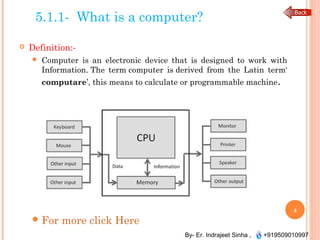
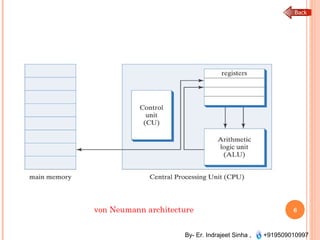
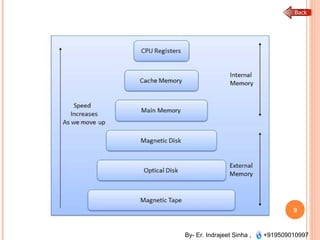
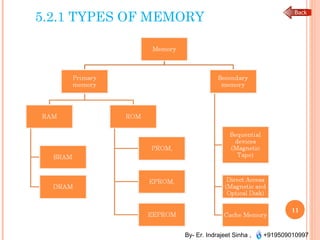
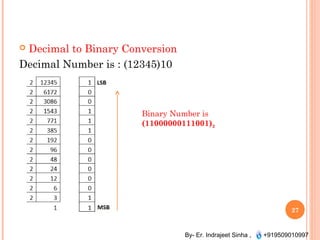
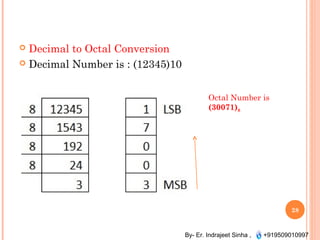
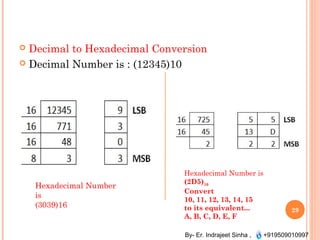
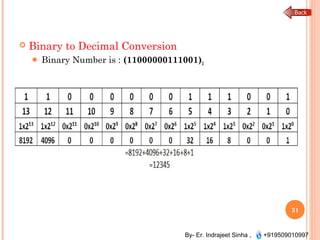
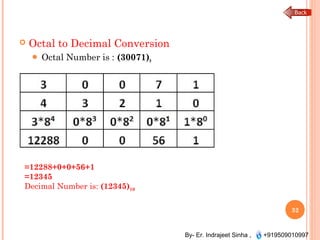
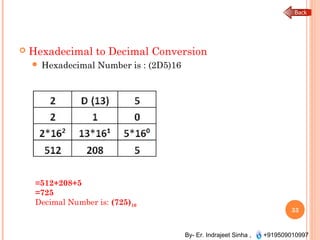
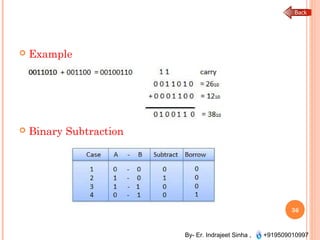
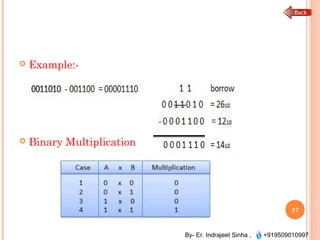
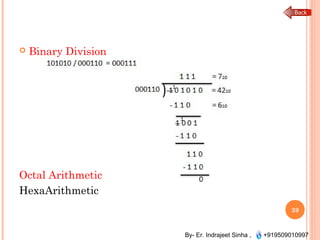
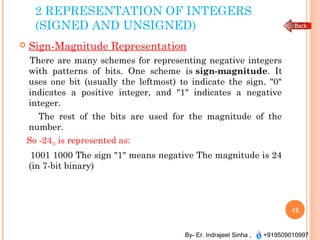
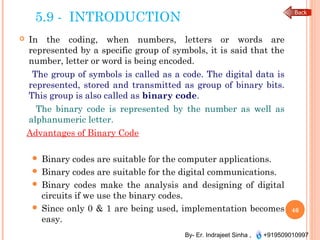
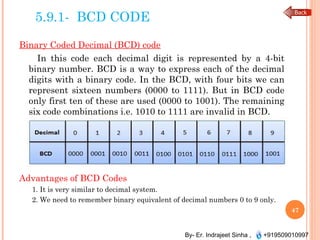
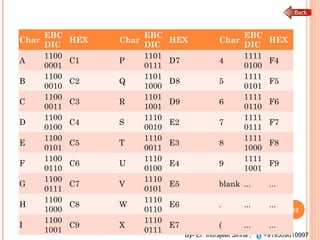
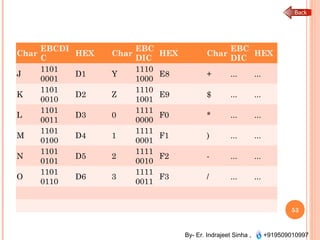
The document outlines the fundamentals of computer architecture and programming, emphasizing the stored program concept conceptualized by John von Neumann, which describes how computers store both data and instructions in memory. It details various types of memory, such as RAM (including SRAM and DRAM), ROM types, and cache memory, with explanations of how these components function within systems. Additionally, it covers number systems, conversions between them, and binary arithmetic, presenting key definitions and examples relevant to number representations in computing.