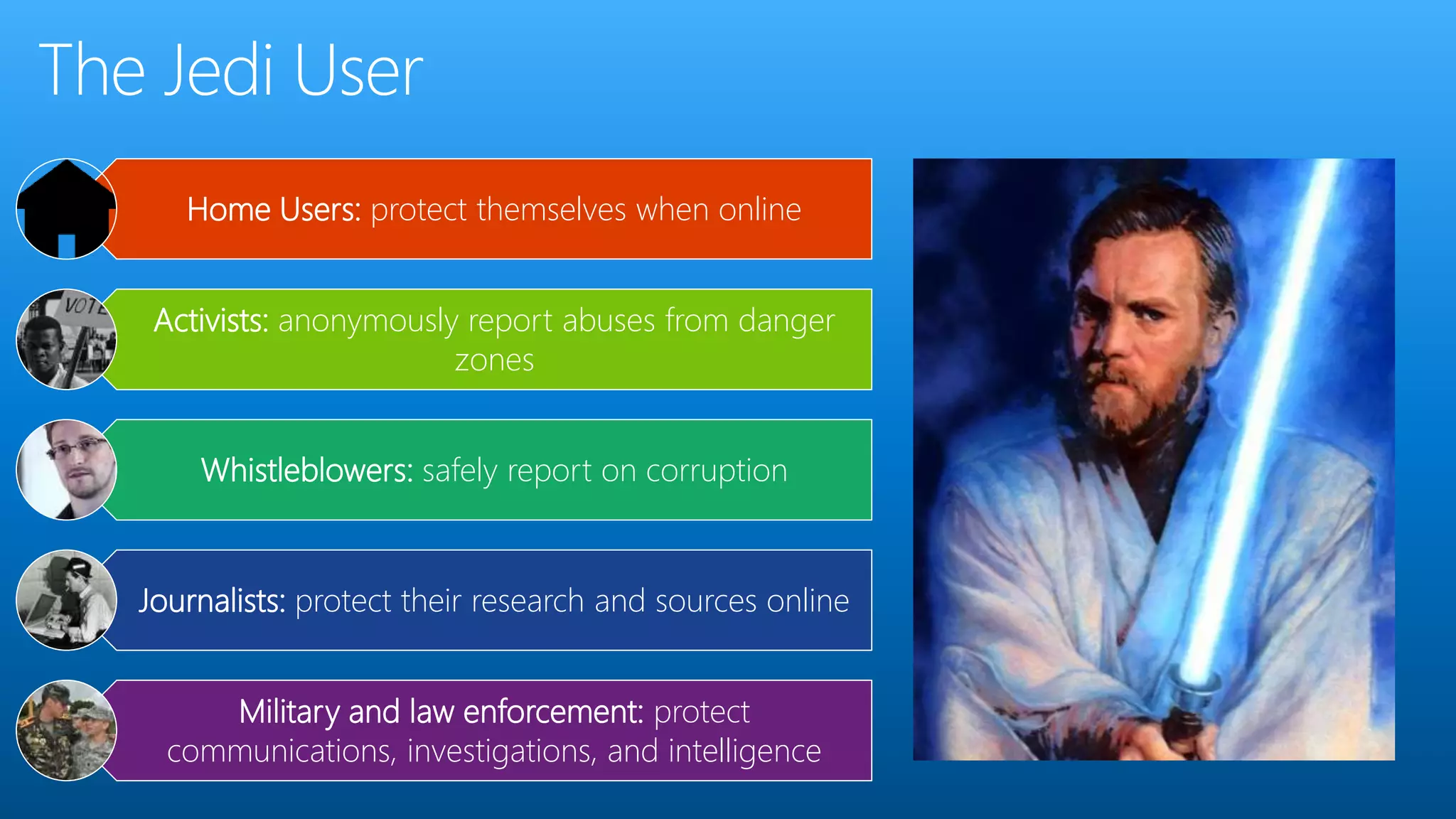
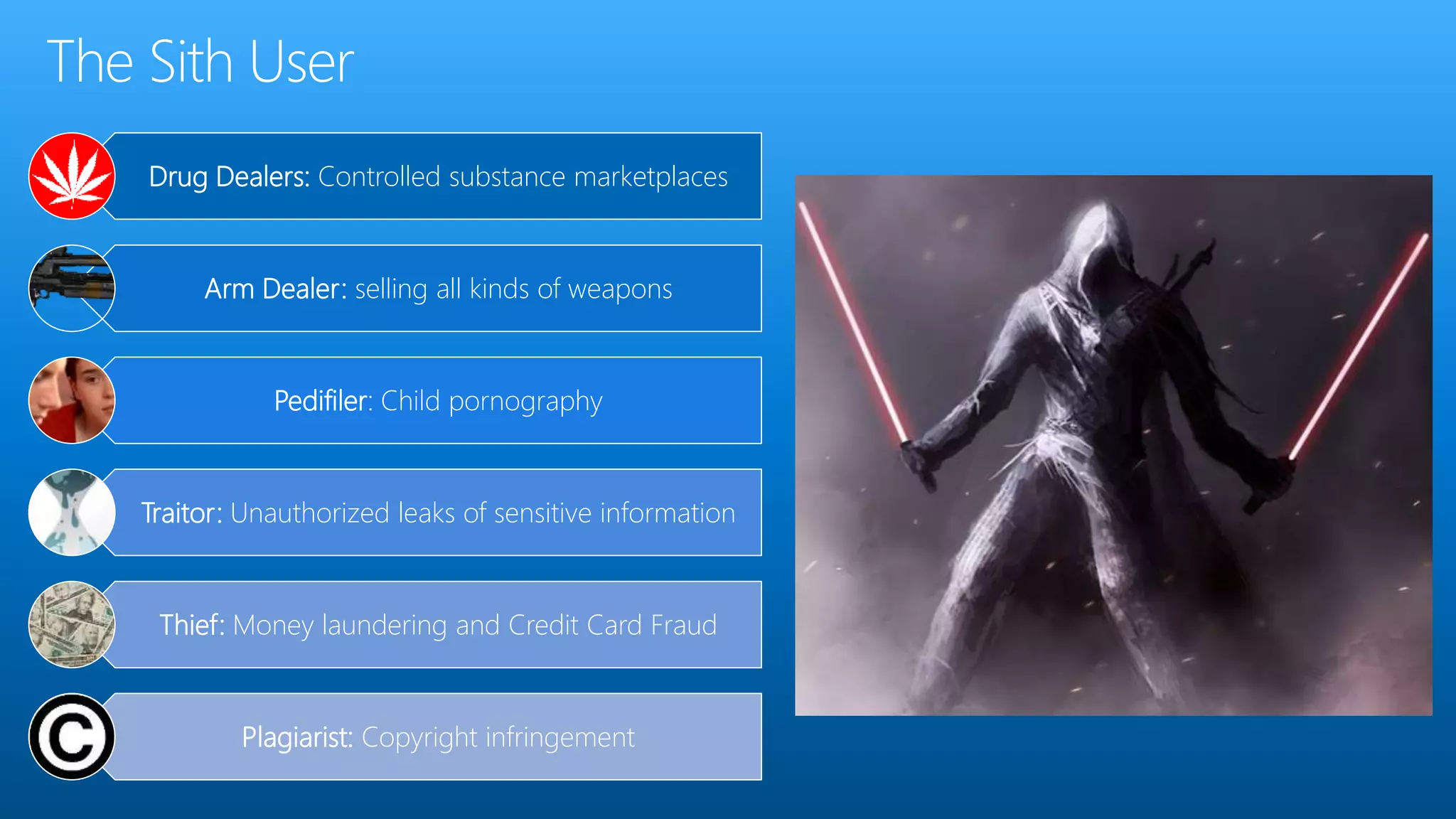
