Computer memory can be divided into primary/main memory and secondary memory. Primary memory is directly accessible by the CPU and can be volatile, losing data on power loss. It includes RAM (random access memory) such as SRAM and DRAM. Secondary memory includes non-volatile storage like hard disks, CDs, DVDs that are accessed via I/O. The document discusses different types of primary memory like cache, RAM, ROM and their characteristics. It also covers memory management techniques like paging, segmentation and virtual memory that allow accessing more memory than physically installed.

![memory out of which one is primary and the other is secondarymemory. Basically a
computer memory can store particularly two things. They are the data and the set of
instructions to execute a program.
Now let us take a brief look towards the types of primary storage (or) primary memory.
This primary memory can be directly accessed by the processing unit. The contents in
the primary memory are temporary. While performing a task if there is any power cut
problems then we may lose the data which is in primary memory. One benefit is that we
can store and retrieve the data with a considerable speed. Primary memory is more
expensive when compared to secondary memory.
RAM (Random Access Memory) could be the best example of primary memory. The
primary memory in the computer system is in the form of Integrated Circuits. These
circuits are nothing but RAM. Each of RAM’s locations can store one byte [1 Byte = 8
bits] of information. This can be in either of the forms 1 or 0. The primary storage
section is made up of several small storage locations in the integrated circuits called
cells. Every single cell can store fixed number of bits called word length. Each cell
contains a unique number assigned to it and it has the unique address; these addresses
are used to identify the cells. The address starts at level 0 and goes up to (N-1).
Typesof primary ORMain memory:
RAM [RANDOM ACCESS MEMORY]
RAM is the best example of primary storage. We have very good reason to justify because in this
kind of memory we can select randomly, use that at any location of the memory, then store and
finally retrieve processed data which is information. RAM is a volatile memory because it loses
its contents when there is a power failure in the computer system. The memories which lose their
contents on power failure are called volatile memories.](https://image.slidesharecdn.com/memorymanagment-161107163116/85/Memory-managment-2-320.jpg)
![Static RAM (SRAM)
The word static indicates that the memory retains its contents as long as
power is being supplied. However, data is lost when the power gets down
due to volatile nature. SRAM chips use a matrix of 6-transistors and no
capacitors. Transistors do not require power to prevent leakage, so SRAM
need not have to be refreshed on a regular basis.
Because of the extra space in the matrix, SRAM uses more chips than DRAM
for the same amount of storage space, thus making the manufacturing
costs higher. So SRAM is used as cache memory and has very fast access.
Dynamic RAM (DRAM)
DRAM, unlike SRAM, must be continually refreshed in order to maintain
the data. This is done by placing the memory on a refresh circuit that
rewrites the data several hundred times per second. DRAM is used for most
system memory because it is cheap and small. All DRAMs are made up of
memory cells which are composed of one capacitor and one transistor.
ROM [READ ONLY MEMORY]:
ROM is also formed by Integrated Circuits. The data which is stored in ROM is permanent. The
ROM can only read the data by CPU but can’t be edited or manipulated.ROM is a non-volatile
memory because it will not lose its contents when there is a power failure in the computer
system. The basic I/O program is stored in the ROM and it examines and initializes various](https://image.slidesharecdn.com/memorymanagment-161107163116/85/Memory-managment-3-320.jpg)
![devices attached to the computer when the power is ON. The contents in the ROM can neither be
changed nor deleted.
PROM [PROGRAMMABLE READ ONLY MEMORY]:
As we know that we cannot edit (or) modify data in the ROM. To overcome this problem to
some extent PROM is very helpful that is in PROM we can store our programs in PROM chip.
Once the programs are written it cannot be changed and remain intact even if the power is
switched off. Therefore programs written in PROM cannot be erased or edited.
MROM (Masked ROM)
The very first ROMs were hard-wired devices that contained a pre-
programmed set of data or instructions. These kind of ROMs are known as
masked ROMs which are inexpensive.
EPROM [ERASABLE PROGRAMMABLE READ ONLY MEMORY]:
EPROM will overcome the problem of PROM. EPROM chip can be programmed time and again
by erasing the information stored earlier in it. EPROM chip has to be exposed to sunlight for
some time so that ultra violet rays fall on the chip and that erases the data on the chip and the
chip can be re-programmed using a special programming facility. There is another type memory](https://image.slidesharecdn.com/memorymanagment-161107163116/85/Memory-managment-4-320.jpg)
![called EEPROM that stands for Electrically Erasable Programmable Read Only Memory in
which we can erase the data and re-program it with a fresh content.
REGISTERS:
Actually computer system uses a number of memory units called registers. Registers store data
or information temporarily and pass it on as directed by the control unit.
FLASH MEMORY:
It is a non-volatile computer memory that can be electrically erased and reprogrammed.
Examples are memory cards, chips, pen drives, and USBflash drives etc. flash memory costs
very less than byte-programmable EEPROM. It is very portable in nature.
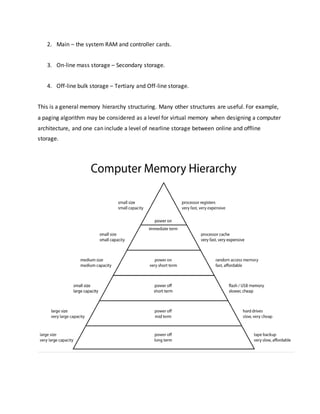
Memory hierarchy:
In computer architecture the memory hierarchy is a concept used to discuss performance
issues in computer architectural design, algorithm predictions, and lower
level programming constructs involving locality of reference. The memory hierarchy
in computer storage separates each of its levels based on response time. Since response time,
complexity, and capacity are related,[1] the levels may also be distinguished by their
performance and controlling technologies.
Designing for high performance requires considering the restrictions of the memory hierarchy,
i.e. the size and capabilities of each component. Each of the various components can be viewed
as part of a hierarchy of memories (m1,m2,...,mn) in which each member mi is typically smaller
and faster than the next highest member mi+1 of the hierarchy. To limit waiting by higher levels,
a lower level will respond by filling a buffer and then signaling to activate the transfer.
There are four major storage levels.
1. Internal – Processor registers and cache.](https://image.slidesharecdn.com/memorymanagment-161107163116/85/Memory-managment-5-320.jpg)