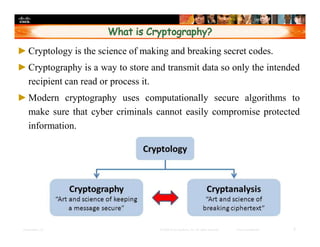
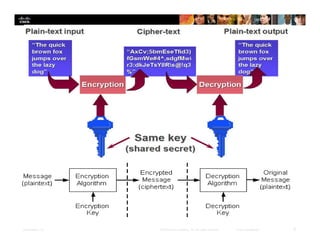
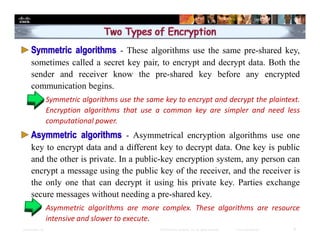
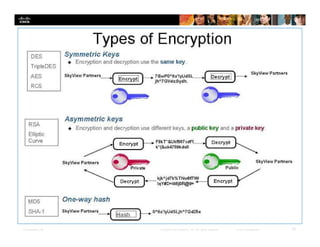
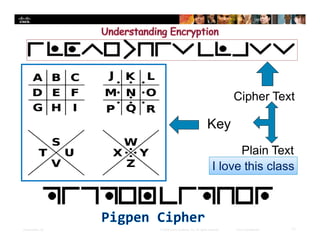
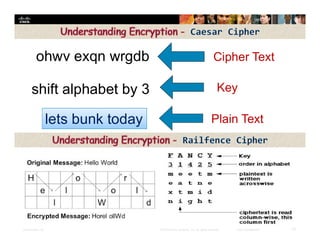
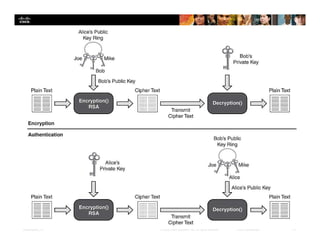
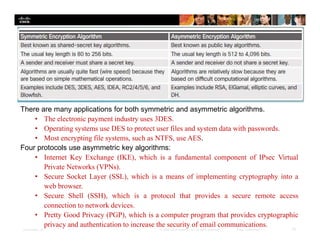
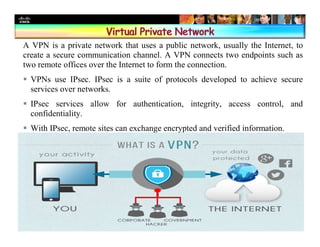
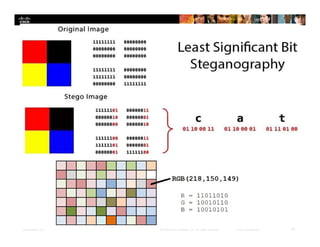
Chapter 4 of the document discusses various methods of protecting data confidentiality, including cryptography, access control, and data obscuring techniques. It covers encryption methods, both symmetric and asymmetric, and their applications in secure communications and data protection. The chapter also addresses access control mechanisms, including mandatory and discretionary controls, as well as data masking and steganography to secure sensitive information.