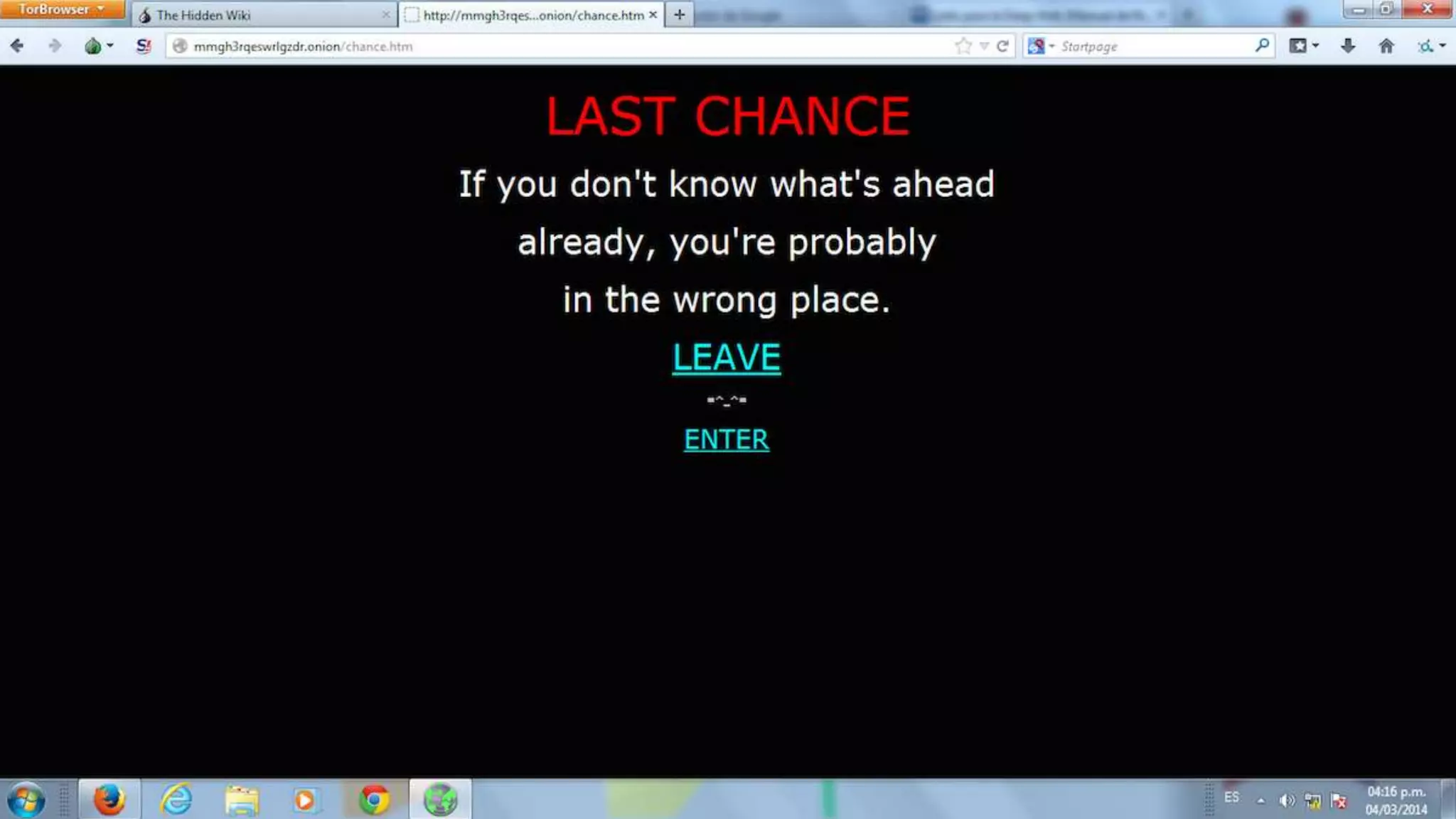
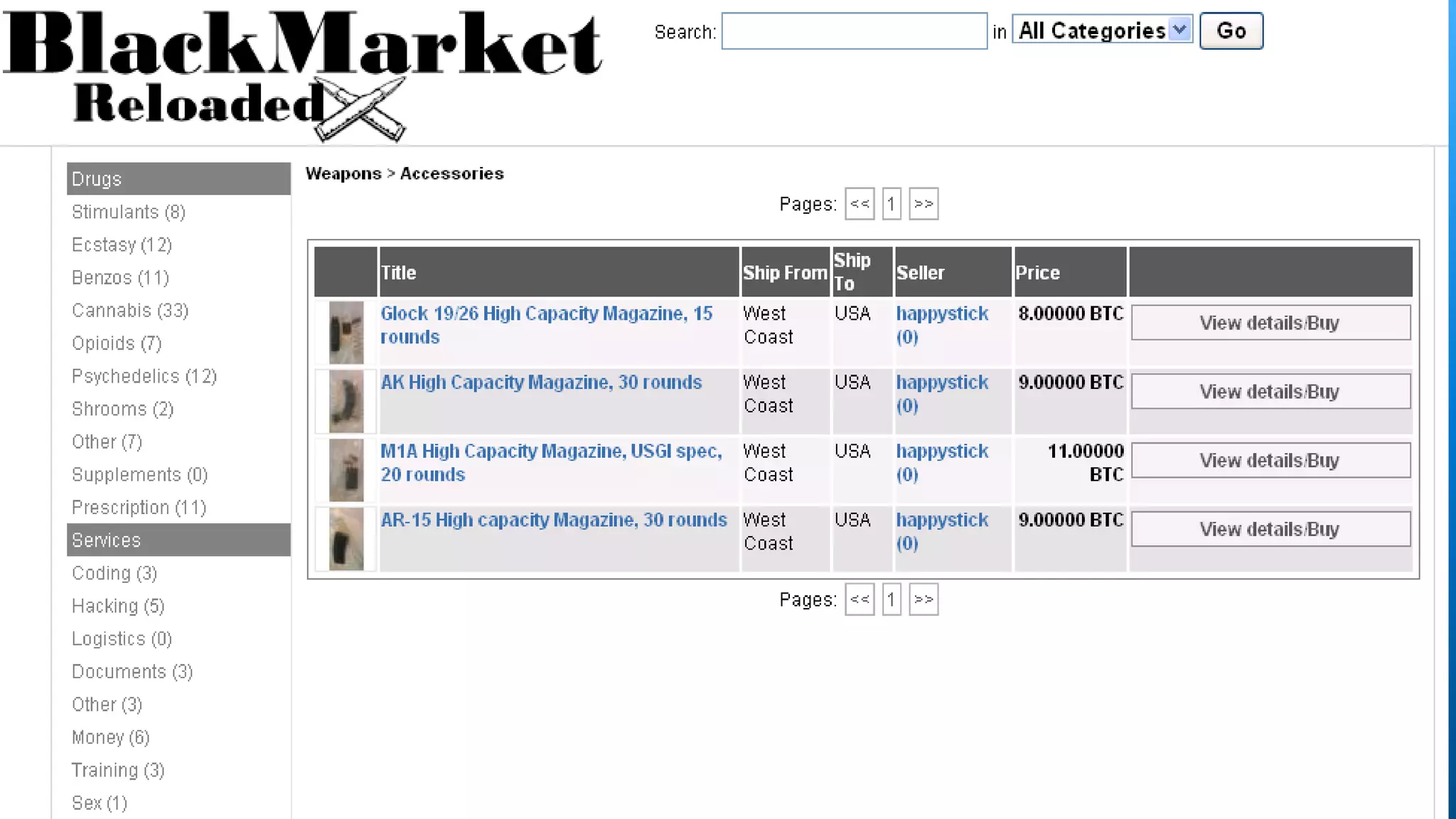
