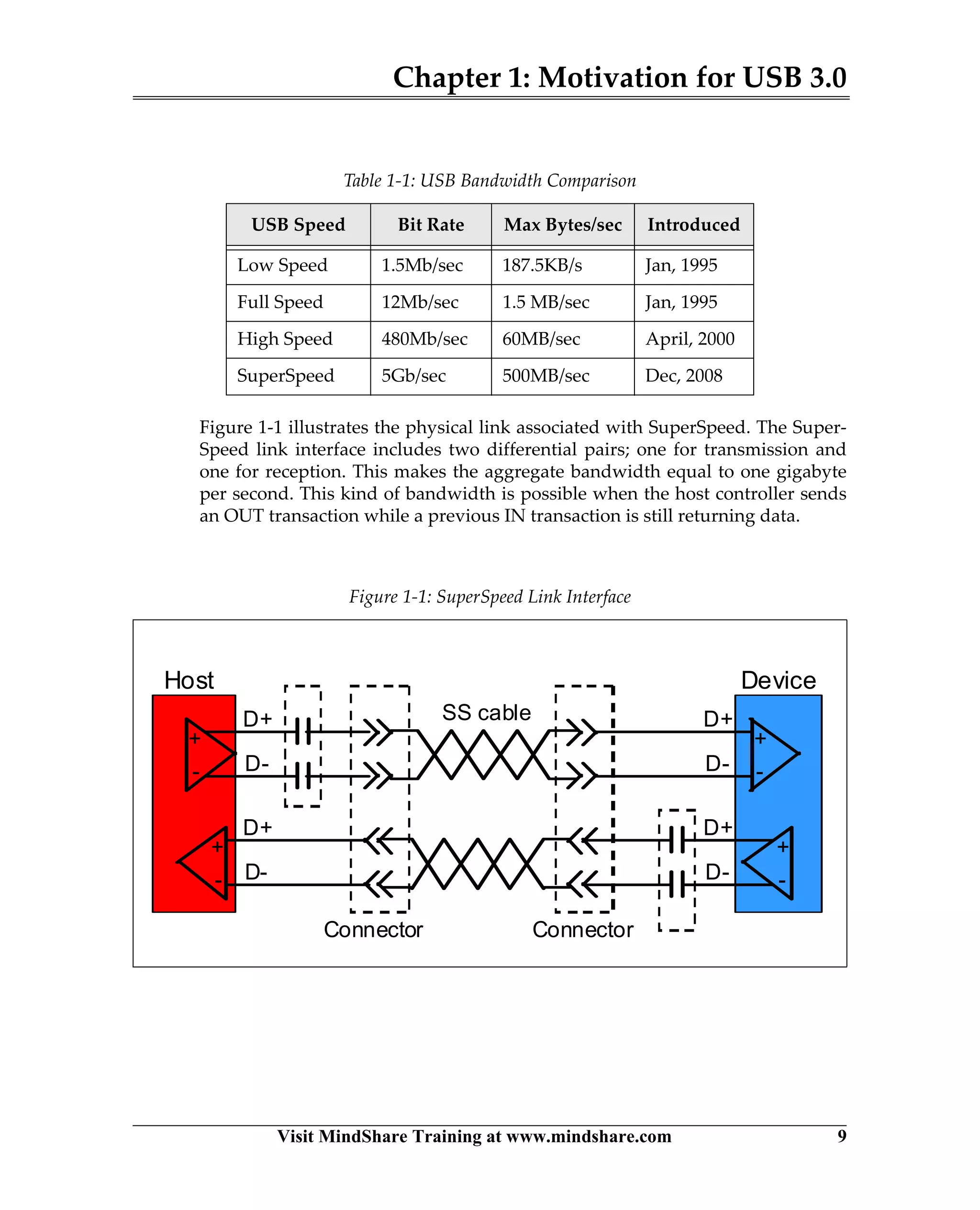
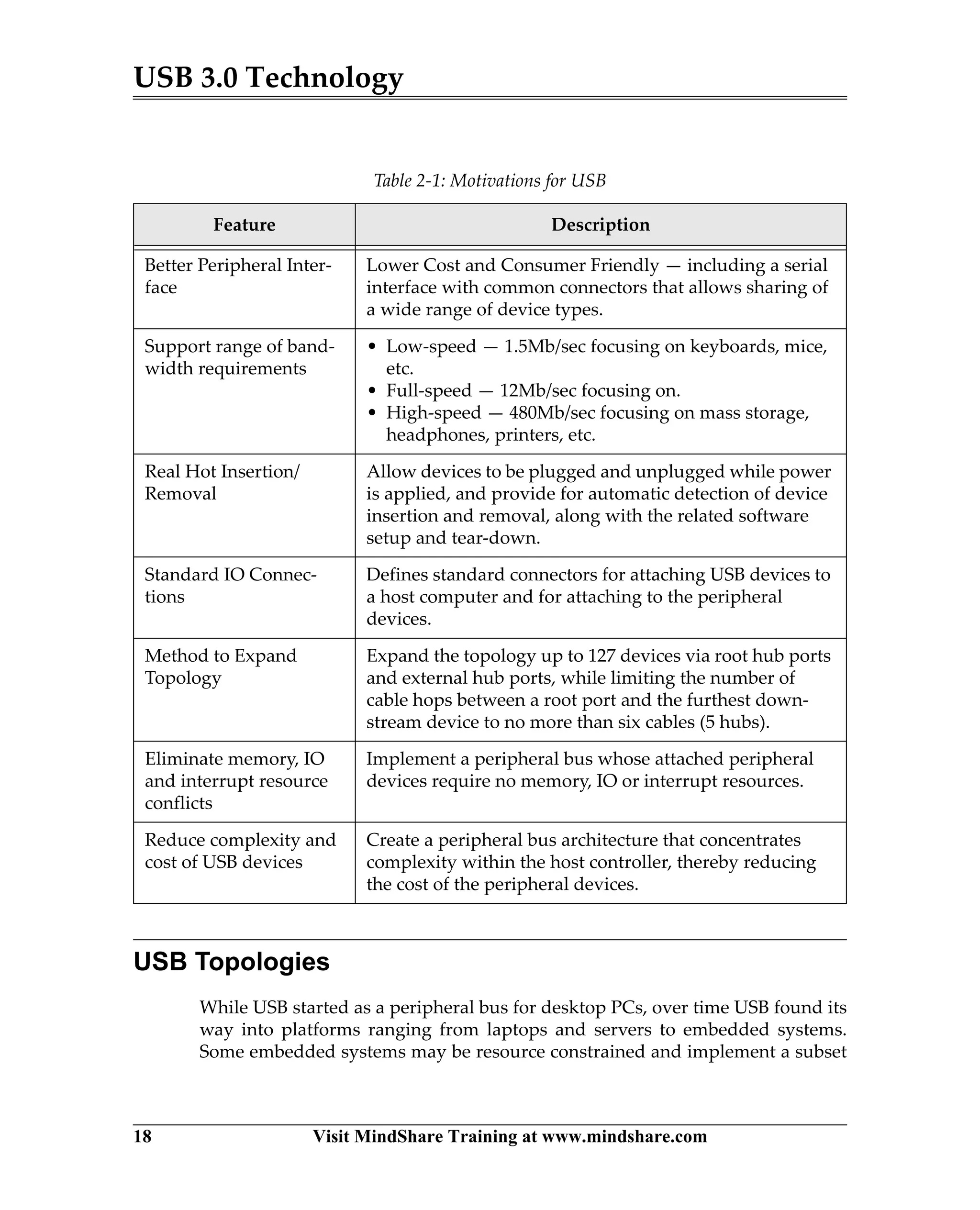
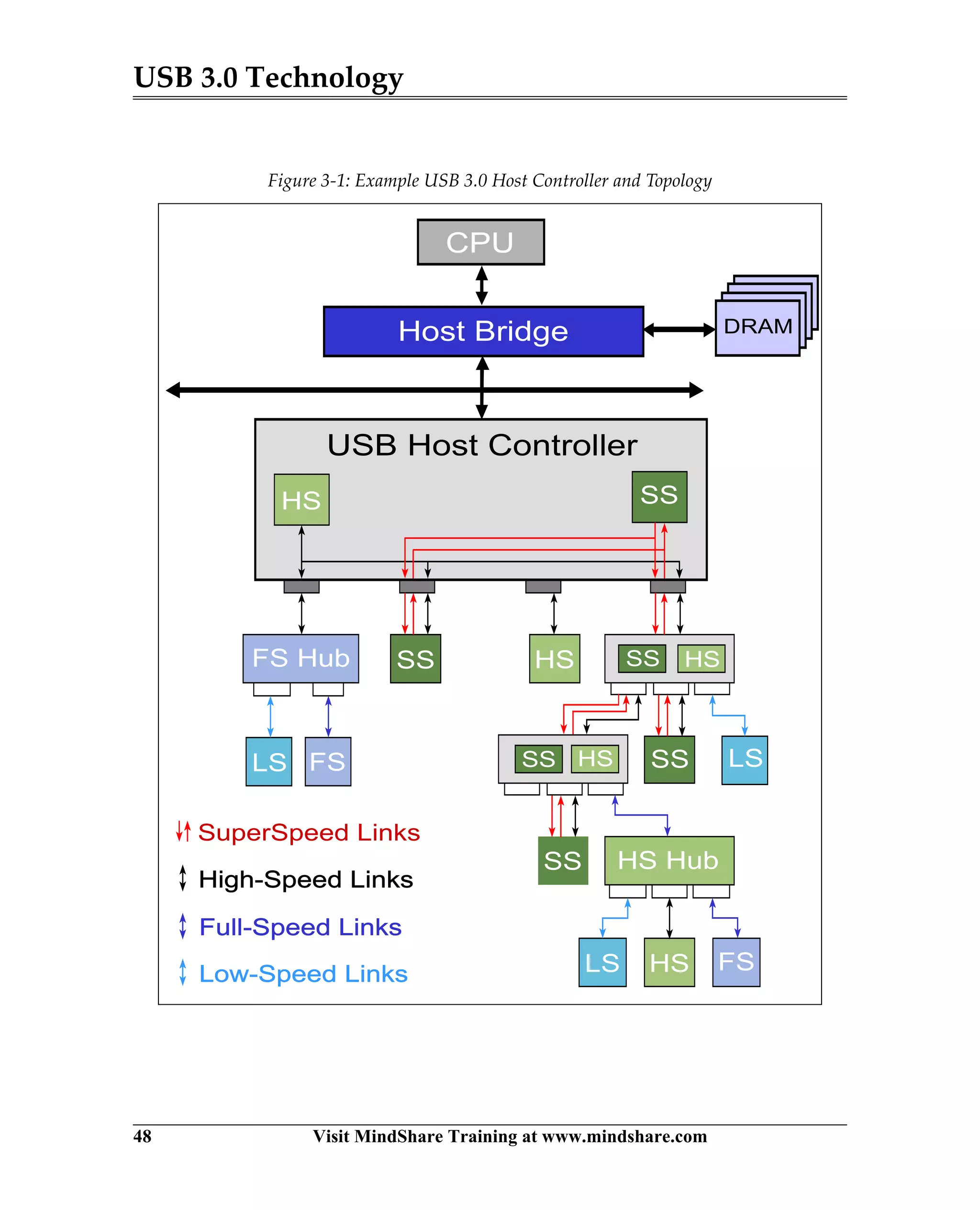
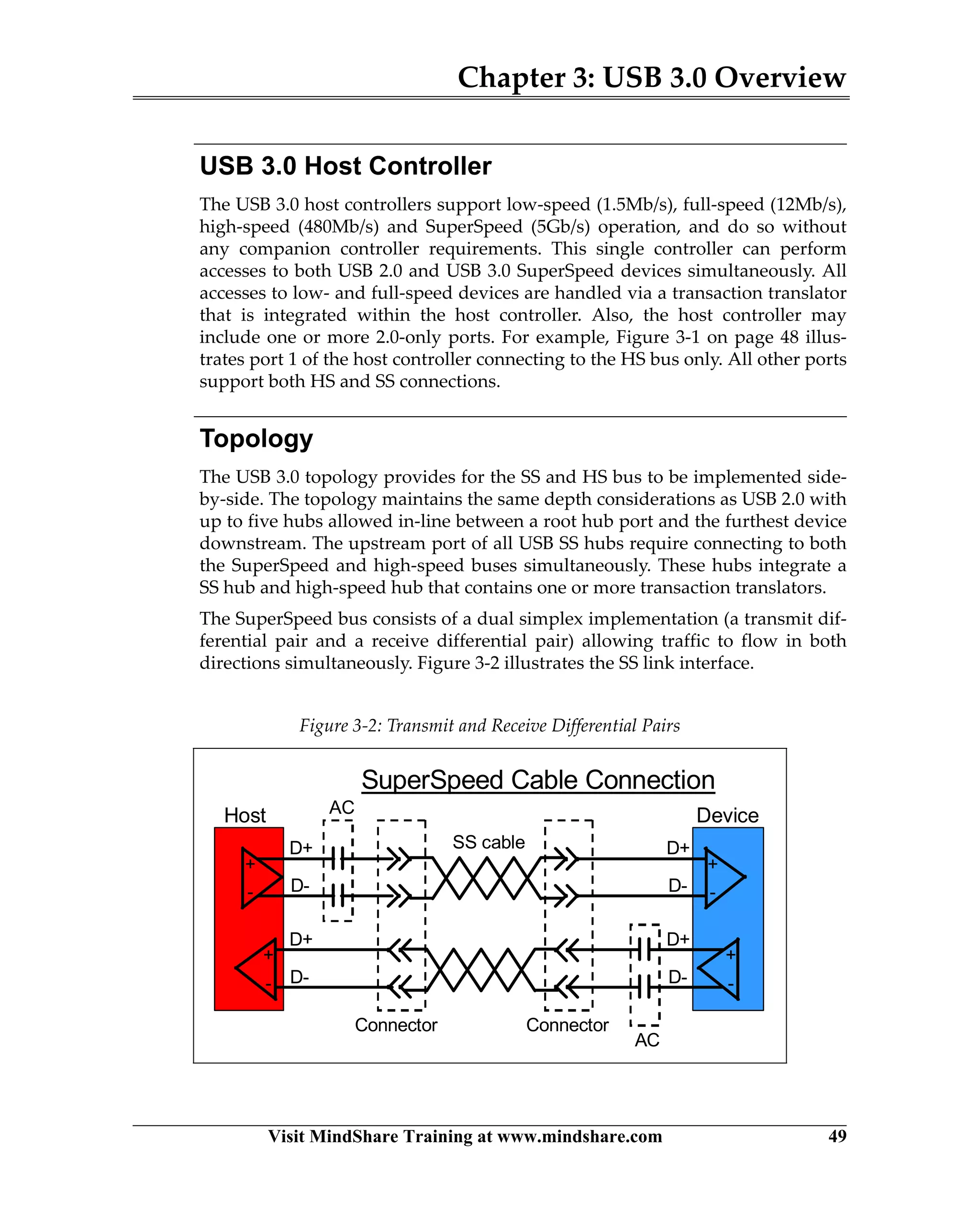
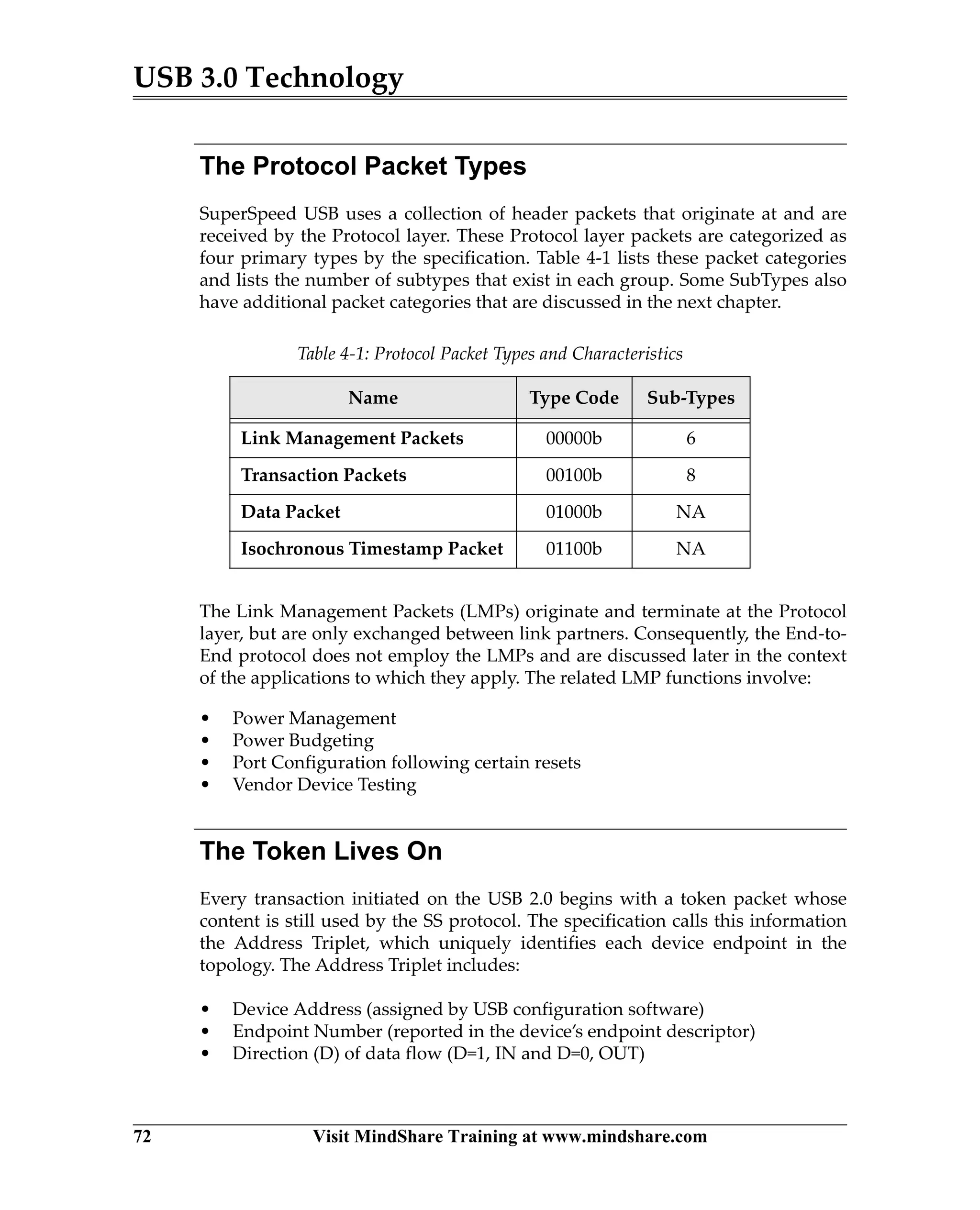
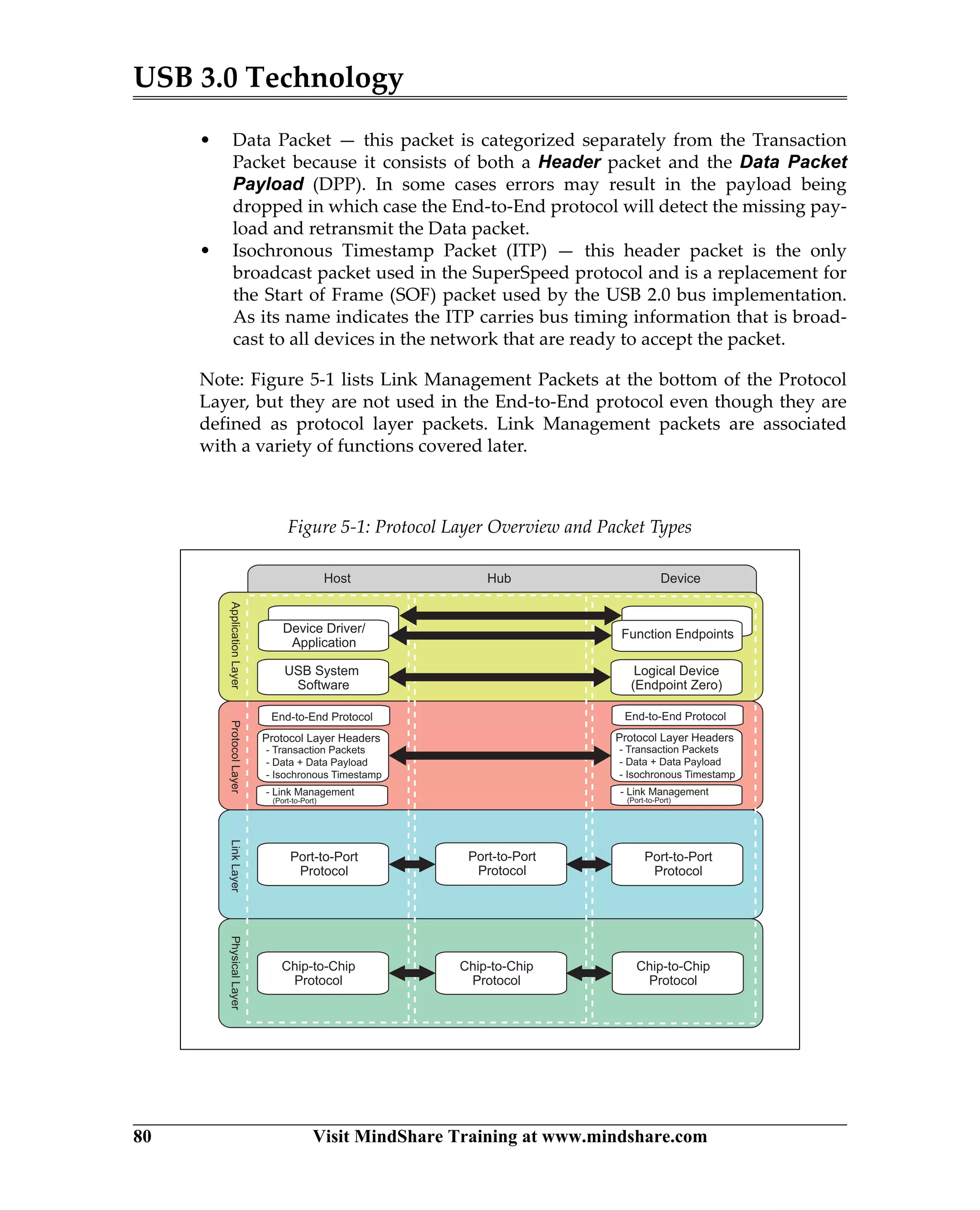
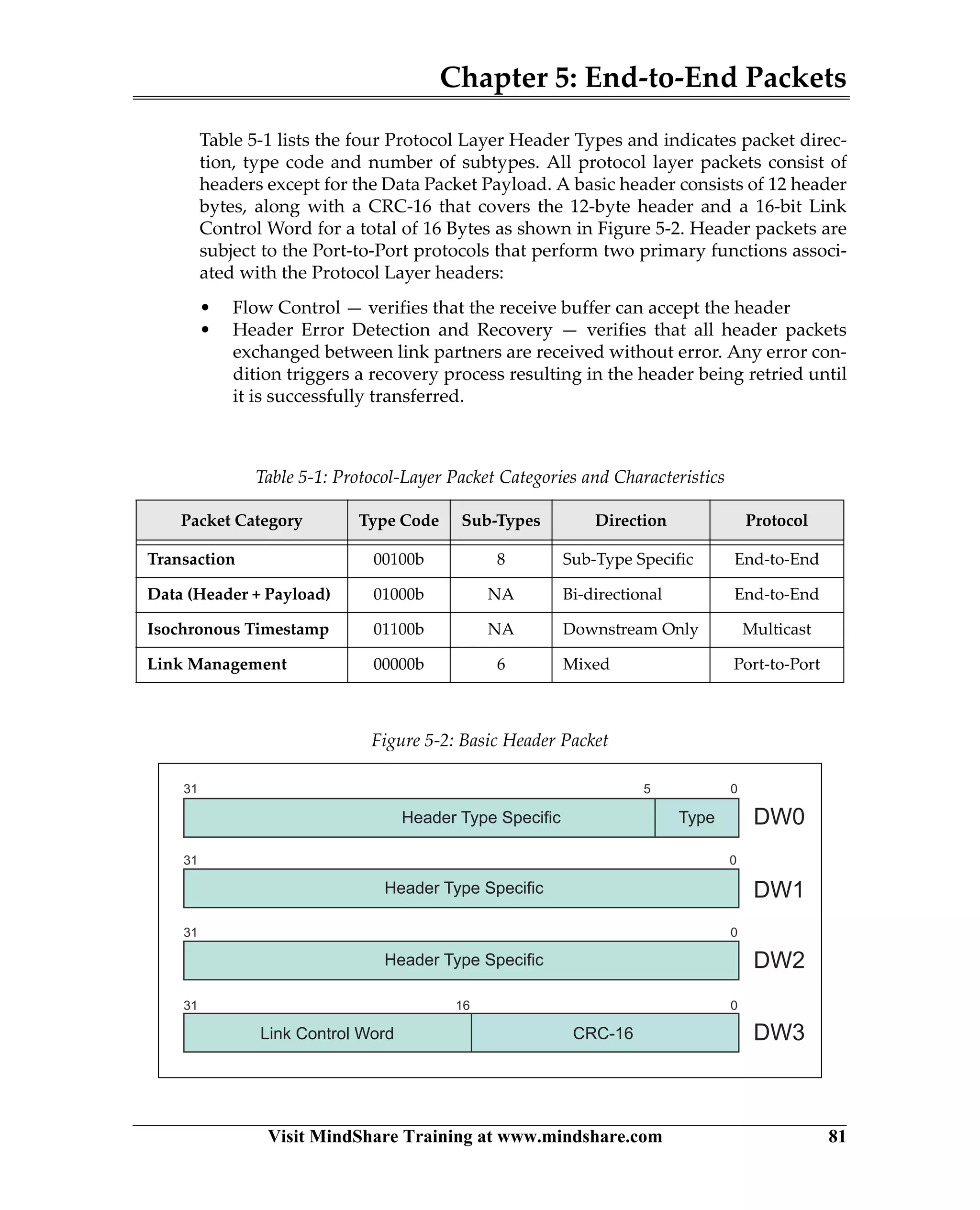
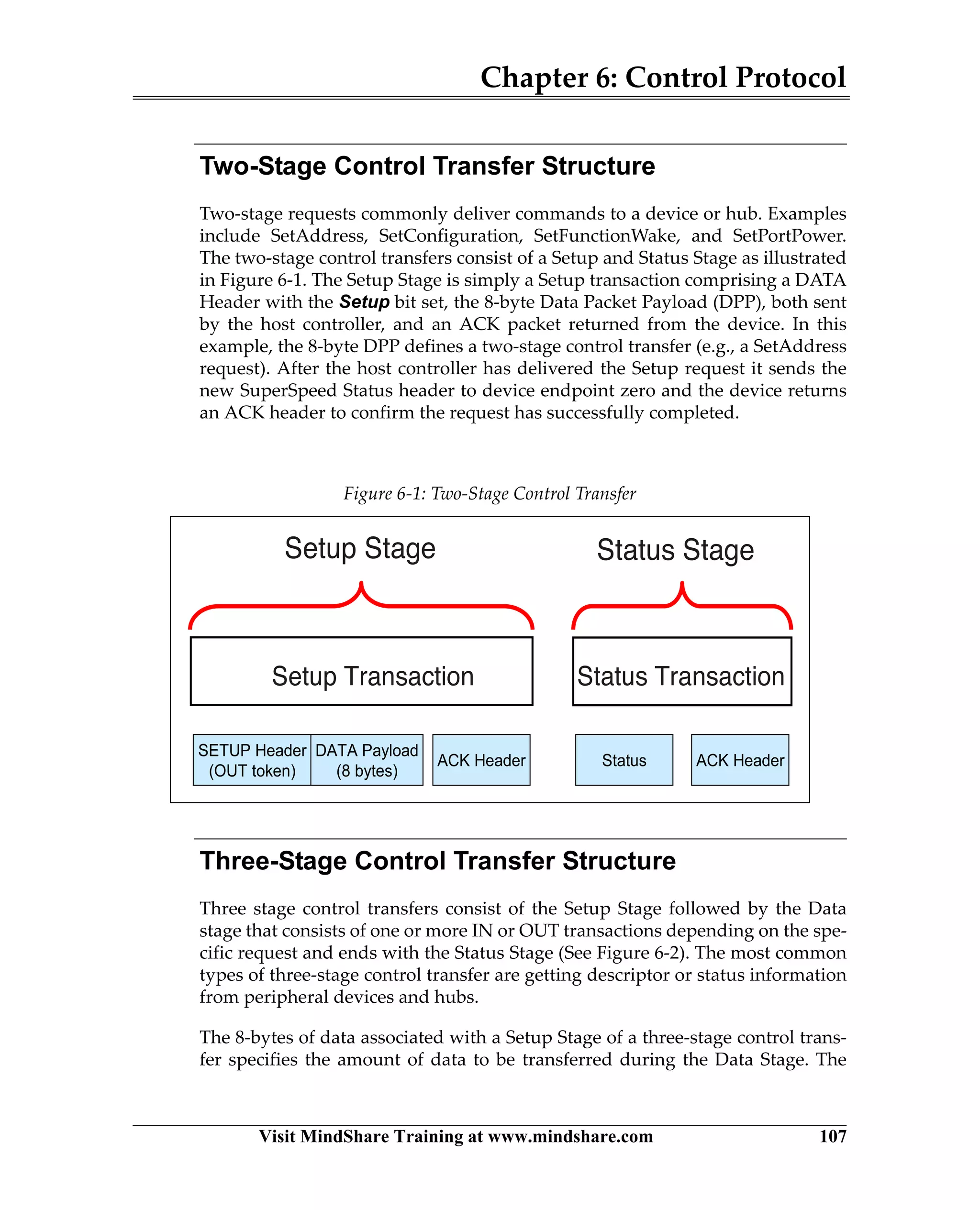
