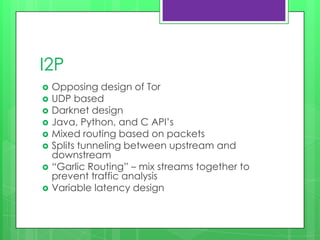
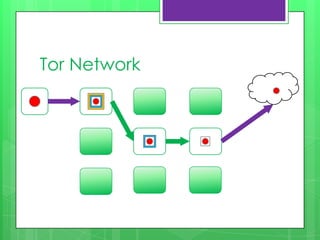
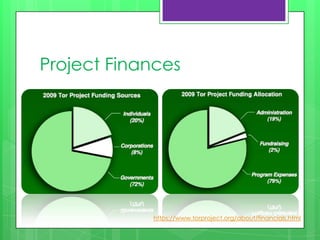
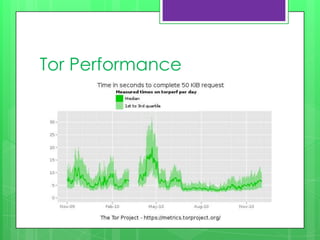
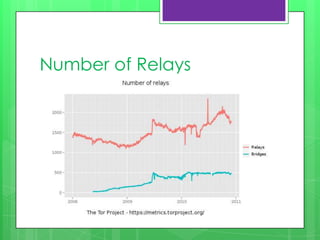
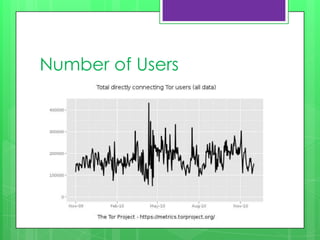
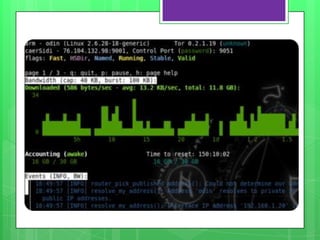
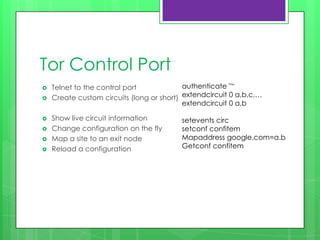
This document provides an overview of anonymity systems like Tor and I2P. It describes how Tor works by passing data through a series of proxies to hide a user's location and usage. The Tor Project is a non-profit organization that maintains the Tor network software to provide anonymity online. The document outlines potential attacks against Tor like traffic analysis, compromised relays, and social engineering. It also lists current sponsors and tools that can be used to access or configure the Tor network.