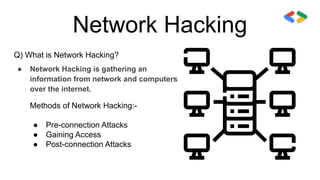
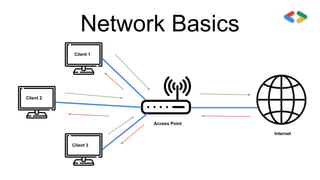
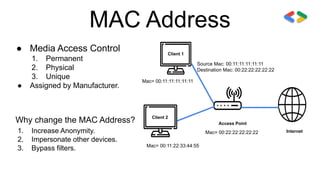
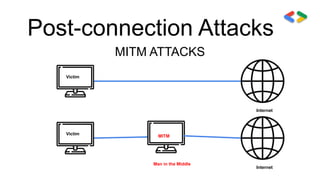
This session covered cyber security and ethical hacking topics such as network hacking, Kali Linux, IPV4 vs IPV6, MAC addresses, wireless hacking techniques like deauthentication attacks, cracking WEP and WPA encryption, and post-connection attacks including ARP spoofing and MITM attacks. The presenter emphasized the importance of securing networks by using strong passwords, disabling WPS, and enabling HTTPS to prevent hacking attempts.






![Network Hacking- Pre-connection
Attacks
Packet Sniffing Using Airodump-ng
1. Part of the aircrack-ng suit.
2. Airodump-ng is a packet sniffer.
3. Used to capture all packets within range.
4. Display detailed info about networks around us.
5. Connected clients...etc
Use:
airodump-ng[MonitorModeInterface]](https://image.slidesharecdn.com/fundamentalsofnetworkhacking-201215171704/85/Fundamentals-of-network-hacking-11-320.jpg)

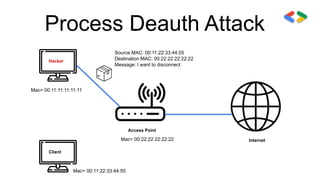
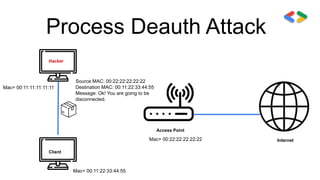
![Deauthentication Attack
→ Disconnect any client from any network.
● Works on encrypted networks(WEP,WPA,WPA2).
● No need to know the network key.
● No need to connect to the network.
Use:
Aireplay-ng --deauth [#DeauthPackets] -a [NetworkMac] -c [TargetMac] [Interface]](https://image.slidesharecdn.com/fundamentalsofnetworkhacking-201215171704/85/Fundamentals-of-network-hacking-13-320.jpg)
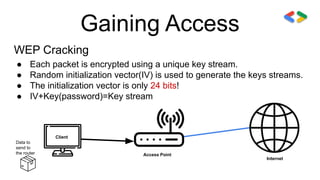




![Creating A Wordlist
Crunch can be used to create a wordlist.
Syntax:
> crunch [min] [max] [characters] -t[pattern] -o[FileName]
Example:
> crunch 6 8 123abc$ -o wordlist -t a@@@@b
Some Wordlists:
1. http://wordlist.sourceforge.net/
2. http://www.openwall.com/mirrors/
3. https://github.com/danielmiessler/SecLists
Now, You have WPA handshake & Wordlist… Now you can hack WPA/WPA2](https://image.slidesharecdn.com/fundamentalsofnetworkhacking-201215171704/85/Fundamentals-of-network-hacking-23-320.jpg)
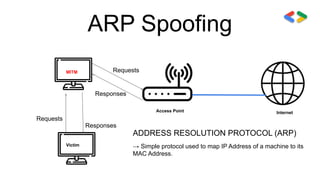
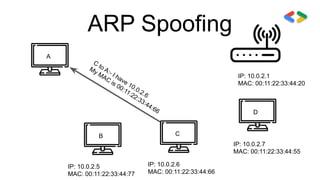
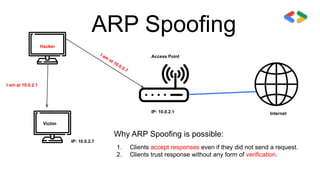
![ARP Spoofing
USING ARPSPOOF
● Arpspoof tool to run arp spoofing attacks.
● Simple and reliable.
● Ported to most operating systems including Android and iOS.
● Usage is always the same.
USE:
airspoof -i [interface] -t [clientIP] [gatewayIP]
airspoof -i [interface] -t [gatewayIP] [clientIP]](https://image.slidesharecdn.com/fundamentalsofnetworkhacking-201215171704/85/Fundamentals-of-network-hacking-31-320.jpg)
![ARP Spoofing
USING BETTERCAP
● Framework to run network attacks.
● Can be used to:
○ ARP Spoof targets (redirect the flow of packets).
○ Sniff data (urls, username, passwords).
○ Bypass HTTPs.
○ Redirect domain requests (DNS Spoofing).
○ Inject code in loaded pages.
○ And more!
USE:
Bettercap -iface [interface]](https://image.slidesharecdn.com/fundamentalsofnetworkhacking-201215171704/85/Fundamentals-of-network-hacking-32-320.jpg)