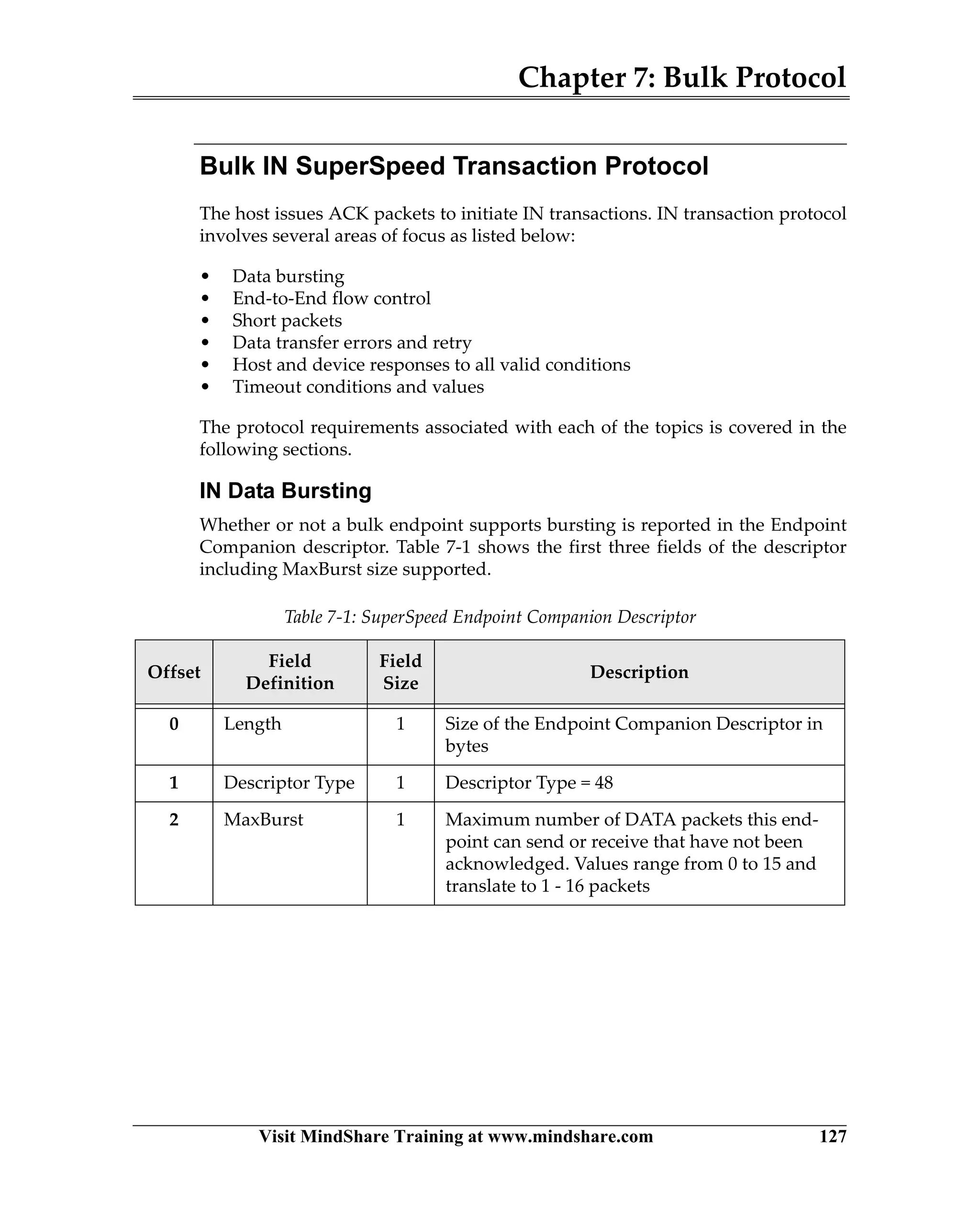
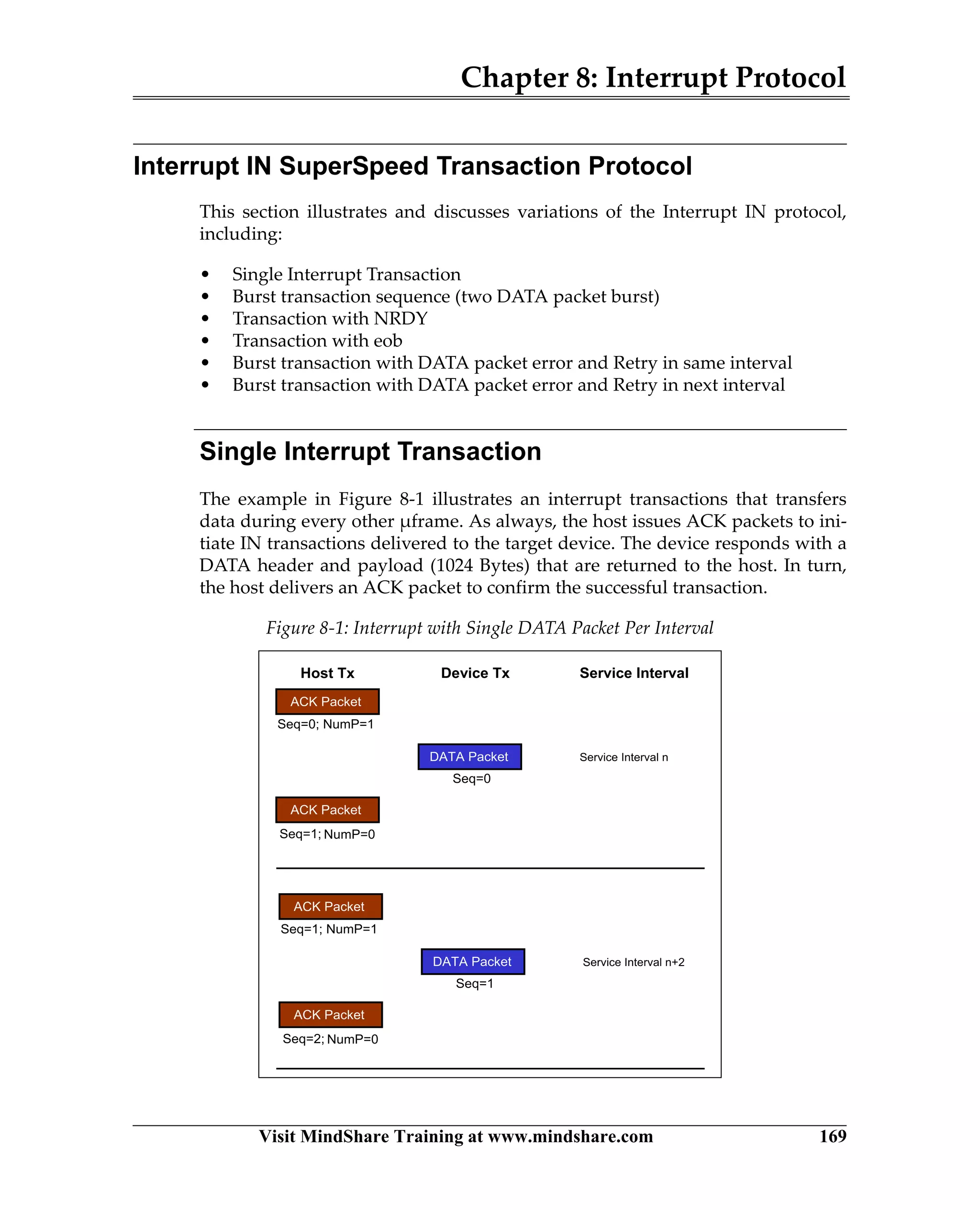
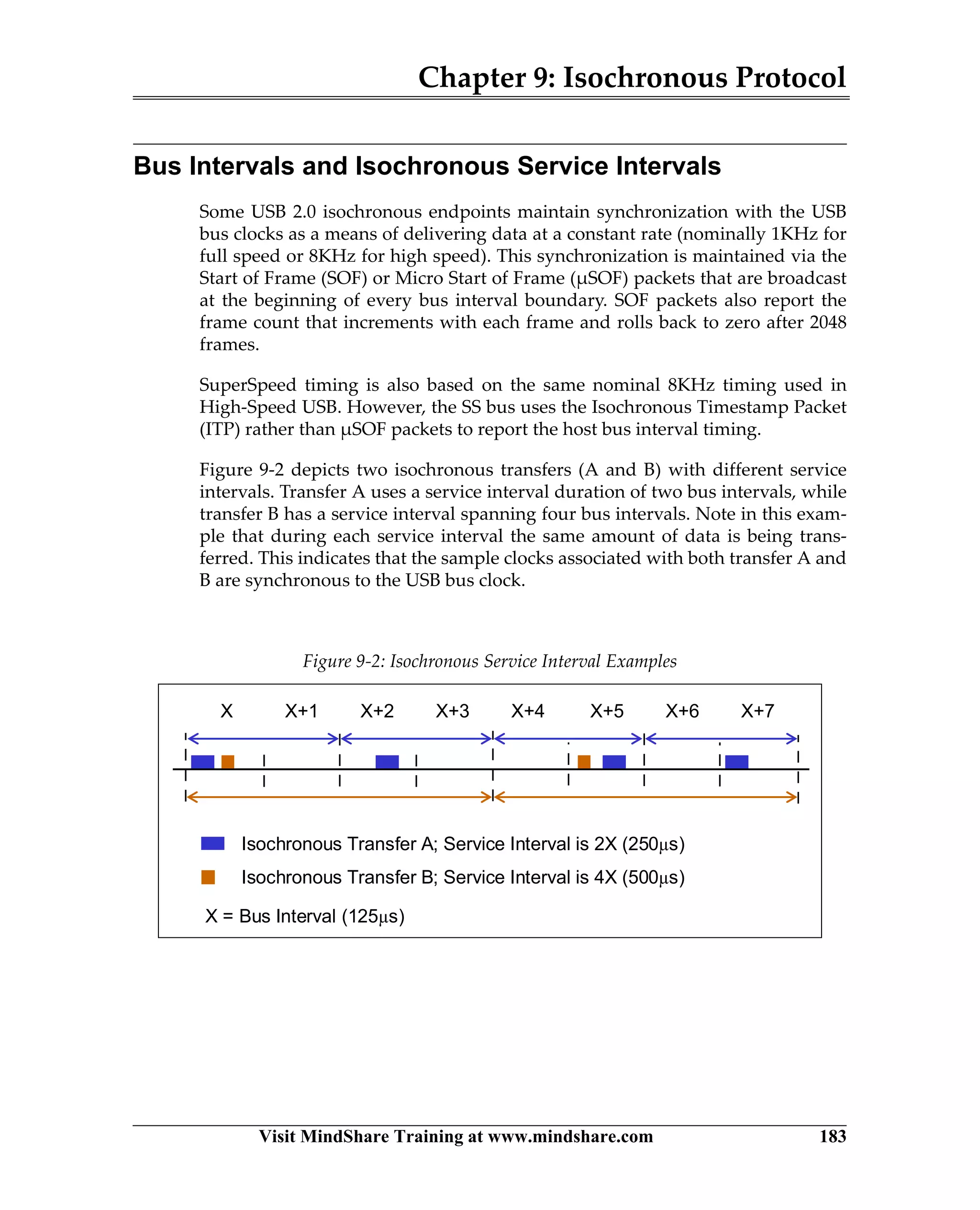
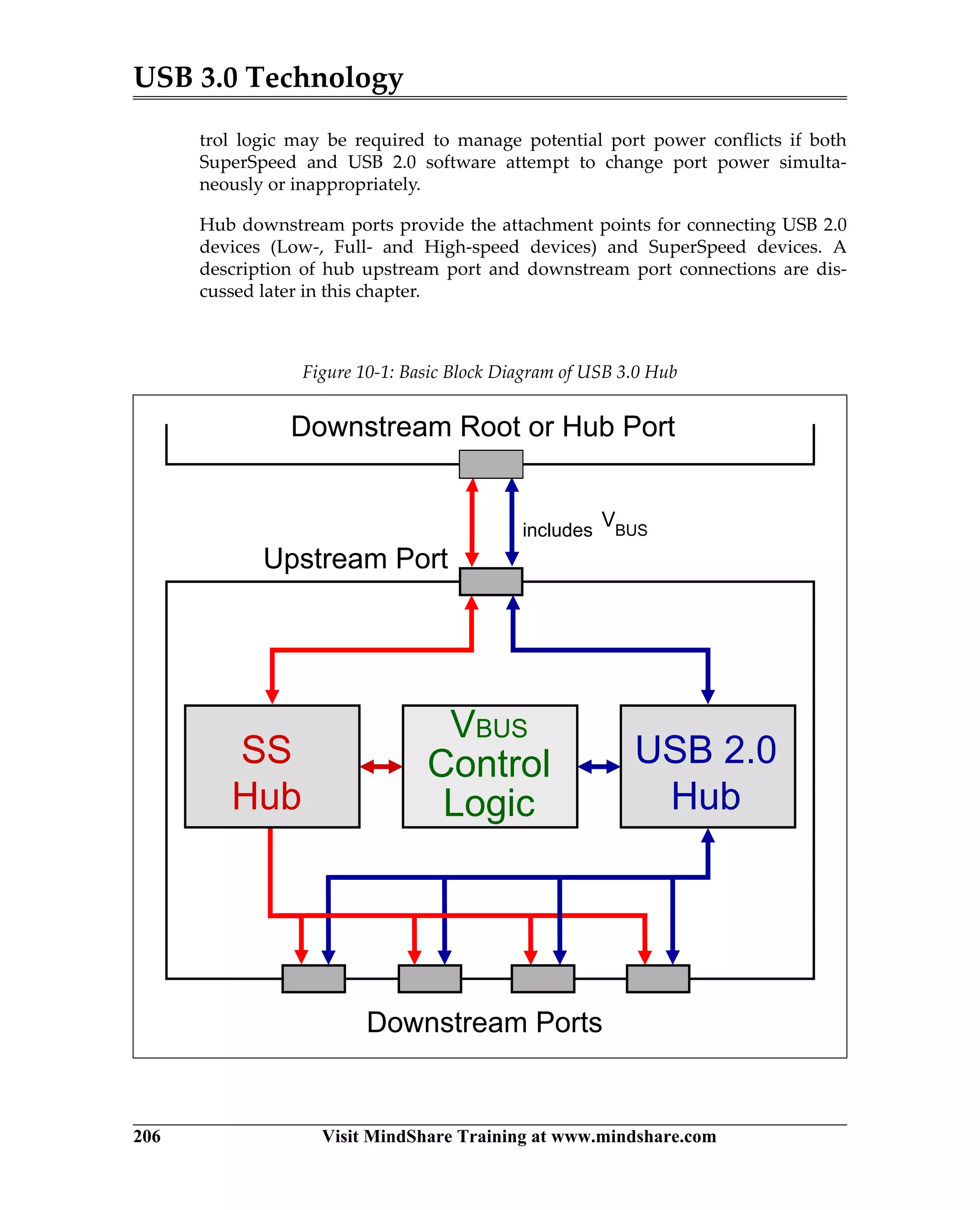
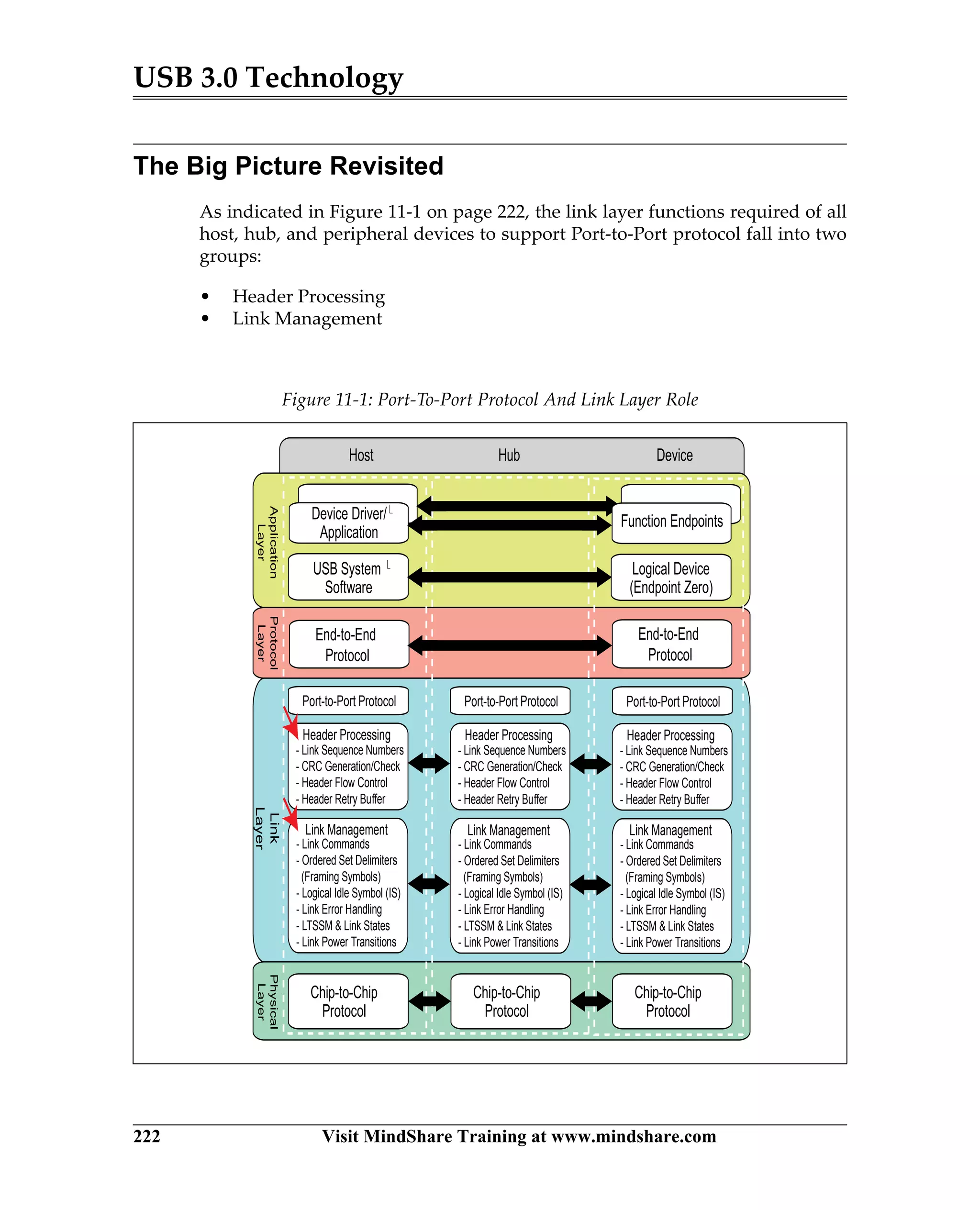
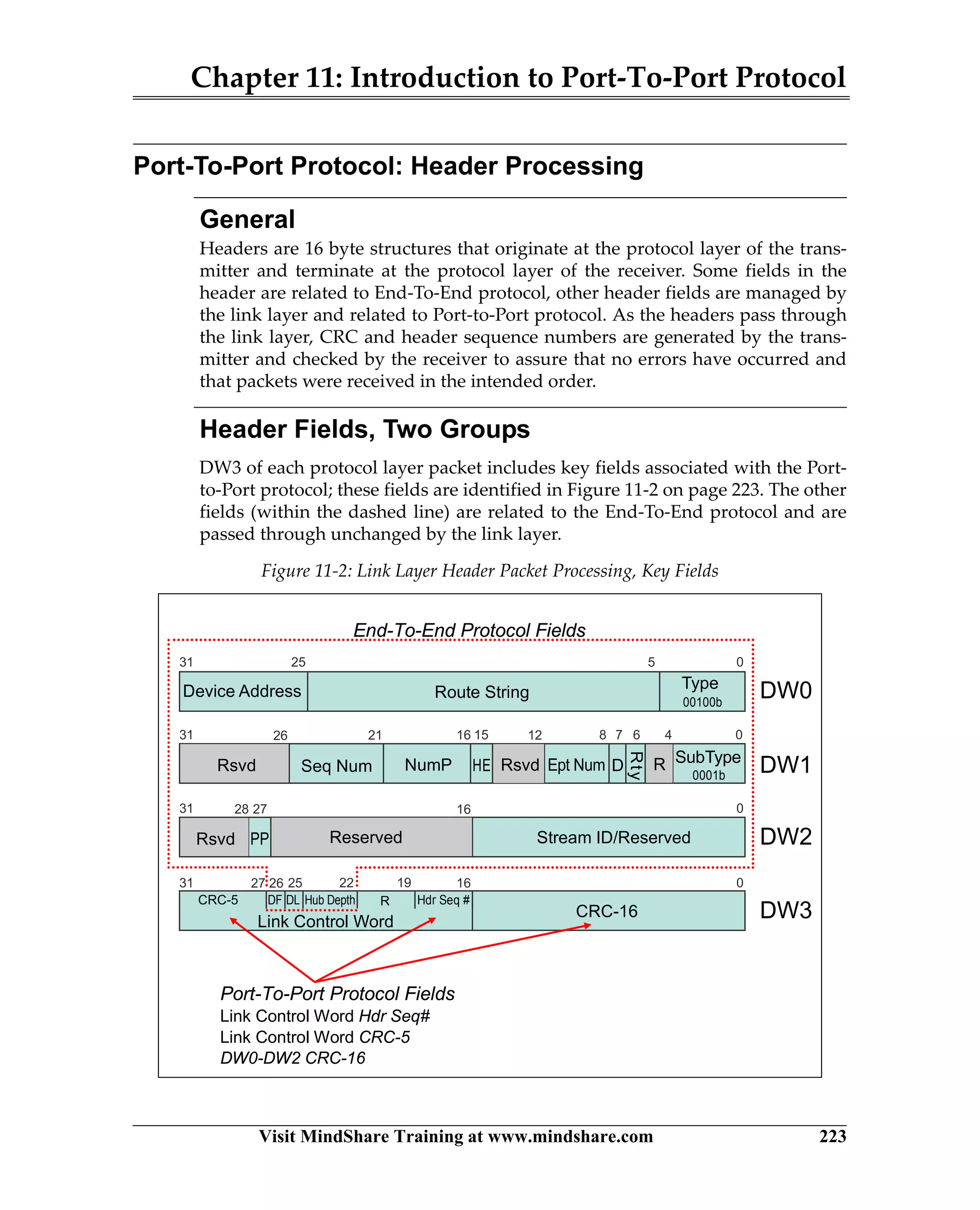
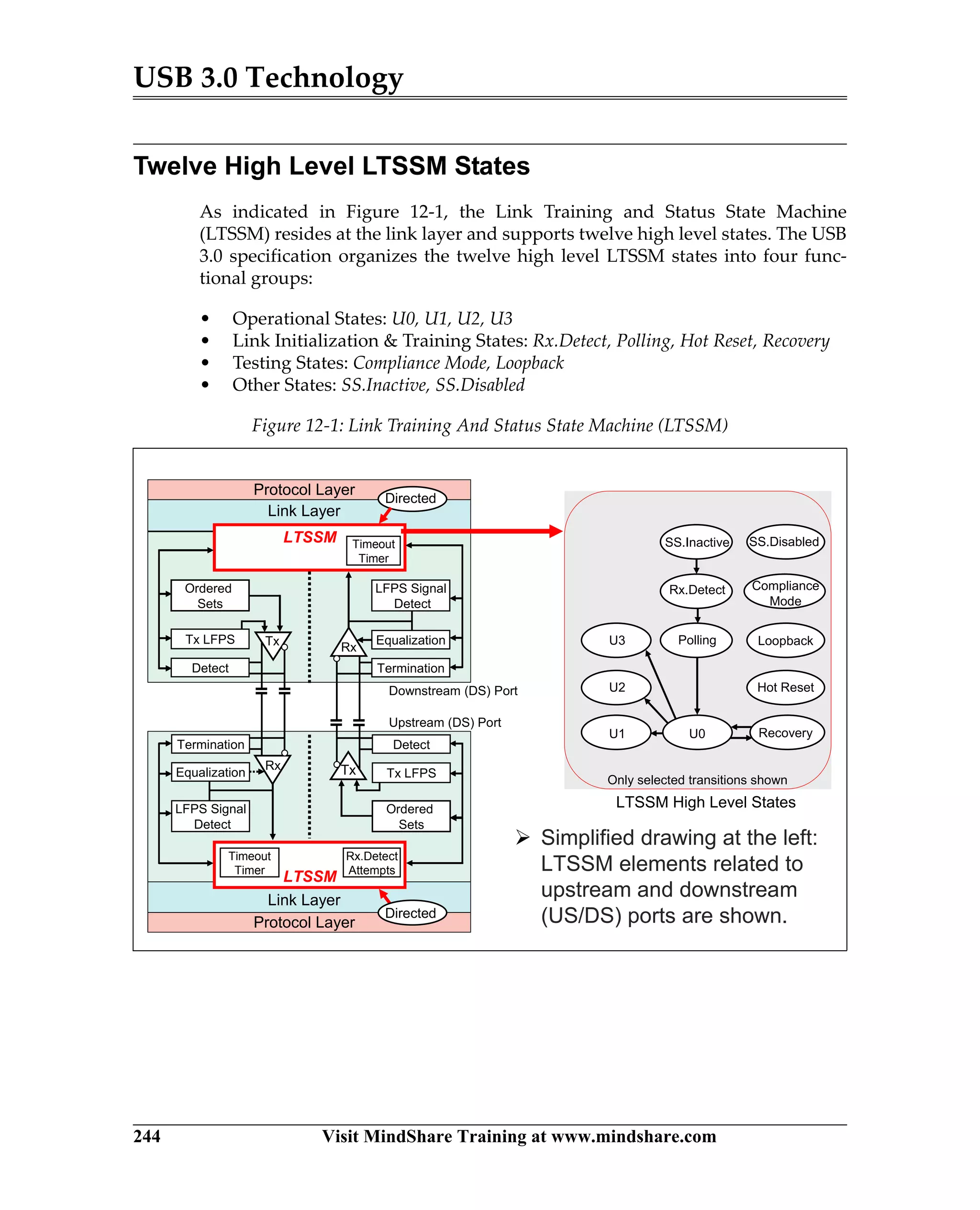
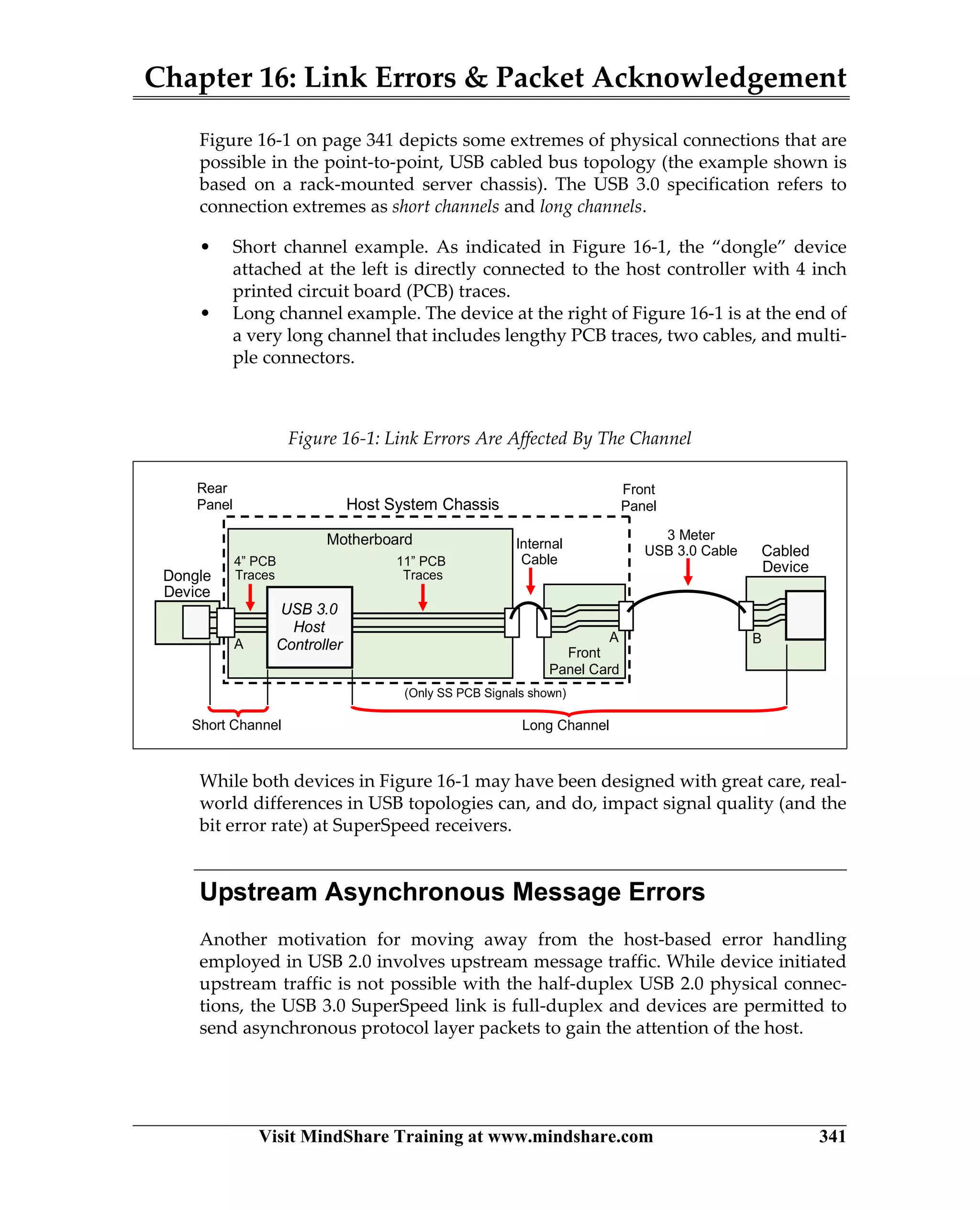
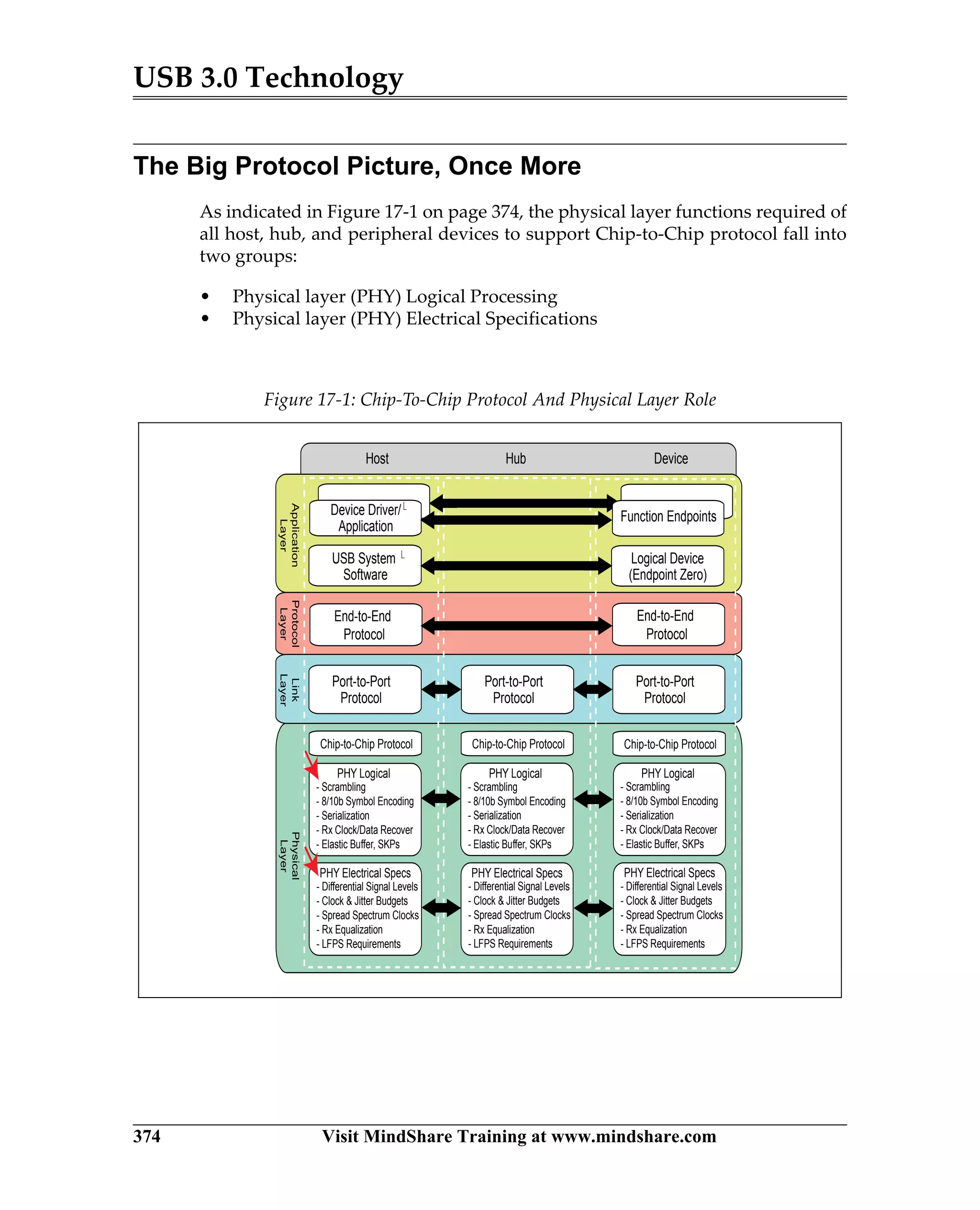
