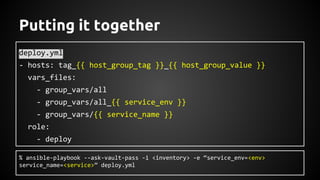
Andrew Hamilton presented on using Ansible for deploying to cloud environments. He discussed that Ansible was chosen to provide a simple and repeatable way to build services and deploy them to configured environments. It allows deploying to multiple languages and cloud platforms. Ansible uses a simple execution model and YAML files. Its key advantages include being agentless over SSH, supporting dynamic inventories, and having modules for common tasks. Hamilton provided tips for using Ansible effectively in cloud environments, such as using dynamic inventories, separating variables, and testing changes thoroughly.




















![Examples of what we put in there
group_vars/all
ansible_ssh_private_key_file: ~/.ssh/{{ key_name | default(service_name) }}.pem
ansible_ssh_user: "{{ remote_user }}"
remote_user:"{{aws_config[my_ec2_region]['remote_user'] | default('ec2-user')}}"
my_ec2_region: "{{ lookup('env', 'EC2_REGION') }}"
default_service_dir: /usr/local/prevoty
java_version: 1.8.0_25
java_home: /opt/jre{{ java_version }}
go_version: go1.4.1](https://image.slidesharecdn.com/usingansiblefordeployingincloudenvironments-150224125514-conversion-gate02/85/Using-Ansible-for-Deploying-to-Cloud-Environments-26-320.jpg)



![Hash merging example
group_vars/all
aws_config : {
“us-west-1” : {
“ami_id” : “ami-00112233”,
“rds_url” : <west_url>,
},
“us-east-1” : {
“ami_id” : “ami-44556677”,
“rds_url” : <west_url>,
}
}
group_vars/<service_name>
aws_config : {
“us-west-1” : {
“elb_name” : <west_elb>,
“vpc_subnet” : [<west_subnet>],
},
“us-east-1” : {
“elb_name” : <east_elb>,
“vpc_subnet” : [<east_subnet>],
}
}](https://image.slidesharecdn.com/usingansiblefordeployingincloudenvironments-150224125514-conversion-gate02/85/Using-Ansible-for-Deploying-to-Cloud-Environments-35-320.jpg)
![Hash merging example cont’d
result
aws_config : {
“us-west-1” : {
“ami_id” : “ami-00112233”,
“rds_url” : <west_url>,
“elb_name” : <west_elb>,
“vpc_subnet” : [<west_subnet>],
},
“us-east-1” : {
“ami_id” : “ami-44556677”,
result cont’d
“rds_url” : <west_url>,
“elb_name” : <east_elb>,
“vpc_subnet” : [<east_subnet>],
}
}](https://image.slidesharecdn.com/usingansiblefordeployingincloudenvironments-150224125514-conversion-gate02/85/Using-Ansible-for-Deploying-to-Cloud-Environments-36-320.jpg)
![Hash merging example cont’d
● Easy access in playbooks based on region
ec2_region: {{ lookup(‘ENV’, ‘EC2_REGION’) }}
- or -
-e “ec2_region=<region>”
● Accessed by:
{{ aws_config[ec2_region][‘elb_name’] }}](https://image.slidesharecdn.com/usingansiblefordeployingincloudenvironments-150224125514-conversion-gate02/85/Using-Ansible-for-Deploying-to-Cloud-Environments-37-320.jpg)





![An example inventory
/tmp/inventory
[tag_<host_group_name>_<service_a>_new]
<service_a> ansible_ssh_host=10.0.xxx.yyy
[tag_<host_group_name>_<service_b>_new]
<service_b> ansible_ssh_host=10.0.xxx.yyy
[tag_<host_group_name>_<service_c>_new]
<service_c> ansible_ssh_host=10.0.xxx.yyy](https://image.slidesharecdn.com/usingansiblefordeployingincloudenvironments-150224125514-conversion-gate02/85/Using-Ansible-for-Deploying-to-Cloud-Environments-43-320.jpg)
