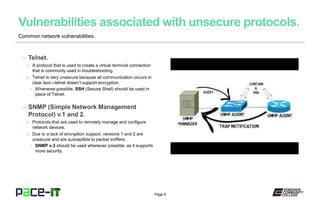
The document outlines common network vulnerabilities and the protocols that should be avoided due to their insecurity, such as Telnet, SNMP v.1 and v.2, FTP, and HTTP. It emphasizes the importance of keeping systems updated, closing unnecessary open ports, disabling unused services, encrypting communication channels, and being aware of applications that transmit credentials in clear text. Security is described as an ongoing task, requiring continuous assessment and action by network administrators.