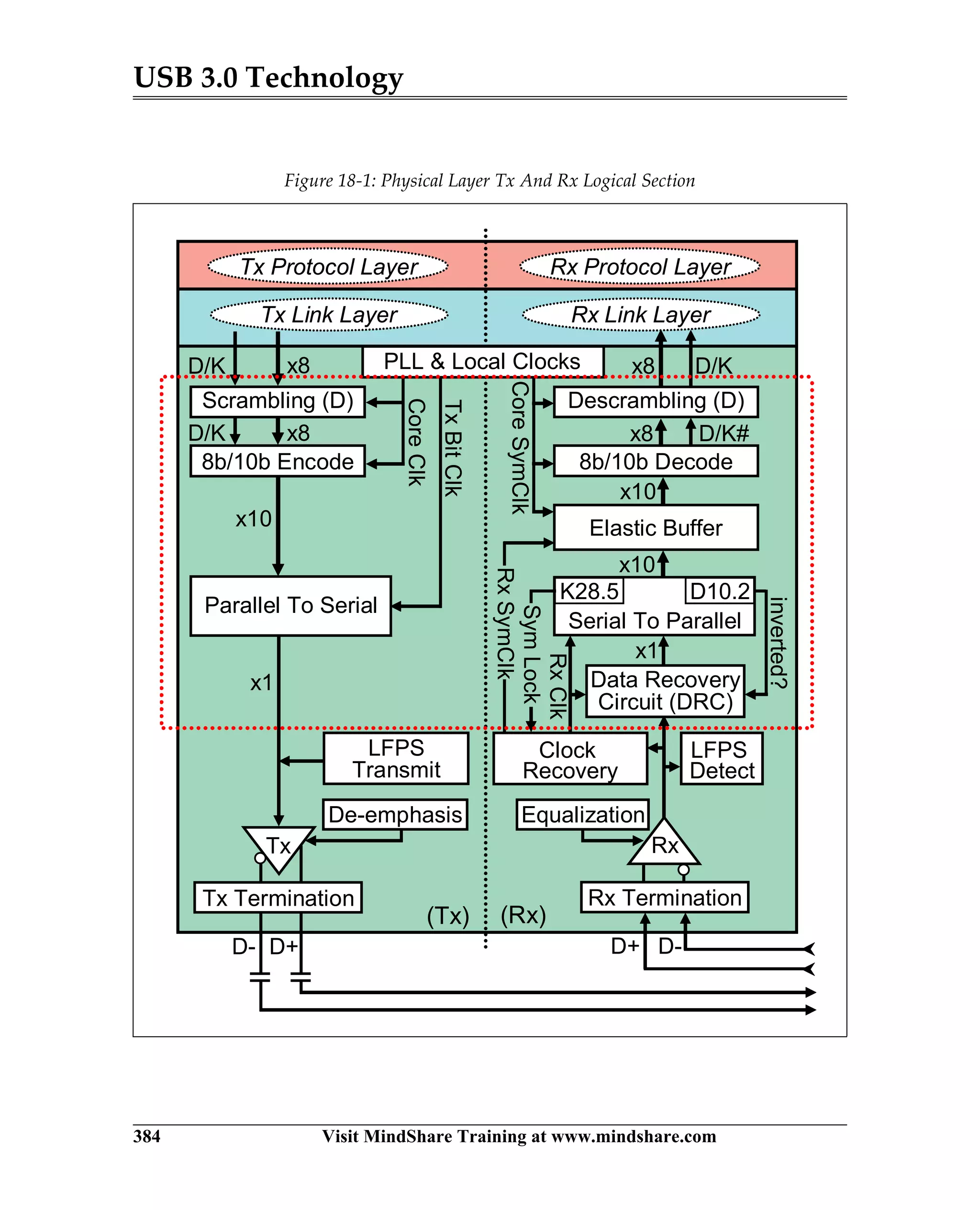
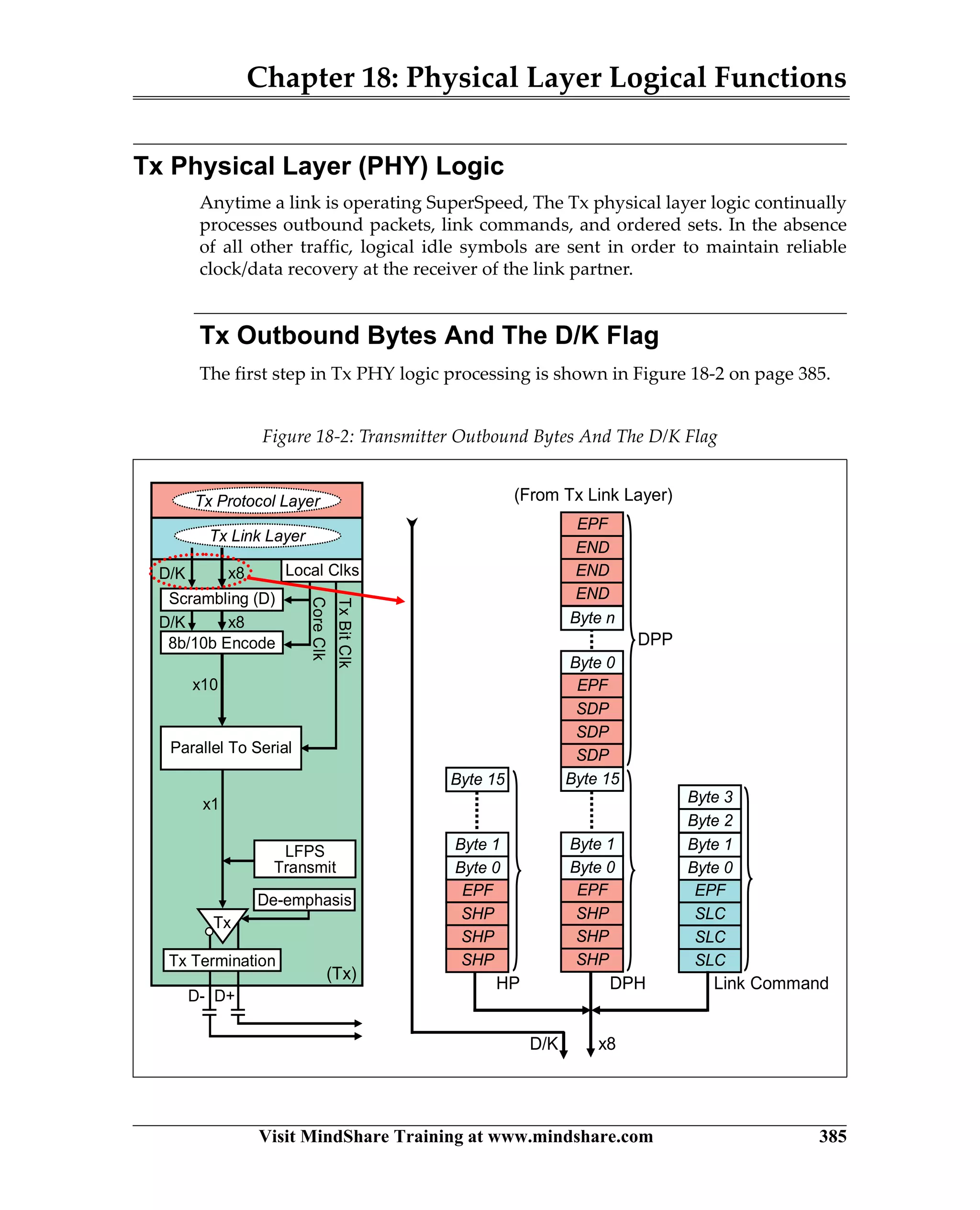
USB 3.0 introduces the SuperSpeed protocol which provides a significant increase in bandwidth over USB 2.0 through a new physical layer capable of 5Gbps speeds. Key features of SuperSpeed USB include bulk streaming which allows high-speed transfer of large