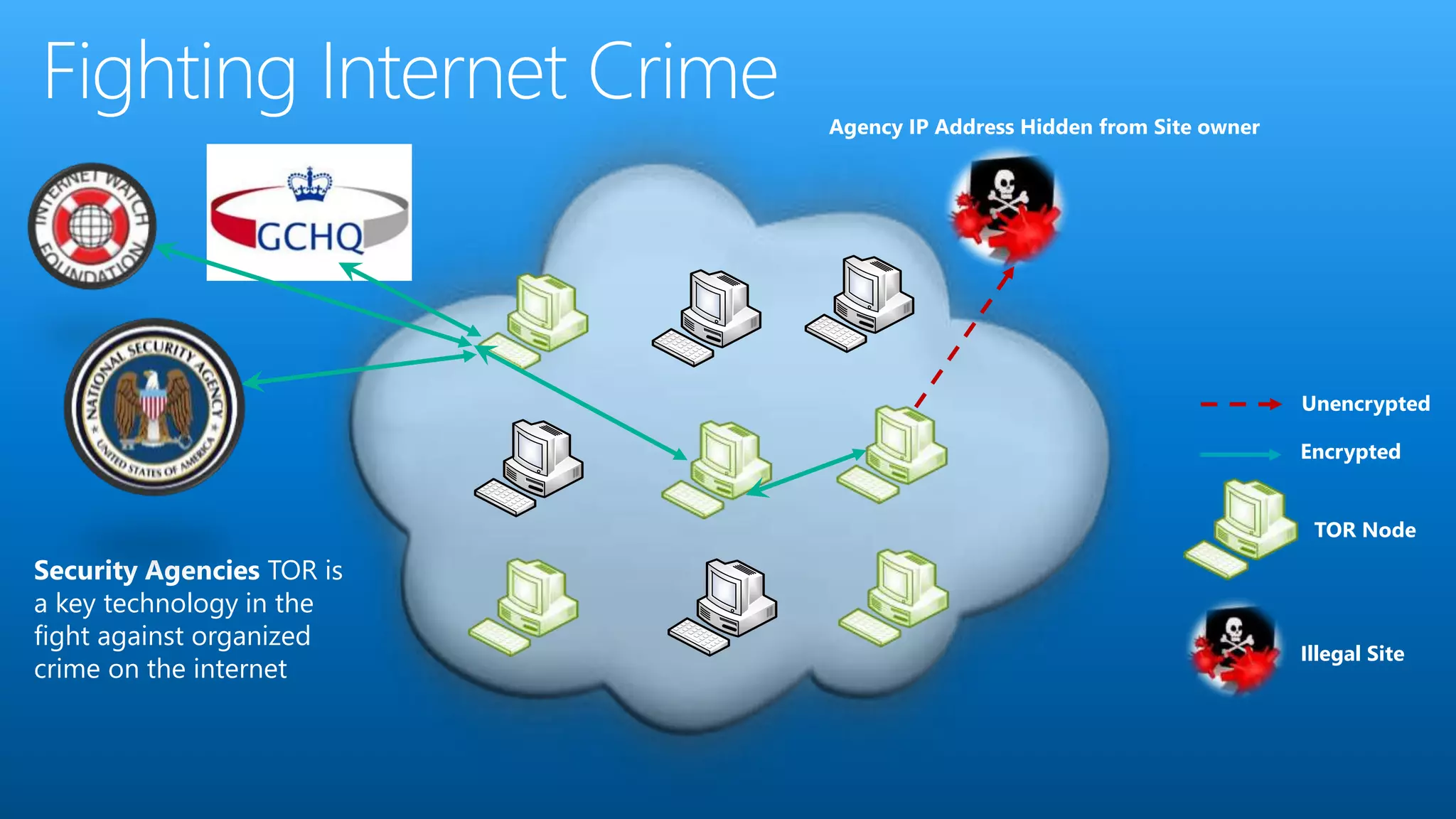
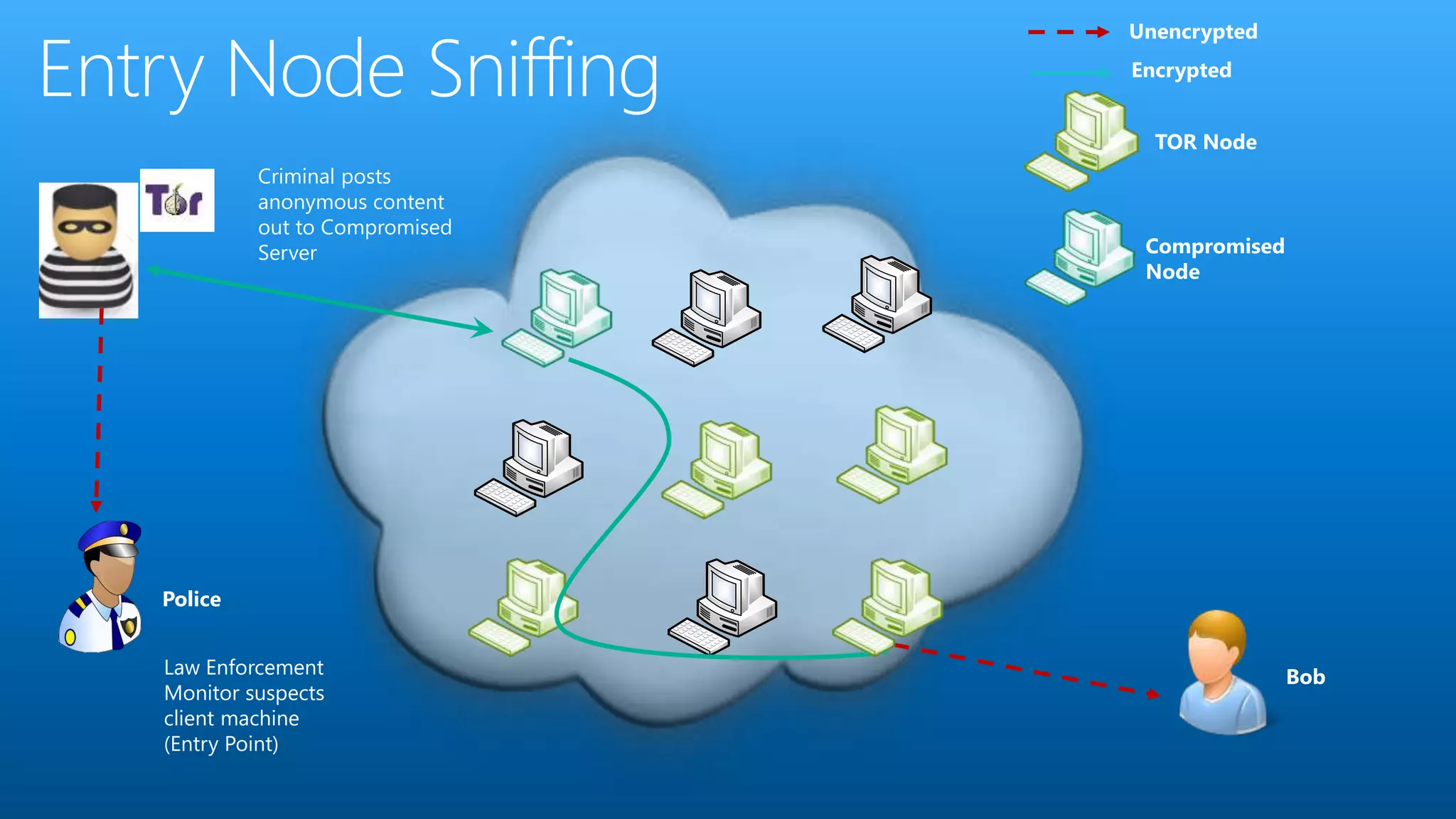
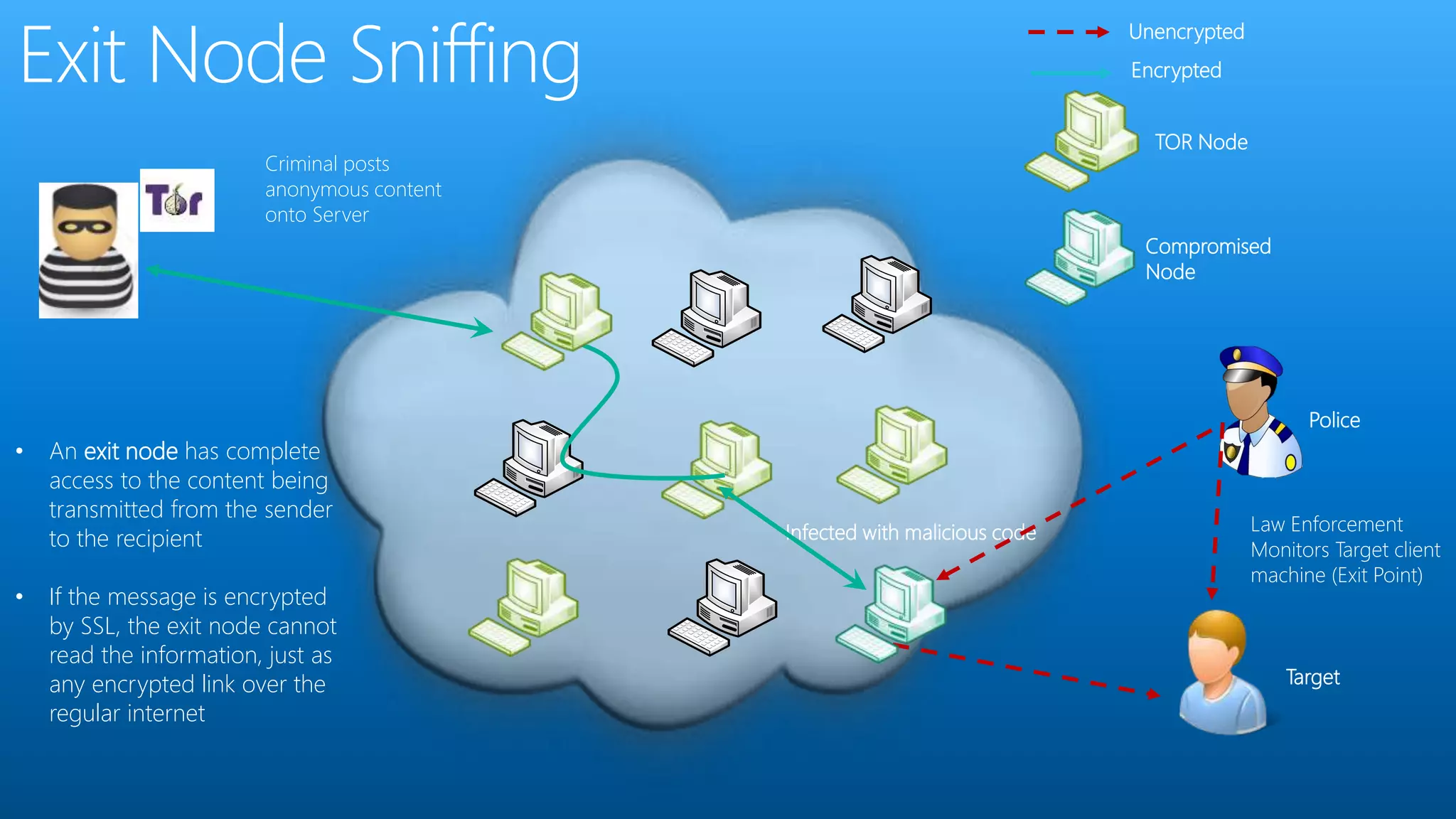
