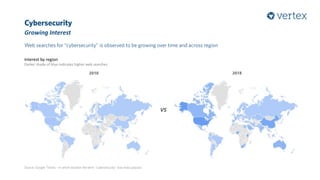
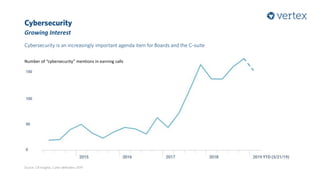
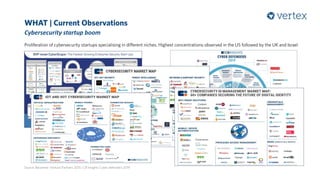
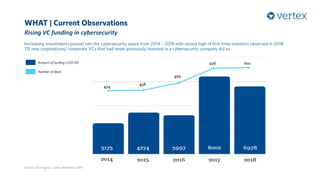
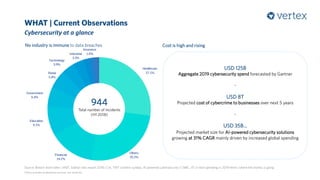
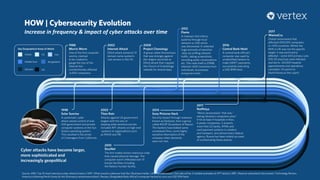
The document discusses the growing importance of cybersecurity, noting a significant increase in interest and investment in the field due to the escalating threat of cyber attacks. It highlights trends such as the convergence of cyber and physical security, the automation of attacks through AI, and the gradual shift from traditional security measures to cloud-based solutions. Additionally, the document presents a selection of cybersecurity startups and their unique solutions addressing various industry challenges.














![WHERE | Looking Ahead
Software to hardware
Source: Intel, Shifting from software to hardware for network security | PW World, Intel divests McAfee | Computer Weekly, Intel set up new group to focus on hardware security | Brookings Institute,
Ensuring hardware cybersecurity | Forbes, Meltdown Spectre vulnerabilities leave millions open to cyber attack | CSO online, spectre and meltdown explained | CS Hub, Cybersecurity demands deeper look
at hardware issues
Traditional model of software protecting software cannot keep up with
advancing security threats. In 2018, variants of vulnerabilities that affects nearly
every computer chip manufactured in the past 20 years was discovered:
It involves a malicious program gaining unauthorized access to data by
exploiting techniques to speed up computer chips.
For a less technical explanation…
Spectre: like a mind trick where you make someone else give you
money; this happens so quickly that they do not realize
Meltdown: like a pickpocket who grabs the money very quickly
In response, every major player in the industry – e.g. Intel, Microsoft, Google,
Apple – have released patches and critical updates. However, software can be
Hence, the way to mitigate these threats have gone beyond relying on patches
and software updates
replaced
updated
downloaded from the internet
altered
As a result, we observe increasing prioritization of hardware security and
hardware becoming the new frontline of the cybersecurity battle:
Evident by large chip makers foray into hardware security
Case Study:
[1] Product Assurance & Security Group: set up to focus on hardware security in
the wake of discoveries that its chips have design flaws
[2] Acquisition (2010) and divestment (2017) of McAfee: Initial intention to
embed McAfee’s technology at the chip level to add layers of security to
hardware and components
[3] Acquisition of Altera: offer hardware security plus the upgradability
advantages of software through Field Programmable Gate Array (FPGA) system
on a chip products which Altera makes
Replacing the entire industry with secure hardware solutions is not necessarily
the right answer considering cost and loss of agility in development. Hardware is
likely to work with software to provide better assurance](https://image.slidesharecdn.com/vertexperspectivescybersecurity-190515100303/85/Cybersecurity-Risk-Impact-Innovations-30-320.jpg)





