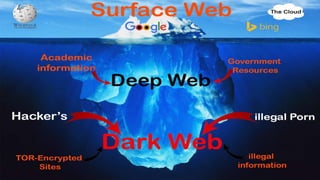
The document discusses Tor, an acronym for 'the onion router,' which is a free and open-source software enabling anonymous communication by concealing users' IP addresses and allowing access to restricted content. It highlights the advantages of Tor, its uses for various groups like activists and journalists, and mentions the dark web, including platforms like Sci-Hub and Facebook's .onion site. However, it also notes drawbacks such as slower speeds compared to VPNs and vulnerabilities like potential spying through exit nodes.