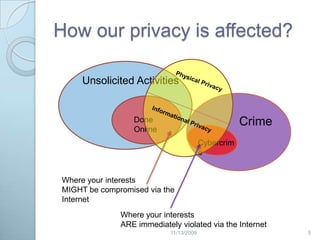
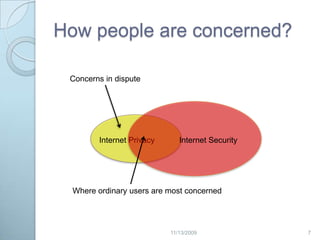
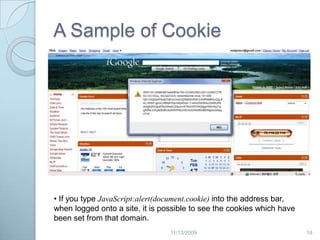
This document discusses privacy concerns related to revealing personal information online. It outlines many ways personal data can be disclosed, such as through internet service providers, email, browsers, search engines, social media and marketing. The document also presents some technical and legal solutions to better protect online privacy, such as cookie controls, encryption, and the Platform for Privacy Preferences framework. However, it notes the difficulty in regulating privacy given priorities around free speech and data sharing. Overall, the document provides context around online privacy issues and risks of personal data being revealed without consent through various internet activities.