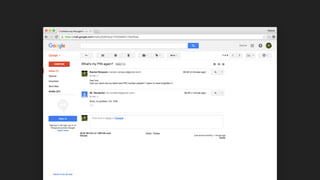
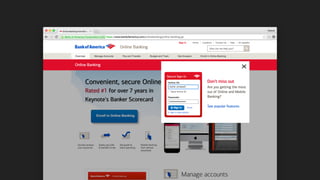
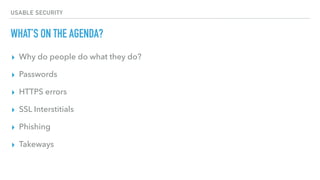
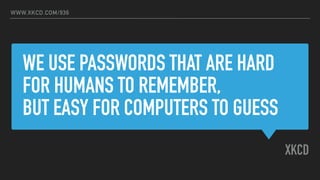
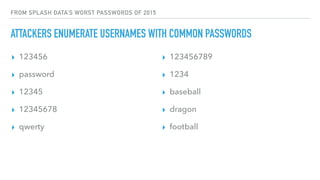
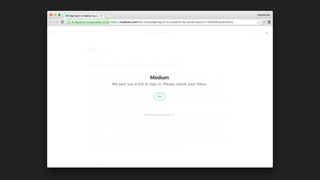
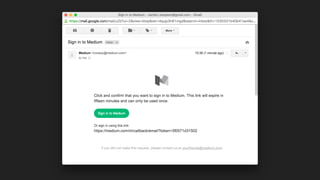
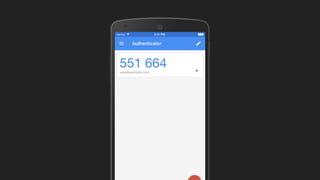
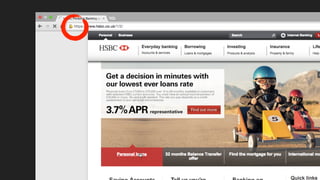
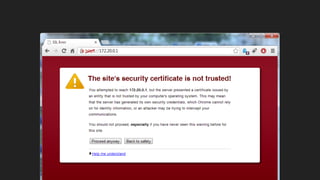
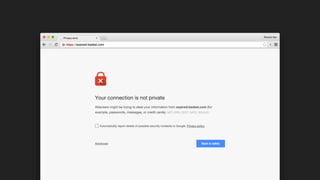
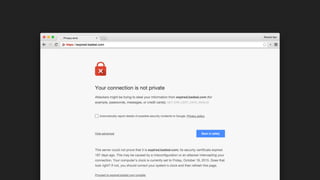
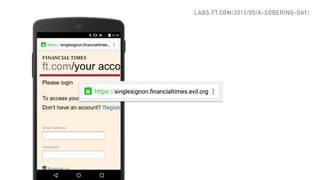
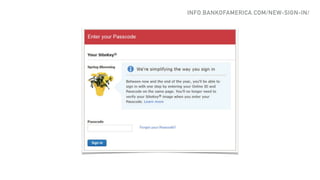
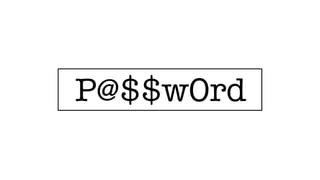The document discusses the challenges of usable security, emphasizing that human factors such as memory, attention, and cognitive load contribute to security vulnerabilities. It highlights issues with password management, phishing susceptibility, and the importance of user-friendly security measures. The authors propose strategies for improvement, including flexibility in security prompts and timely communication to better inform users.