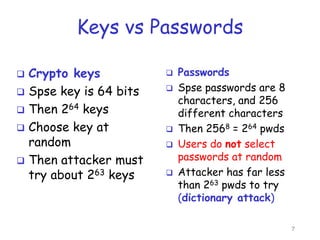
This document discusses access control and authentication. It covers two parts of access control - authentication and authorization. Authentication determines who is accessing the system, such as through passwords, biometrics, or something you have. Authorization determines what access and actions a user is allowed once authenticated. The document provides examples of access control lists and capabilities for managing authorization. It also discusses password issues and cracking tools. CAPTCHAs are introduced as a type of reverse Turing test to distinguish humans from computers to control access.