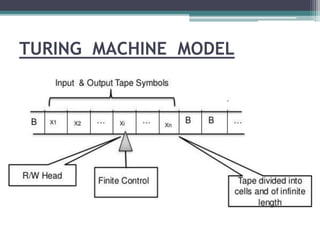
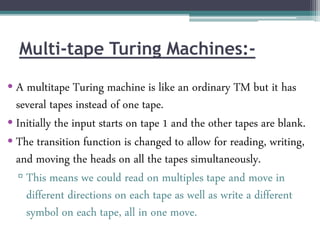
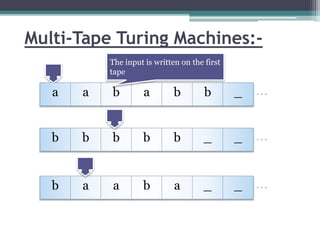
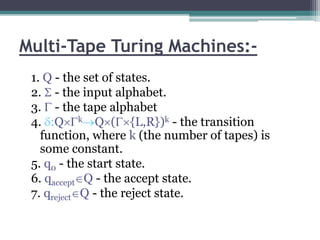
This document describes a report submitted by three students - Sonam Lanjewar, Sumbul Fatima Khan, and Aafaqueahmad Khan - on the theoretical foundations of computer science. It focuses on Turing machines, introducing them as a simple mathematical model of a computer conceived by Alan Turing in 1936. Key aspects of a Turing machine are described, including its finite tape divided into cells, read/write head, state register, and finite table of instructions defining its behavior based on the current state and symbol read. Formal definitions of Turing machines and multi-tape Turing machines are also provided. The document aims to inform the reader about Turing machines and their role in modeling computational capability.