files without host involvement, improved flow control mechanisms, and enhanced power management.






![Many of the designations used by manufacturers and sellers to distinguish their prod-
ucts are claimed as trademarks. Where those designators appear in this book, and Mind-
Share was aware of the trademark claim, the designations have been printed in initial
capital letters or all capital letters.
The authors and publisher have taken care in preparation of this book, but make no
expressed or implied warranty of any kind and assume no responsibility for errors or
omissions. No liability is assumed for incidental or consequential damages in connec-
tion with or arising out of the use of the information or programs contained herein.
Library of Congress Cataloging-in-Publication Data
Anderson, Don and Trodden, Jay
USB 3.0 Technology / MindShare, Inc. Donovan Anderson, Jay Trodden....[et al.]
Includes index
ISBN: 978-0-9836465-1-8
1. Computer Architecture 2. Microcomputers - buses.
I. Anderson, Don II. MindShare, Inc. III. Title
Library of Congress Number:
ISBN: 978-0-9836465-1-8
Copyright ©2013 by MindShare, Inc.
All rights reserved. No part of this publication may be reproduced, stored in a retrieval
system, or transmitted, in any form or by any means, electronic, mechanical, photocopy-
ing, recording, or otherwise, without the prior written permission of the publisher.
Printed in the United States of America.
Sponsoring Editor:
Project Manager: Maryanne Daves
Cover Design: Greenhouse Creative and MindShare, Inc.
Set in 10 point Palatino Linotype by MindShare, Inc.
First Edition, First Printing,](https://image.slidesharecdn.com/usb3-140317233000-phpapp02/75/Usb-3-0-technology-mindshare-7-2048.jpg)