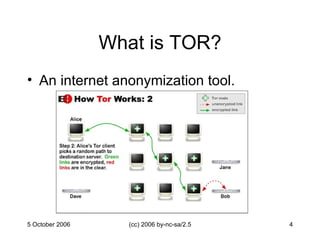
The document discusses the limitations of conducting Tor research at UC Berkeley, highlighting both legal and institutional barriers that hindered a planned experiment aimed at profiling Tor traffic. It outlines various options for researchers within the constraints posed by federal and state laws, as well as campus security policies. Recommendations are made to improve opportunities for Tor research while addressing these challenges.