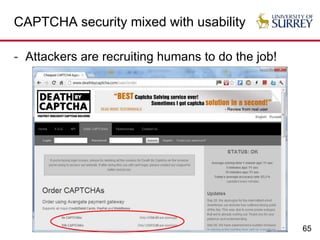
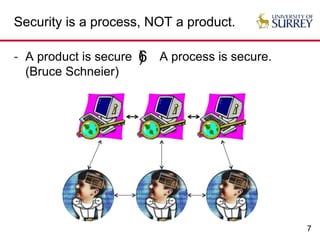
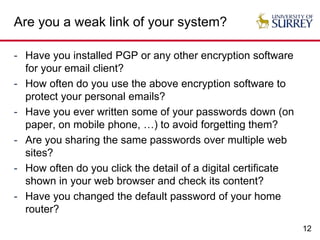
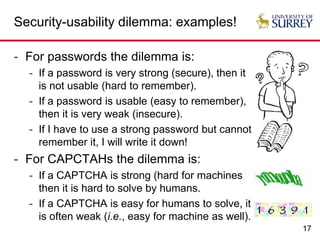
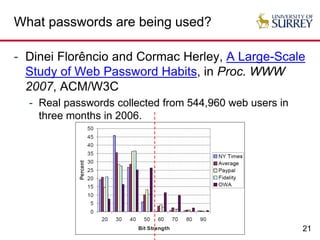
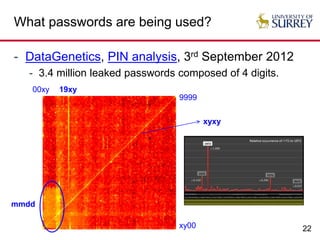
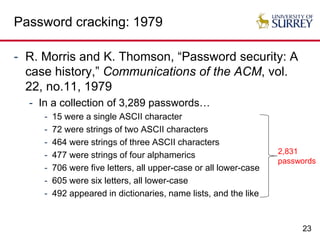
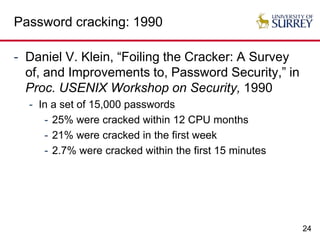
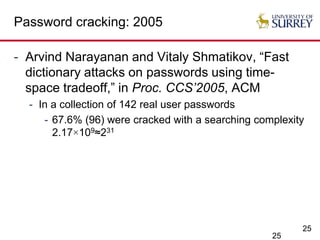
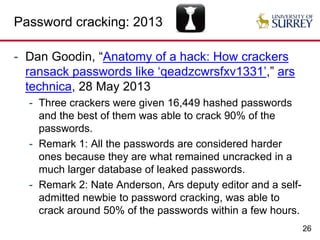
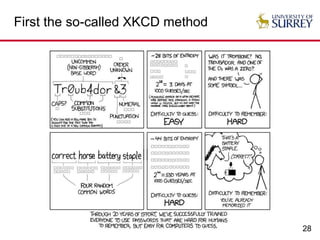
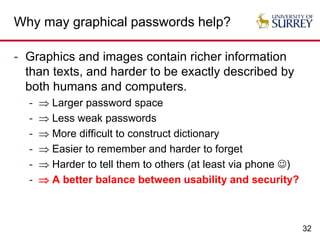
The document explores the relationship between security and usability, highlighting that humans are often the weakest link in security processes. It discusses examples such as passwords and CAPTCHAs to outline the usability-security dilemma, emphasizing the challenges in balancing secure yet user-friendly solutions. Possible solutions include graphical passwords and hardware-based security measures, although the search for effective replacements for traditional textual passwords remains ongoing.

































![63
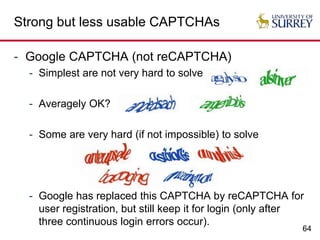
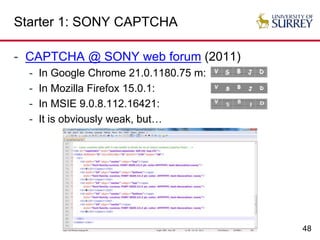
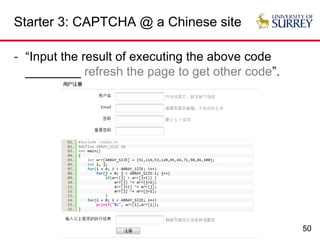
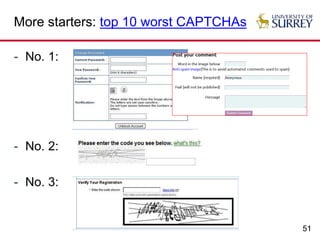
Insecure but usable CAPTCHAs
- Almost all (if not all) e-banking CAPTCHAs [S. Li
et al. ACSAC 2010]](https://image.slidesharecdn.com/usablesecurity-160326113855/85/Usable-Security-When-Security-Meets-Usability-63-320.jpg)