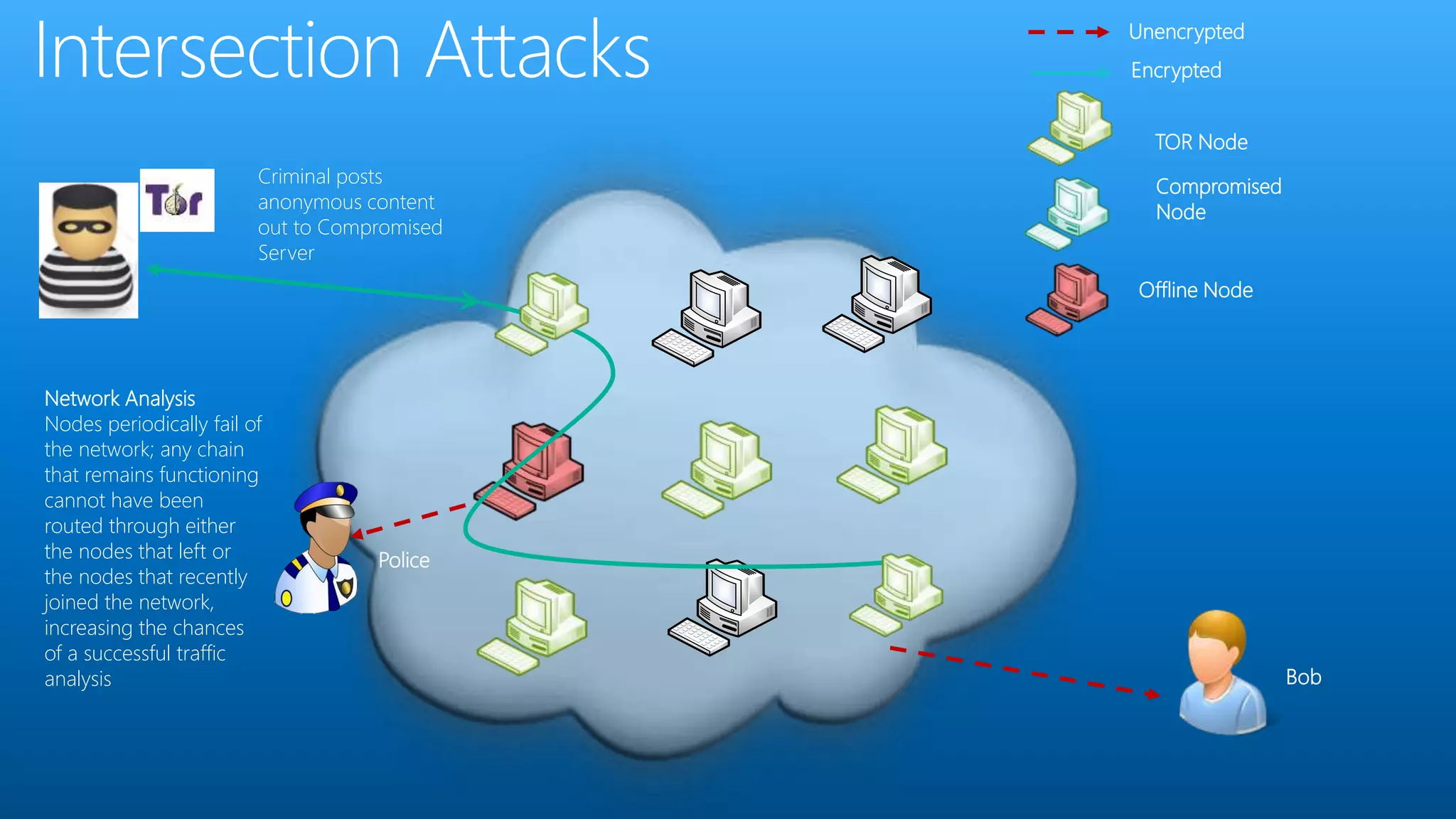
Paul Wilson is a husband, father, blogger, and marketer with nearly 20 years of experience in online marketing. He has a Master of Science in IT from Carnegie Mellon University and lobbied against child pornography. He explores both the positive and negative aspects of the dark web and TOR network in his blog and discusses how it can be used to both protect civil liberties and enable illegal activities.